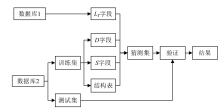
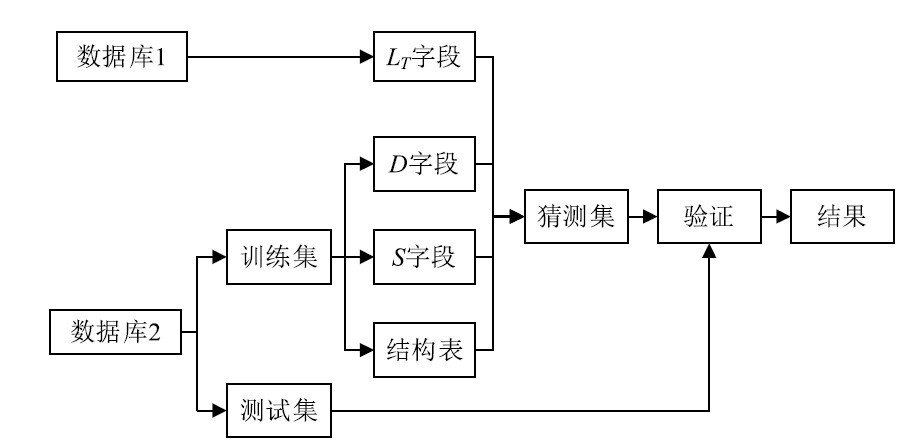
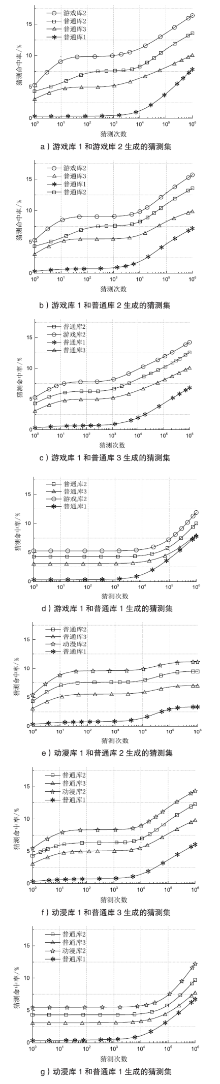
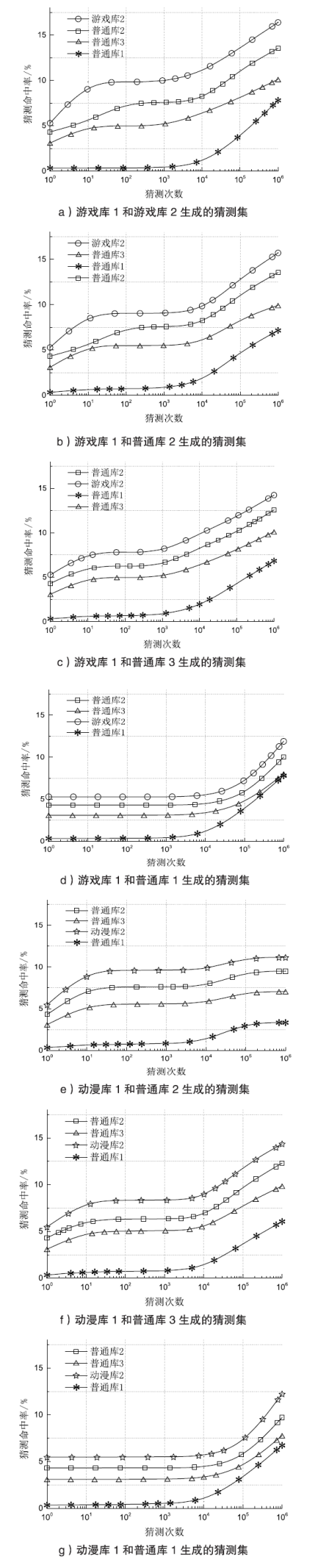
| [1] |
WANG Ding, WANG Nan, WANG Ping, et al. Preserving Privacy for Free: Efficient and Provably Secure Two-factor Authentication Scheme with User Anonymity[EB/OL]. , 2018-12-11.
|
| [2] |
BIDDLE R, CHIASSON S, VAN OORSCHOT P C. Graphical Passwords: Learning from the First Twelve Years[J]. ACM Computing Surveys, 2012, 44(4): 1-41.
|
| [3] |
KEITH M, SHAO B, STEINBART P J.The Usability of Passphrases for Authentication: An Empirical Field Study[J]. International Journal of Human-computer Studies, 2007, 65(1): 17-28.
|
| [4] |
BONNEAU J.The Science of Guessing: Analyzing an Anonymized Corpusof 70 Million Passwords[C]//IEEE. 2012 IEEE Symposium on Security and Privacy, May 20-23, 2012, San Francisco, CA, USA. New Jersey: 2012: 538-552.
