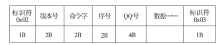
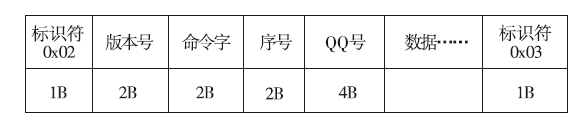
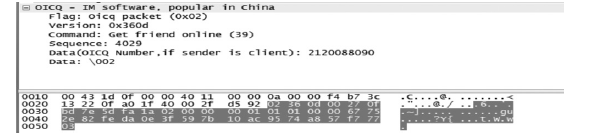
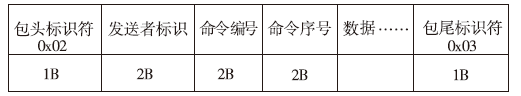
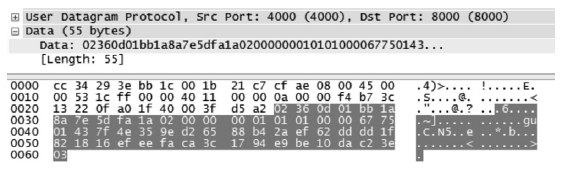
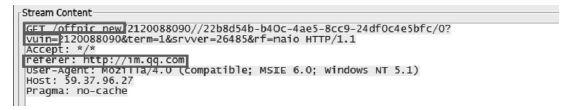
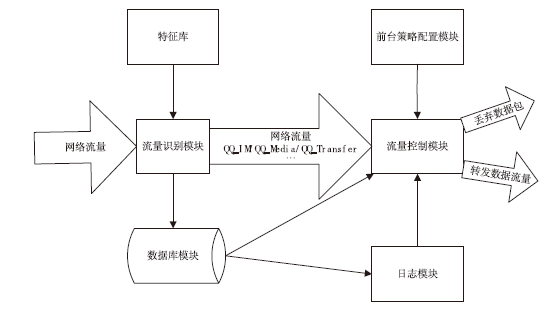
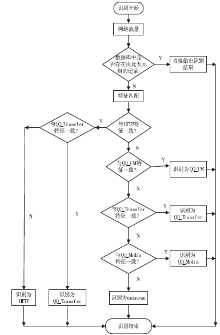
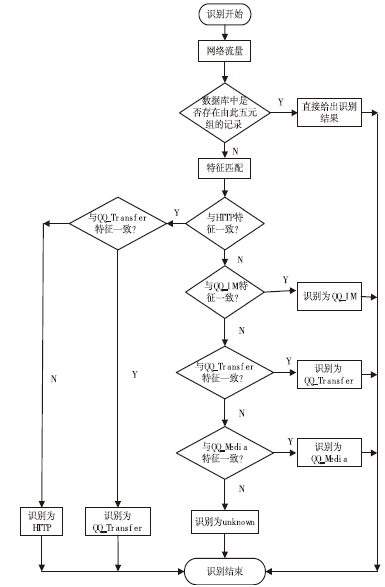
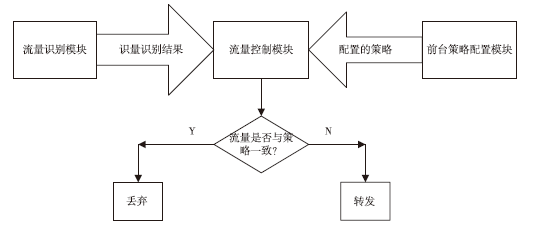
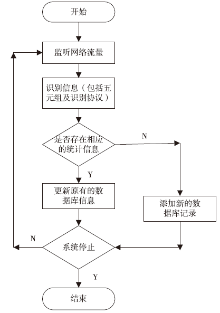
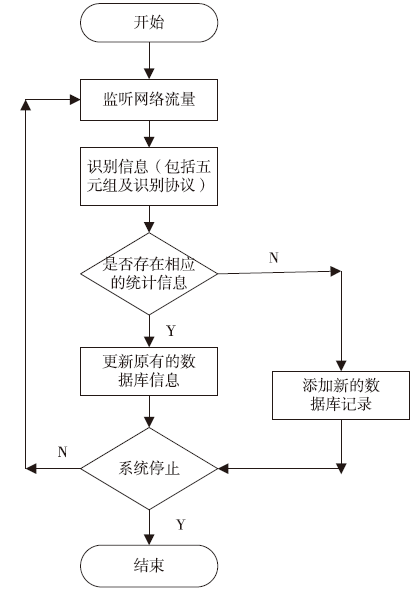
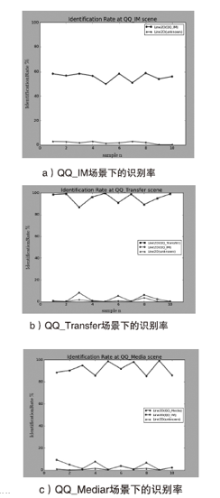
| [1] |
肖梅,辛阳. 基于朴素贝叶斯算法的VoIP流量识别技术研究[J]. 信息网络安全,2015(10):74-79.
