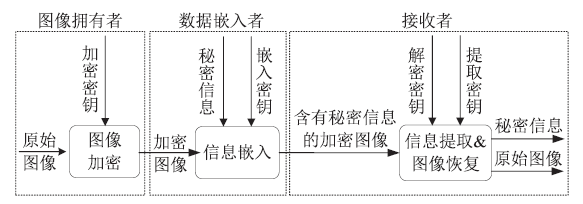
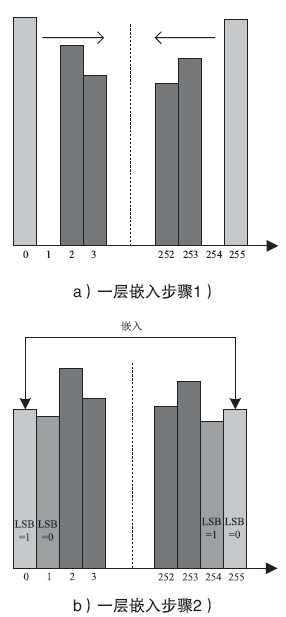
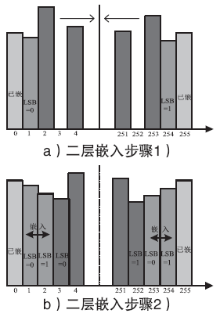
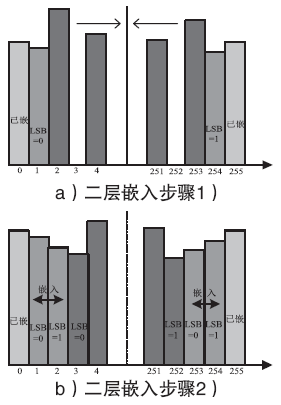
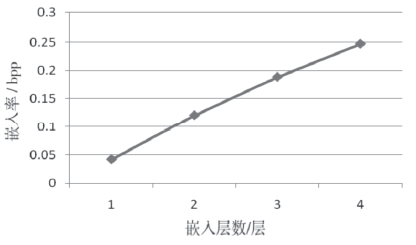
| [1] |
CELIK M U, SHARMA G, TEKALP A M.Lossless Watermarking for Image Authentication: A New Framework and an Implementation[J]. IEEE Transactions on Image Processing, 2006, 15(4): 1042-1049.
|
| [2] |
TIAN Jun.Reversible Data Embedding Using a Difference Expansion[J]. IEEE Transactions on Circuits and System for Video Technology, 2003, 13(8): 890-896.
|
| [3] |
NI Zhicheng, SHI Yunqing, NIRWAN A, et al.Reversible Data Hiding[J]. IEEE Transactions on Circuits and System for Video Technology, 2006, 16(3): 354-362.
|
| [4] |
TSA P, HU Yuchen, YEH H L.Reversible Data Hiding Scheme Using Predictive Coding and Histogram Shifting[J]. Signal Processing,2009,89(6): 1129-1143.
|
| [5] |
ZHANG Xinpeng.Reversible Data Hiding in Encrypted Images[J]. IEEE Signal Process Letters, 2011, 18(4): 255-258.
|
| [6] |
HONG W, CHEN T S, Wu Hanyan.An Improved Reversible Data Hiding in Encrypted Images Using Side Match[J]. IEEE Signal Process Letters, 2012, 19(4): 199-202.
|
| [7] |
LIAO Xin, SHU Changwen.Reversible Data Hiding in Encrypted Images Based on Absolute Mean Difference of Multiple Neighboring Pixels[J]. Journal of Visual Communication and Image Representation, 2015, 28(1): 21-27.
|
| [8] |
QIAN Zhenxing, ZHANG Xinpeng, REN Yanlin, et al. Block Cipher Based Separablereversible Data Hiding in Encrypted Images[EB/OL]. , 2015-7-7.
|
| [9] |
MA Kede, ZHAO Xianfeng.Reversible Data Hiding in Encrypted Images by Reserving Room Before Encryption[J]. IEEE Transactions on Information Forensics and Security, 2013, 8(3): 553-562.
|
| [10] |
ZHANG Weiming, MA Kede, YU Nenghai.Reversibility Improved Data Hiding in Encrypted Images[J]. Signal Processing, 2014, 94(1): 118-127.
|
| [11] |
肖迪,杜社,郑洪英. 基于差值域直方图平移的密文可逆水印算法[J]. 计算机应用研究,2014,31(12):3668-3672.
|
| [12] |
吕海峰,丁勇,代洪艳,等. LWE上的全同态加密方案研究[J]. 信息网络安全,2015(1):32-38.
|
| [13] |
CHEN Yuchi, SHIU C W, HORNG G.Encrypted Signal-based Reversible Data Hiding with Public Key Cryptosystem[J]. Journal of Visual Communication and Image Representation, 2014, 25(5): 1164-1170.
|
| [14] |
王志刚,马春光,史晓倩. 基于Binary LWE的全同态加密方案研究[J]. 信息网络安全,2015(7):41-50.
|
 ), Ying WANG, Yanting CHANG, Jiaqi ZHOU
), Ying WANG, Yanting CHANG, Jiaqi ZHOU