信息网络安全 ›› 2025, Vol. 25 ›› Issue (4): 578-586.doi: 10.3969/j.issn.1671-1122.2025.04.006
基于DACDiff的分布式电源调度控制系统FDIAs防御方法
- 1.华北电力大学控制与计算机工程学院,北京 102206
2.北京航空航天大学网络空间安全学院,北京 100191
-
收稿日期:2024-11-22出版日期:2025-04-10发布日期:2025-04-25 -
通讯作者:李元诚ncepua@163.com -
作者简介:李元诚(1970—),男,山东,教授,博士,CCF会员,主要研究方向为电力信息安全与隐私保护、人工智能及安全|孙鹤洋(1999—),女,陕西,硕士研究生,主要研究方向为电力信息安全|张桐(2001—),女,山西,硕士研究生,主要研究方向为电力信息安全|张贺方(2000—),男,河南,硕士研究生,主要研究方向为电力信息安全|杨立群(1990—),男,河北,副教授,博士,CCF会员,主要研究方向为网络安全、工业互联网和工控安全 -
基金资助:国家自然科学基金(62302025);国家自然科学基金(U2333205);国家电网有限公司总部科技项目(5108-202325046A-1-1-ZN)
DACDiff-Based Defense against FDIAs in Distributed Generation Dispatch and Control System
LI Yuancheng1( ), SUN Heyang1, ZHANG Tong1, ZHANG Hefang1, YANG Liqun2
), SUN Heyang1, ZHANG Tong1, ZHANG Hefang1, YANG Liqun2
- 1. School of Control and Computer Engineering, North China Electric Power University, Beijing 102206, China