|
| [2] |
金婷,王攀,张顺颐,等.基于DPI和会话关联技术的QQ语音业务识别模型和算法[J].重庆邮电学报:自然科学版,2006,18(6):789-792.
|
| [3] |
齐行程,刘文波.基于Netfilter L7-filter过滤系统的研究[J].电子科技,2011,24(3):31-33,37.
|
| [4] |
贾堃,孙长宾,姜凌.基于QQ软件的通信原理分析[J].数字研究与应用,2014(4):108-109.
|
| [5] |
CHEN Xiaoxian, YUAN Zhenlong, XUE Yibo.PBC: A Novel Method for Identifying QQ Traffic[C]//International Conference on Computing, Networking & CommunicationsIn. August 19-21,2014 in Xiamen, China. Proceeding of IEEE ICNC, 2014. :787-791.
|
| [6] |
李巍,李丽辉,李佳,等.远控型木马通信三阶段流量行为特征分析[J]. 信息网络安全,2015(5):10-15.
|
| [7] |
陈磊. 基于QQ聊天程序的通信原理编程探讨[J].赤峰学院学报(科学教育版),2011,3(4):133-134.
|
| [8] |
李晗. IP网络流量监测及用户行为分析[D].北京:北京邮电大学,2010.
|
| [9] |
卞琛,于兴艳,修位蓉,等.基于MPLS VPN技术的网络监控系统分析与设计[J]. 信息网络安全,2015(5):28-33.
|
| [10] |
刘胤. 深度包检测的研究与设计[D].贵阳:贵州大学,2008.
|
| [11] |
吴倩. 基于DPI与DFI的流量识别与控制系统的设计与实现[D].成都:电子科技大学,2013.
|
| [12] |
万兵,杨阳.VoIP流量监测技术的研究与应用[J].电信快报,2010(2):32-35.
|
| [13] |
丁卫球. 基于网络行为特征的木马检测技术[D]. 南京:南京邮电大学,2013.
|
| [14] |
杨俊. 移动P2P软件的下载调度与优化[D]. 武汉:华中科技大学,2013.
|
| [15] |
葛潇逸. UDP网络流量的分类研究[D]. 呼和浩特:内蒙古大学,2013.
|
| [16] |
张瀚. 基于DPI技术的P2P流量检测系统设计[D]. 北京:北京邮电大学,2013.
|
| [17] |
文政. 基于混沌-支持向量机理论的网络流量预测[D]. 郑州:郑州大学,2012.
|
| [18] |
贾艳艳. 基于被动测量的迅雷体系结构及下载策略研究[D]. 昆明:云南大学,2012.
|
| [19] |
周东旭. Ares协议分析与流量检测机制研究[D]. 南京:南京邮电大学,2012.
|
| [20] |
张小敏. 基于DPI的P2P流量识别方法研究[D]. 南京:南京邮电大学,2012.
|
| [21] |
荣义昌. 基于PDNS的BitTorrent流量局域化算法的仿真与实现[D]. 武汉:华中科技大学,2011.
|
| [22] |
杨东清. 计算机网络P2P流量的检测识别研究[D]. 昆明:云南大学,2011.
|
| [23] |
雷蕾. 关于P2P流媒体流量识别的研究与实现[D]. 上海:华东师范大学,2008.
|
| [24] |
王一. P2P流媒体监控平台的设计与实现[D]. 上海:上海交通大学,2008.
|
| [25] |
张文. 局域网下针对P2P流量识别技术的研究与实现[D]. 济南:山东大学,2007.
|
| [26] |
张海宁. 流量属性选择在P2P流量识别中的应用研究[D]. 北京:北京邮电大学,2008.
|
| [27] |
陆晓雯. P2P流量识别与控制系统的设计研究[D]. 南京:南京理工大学,2008.
|
| [28] |
任肖丽. P2P流量识别的研究与实现[D].上海:华东师范大学,2007.
|
| [29] |
沈磊. P2P流量控制系统的研究与实现[D]. 成都:电子科技大学,2007.
|
| [30] |
蔡向峰. 基于应用层的P2P流量识别研究[D]. 北京:北京邮电大学,2007.
|
| [31] |
刘强. P2P流量监控技术研究与实现[D]. 北京:北京邮电大学 2007.
|