| [1] |
卿斯汉,曾山松,杜超. Windows安全基线研究[J]. 信息网络安全,2015(3):6-13.
|
| [2] |
MILLER M, BURRELL T, HOWARD M. Mitigating Software Vulnerabilities[EB/OL]. .
|
| [3] |
LI Lixin, JUST J E, SEKAR R.Address-space Randomization for Windows Systems[C]//IEEE.Computer Security Applications Conference, 2006, December 11 - 15, 2006. Miami Beach, FL, USA.NJ:IEEE,2006: 329-338.
|
| [4] |
SHACHAM H, PAGE M, PFAFF B, et al.On the Effectiveness of Address-Space Randomization[C]//ACM.ACM Conference on Computer and Communications Security, 2004, October 25 - 29, 2004. Washington DC, USA .New York:ACM,2004: 298-307 .
|
| [5] |
卿斯汉,程伟,杜超. Windows操作系统的安全风险可控性分析[J]. 信息网络安全,2015(4):5-12.
|
| [6] |
胡兆阳,谢余强,舒辉. Windows下堆内存管理机制研究[J]. 计算机工程与应用, 2005, 41(17):59-61.
|
| [7] |
HAWKES B. Attacting Vista Heap [EB/OL]. .
|
| [8] |
VALASEK C. Understading the Low Fragmentation Heap [EB/OL]. .
|
| [9] |
VALASEK C, MANDT T. Windows 8 Heap Internals [EB/OL]. .
|
| [10] |
WHITEHOUSE O. An Analysis of Address Space Layout Randomization on Windows Vista [EB/OL]. https://www.researchgate.net/publication/228569932_An_analysis_of_address_space_layout_randomization_on_Windows_Vista, 2017 -3-31.
|
| [11] |
徐鑫,张松年,胡建伟 . 基于任意函数地址的ASLR绕过技术研究[J]. 信息网络安全,2016(7):47-52.
|
| [12] |
ALEXANDER S, MARK D. Bypassing Browser Memory Protections[EB/OL]. https://www.mendeley.com/research-papers/bypassing-browser-memory-protections/,2017 -3-31.
|
| [13] |
WAISMAN N. Understanding and Bypassing Windows Heap Protection [EB/OL]. .
|
| [14] |
CHEN Zhang. Smashing The Browser: From Vulnerability Discovery To Exploit [EB/OL]. https://github.com/demi6od/Smashing_The_Browser/blob/master/Smashing%20The%20Browser%20-%20From%20Vulnerability%20Discovery%20To%20Exploit@slides.pdf,2017 -3-31.
|
| [15] |
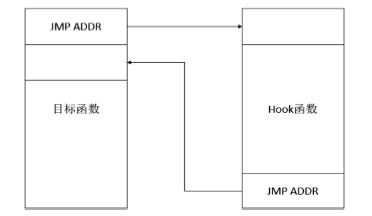
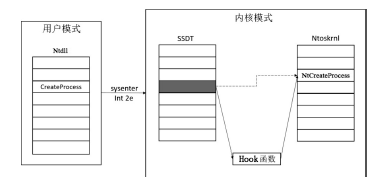
MARIANI B. Inline Hooking in Windows [EB/OL]. https://dl.packetstormsecurity.net/papers/general/inline_hooking_in_windows.pdf,2011 -9-6.
|
 ), Shilin JIA1, Jiawei DU2, Ce QIN1
), Shilin JIA1, Jiawei DU2, Ce QIN1