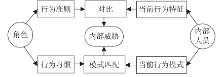
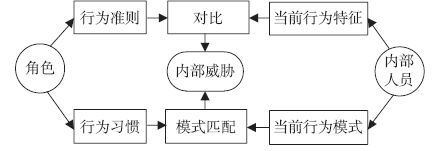
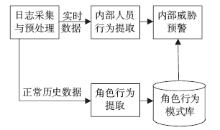
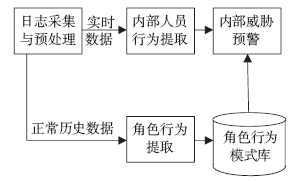
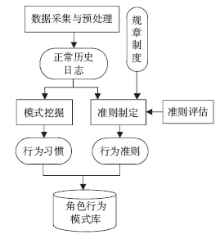
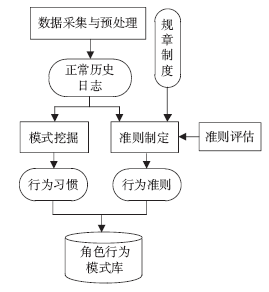
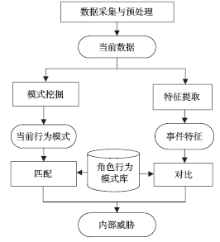
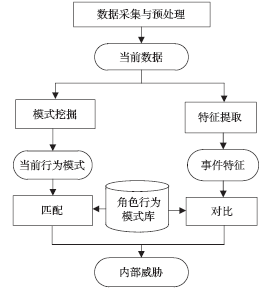
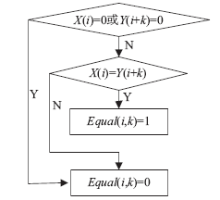
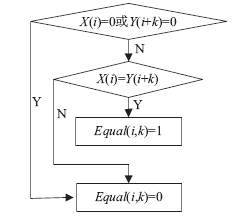
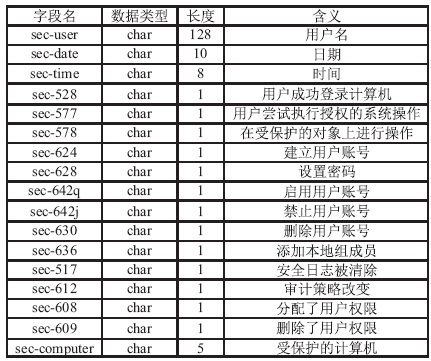
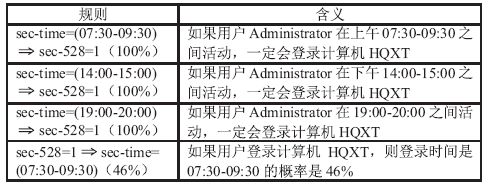
| [1] |
PARKER D B.Fighting Computer Crime: A New Framework for Protecting Information[M]. New York: John Wiley & Sons, 1998.
|
| [2] |
WOOD B J. An Insider Threat Model for Adversary Simulation[EB/OL]. , 2016-11-12.
|
| [3] |
PARK J S, HO S M. Composite Role-based Monitoring (CRBM) for Countering Insider Threats[EB/OL]. , 2016-11-12.
|
| [4] |
RAY I, POOLSAPASSIT N.Using Attack Trees to Identify Malicious Attacks from Authorized Insiders[C]//Spring. 10th European Symposium on Research in Computer Security, September 12-14, 2005, Milan, Italy. Heidelberg: Spring, 2005: 231-246.
|
| [5] |
叶伟伟,欧庆于,柏小武. 基于服务架构的密码服务系统认证方案研究[J]. 信息网络安全,2016(5):37-43.
|
| [6] |
SEO Y W, SYCARA K.Cost-sensitive Access Control for Illegitimate Confidential Access by Insiders[C]//2006 International Conference on Intelligence and Security Informatics, May 23-24, 2006, San Diego, CA, USA. Heidelberg: Spring, 2006, 3975: 117-128.
