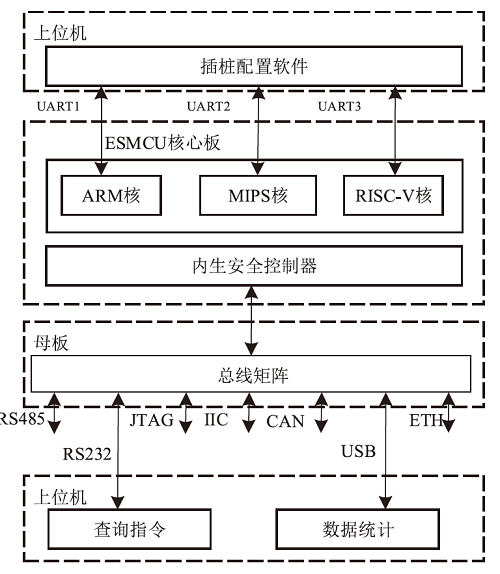
| [1] |
WU Jiangxing. Introduction to Cyberspace Mimic Defense[M]. Beijing: Science Press, 2017.
|
|
邬江兴. 网络空间拟态防御导论[M]. 北京: 科学出版社, 2017.
|
| [2] |
ZHENG Qiuhua, HU Chengnan, CUI Tingting, et al. A Security Analysis Approach for Dynamic Heterogeneous Redundancy Model Based on Probability Analysis[J]. Acta Electronica Sinica, 2021, 49(8): 1586-1598.
doi: 10.12263/DZXB.20201063
|
|
郑秋华, 胡程楠, 崔婷婷, 等. 一种基于概率分析的DHR模型安全性分析方法[J]. 电子学报, 2021, 49(8):1586-1598.
doi: 10.12263/DZXB.20201063
|
| [3] |
ZHU Weijun, GUO Yuanbo, HUANG Bohu. A Mimic Defense Automaton Model of Dynamic Heterogeneous Redundancy Structures[J]. Acta Electronica Sinica, 2019, 47(10): 2025-2031.
doi: 10.3969/j.issn.0372-2112.2019.10.002
|
|
朱维军, 郭渊博, 黄伯虎. 动态异构冗余结构的拟态防御自动机模型[J]. 电子学报, 2019, 47(10):2025-2031.
doi: 10.3969/j.issn.0372-2112.2019.10.002
|
| [4] |
WANG Wei, YANG Benchao, LI Guangsong, et al. Security Analysis of Heterogeneous Redundant Systems[J]. Computer Science, 2018, 45(9): 183-186.
doi: 10.11896/j.issn.1002-137X.2018.09.030
|
|
王伟, 杨本朝, 李光松, 等. 异构冗余系统的安全性分析[J]. 计算机科学, 2018, 45(9):183-186.
doi: 10.11896/j.issn.1002-137X.2018.09.030
|
| [5] |
MA Hailong, REN Quan, YI Peng. Modeling and Quantitative Evaluation of Cyberspace Mimic Defense[J]. ZTE Communications, 2022, 28(6): 57-62.
|
|
马海龙, 任权, 伊鹏. 网络空间拟态防御建模与量化评估技术研究[J]. 中兴通讯技术, 2022, 28(6):57-62.
|
| [6] |
ZHANG Wenjian. Research on Key Technologies of Endogenous Security for Software-Defined Networks[D]. Zhengzhou: Information Engineering University, 2021.
|
|
张文建. 面向软件定义网络的内生安全关键技术研究[D]. 郑州: 战略支援部队信息工程大学, 2021.
|
| [7] |
LI Lingshu. Research on the Security Architecture and Key Technologies of Mimic SaaS Cloud[D]. Zhengzhou: Information Engineering University, 2021.
|
|
李凌书. 拟态SaaS云安全架构及关键技术研究[D]. 郑州: 战略支援部队信息工程大学, 2021.
|
| [8] |
ZHANG Jiexin, PANG Jianmin, ZHANG Zheng. Quantification Method for Heterogeneity on Web Server with Mimic Construction[J]. Journal of Software, 2020, 31(2): 564-577.
|
|
张杰鑫, 庞建民, 张铮. 拟态构造的Web服务器异构性量化方法[J]. 软件学报, 2020, 31(2):564-577.
