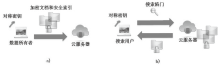
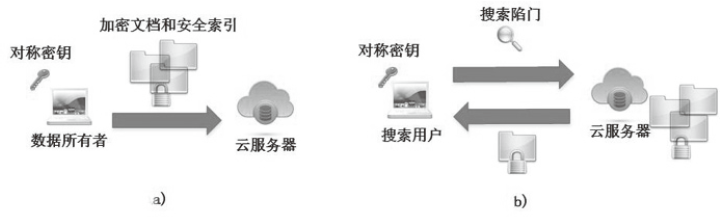
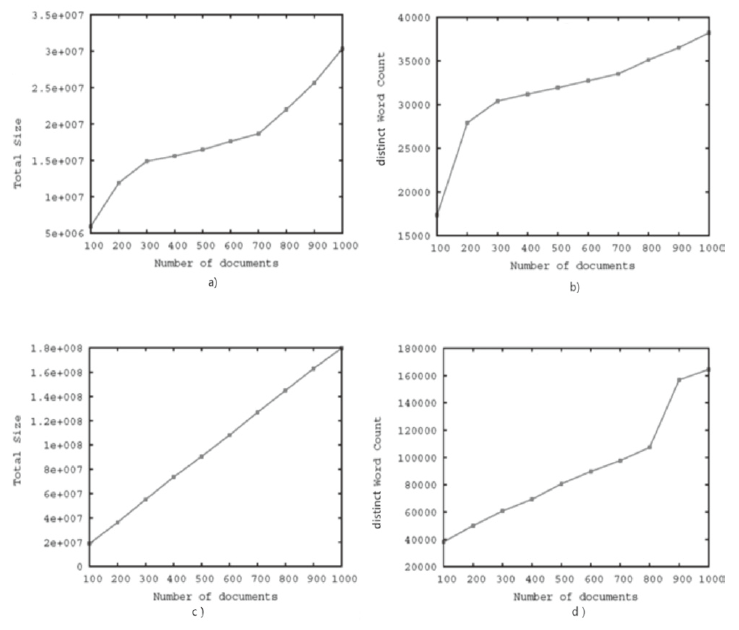
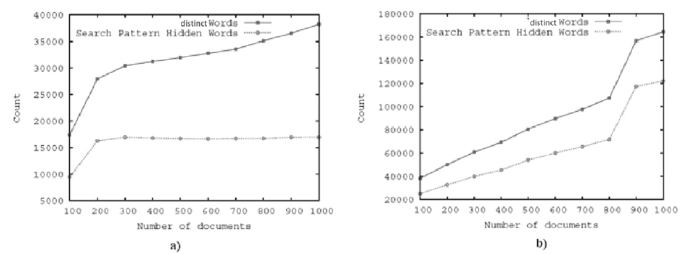
| [1] |
SP 800-145 The NIST Definition of Cloud Computing[S]. USA: National Institute of Standards & Technology, 2011.
|
| [2] |
ARMBRUST M, FOX A, GRIFFITH A, et al.Above the Clouds: A Berkeley View of Cloud Computing[R]. USA: University of California, Berkeley, Technical Report No.UCB/EECS-2009-28, 2009.
|
| [3] |
KAMARA S, LAUTER K E.Cryptographic Cloud Storage[C]//Springer. 14th International Conference on Financial Cryptography and Data Security, January 25-28, 2010, Tenerife, Canary Islands, Spain. Germany: Springer Berlin Heidelberg, 2010: 136-149.
|
| [4] |
GOH E J.Secure Indexes[R]. USA: IACR ePrint Cryptography Archive, 2003/216, 2003.
|
| [5] |
FRAKES W B, BAEZAYATES R.Information Retrieval: Data Structures and Algorithms[M]. USA: Prentice Hall, 1992.
|
| [6] |
CURTMOLA R, GARAY J, KAMARA S, et al.Searchable Symmetric Encryption: Improved Definitions and Efficient Constructions[C]//ACM. 13th ACM Conference on Computer and Communications Security, October 30-November 3, 2006, Alexandria, VA, USA. USA: ACM Press, 2006: 79-88.
|
| [7] |
CURTMOLA R, GARAY J, KAMARA S,et al.Searchable Symmetric Encryption: Improved Definitions and Efficient Constructions[J]. Journal of Computer Security, 2011, 19(5): 895-934.
|
| [8] |
张平,陈长松,胡红钢. 基于分组密码的认证加密工作模式[J]. 信息网络安全,2014(11):8-17.
|
| [9] |
ISLAM MS, KUZU M, KANTARCIOGLU M.Access Pattern Disclosure on Searchable Encryption: Ramification, Attack and Mitigation[C]// 19th Annual Network & Distributed System Security Symposium, February 5-8, 2012, San Diego, California, USA. USA: Internet Society, 2012: 12-26.
|
| [10] |
LIU C, ZHU L, WANG M, et al.Search Pattern Leakage in Searchable Encryption: Attacks and New Constructions[J]. Information Sciences, 2014, 256(1): 176-188.
|
| [11] |
秦志光,包文意,赵洋,等. 云存储中一种模糊关键字搜索加密方案[J]. 信息网络安全,2015(6):7-12.
|