2. School of Cyber Science and Technology, Beihang University, Beijing 100191, China
-
Received:2024-11-22Online:2025-04-10Published:2025-04-25
摘要:
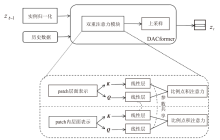
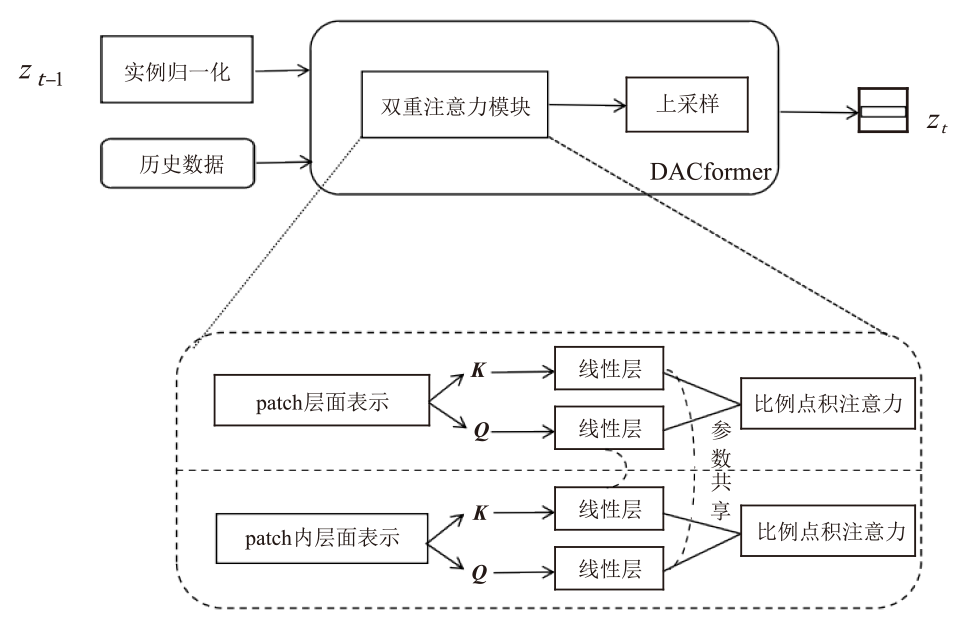
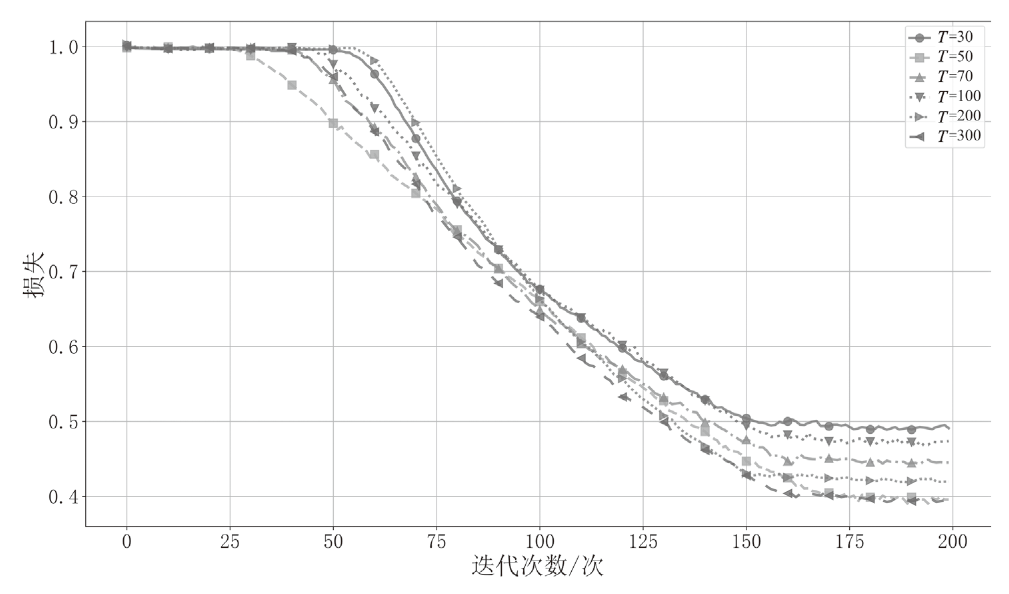
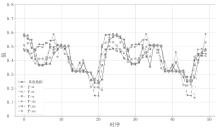
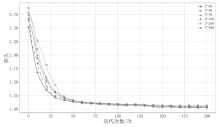
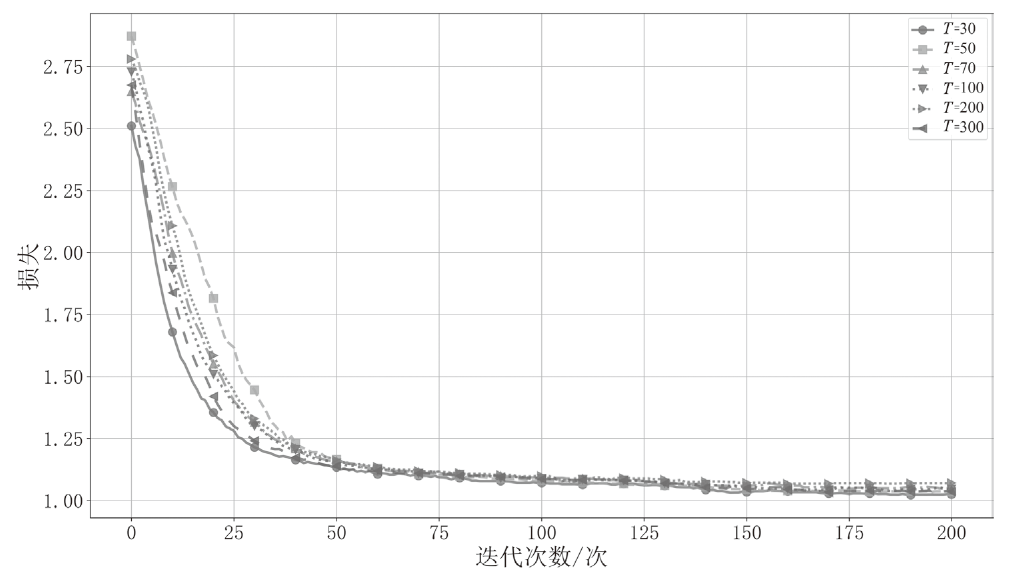
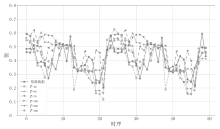
随着可再生能源的发展,分布式电源的应用规模持续扩大,其在高效能源利用和绿色环保方面的优势得到了广泛认可。然而,由于系统的分散性、复杂性和不确定性,使分布式电源调控更易受到虚假数据注入攻击(FDIAs)的安全威胁。FDIAs篡改实时量测数据干扰状态估计和调度决策,可能导致电力系统的不稳定、运行失误,甚至引发严重的电力事故。为确保新型电力系统的安全可靠运行,文章提出一种针对分布式电源调控FDIAs的DACDiff防御方法,该模型基于改进的条件扩散模型,采用DACformer作为去噪网络,采用双重注意力机制捕捉时间序列中的依赖性,通过上采样和多尺度设计更好保留数据特征,用高度逼真的生成数据替换受攻击影响的数据,以保证状态估计的连续性和调控指令的正确性。在电力数据集上的仿真实验结果表明,DACDiff模型在数据生成质量和防御能力方面表现优异,能够有效恢复受到FDIAs影响的分布式电源调控系统,提供了更优的安全性与稳定性。
中图分类号:
引用本文
李元诚, 孙鹤洋, 张桐, 张贺方, 杨立群. 基于DACDiff的分布式电源调度控制系统FDIAs防御方法[J]. 信息网络安全, 2025, 25(4): 578-586.
