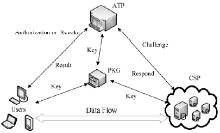
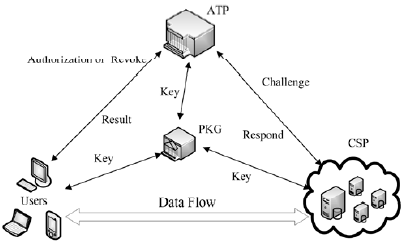
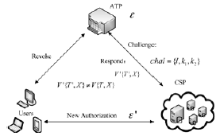
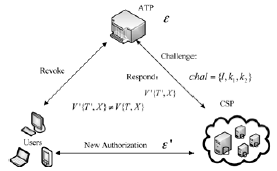
| [1] |
ATENIESE G, BURNS R, CURTMOLA R, et al.Provable data possession at untrusted stores [C]//Proceedings of the 14th ACM conference on Computer and communications security.Acm, 2007: 598-609.
|
| [2] |
ATENIESE G, DI PIETRO R, MANCINI L V, et al.Scalable and efficient provable data possession[C]//Proceedings of the 4th international conference on Security and privacy in communication netowrks. ACM, 2008: 9.
|
| [3] |
SEBÉ F, DOMINGO-FERRER J, MARTINEZ-BALLESTE A, et al.Efficient remote data possession checking in critical information infrastructures[J]. Knowledge and Data Engineering, IEEE Transactions on, 2008, 20(8): 1034-1038.
|
| [4] |
ERWAY C, KÜPÇÜ A, PAPAMANTHOU C, et al. Dynamic provable data possession[C]//Proceedings of the 16th ACM conference on Computer and communications security. Acm, 2009: 213-222.
|
| [5] |
WANG C, WANG Q, REN K, et al.Privacy-preserving public auditing for data storage security in cloud computing[C]//INFOCOM, 2010 Proceedings IEEE. Ieee, 2010: 1-9.
|
| [6] |
ZHU Y, HU H, AHN G J, et al.Cooperative provable data possession for integrity verification in multicloud storage[J]. Parallel and Distributed Systems, IEEE Transactions on, 2012, 23(12): 2231-2244.
|
| [7] |
WANG H.Proxy provable data possession in public clouds[J]. Services Computing, IEEE Transactions on, 2013, 6(4): 551-559.
|
| [8] |
WANG H.Identity-based distributed provable data possession in multi-cloud storage[J]. Services Computing IEEE Transactions on, 2015, 8(2):328-340.
|
| [9] |
ZHU Y, WANG H, HU Z, et al.Dynamic audit services for integrity verification of outsourced storages in clouds[C]//Proceedings of the 2011 ACM Symposium on Applied Computing. ACM, 2011: 1550-1557.
|
| [10] |
REN Y, CHEN Y, WANG J, et al.Leakage Resilient Provable Data Possession in Public Cloud Storage[C]//Intelligent Information Hiding and Multimedia Signal Processing (IIH-MSP), 2014 Tenth International Conference on. IEEE, 2014: 706-709.
|
| [11] |
REN Y, SHEN J, WANG J, et al.Security Analysis of Delegable and Proxy Provable Data Possession in Public Cloud Storage[C]//Intelligent Information Hiding and Multimedia Signal Processing (IIH-MSP), 2014 Tenth International Conference on. IEEE, 2014: 795-798.
|
| [12] |
ESINER E, KÜPÇÜ A, ÖZKASAP Ö. Analysis and Optimizations on FlexDPDP: A Practical Solution for Dynamic Provable Data Possession[C]//ICC: International Conference on Intelligent Cloud Computing, Muscat. 2014.
|
| [13] |
JUELS A, KALISKI JR B S. PORs: Proofs of retrievability for large files[C]//Proceedings of the 14th ACM conference on Computer and communications security. Acm, 2007: 584-597.
|
| [14] |
SHACHAM H, WATERS B.Compact proofs of retrievability[C]//14th International Conference on the Theory and Application of Cryptology and Information Security, Melbourne, Australia, 2008: 90-107.
|
| [15] |
WANG Q, WANG C, LI J, et al.Enabling public verifiability and data dynamics for storage security in cloud computing[C]//14th European Symposium on Research in Computer Security, Saint-Malo, France, 2009: 355-370.
|
| [16] |
ZHENG Q, XU S.Fair and dynamic proofs of retrievability[C]//Proceedings of the first ACM conference on Data and application security and privacy. ACM, 2011: 237-248.
|
| [17] |
MO Z, ZHOU Y, CHEN S.A dynamic Proof of Retrievability (PoR) scheme with O (logn) complexity[C]//Communications (ICC), 2012 IEEE International Conference on. IEEE, 2012: 912-916.
|
| [18] |
YUAN J, YU S.Proofs of retrievability with public verifiability and constant communication cost in cloud[C]//Proceedings of the 2013 international workshop on Security in cloud computing. ACM, 2013: 19-26.
|
| [19] |
BOWERS K D, JUELS A, OPREA A.Proofs of retrievability: Theory and implementation[C]//Proceedings of the 2009 ACM workshop on Cloud computing security. ACM, 2009: 43-54.
|
| [20] |
DODIS Y, VADHAN S, WICHS D.Proofs of retrievability via hardness amplification[C]//6th Theory of Cryptography Conference, TCC 2009, San Francisco, CA, USA, 2009, 2009: 109-127.
|
| [21] |
ZHU Y, WANG H, HU Z X, et al.Zero-knowledge proofs of retrievability[J]. Science China Information Sciences, 2011, 54(8): 1608-1617.
|
| [22] |
SHI E, STEFANOV E, PAPAMANTHOU C.Practical dynamic proofs of retrievability[C]//Proceedings of the 2013 ACM SIGSAC conference on Computer & communications security. ACM, 2013: 325-336.
|
| [23] |
LI J, TAN X, CHEN X, et al.OPoR: Enabling Proof of Retrievability in Cloud Computing with Resource-Constrained Devices[J]. Cloud Computing IEEE Transactions on, 2015, 3:1-1.
|
| [24] |
HUI C, YI M, MAN H A.Proof of retrievability with public verifiability resilient against related-key attacks[J]. Iet Information Security, 2015, 9(1):43-49.
|
| [25] |
BONEH D, LYNN B, SHACHAM H. Short signatures from the Weil pairing[J]. Journal of Cryptology, 2004, 17, (4): 297-319.
|
| [26] |
CERTICOM S E C.. SEC 2: Recommended Elliptic Curve Domain Parameters[EB/OL]. , 2015-3-25.
|
| [27] |
MILLER V.Use of elliptic curves in cryptography[C]//Advances in Cryptology—CRYPTO'85 Proceedings. Springer Berlin/Heidelberg, 1986: 417-426.
|
| [28] |
RIVEST R L, HELLMAN M E, ANDERSON J C, et al.Responses to NIST's Proposal[J]. Communications of the ACM, 1992, 35(7): 41-54.
|
 ), XIONG Hu, REN Hua-qiang
), XIONG Hu, REN Hua-qiang