Netinfo Security ›› 2014, Vol. 14 ›› Issue (10): 54-58.doi: 10.3969/j.issn.1671-1122.2014.10.010
Previous Articles Next Articles
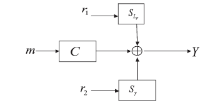
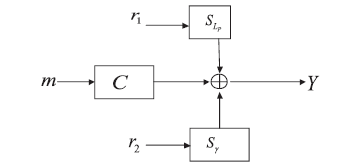
Research on Parameter Selection of a Code-based Public-Key Cryptosystem
XU Quan-zuo, CAI Qing-jun
- School of Mathematics and Information Science of Guangzhou University, Guangzhou Guangdong 510006, China