Netinfo Security ›› 2016, Vol. 16 ›› Issue (2): 60-65.doi: 10.3969/j.issn.1671-1122.2016.02.010
• Orginal Article • Previous Articles Next Articles
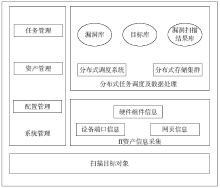
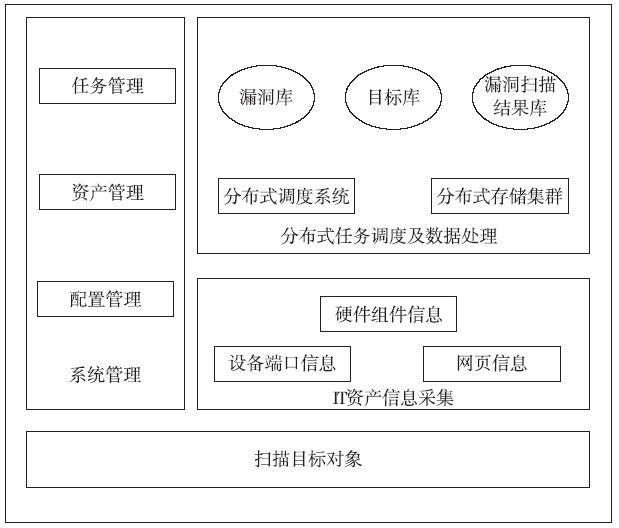
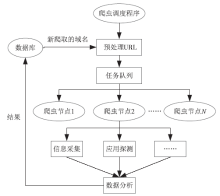
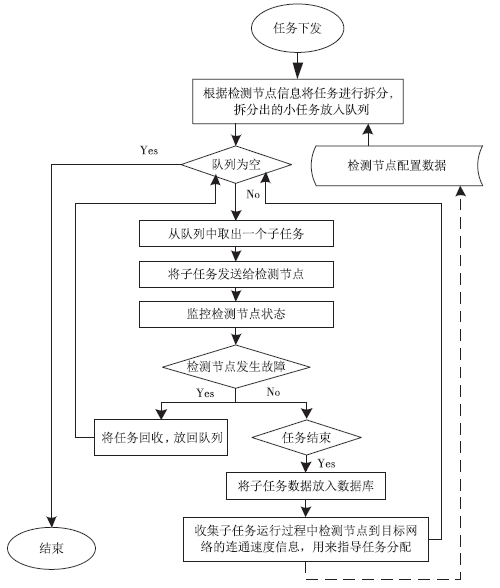
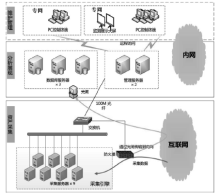
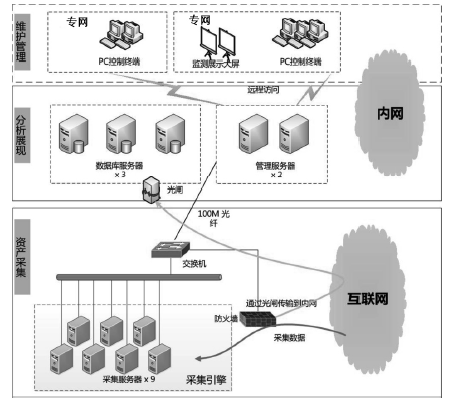
IT Assets Safety Monitoring System Based on Huge Data
Hongkai WANG1, Shengjun ZHENG2, Longhua GUO3( ), Yun LIU4
), Yun LIU4
- 1. Information and Telecommunication Branch of State Grid Zhejiang Electric Power Company, Hangzhou Zhejiang 310007, China
2. Beijng GuoDianTong Network Technology Co.,Ltd, Beijing 100070, China
3. School of Electronic Information and Electric Engineering, Shanghai JiaoTong University, Shanghai 200240, China
4. State Grid JIBEI Electric Power Company, Beijing 100053, China