信息网络安全 ›› 2024, Vol. 24 ›› Issue (12): 1911-1921.doi: 10.3969/j.issn.1671-1122.2024.12.009
基于语义融合轨迹生成的k匿名轨迹集补全方法
徐健锋1, 张炜1, 涂敏2,3( ), 魏勍颋1, 赖展晴1, 王倩倩1
), 魏勍颋1, 赖展晴1, 王倩倩1
- 1.南昌大学软件学院,南昌 330031
2.江西警察学院网络安全学院,南昌 330103
3.电子数据管控与取证江西省重点实验室,南昌 330103
-
收稿日期:2024-06-11出版日期:2024-12-10发布日期:2025-01-10 -
通讯作者:涂敏tumin_y@163.com -
作者简介:徐健锋(1973—),男,江西,教授,博士,CCF会员,主要研究方向为人工智能、网络空间安全、软件工程、粒计算理论、粗糙集理论、三支决策|张炜(2001—),男,江西,硕士研究生,主要研究方向为网络安全|涂敏(1967—),女,江西,教授,本科,主要研究方向为网络安全、电子数据取证|魏勍颋(1981—),女,江西,讲师,博士,CCF会员,主要研究方向为智能计算、信息安全、生物信息学|赖展晴(1999—),男,江西,硕士研究生,主要研究方向为网络安全|王倩倩(2004—),女,江西,本科,主要研究方向为网络安全 -
基金资助:国家自然科学基金(62266032);国家自然科学基金(62362050);江西省主要学科学术技术带头人领军人