|
| [9] |
SONG Ke, LIU Qinrang, WEI Shuai, et al. Endogenous Security Architecture of Ethernet Switch Based on Mimic Defense[J]. Journal on Communications, 2020, 41(5): 18-26.
doi: 10.11959/j.issn.1000-436x.2020098
|
|
宋克, 刘勤让, 魏帅, 等. 基于拟态防御的以太网交换机内生安全体系结构[J]. 通信学报, 2020, 41(5):18-26.
doi: 10.11959/j.issn.1000-436x.2020098
|
| [10] |
JIN Liang, LOU Yangming, SUN Xiaoli, et al. Concept and Vision of Wireless Endogenous Safety and Security[J]. Scientia Sinica Inform, 2023, 53(2): 344-364.
|
| [11] |
JI Xinsheng, HUANG Kaizhi, WU Jiangxing, et al. Endogenous Security for the Space-Integrated-Ground Information Network in 6G[J]. Space-Integrated-Ground Information Networks, 2023, 4(2): 2-12.
doi: 10.11959/j.issn.2096-8930.2023014
|
| [12] |
GUO Wei. Research on Simulation Architecture and Key Technologies of Distributed Storage System[D]. Zhengzhou: Information Engineering University, 2019.
|
|
郭威. 分布式存储系统拟态化架构与关键技术研究[D]. 郑州: 战略支援部队信息工程大学, 2019.
|
| [13] |
ZHANG Ruyun, LI Heyuan, LI Shunbin. Mimic Security Scheduling Algorithm for Industrial Control under Limited Heterogeneous Resource Constraints[J]. Telecommunications Science, 2021, 37(3): 57-65.
doi: 10.11959/j.issn.1000-0801.2021047
|
|
张汝云, 李合元, 李顺斌. 有限异构资源条件下的工业控制拟态调度算法[J]. 电信科学, 2021, 37(3):57-65.
doi: 10.11959/j.issn.1000-0801.2021047
|
| [14] |
YAN Wenjiao, LIU Xingyu, ZHANG Yi, et al. A Method for Arbitration and Scheduling of Mimic Industrial Controllers[J]. Journal of Information Security Research, 2022, 8(6): 534-544.
|
| [15] |
LIN Hongyu. Research on Security Defense Technology of Internet of Things Based on DHR[D]. Nanjing: Southeast University, 2022.
|
|
林泓宇. 基于DHR的物联网安全防御技术研究[D]. 南京: 东南大学, 2022.
|
| [16] |
OUYANG Ling, SONG Ke, LAN Julong. Design and Implementation of Microcontroller Based on Dynamic Heterogeneous Redundancy Architecture[EB/OL]. (2024-04-18)[2024-08-11]. https://link.cnki.net/urlid/11.2087.tn.20240415.190.022.
|
|
欧阳玲, 宋克, 兰巨龙. 基于动态异构冗余架构的微控制器设计与实现[EB/OL]. (2024-04-18)[2024-08-11]. https://link.cnki.net/urlid/11.2087.tn.20240415.190.022.
|
| [17] |
OUYANG Ling, SONE Ke, ZHANG Wenjian, et al. Microcontroller Design Based on Dynamic Heterogeneous Redundancy Architecture[J]. China Communications, 2023, 20(9): 144-159.
doi: 10.23919/JCC.fa.2022-0374.202309
|
| [18] |
OUYANG Ling. Research on Key Technologies of Dynamic Heterogeneous Redundant Microcontrollers[D]. Zhengzhou: Information Engineering University, 2023.
|
|
欧阳玲. 动态异构冗余微控制器关键技术研究[D]. 郑州: 战略支援部队信息工程大学, 2023.
|
| [19] |
HU Hongchao, CHEN Fucai, WANG Zhenpeng. Performance Evaluations on DHR for Cyberspace Mimic Defense[J]. Journal of Cyber Security, 2016, 1(4): 40-51.
|
| [20] |
WEI Shuai, YU Hong, GU Zeyu, et al. Architecture of Mimic Security Processor for Industry Control System[J]. Journal of Cyber Security, 2017, 2(1): 54-73.
|
 ), LAN Julong1, OUYANG Ling2
), LAN Julong1, OUYANG Ling2