| [1] |
王小山,杨安,石志强,等. 工业控制系统信息安全新趋势[J]. 信息网络安全,2015,(1):6-11.
|
| [2] |
Flame[EB/OL].
|
| [3] |
姚为光. 软件加壳技术的研究[D].成都:电子科技大学. 2011.
|
| [4] |
任伟,柳坤,周金. AnDa:恶意代码动态分析系统[J]. 信息网络安全,2014,(8):28-33.
|
| [5] |
Chen X, Andersen J, Mao Z M, et al.Towards an understanding of anti-virtualization and anti-debugging behavior in modern malware[C]//Dependable Systems and Networks With FTCS and DCC, 2008. DSN 2008. IEEE International Conference on. IEEE, 2008: 177-186.
|
| [6] |
彭小详,户振江,龚涛,等. 恶意代码自动脱壳技术研究[J]. 信息网络安全,2014,(5):41-45.
|
| [7] |
Willems C, Holz T, Freiling F.Toward automated dynamic malware analysis using cwsandbox[J]. IEEE Security & Privacy, 2007 (2): 32-39.
|
| [8] |
Cuckoo Sandbox[EB/OL], .
|
| [9] |
Bayer U, Kruegel C, Kirda E.TTAnalyze: A tool for analyzing malware[M]. NA, 2006.
|
| [10] |
Anubis[EB/OL], https://anubis.iseclab.org/, 2015-6.
|
| [11] |
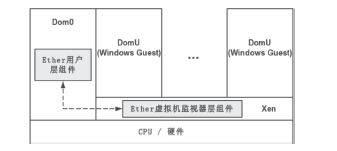
Dinaburg A, Royal P, Sharif M, et al.Ether: malware analysis via hardware virtualization extensions[C]//Proceedings of the 15th ACM conference on Computer and communications security. ACM, 2008: 51-62.
|
| [12] |
Smith J, Nair R.Virtual machines: versatile platforms for systems and processes[M]. Elsevier, 2005.
|
| [13] |
x86 virtualization[EB/OL].
|
| [14] |
Xen[EB/OL].
|
| [15] |
Neugschwandtner M, Platzer C, Comparetti P M, et al.Danubis-dynamic device driver analysis based on virtual machine introspection[M]//Detection of Intrusions and Malware, and Vulnerability Assessment. Springer Berlin Heidelberg, 2010: 41-60.
|
| [16] |
Chen P M, Noble B D.When virtual is better than real [operating system relocation to virtual machines][C]//Hot Topics in Operating Systems, 2001. Proceedings of the Eighth Workshop on. IEEE, 2001: 133-138.
|
| [17] |
Yan L K, Jayachandra M, Zhang M, et al.V2E: combining hardware virtualization and softwareemulation for transparent and extensible malware analysis[J]. ACM Sigplan Notices, 2012, 47(7): 227-238.
|
| [18] |
朱平,杜彦辉. 基于虚拟机与API调用监控技术的APT木马取证研究[J]. 信息网络安全,2014,(4):78-81.
|
 ), Li-min LIU1,3, Neng GAO1,3, Hong-da LI1,3
), Li-min LIU1,3, Neng GAO1,3, Hong-da LI1,3