|
| [5] |
UR B, KELLY P G, KOMANDURI S, et al.How Does Your PasswordMeasure Up? The Effect of Strength Meters on Password Creation[C]//ACM. 21st USENIX Conference on Security symposium, August 8-10, 2012, Bellevue, CA, USA. New York: ACM, 2012: 65-80.
|
| [6] |
MELICHER W, UR B, SEGRETI S M, et al.Fast, Lean, and Accurate: Modeling Password Guessability Using Neural Networks[J]. Journal of Networks, 2013, 8(6): 1278-1284.
|
| [7] |
VAITHYASUBRAMANIAN S, CHRISTY A.A Scheme to Create Secured Random Password Using Markov Chain[J]. Artificial Intelligence and Evolutionary Algorithms in Engineering Systems, 2014, 2(11): 809-814.
|
| [8] |
VERASR, COLLINS C, THORPE J. On the Semantic Patterns of Passwords and Their Security Impact[EB/OL]. , 2018-12-12.
|
| [9] |
NEDERHOF M J, SATTA G.Computing Partition Functions of PCFGs[J]. Research on Language & Computation, 2009, 7(2-4): 233-233.
|
| [10] |
MA J, YANG Weining, LUO Min, et al.A Study of Probabilistic Password Models[C]//IEEE. 2014 IEEE Symposium on Security and Privacy, May 18-21, 2014, San Jose, CA, USA. New Jersey: IEEE, 2014: 689-704.
|
| [11] |
WAGN Ding, CHENG H, GU Q, et al. Understanding Passwords of Chinese Users: Characteristics, Security, and Implications[EB/OL]. , 2018-12-22.
|
| [12] |
SHAY R, BAUER L, CHRISTIN N, et al.A Spoonful of Sugar?: The Impact of Guidance and Feedback on Password-creation Behavior[C]//ACM. 33rd Annual ACM Conference on Human Factors in Computing Systems, April 18-23, 2015, Seoul, Republic of Korea. New York: ACM, 2015: 2903-2912.
|
| [13] |
WEIR M, AGGARWAL S, MEDEIROS B D, et al.Password Cracking Using Probabilistic Context-free Grammars[C]//IEEE. 30th IEEE Symposium on Security and Privacy, May 17-20, 2009, Berkeley, CA, USA. New Jersey: IEEE, 2009: 391-405.
|
| [14] |
NARAYANAN A, SHMATIKOV V.Fast Dictionary Attacks on Passwords Using Time-space Tradeoff[C]//ACM. 12th ACM Conference on Computer and Communications Security, November 7-11, 2005, Alexandria, VA, USA. New York: ACM, 2005: 364-372.
|
| [15] |
FLORENCIO D, HERLEY C. A Large-scale Study of Web Password Habits[C]//ACM. 16th International Conference on World Wide Web, May 8-12, 2007, Banff, Alberta, Canada. New York: 657-666.
|
| [16] |
WANG Ding, CHENG Haibo, WANG Ping. Understanding Passwords of Chinese Users: A Data-driven Approach[EB/OL]. ,2019-1-10.
|
| [17] |
FURNELL S.An Assessment of Website Password Practices[J]. Comput Secur, 2007, 26(7): 445-451.
|
| [18] |
LIU Gongshen, QIU Weidong, MENG Kui, et al.Password Vulnerability Assessment and Recovery Based on Real Data Mining[J]. Chinese Journal of Computers, 2016, 39(3): 454-467.
|
|
刘功申,邱卫东,孟魁,等.基于真实数据挖掘的口令脆弱性评估及恢复[J].计算机学报,2016,39(3):454-467.
|
| [19] |
LI Zhigong, HAN Weili, XU Wenyuan. A Large-scale Empirical Analysis on Chinese Web Passwords[C]//ACM. 23rd USENIX conference on Security Symposium, August 20-22, 2014, San Diego, CA. New York: ACM: 559-574.
|
| [20] |
DAILEY D V, MARKUS DÜRMUTH, PAAR C. Statistics on Password Re-use and Adaptive Strength for Financial Accounts[C]//Springer. 2014 International Conference on Security and Cryptography for Networks, September 3-5, 2014, Amalfi, Italy. Heidelberg: Springer, 2014: 218-235.
|
| [21] |
YOU Lin, LIANG Jiahao.Research on Secure Identity Authentication Based on Homomorphic Encryption and Biometrics[J]. Netinfo Security, 2018, 18(4): 7-14.
|
|
游林,梁家豪.基于同态加密与生物特征的安全身份认证研究[J].信息网络安全,2018,18(4):7-14.
|
 ), Yufu LI2
), Yufu LI2