LI Yuancheng, SUN Heyang, ZHANG Tong, ZHANG Hefang, YANG Liqun. DACDiff-Based Defense against FDIAs in Distributed Generation Dispatch and Control System[J]. Netinfo Security, 2025, 25(4): 578-586.
| [1] | LI Zheng, LI Weiqi, ZHANG Zhongwei, et al. Development Strategy of Flexible Resources in China’s Power System under the Carbon Peaking and Carbon Neutrality Goals[J]. Strategic Study of CAE, 2024, 26(4): 108-120. |
|
李政, 李伟起, 张忠伟, 等. “双碳”目标下我国电力系统灵活性资源发展策略研究[J]. 中国工程科学, 2024, 26(4): 108-120.
doi: 10.15302/J-SSCAE-2024.04.018 |
|
| [2] | LI Yuancheng, LUO Hao, WANG Qingle, et al. An Advanced Persistent Threat Model of New Power System Based on ATT&CK[J]. Netinfo Security, 2023, 23(2): 26-34. |
| 李元诚, 罗昊, 王庆乐, 等. 一种基于ATT&CK的新型电力系统APT攻击建模[J]. 信息网络安全, 2023, 23(2): 26-34. | |
| [3] | YANG Yuze, LIU Wenxia, LI Chengze, et al. Review of FDIA Detection Methods for Electric Power SCADA System[J]. Proceedings of the CSEE, 2023, 43(22): 8602-8621. |
| 杨玉泽, 刘文霞, 李承泽, 等. 面向电力SCADA系统的FDIA检测方法综述[J]. 中国电机工程学报, 2023, 43(22): 8602-8621. | |
| [4] | LIAN Zhi, SHI Peng, CHEN Mou. A Survey on Cyber-Attacks for Cyber-Physical Systems: Modeling, Defense, and Design[J]. IEEE Internet of Things Journal, 2025, 12(2): 1471-1483. |
| [5] | HE Quanpeng, WANG Qi, WU Zhong. A Moving Target Defense Strategy against FDIA Based on Flexible Switching of Spare Lines[C]// IEEE. 2022 IEEE/IAS Industrial and Commercial Power System Asia (I&CPS Asia). New York: IEEE, 2022: 1082-1087. |
| [6] | ZHANG Zhenyong, TIAN Youliang, DENG Ruilong, et al. A Double-Benefit Moving Target Defense against Cyber-Physical Attacks in Smart Grid[J]. IEEE Internet of Things Journal, 2022, 9(18): 17912-17925. |
| [7] | ZHANG Meng, FAN Xuzhen, LU Rongxing, et al. Extended Moving Target Defense for AC State Estimation in Smart Grids[J]. IEEE Transactions on Smart Grid, 2023, 14(3): 2313-2325. |
| [8] | BI Jichao, HE Shibo, LUO Fengji, et al. Differential Game Approach for Modelling and Defense of False Data Injection Attacks Targeting Energy Metering Systems[C]// IEEE. 2022 IEEE International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom). New York: IEEE, 2022: 97-104. |
| [9] | BI Jichao, LUO Fengji, HE Shibo, et al. False Data Injection- and Propagation-Aware Game Theoretical Approach for Microgrids[J]. IEEE Transactions on Smart Grid, 2022, 13(5): 3342-3353. |
| [10] | LI Hu, PAN Huan. A Defense Strategy against False Data Injection Attack in Smart Grid Based on Multi-Stage Game[C]// IEEE. 2024 The 9th International Conference on Power and Renewable Energy (ICPRE). New York: IEEE, 2024: 685-691. |
| [11] |
LI Yuancheng, HUANG Rong, MA Longqiang. False Data Injection Attack and Defense Method on Load Frequency Control[J]. IEEE Internet of Things Journal, 2021, 8(4): 2910-2919.