才项目(20225BCI22016);江西省教育厅2022年科学技术研究项目(GJJ2202302)
A k-Anonymity Completion Method Generated Based on Semantic Fusion Trajectories
XU Jianfeng1, ZHANG Wei1, TU Min2,3( ), WEI Qingting1, LAI Zhanqing1, WANG Qianqian1
), WEI Qingting1, LAI Zhanqing1, WANG Qianqian1
- 1. School of Software, Nanchang University, Nanchang 330031, China
2. Jiangxi Police Academy Network Security College, Nanchang 330103, China
3. Key Laboratory of Electronic Data Control and Evidence Collection, Nanchang 330103, China
-
Received:2024-06-11Online:2024-12-10Published:2025-01-10
摘要:
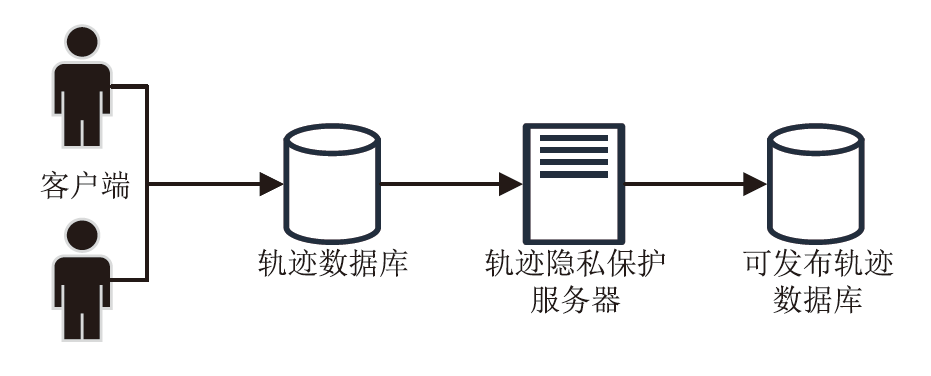
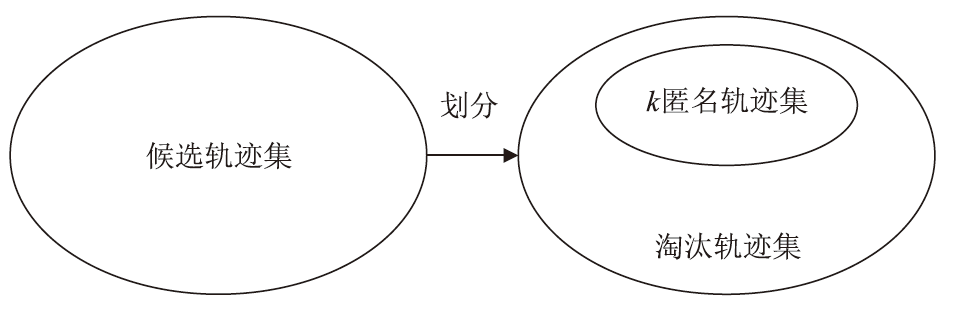
