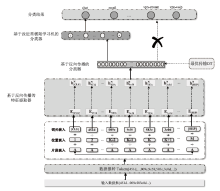
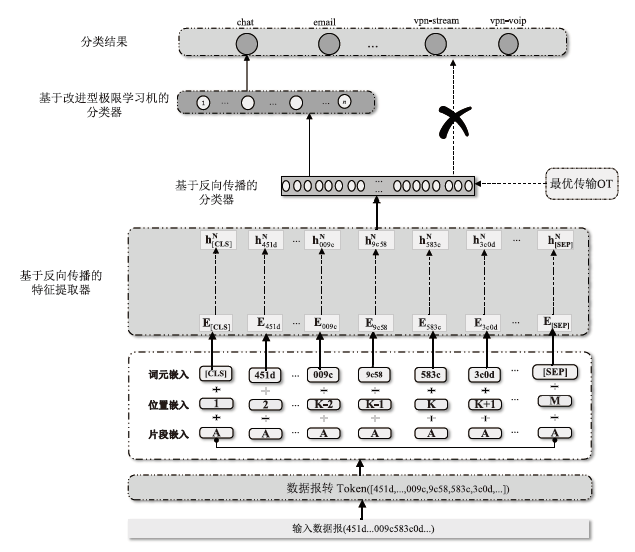
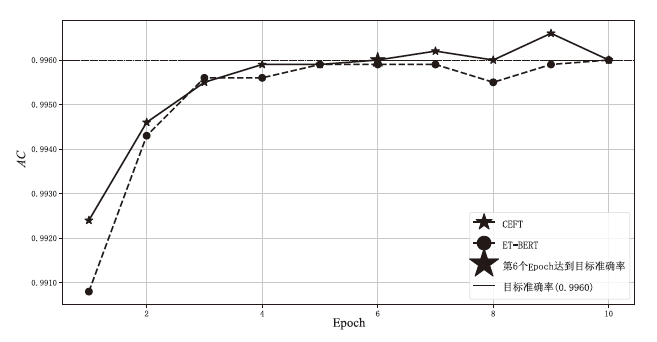
| [1] |
REZAEI S, LIU Xin. Deep Learning for Encrypted Traffic Classification: An Overview[J]. IEEE Communications Magazine, 2019, 57(5): 76-81.
doi: 10.1109/MCOM.2019.1800819
|
| [2] |
DONG Wenqi, YU Jing, LIN Xinjie, et al. Deep Learning and Pre-Training Technology for Encrypted Traffic Classification: A Comprehensive Review[J]. Neurocomputing, 2025, 617: 128444.
|
| [3] |
OTTER D W, MEDINA J R, KALITA J K. A Survey of the Usages of Deep Learning for Natural Language Processing[J]. IEEE Transactions on Neural Networks and Learning Systems, 2021, 32(2): 604-624.
|
| [4] |
MINAEE S, BOYKOV Y, PORIKLI F, et al. Image Segmentation Using Deep Learning: A Survey[J]. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2022, 44(7): 3523-3542.
|
| [5] |
SCHMIDHUBER J. Deep Learning in Neural Networks: An Overview[J]. Neural Networks, 2015, 61: 85-117.
pmid: 25462637
|
| [6] |
CONNEAU A, LAMPLE G. Cross-Lingual Language Model Pretraining[C]// NIPS. Proceedings of the 33rd International Conference on Neural Information Processing Systems. New York: Curran Associates, 2019: 7059-7069.
|
| [7] |
DEVLIN J, CHANG M, LEE K, et al. BERT: Pre-Training of Deep Bidirectional Transformers for Language Understanding[C]// ACL. Proceedings of the 2019 Conference of the North American Chapter of the Association for Computational Linguistics:Human Language Technologies. Minneapolis: ACL, 2019: 4171-4186.
|
| [8] |
WANG Qing, LI Linyu, JIANG Bo, et al. Malicious Domain Detection Based on K-Means and SMOTE[C]// Springer. International Conference on Computational Science. Heidelberg: Springer, 2020: 468-481.
|
| [9] |
KONG He, LI Tong, GE Jingguo, et al. A Novel Method with Transformers for Fine-Grained Encrypted Traffic Classification[C]// IEEE. 2023 IEEE International Conference on High Performance Computing & Communications, Data Science & Systems, Smart City & Dependability in Sensor, Cloud & Big Data Systems & Application (HPCC/DSS/SmartCity/DependSys). New York: IEEE, 2023: 74-81.