doi: 10.1109/JIOT.2020.3021429 |
| [12] | LIU Zhiying, LI Yuancheng, WANG Qingle, et al. TSCW-GAN Based FDIAs Defense for State-of-Charge Estimation of Battery Energy Storage Systems in Smart Distribution Networks[J]. IEEE Transactions on Industrial Informatics, 2024, 20(4): 5048-5059. |
| [13] | ZHANG Zhixun, HU Jianqiang, LU Jianquan, et al. Detection and Defense Method against False Data Injection Attacks for Distributed Load Frequency Control System in Microgrid[J]. Journal of Modern Power Systems and Clean Energy, 2024, 12(3): 913-924. |
| [14] | ZHENG Pan, WU Zhaoyue, PAOLETTI M, et al. Typical Mineral Abundance Estimation of Chang’e-3 Yutu Rover with Hyperspectral Data Based on Diffusion Autoencoder Unmixing Model[EB/OL]. (2024-07-12)[2024-10-15]. https://ieeexplore.ieee.org/document/10642898. |
| [15] | GUO Lianghu, TAO Tianli, CAI Xinyi, et al. Cas-DiffCom:Cascaded Diffusion Model for Infant Longitudinal Super-Resolution 3D Medical Image Completion[EB/OL]. (2024-02-21)[2024-10-15]. https://arxiv.org/abs/2402.13776. |
| [16] | MENG Yuyu, ZHANG Fengqi, HUO Jiuyuan, et al. Wind Turbine Fault Sample Generation Method Based on Improved Denoising Diffusion Probability Model[J]. Journal of Vibration and Shock, 2025, 44(4): 286-297. |
| 孟昱煜, 张沣琦, 火久元, 等. 基于改进去噪扩散概率模型的风电机组故障样本生成方法[J]. 振动与冲击, 2025, 44(4):286-297. | |
| [17] | HO J, JAIN A, ABBEEL P. Denoising Diffusion Probabilistic Models[EB/OL]. (2020-12-16)[2024-10-15]. https://arxiv.org/abs/2006.11239. |
| [18] | LI Shiyang, JIN Xiaoyong, XUAN Yao, et al. Enhancing the Locality and Breaking the Memory Bottleneck of Transformer on Time Series Forecasting[EB/OL]. (2020-01-03)[2024-10-15]. https://arxiv.org/abs/1907.00235. |
| [19] | SALINAS D, FLUNKERT V, GASTHAUS J, et al. DeepAR: Probabilistic Forecasting with Autoregressive Recurrent Networks[J]. International Journal of Forecasting, 2020, 36(3): 1181-1191. |
| [20] | NIE Yuqi, NGUYEN N H, SINTHONG P, et al. A Time Series is Worth 64 Words: Long-Term Forecasting with Transformers[EB/OL]. (2023-03-05)[2024-10-15]. |
| [21] | LI Pengchao, ZHANG Quantao, HU Yuan. Smart Contract Vulnerability Detection Method Based on Graph Convolutional Network with Dual Attention Mechanism[J]. Netinfo Security, 2024, 24(11): 1624-1631. |
| 李鹏超, 张全涛, 胡源. 基于双注意力机制图神经网络的智能合约漏洞检测方法[J]. 信息网络安全, 2024, 24(11): 1624-1631. |
| [1] | 谢盈, 曾竹, 胡巍, 丁旭阳. 一种虚假数据注入攻击检测与补偿方法[J]. 信息网络安全, 2023, 23(6): 22-33. |
| [2] | 冯光升, 张盈希, 任奕菲, 高素林. 无线传感器网络中虚假数据途中过滤技术研究[J]. 信息网络安全, 2023, 23(5): 22-31. |
| [3] | 周婧怡, 李红娇. 针对PMU测量的虚假数据注入攻击检测方法[J]. 信息网络安全, 2022, 22(5): 75-83. |
| [4] | 张伟, 徐智刚, 陈云芳, 黄海平. 一种基于动态Docker的SDN蜜网设计与实现[J]. 信息网络安全, 2022, 22(4): 40-48. |
| [5] | 王志强;龚小刚;王红凯;夏威. 智能电网信息安全防御实践[J]. , 2013, 13(10): 0-0. |
| [6] | 章翔凌;王欢. 基于白名单技术构建主动防御体系[J]. , 2013, 13(10): 0-0. |
| [7] | 姚晓宇;马辉;廉喆. 基于特征分解的免杀方法研究[J]. , 2012, 12(4): 0-0. |
| [8] | 高静峰. 浅析云查杀与主动防御[J]. , 2011, 11(9): 0-0. |
| [9] | 刘志;钱鲁锋;邵宏韬. 计算机病毒防治技术的发展研究[J]. , 2011, 11(7): 0-0. |
| [10] | 米军. DDOS攻击下基于TTL策略的数据安全方法研究[J]. , 2009, 9(6): 0-0. |
| [11] | 高晓飞;申普兵. 浅析网络安全主动防御技术[J]. , 2008, 8(8): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||