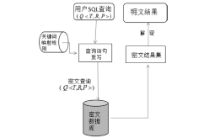
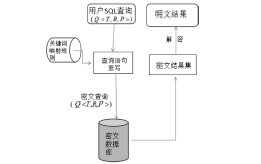
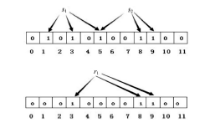
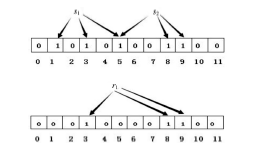
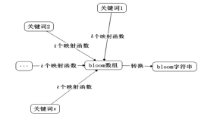
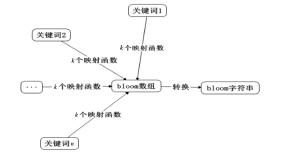
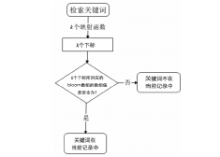
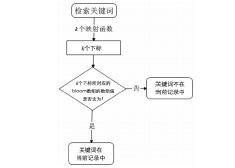
| [1] |
计海萍,徐磊,蔚晓玲,等. 云计算环境下基于身份的分层加密管理系统研究[J]. 信息网络安全,2016(5):30-36.
|
| [2] |
RIVEST R L, ADLEMAN L, Dertouzos M L.On Data Banks and Pri-vacy Homomorphisms[J]. Foundations of Secure Computation,1978:169-179.
|
| [3] |
AGRAWAL R, KIERNAN J,Srikant R.Order Preserving Encryption for Numeric data[C]//ACM.Proceedings of the 2004 ACM SIGMOD International Conference on Management of Data,ACM, June 13-18,2004.Paris,France.NY:ACM,2004:563-574.
|
| [4] |
HACIGUMUS H, IYER B.Executing SQL over Encrypted Data in the Database-Service-Provider Model[C]//ACM. Proceedings of the 2002 ACM SIGMOD International Conference on Management of Data. ACM,June 4-6,2002.Madison,USA.NY:ACM,2002:216-227.
|
| [5] |
SHI Baile,WANG Wei,WANG Zhengfei.Storage and Query over En-crypted Character and Numerical Data in Database[C]//IEEE.The Fifth International Conference on Computer and Information Technology, January 1-1,2005.Shanghai,China.NJ:IEEE,2005:77-81.
|
| [6] |
HACIGUMUS H, IYER B,MEHROTRA S.Efficient Execution of Aggregation Queries over Encrypted Relational Data-bases[M]//Database Systems for Advanced Applications. Berlin Heidelberg:Springer, 2004:125-136.
|
| [7] |
ZHU Hong, CHENG Jing, JIN Renchao,et al.Executing Query over Encrypted Character Strings in Databases[C]//IEEE.2010 Fifth Interna-tional Conference on Frontier of Computer Science and Technol-ogy,IEEE Computer Society, November 1-3,2007.Wuhan,China.NJ:IEEE,2007:90-97.
|
| [8] |
ALHANJOURI M, AYMAN M A D. A New Method of Query over Encrypted Data in Database Using Hash Map[J]. International Journal of Computer Applications, 2012,41(4):46-51.
|
| [9] |
秦志光,包文意,赵洋,等. 云存储中一种模糊关键字搜索加密方案[J]. 信息网络安全,2015(6):7-12.
|
| [10] |
冯登国. 密码学导引[M].北京:科学出版社, 1999.
|
| [11] |
BURTON H B.Space/Time Trade-offs in Hash Coding with Allow-able Errors[J]. Communications of the Acm, 2010,13(7):422-426.
|
| [12] |
刘威, 郭渊博, 黄鹏. 基于Bloom filter的多模式匹配引擎[J]. 电子学报, 2010, 38(5):1095-1099.
|
| [13] |
TPC.TPC-H [EB/OL]..
|
| [14] |
秦志光,包文意,赵洋,等. 云计算里的一种无双线性对的模糊关键字加密方式[J]. 信息网络安全,2015(11):1-6.
|
 ), Chengliang TIAN1,3, Min LI1
), Chengliang TIAN1,3, Min LI1