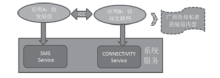
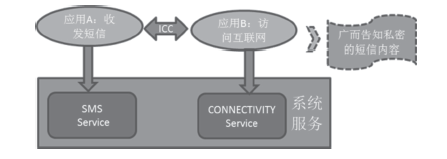
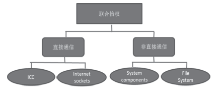
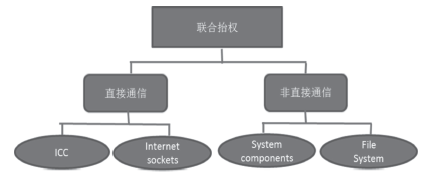
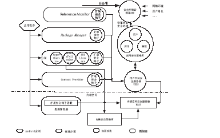
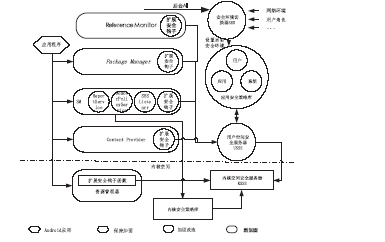
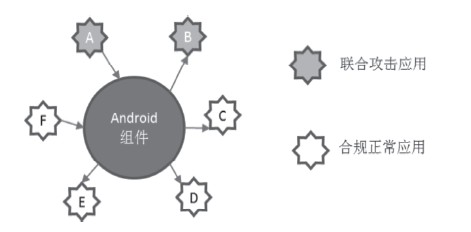
| [1] |
Llamas R, Restivo K, Shirer M.Android Marks Fourth Anniversary Since Launch with 75.0% Market Share in Third Quarter [EB/OL].https://www.idc.com/getdoc.jsp?containerId=prUS23771812,2012.
|
| [2] |
Armando A, Merlo A, Verderame L,et al.An Empirical Evaluation of the Android Security Framework[C] //Proceedings of the 28th IFIP TC-11 International Information Security and Privacy Conference (SEC 2013). Auckland:2013,176-189.
|
| [3] |
新浪科技. Android被曝多处安全漏洞影响所有版本 [EB/OL]. .
|
| [4] |
罗喧,梁柏青,潘军彪,等. 智能手机应用安全关键技术探讨[J]. 电信科学,2013,(5):19-27.
|
| [5] |
杨柳. Android驱动开发权威指南[M]. 北京:机械工业出版社,2014.
|
| [6] |
黄可臻,李宇翔,林柏钢. 基于Android的隐私数据安全保护系统[J]. 信息网络安全,2014,(9):54-57.
|
| [7] |
Hornyack P, Han S, Jung J,et al.These aren’t the Droids you’re looking for: Retrofitting Android to protect data from imperious applications[C] //Proceedings of the 18th ACM Conference on Computer and communications Security (CCS). Chicago, USA:2011.
|
| [8] |
Ongtang M, McLaughlin M, Enck W,et al. Semantically rich application-centric security in Android[J]. Security and Communication Networks,2012,5(6):658-673.
|
| [9] |
Enck I, Gilbert P, Chun B,et al.TaintDroid:An Information-Flow Tracking System for Realtime Privacy Monitoring on Smartphones[C]//Proceeding of 9th USENIX Symposium on Operating Systems Design and Implementation, OSDI 2010. Vancouver, BC, Canada:2010, 1-6.
|
| [10] |
刘洋, 邵旭东, 潘程达,胡正梁. 立体安全防御系统TDSD-Droid的实现[J]. 计算机科学,2013,(11A):228-234.
|
| [11] |
刘智伟,孙其博. 基于权限管理的Android应用行为检测[J]. 信息网络安全,2014,(6):72-77.
|
| [12] |
张金鑫,杨晓辉. 基于权限分析的Android应用程序检测系统[J]. 信息网络安全,2014,(7):30-34.
|
| [13] |
Sally. SELinux学习笔记[EB/OL]. .
|
| [14] |
郑志蓉. 可信计算平台可信计算基构建研究[J]. 信息安全与通信保密,2012,(9):116-117.
|