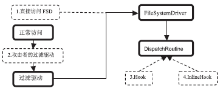
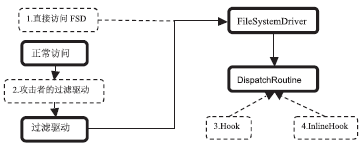
| [1] |
SUN Ying-ying, ZHENG Kou-gen,Filemonitoringsystem based on minifilter[J]. Journal of Computer Applications, 2010,30(11):3115-3117.
|
| [2] |
FileSystemFilterDrivers[EB/OL]..
|
| [3] |
XUE Sheng-jun, CAO Feng-yan.Security Software Files Protection Based on Minifilter[J]. JOURNAL OF WUHAN UNIVERSITY OF TECHNOLOGY, 2011,33(4):130-133.
|
| [4] |
FileSystemMinifilterDrivers[EB/OL]. .
|
| [5] |
ZHANG Fan,SHI Cai-cheng.Windows Driver Development Internals[M]. Beijing: Publishing House of Electronics Industry,2008.
|
| [6] |
TAN Wen,YANG Xiao,SHAO Jian-lei.Windows Kernel security programming[M].Beijing: BEIJING Publishing House of Electronics Industry,2009.
|
| [7] |
CHEN Jian-xiong,JIE She,ZHANG Xin.Implementation of Virus Prevention Method Based on File System Filter Driver[J].COMPUTER TECHNOLOGY AND DEVELOPMENT,2013,23(3):143-146.
|
| [8] |
GE Yang-yang,MAO Yu-guang,File Security Protection System Based on Minifilter[J]. Computer & Digital Engineering, 2013,(4):631-634.
|
| [9] |
YAN Zhen, LIU Ming,File monitoring system based on file filter driver design and implementation[D].Chengdu:University of electronic science and technology of computer system structure. 2012.
|
| [10] |
HU Ji-ying, ZHAI Jian-song, SONG Yang.A file system based on Minifilter framework design and implementation of security module[D].Ha Er-bin:Harbin industrial university, 2013.
|
| [11] |
PI Chang-di, LIU Nai-qi.Secure file system based on filter drivers in the research and implementation[D].Chengdu:Department of electronic science and technology of large software engineering,2010.
|
| [12] |
LIU Sheng,ZHOU An-min, JIANG Lei.File operations detecting system based on minifilter driver[J].Information and electronic engineering,2012,10(6):779-782.
|
| [13] |
LI Min, FANG Yong, LIU Lin-chao, XIONG Fan.File Driver on FSD and its Applications[J].Information and electronic engineering, 2005, 3(4):290-292.
|
| [14] |
CHEN Ling, TANG Zhen-min.Redirect implementation and its application in file system filter driver[J].The information technology,The China science and technology information 2007, (22):92-93.
|
| [15] |
WANG Yang,WANG Qin,The development of the sandbox security technology research[J].Software Guide,2009,8(8):152-153.
|