|
| [10] |
LIN Xinjie, XIONG Gang, GOU Gaopeng, et al. ET-BERT: A Contextualized Datagram Representation with Pre-Training Transformers for Encrypted Traffic Classification[C]// ACM. Proceedings of the ACM Web Conference 2022. New York: ACM, 2022: 633-642.
|
| [11] |
LOTFOLLAHI M, JAFARI S M, SHIRALI H Z R, et al. Deep Packet: A Novel Approach for Encrypted Traffic Classification Using Deep Learning[J]. Soft Computing, 2020, 24(3): 1999-2012.
|
| [12] |
PEYRÉ G, CUTURI M. Computational Optimal Transport[J]. Foundations and Trends in Machine Learning, 2019, 11(5-6): 355-607.
|
| [13] |
JIRAMANEEPINIT B, WATCHAREERUETAI U. Iterative Extreme Learning Machine[C]// IEEE. 2018 22nd International Computer Science and Engineering Conference (ICSEC). New York: IEEE, 2018: 1-6.
|
| [14] |
DAINOTTI A, PESCAPE A, CLAFFY K C. Issues and Future Directions in Traffic Classification[J]. IEEE Network, 2012, 26(1): 35-40.
|
| [15] |
SHERRY J, LAN Chang, POPA R A, et al. BlindBox: Deep Packet Inspection over Encrypted Traffic[C]// ACM. Proceedings of the 2015 ACM Conference on Special Interest Group on Data Communication. New York: ACM, 2015: 213-226.
|
| [16] |
VAN EDE T, BORTOLAMEOTTI R, CONTINELLA A, et al. FlowPrint: Semi-Supervised Mobile-App Fingerprinting on Encrypted Network Traffic[C]// ACM. Proceedings 2020 Network and Distributed System Security Symposium. New York: ACM, 2020: 1-12.
|
| [17] |
TAYLOR V F, SPOLAOR R, CONTI M, et al. Robust Smartphone App Identification via Encrypted Network Traffic Analysis[J]. IEEE Transactions on Information Forensics and Security, 2018, 13(1): 63-78.
|
| [18] |
AL-NAAMI K, CHANDRA S, MUSTAFA A, et al. Adaptive Encrypted Traffic Fingerprinting with Bi-Directional Dependence[C]// ACM. Proceedings of the 32nd Annual Conference on Computer Security Applications. New York: ACM, 2016: 177-188.
|
| [19] |
ZENG Yi, GU Huaxi, WEI Wenting, et al. Deep-Full-Range: A Deep Learning Based Network Encrypted Traffic Classification and Intrusion Detection Framework[J]. IEEE Access, 2019, 7: 45182-45190.
|
| [20] |
CUTURI M. Sinkhorn Distances: Lightspeed Computation of Optimal Transportation Distances[EB/OL]. [2024-11-01]. https://arxiv.org/abs/1306.0895v1.
|
| [21] |
KANG Bingyi, XIE Saining, ROHRBACH M, et al. Decoupling Representation and Classifier for Long-Tailed Recognition[C]// ICLR. 8th International Conference on Learning Representations (ICLR 2020). Washington: ICLR, 2020: 1-16.
|
| [22] |
HAYES J, DANEZIS G. k-Fingerprinting: A Robust Scalable Website Fingerprinting Technique[C]// USENIX. 25th USENIX Security Symposium (USENIX Security 16). Berkeley: USENIX, 2016: 1187-1203.
|
| [23] |
SIRINAM P, IMANI M, JUAREZ M, et al. Deep Fingerprinting: Undermining Website Fingerprinting Defenses with Deep Learning[C]// ACM. Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2018: 1928-1943.
|
| [24] |
LIU Chang, HE Longtao, XIONG Gang, et al. FS-Net: A Flow Sequence Network for Encrypted Traffic Classification[C]// IEEE. 2019 IEEE Conference on Computer Communications (INFOCOM 2019). New York: IEEE, 2019: 1171-1179.
|
| [25] |
HE Hongye, YANG Zhiguo, CHEN Xiangning. PERT: Payload Encoding Representation from Transformer for Encrypted Traffic Classification[C]// IEEE. 2020 ITU Kaleidoscope:Industry-Driven Digital Transformation (ITU K). New York: IEEE, 2020: 1-8.
|
| [26] |
LIN Xinjie, HE Longtao, GOU Gaopeng, et al. CETP: A Novel Semi-Supervised Framework Based on Contrastive Pre-Training for Imbalanced Encrypted Traffic Classification[J]. Computers & Security, 2024, 143: 103892.
|
 )
)