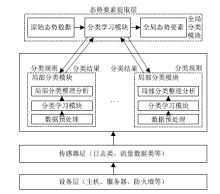
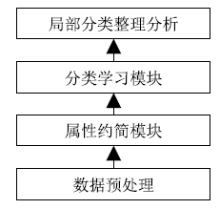
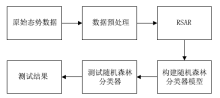
| [1] |
GONG Jian, ZANG Xiaodong, SU Qi, et al.Survey of Network Security Situation Awareness[J]. Journal of Software, 2017, 28(4): 1010-1026.
|
|
龚俭,臧小东,苏琪,等.网络安全态势感知综述[J].软件学报,2017,28(4):1010-1026.
|
| [2] |
BASS T, GRUBER D.A Glimpse into the Future of ID[J]. USENIX & SAGE, 1999, 24(5): 40-45.
|
| [3] |
YURCIK W.Visualizing NetFlows for Security at Line Speed: the SIFT Tool Suite[C]//USENIX. Conference on Systems Administration, December 4-9, 2005, San Diego. Berkeley: USENIX, 2005: 169-176.
|
| [4] |
LAU S.The Spinning Cube of Potential Doom[J]. Communications of the ACM, 2004, 47(6): 25-26.
|
| [5] |
TIM B.Intrusion Detection Systems and Multisensory Data Fusion[J]. Communications of the ACM, 2000, 43(4): 136-147.
|
| [6] |
SRIHARI R K, WU Xin.Mining Concept Associations for Knowledge Discovery Through Concept Chain Queries[EB/OL]. , 2018-3-18.
|
| [7] |
LI Dongyin.The Research on Situation Element Extraction of Network Security Based on Logistic Regression[D]. Fuzhou: Fuzhou University, 2014.
|
|
李冬银. 基于Logistic回归的网络安全态势要素获取研究[D].福州:福州大学,2014.
|
| [8] |
WANG Huiqiang, LIANG Ying, YE Haizhi.An Extraction Method of Situational Factors for Network Security Situational Awareness[C]//ACM. 2008 International Conference on Internet Computing in Science and Engineering, January 28-29, 2008, Harbin, China. New York: ACM, 2008: 317-320.
|
| [9] |
SI Cheng, ZHANG Hongqi, WANG Yongwei, et al.Research on Network Security Situational Elements Knowledge Base Model Based on Ontology[J]. Computer Science, 2015, 42(5): 173-177.
|
|
司成,张红旗,汪永伟,等.基于本体的网络安全态势要素知识库模型研究[J].计算机科学,2015,42(5):173-177.
|
| [10] |
LIU Xiaowu, WANG Huiqiang, Lü Hongwu, et al.Fusion-Based Cognitive Awareness-control Model for Network Security Situation[J]. Journal of Software, 2016, 27(8): 2099-2114.
|
|
刘效武,王慧强,吕宏武,等.网络安全态势认知融合感控模型[J].软件学报,2016,27(8):2099-2114.
|
| [11] |
LIANG Ying, WANG Huiqiang, LAI Jibao.A Method of Network Security Situation Awareness Based on Rough Set Theory[J].Computer Science, 2007(8): 95-97, 147.
|
|
梁颖,王慧强,赖积保.一种基于粗糙集理论的网络安全态势感知方法[J].计算机科学,2007(8):95-97,147.
|
| [12] |
GUO Jian.Studythe Technology of Extraction Situational Factor for Network Security Situational Awareness[D]. Shenyang: Northeastern University, 2011.
|
|
郭剑. 网络安全态势感知中态势要素获取技术的研究[D].沈阳:东北大学,2011.
|
| [13] |
LAI Jibao, WANG Ying, Wang Huiqiang, et al.Research on Network Security Situation Awareness System Architecture Based on Multi-source Heterogeneous Sensors[J]. ComputerScience, 2011, 38(3): 144-149, 158.
|
|
赖积保,王颖,王慧强,等.基于多源异构传感器的网络安全态势感知系统结构研究[J].计算机科学,2011,38(3):144-149,158.
|
| [14] |
LIN Weining, CHEN Mingzhi, ZHAN Yunqing, et al.Research on an Intrusion Detection Algorithm Based on PCA and Random-forest Classification[J]. Netinfo Security, 2017, 17(11): 50-54.
|
|
林伟宁,陈明志,詹云清,等.一种基于PCA和随机森林分类的入侵检测算法研究[J].信息网络安全,2017,17(11):50-54.
|
| [15] |
LI Hong.Approach to Network Security Situational Element Extraction Based on Rough Set[D]. Shijiazhuang: Hebei Normal University, 2017.
|
|
李红. 基于粗糙集的网络安全态势要素提取研究[D].石家庄:河北师范大学,2017.
|
| [16] |
KWOK SW, CARTER C. Multiple Decision Trees[EB/OL]. 2363, 2018-1-31.
|
| [17] |
HO T K.The Random Subspace Method for Constructing Decision Forests[J]. IEEE Transactions on Patternanalysis and Machine Intelligence, 1998, 20(8): 832-844.
|
| [18] |
QUINLAN J R.Induction of Decision Trees[J]. Machinelearning, 1986, 1(1): 81-106.
|
| [19] |
QUINLAN J R.C4.5: Programs for Machine Learning[M]. New York: Elsevier, 2014.
|
| [20] |
BREIMAN L, FRIEDMAN J, STONE C J, et al.Classification and Regression Trees[M]. Boca Raton: CRC press, 1984.
|
| [21] |
QI Ben, WANG Mengdi.A Method Using Information Gain and Naive Bayes to Extract Network Situation Information[J]. Netinfo Security, 2017, 17(9): 54-57.
|
|
戚犇,王梦迪.基于信息增益的贝叶斯态势要素提取[J].信息网络安全,2017,17(9):54-57.
|
 ), Le YANG1
), Le YANG1