|
| [7] |
邵剑雨,陈福臻,秦鹏宇,等. 移动互联网环境下基于动态信任值的访问控制方法研究[J]. 信息网络安全,2016(8):46-53.
|
| [8] |
BYUN J W, LI Ninghui.Purpose Based Access Control for Privacy Protection in Relational Database Systems[J]. VLDB International Journal on Very Large Data Bases, 2008, 17(4): 603-619.
|
| [9] |
BEIMEL D, PELEG M.The Context and the SitBAC Models for Privacy Preservation-An Experimental Comparison of Model Comprehension and Synthesis[J]. IEEE Transactions on Knowledge and Data Engineering, 2010, 22(10): 1475-1488.
|
| [10] |
孙超. 基于用户行为和关系的内部风险分析[D]. 济南:山东大学,2015.
|
| [11] |
KAMRA A, TERZI E, BERTINO E.Detecting Anomalous Access Patterns in Relational Databases[J]. VLDB Journal- the International Journal on Very Large Data Bases, 2008, 17(5): 1063-1077.
|
| [12] |
KHOLIDY H A, BAIARDI F, Hariri S.DDSGA: A Data-driven Semi-global Alignment Approach for Detecting Masquerade Attacks[J]. IEEE Transactions on Dependable and Secure Computing, 2015, 12(2): 164-178.
|
| [13] |
MALOOF M A, STEPHENS G D.ELICIT: A System for Detecting Insiders Who Violate Need-to-Know[C]//Spring. 10th International Conference on Recent Advances in Intrusion Detection (RAID) September 5-7, 2007, Gold Goast, Australia. Heidelberg: Springer, 2007: 146-166.
|
| [14] |
文雨,王伟平,孟丹. 面向内部威胁检测的用户跨域行为模式挖掘[J]. 计算机学报,2016,39(8):1-15.
|
| [15] |
张锐. 基于文件访问行为的内部威胁异常检测模型研究[D]. 北京:北京交通大学,2015.
|
| [16] |
郭东峰. 基于分层特征云计算模型的电网内部威胁检测[J]. 计算机测量与控制,2013,21(2):340-343.
|
| [17] |
章文明. 基于异常概率和隐马尔科夫模型的资源滥用行为[D]. 衡阳:南华大学,2012.
|
| [18] |
闫超,南凯. 基于语义标签的协同信息系统内部隐私威胁检测模型[J]. 科研信息化技术与应用,2015,6(3):3-13.
|
| [19] |
杨姗媛,朱建明. 基于内部威胁的信息安全风险管理模型及防范措施[J]. 管理现代化,2013,(2):47-49.
|
| [20] |
矢敏,叶伟伟,欧庆于. 不需双线性对的基于身份的认证密钥协商协议[J]. 信息网络安全,2016(10):21-27.
|
| [21] |
梁礼,杨君刚,朱广良,等. 基于实时告警的层次化网络安全风险评估方法[J]. 计算机工程与设计,2013,34(7):2316-2323.
|
| [22] |
程思嘉,张昌宏,潘帅卿. 基于CP-ABE算法的云存储数据访问控制方案设计[J]. 信息网络安全,2016(2):1-6.
|
| [23] |
BARTH A, BONEH D, WATERS B.Privacy in Encrypted Content Distribution using Private Broadcast Encryption[C]//ACM. 10th International Conference on Financial Cryptography and Data Security, February 27-March 2, 2006, Anguilla, British West Indies. New York: ACM, 2006: 52-64.
|
| [24] |
范运东,吴晓平,石雄. 基于信任值评估的云计算访问控制模型研究[J]. 信息网络安全,2016(7):71-77.
|
| [25] |
GUNTER C A, LIEBOVITZ D M, MALIN B.Experience-based Access Management: A Life-cycle Framework for Identity and Access Management Systems[J]. IEEE Security and Privacy Magazine, 2011, 9(5): 48-55.
|
 ), Fang YUAN3
), Fang YUAN3