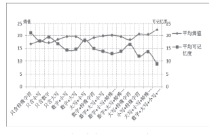
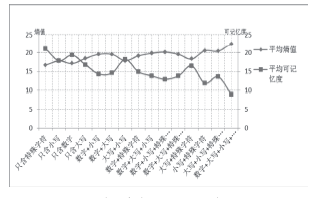
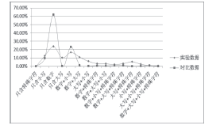
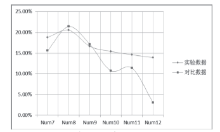
| [1] |
卿斯汉. 关键基础设施安全防护[J]. 信息网络安全,2015(2):1-6.
|
| [2] |
陈明. 白盒密码安全性分析与研究. 网络安全技术与应用,2015( 3): 116-117.
|
| [3] |
张平,陈长松,胡红钢. 基于分组密码的认证加密工作模式[J]. 信息网络安全,2014(11):8-17.
|
| [4] |
解理,任艳丽. 两个公钥加密方案的安全性分析[J]. 计算机应用研究,2015,32(1):218-221.
|
| [5] |
文伟平,郭荣华,孟正,等. 信息安全风险评估关键技术研究与实现[J]. 信息网络安全,2015(2):7-14.
|
| [6] |
MASSEY J L.Guessing and entropy[C]//IEEE, International Symposium on Information Theory, June 27-July 1, 1994, Trondheim, Norway. Piscataway: IEEE, 1994: 204.
|
| [7] |
KOMANDURI S, SHAY R, KELLEY P G, et al.Of Passwords and People: Measuring the Effect of Password-composition Policies[C]// ACM Special Interest Group on Computer-Human Interaction, Conference on Human Factors in Computing Systems. May 7-12, 2011, Vancouver, Canada. New York: ACM, 2011: 2595-2604.
|
| [8] |
KULKARNI D.A Novel Web-based Approach for Balancing Usability and Security Requirements of Text Passwords[J]. International Journal of Network Security & its Applications, 2010, 2(3): 1.
|
| [9] |
CLAIR L S, JOHANSEN L, ENCK W, et al.Password Exhaustion: Predicting the End of Password Usefulness[J]. Lecture Notes in Computer Science, 2006 (4332): 37-55.
|
| [10] |
BURR W E, DODSON D F, NEWTON E M, et al.Electronic Authentication Guideline[M]. Gaithersburg: National Institute of Standards and Technology, 2004.
|
| [11] |
VU K P L, PROCTOR R W, BHARGAV S A, et al. Improving Password Security and Memorability to Protect Personal and Organizational information[J]. International Journal of Human-Computer Studies, 2007, 65(8): 744-757.
|