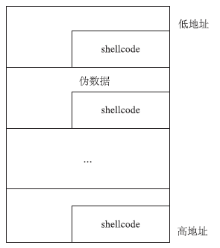
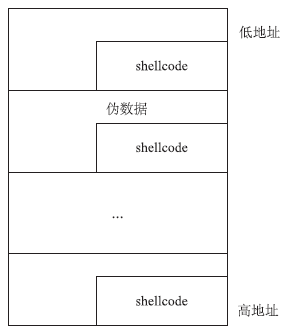
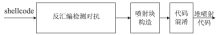
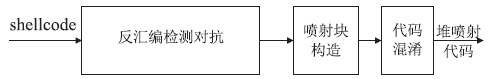
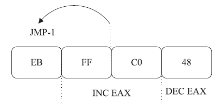
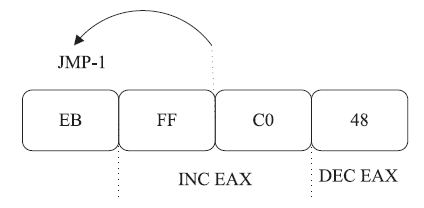
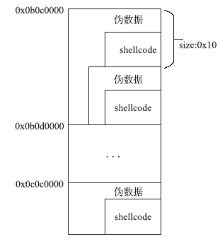
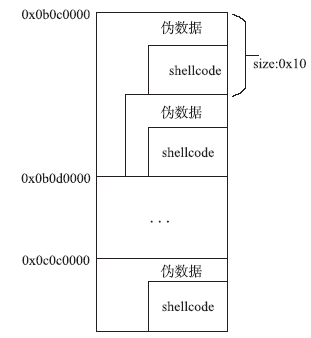
| [1] |
CHOI Y, KIM H, LEE D.Detecting Heap-spraying Code Injection Attacks in Malicious Web Pages Using Runtime Execution[J]. IEICE Transactions on Communications, 2012, 95(5): 1711-1721.
|
| [2] |
ANIBAL S, FEDERICO M. HTML5 Heap Sprays, Pwn All The Things[EB/OL]. , 2012-9-20.
|
| [3] |
PETER V E. DEPS—Precise Heap Spray on Firefox and IE10[EB/OL]. , 2013-2-19.
|
| [4] |
PETER V. A Browser is Only as Strong as Its Weakest Byte-Part 2[EB/OL]. , 2013-12-28.
|
| [5] |
Ga1ois. The Art of Leaks: The Return of Heap Feng Shui[EB/OL]. , 2014-3-14.
|
| [6] |
Exp-sky. IE 11 0day & Windows 8.1 Exploit[EB/OL]. , -9-25.
|
| [7] |
SOTIROV A, DOWD M. Bypassing Browser Memory Protections in Windows Vista[EB/OL]. , -1-22.
|
| [8] |
韦鲲鹏,葛志辉,杨波. PHP Web应用程序上传漏洞的攻防研究[J]. 信息网络安全,2015(10):53-60.
|
| [9] |
魏强,韦韬,王嘉捷. 软件漏洞利用缓解及其对抗技术演化[J]. 清华大学学报:自然科学版,2011,51(10):1274-1280.
|
| [10] |
DANNY W. Windows漏洞利用技术总结[EB/OL]. , 2014-6-3
|
| [11] |
DEREK S. Memory Retrieval Vulnerabilities[EB/OL]. , -12-23.
|
| [12] |
Wikipedia. Heap Spraying[EB/OL]. , 2015-12-22.
|
| [13] |
卿斯汉,程伟,杜超. Windows操作系统的安全风险可控性分析[J]. 信息网络安全,2015(4):5-12.
|
| [14] |
MOSHE B A. Advanced Heap Spraying Techniques[EB/OL]. , 2010-2-7.
|
| [15] |
卿斯汉,曾山松,杜超. Windows安全基线研究[J]. 信息网络安全,2015(3):6-13.
|
| [16] |
NAVARAJ J M S, KASHYAP R C. Method and System for Protecting against Unknown Malicious Activities by Detecting a Heap Spray Attack on an Electronic Device[EB/OL]. , -2-1-22.
|
| [17] |
LIU Lei, WANG Yijun, XUE Zhi. Research on Detection of Vulnerability-Exploiting Technology Heap Spray[EB/OL]. , -1-23.
|
| [18] |
刘磊. Windows下缓冲区溢出漏洞利用技术Heap spray研究[D]. 上海交通大学,2012.
|
| [19] |
刘磊,王轶骏,薛质. 漏洞利用技术Heap Spray检测方法研究[J]. 信息安全与通信保密,2012(6):70-72.
|
| [20] |
宁戈,张涛,伟平,等. 一种非堆喷射的IE浏览器漏洞利用技术研究[J]. 信息网络安全,2014(6):39-42.
|
| [21] |
陈瑞东. 恶意WEB页面自动化分析与识别技术的研究与实现[D]. 电子科技大学,2012.
|
| [22] |
HSU F H, HUANG C H, HSU C H, et al.HSP: A solution against heap sprays[J]. Journal of Systems & Software, 2010, 83(11): 2227-2236.
|
| [23] |
张慧琳,邹维,韩心慧. 网页木马机理与防御技术[J]. 软件学报,2013,24(4):843-858.
|
| [24] |
何鹏程,方勇. 一种基于Web日志和网站参数的入侵检测和风险评估模型的研究[J]. 信息网络安全,2015(1):61-65.
|