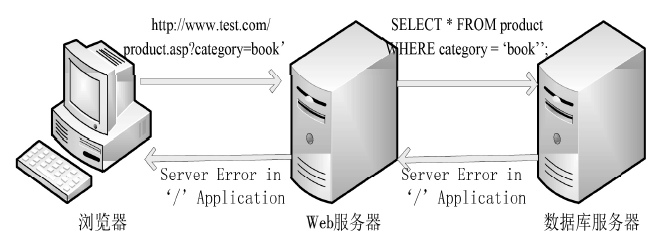
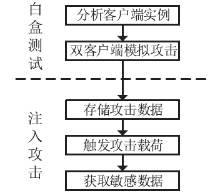
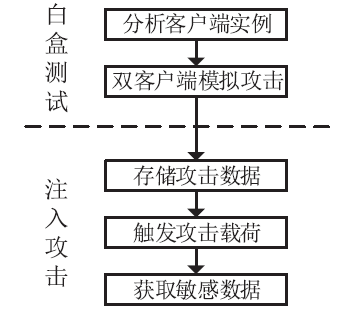
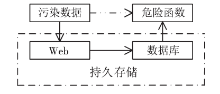
| [1] |
BISHT P, VENKATAKRISHNAN V N. XSS-GUARD.Detection of Intrusions and Malware, and Vulnerability Assessment[M]. Berlin Heidelberg:Springer, 2008.
|
| [2] |
ZELLER W, FELTEN E W.Cross-site Request Forgeries: Exploitation and Prevention[J]. The New York Times, 2008: 1-13.
|
| [3] |
陈林博,江建慧,张丹青. 基于双栈的缓冲区溢出攻击的防御[J]. 同济大学学报:自然科学版,2012,40(3):452-458.
|
| [4] |
OWASP Foundation. OWASP Top Ten Project[EB/OL]. , 2015-5-15.
|
| [5] |
ANLEY C. Advanced SQL Injection in SQL Server Applications[EB/OL]. ,2015-5-15.
|
| [6] |
陈小兵,张汉煜,骆力明,等. SQL 注入攻击及其防范检测技术研究[J]. 计算机工程与应用,2007,43(11): 150-152.
|
| [7] |
HALFOND W G, VIEGAS J, ORSO A.A Classification of SQL-injection Attacks and Countermeasures[C]//IEEE. IEEE International Symposium on Secure Software Engineering, March 13-15, 2006, McLean, Virginia. Piscataway, NJ: IEEE, 2006, (1): 13-15.
|
| [8] |
韩涛. 基于解析树的SQL注入检测方法研究[D]. 哈尔滨:哈尔滨工业大学, 2013.
|
| [9] |
FU X, LU X, PELTSVERGER B, et al.A Static Analysis Framework for Detecting SQL Injection Vulnerabilities[C]// IEEE. 31st Annual International of Computer Software and Applications Conference, 2007(COMPSAC 2007 ). July 24-27 2007, Beijing, China. Piscataway, NJ: IEEE, 2007, (1) : 87-96.
|
| [10] |
田伟,许静,杨巨峰,等. 模型驱动的Web应用SQL注入渗透测试[J]. 高技术通讯,2012,22(11):1161-1168.
|
| [11] |
马小婷,胡国平,李舟军. SQL 注入漏洞检测与防御技术研究[J]. 计算机安全,2010(11):18-24.
|
| [12] |
BANDHAKAVI S, BISHT P, MADHUSUDAN P, et al.CANDID: Preventing SQL Injection Attacks Using Dynamic Candidate Evaluations[C]//ACM. 14th ACM conference on Computer and communications security. Oct. 29-Nov. 2, 2007, Alexandria, VA, USA. New York, NY: ACM, 2007: 12-24.
|
| [13] |
刘华星,杨庚. HTML5——下一代Web开发标准研究[J]. 计算机技术与发展,2011,21(8):54-58.
|
| [14] |
孙茜. Web2.0的含义、特征与应用研究[J]. 现代情报,2006,26(2):69-70.
|
| [15] |
冯谷,高鹏. 新型SQL注入技术研究与分析[J]. 计算机科学, 2012,(S3):415-417.
|
| [16] |
CLARKE J.SQL Injection Attacks and Defense[M]. Amsterdam: Elsevier, 2009.
|
| [17] |
赵瑞颖. 基于时间的SQL 注入分析与防范[J],信息网络安全,2010(1):56-57.
|
| [18] |
张卓. SQL注入攻击技术及防范措施研究[D]. 上海:上海交通大学,2007.
|
| [19] |
WEI K, MUTHUPRASANNA M, KOTHARI S.Preventing SQL Injection Attacks in Stored Procedures[C]// IEEE. Piscataway, Software Engineering Conference, May 20-28, 2006, Shanghai, China. Piscataway, NJ: IEEE, 2006: 191-198.
|
| [20] |
GUPTA N, SAIKIA A.Web Application Firewall[R]. Tech. Report: CS499, Department of Computer Science and Engineering Indian Institute of Technology, Kanpur, 2007.
|
| [21] |
RISRIC I.ModSecurity Handbook[M]. London: Feisty Duck, 2010.
|
| [22] |
Comodo Security Solutions Inc. Comodo Web Application Firewall -Quick Start Guide[EB/OL]. ,2015-5-15.
|
| [23] |
MCCLURE R, KRÜGER I H. SQL DOM: Compile Time Checking Of Dynamic SQL Statements[C]// IEEE.2005.27th International Conference on ICSE. May 15-21, 2005, St. Louis, Missouri, USA. Piscataway, NJ: IEEE, 2005: 88-96.
|
| [24] |
COOK W R, RAI S.Safe Query Objects: Statically Typed Objects as Remotely Executable Queries[C]//IEEE. 27th International Conference on ICSE. May 15-21, 2005, St. Louis, Missouri, USA. Piscataway, NJ :IEEE, 2005: 97-106.
|
| [25] |
BOYD S W, KEROMYTIS A D. SQLrand: Preventing SQL Injection Attacks[J]. Lecture Notes in Computer Science, 2004, (3089): 292--302.
|
| [26] |
STUTTARD D, PINTO M.The Web Application Hacker's Handbook: Finding and Exploiting Security Flaws[M]. New York: John Wiley & Sons, 2011.
|
| [27] |
闫璐. Web 应用二阶 SQL 注入漏洞检测方法研究[D]. 天津:天津大学,2014.
|
| [28] |
DAHSE J, HOLZ T.Static Detection of Second-Order Vulnerabilities in Web Applications[C]//USENIX. The Advanced Computing Systems Association,USENIX Security Symposium, August 20-22, 2014, San Diego, CA, USA. Berkeley,CA: USENIX, 2014: 989-1003.
|
 ), Weiwei ZHANG1, Zichang SUI2, Lixin ZHENG1
), Weiwei ZHANG1, Zichang SUI2, Lixin ZHENG1