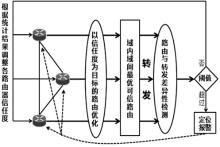
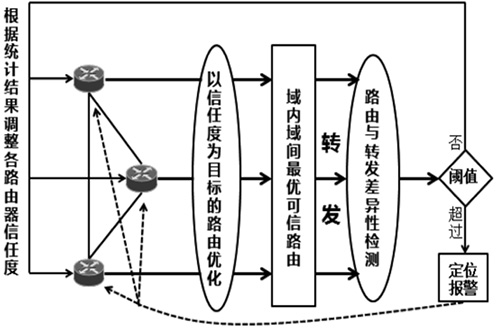
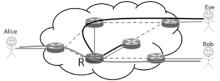
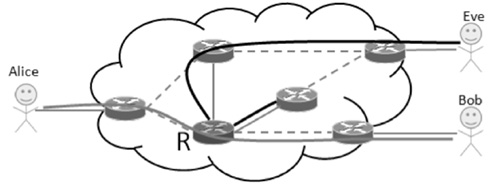
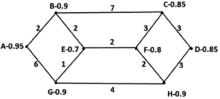
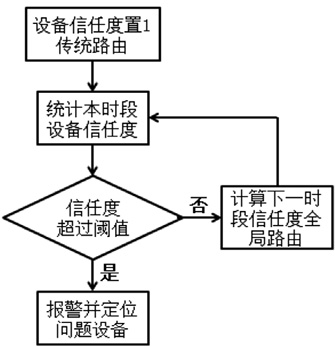
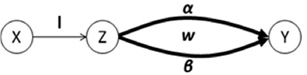
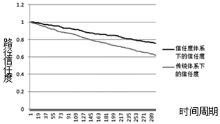
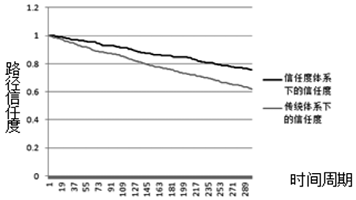
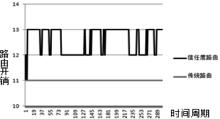
| [1] |
Wikipedia. PRISM (surveillance program) [EB/OL]., 2014-10-31.
|
| [2] |
南华早报.斯诺登:美国政府长期窃取中国大陆及香港网络信息[EB/OL]. , 2013-6-12.
|
| [3] |
林闯,汪洋,李泉林. 网络安全的随机模型方法与评价技术[J].计算机学报,2005,28(12):1943-1956.
|
| [4] |
林闯,彭学海.可信网络研究[J].计算机学报,2005,28(5):751-758.
|
| [5] |
林闯,王元卓,田立勤.可信网络的发展及其面对的技术挑战[J].中兴通讯技术,2008,14(1):14-41.
|
| [6] |
罗安安,林闯,王元卓,等.可信网络连接的安全量化分析与协议改进[J].计算机学报,2009,32(5):887-898.
|
| [7] |
林闯,王元卓.基于随机博弈模型的网络安全分析与评价[M].北京:清华大学出版社,2012.
|
| [8] |
李小勇,桂小林,毛倩,等.基于行为监控的自适应动态信任度测模型[J]. 计算机学报,2009,32(4):664-674.
|
| [9] |
李小勇,桂小林.可信网络中基于多维决策属性的信任量化模型[J].计算机学报, 2009 ,32(3):405-416.
|
| [10] |
徐恪,朱亮,朱敏. 互联网地址安全体系与关键技术[J]. 软件学报, 2014,25(1):78-97.
|
| [11] |
徐恪,朱敏,林闯.互联网体系结构评估模型、机制及方法研究综述[J]. 计算机学报,2012,35(10):1985-2006.
|
| [12] |
Pierre Francois, Clarence Filsfils, John Evans, et al.Achieving SubSecond IGP Convergence in Large IP Networks[C]//Proc.SIGCOMM, 2005, 35(2):35-44.
|
| [13] |
Joao Luıs Sobrinho.Network Routing with Path Vector Protocols: Theory and Applications[C]// Proc.SIGCOMM,2003:49-60
|
| [14] |
张焕国,罗捷,金刚,等.可信计算研究进展[J]. 武汉大学学报, 2006,52(5):513-518.
|
| [15] |
张焕国,陈璐,张立强.可信网络连接研究[J].计算机学报,2010,33(1):706-717.
|
| [16] |
徐恪,徐明伟,陈文龙.高级计算机网络[M]. 北京:清华大学出版社,2012.
|
 ), XU Ke, ZHU Liang
), XU Ke, ZHU Liang