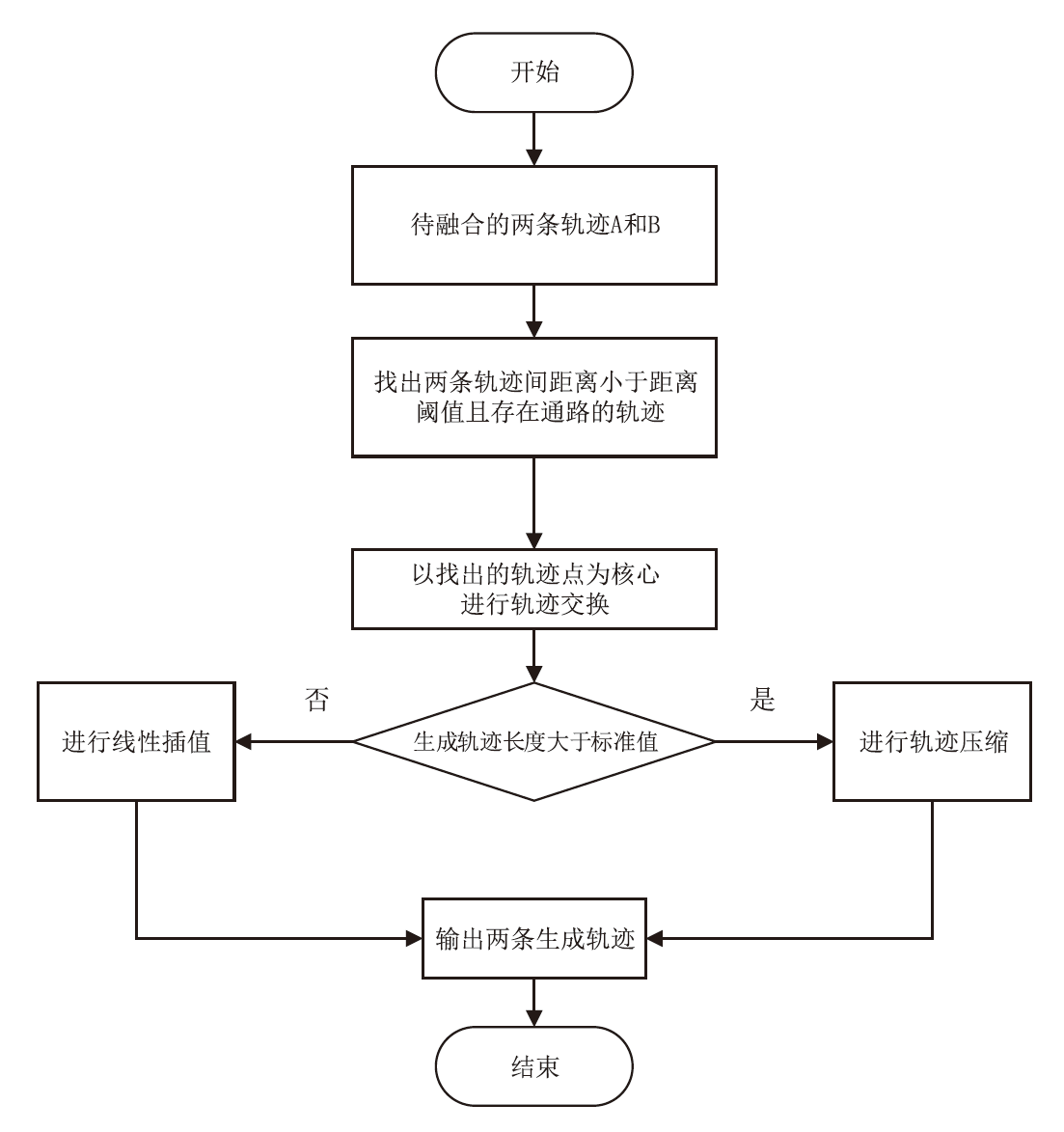
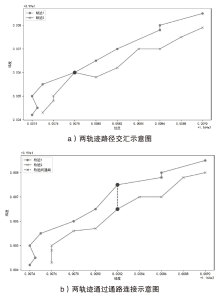
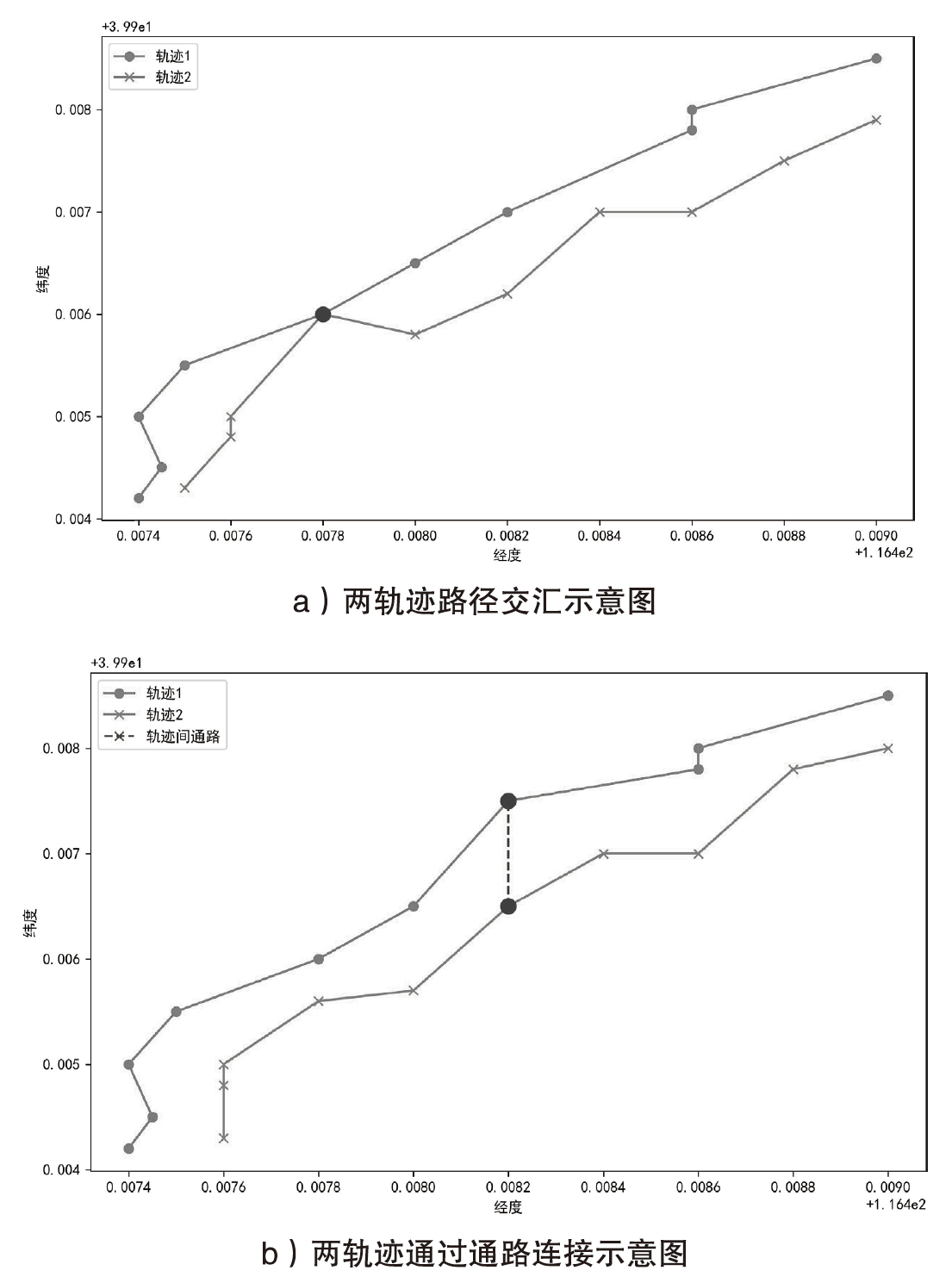
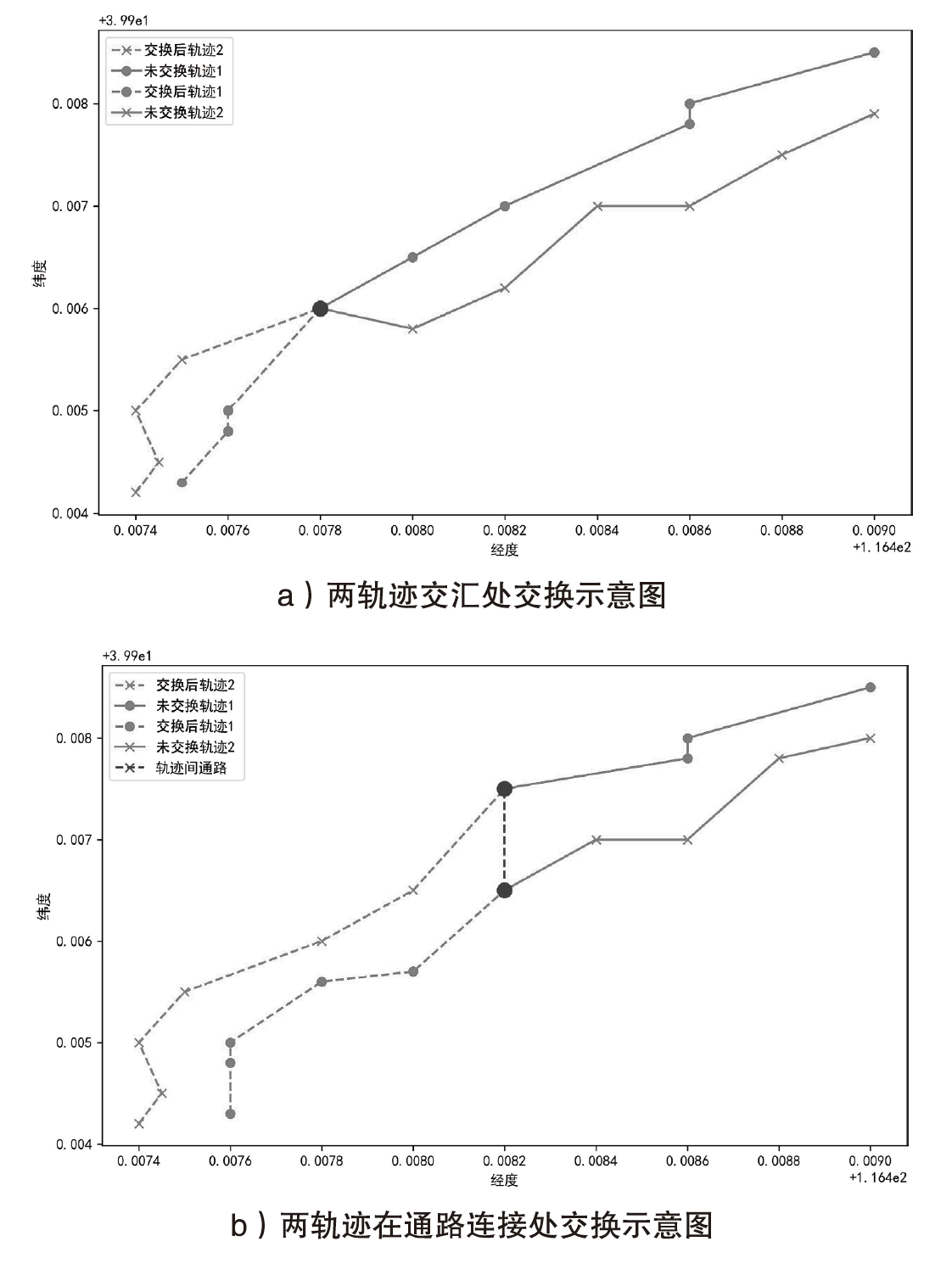
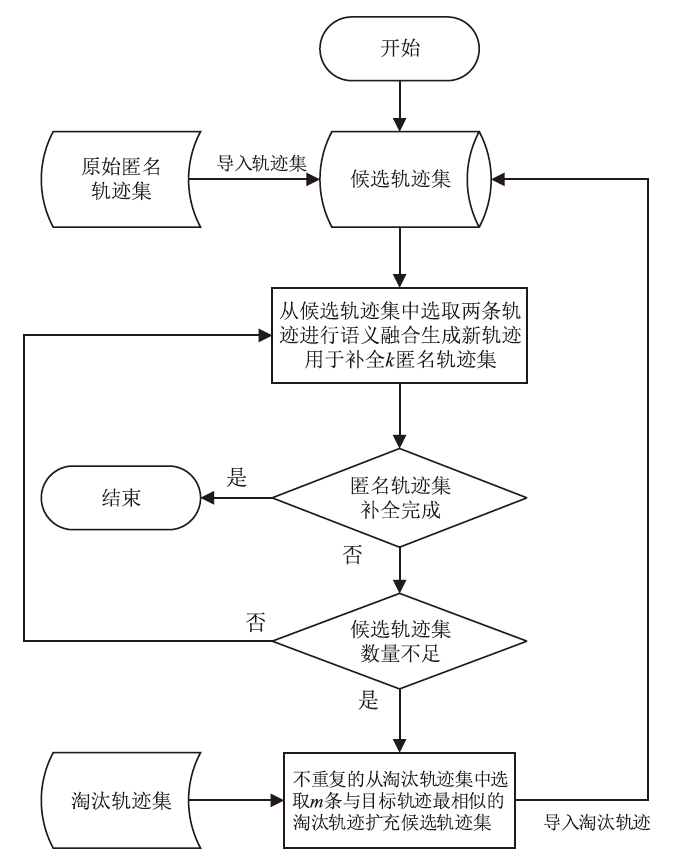
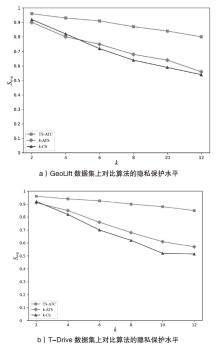
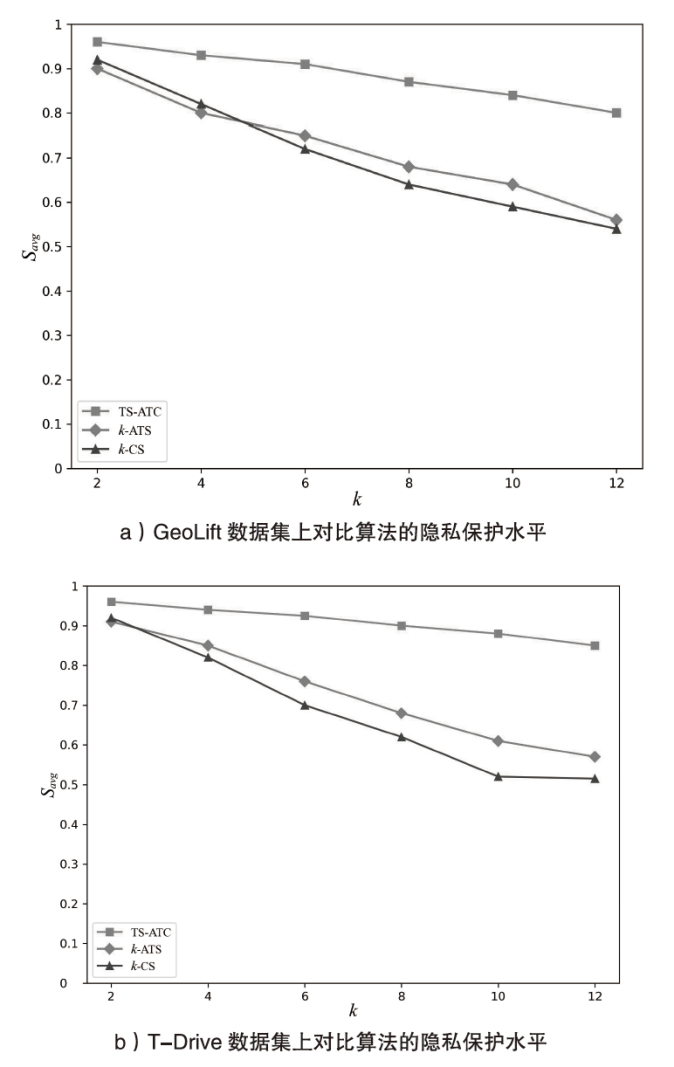
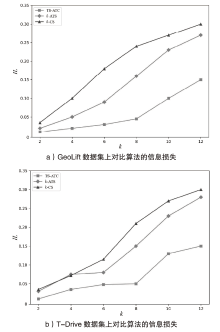
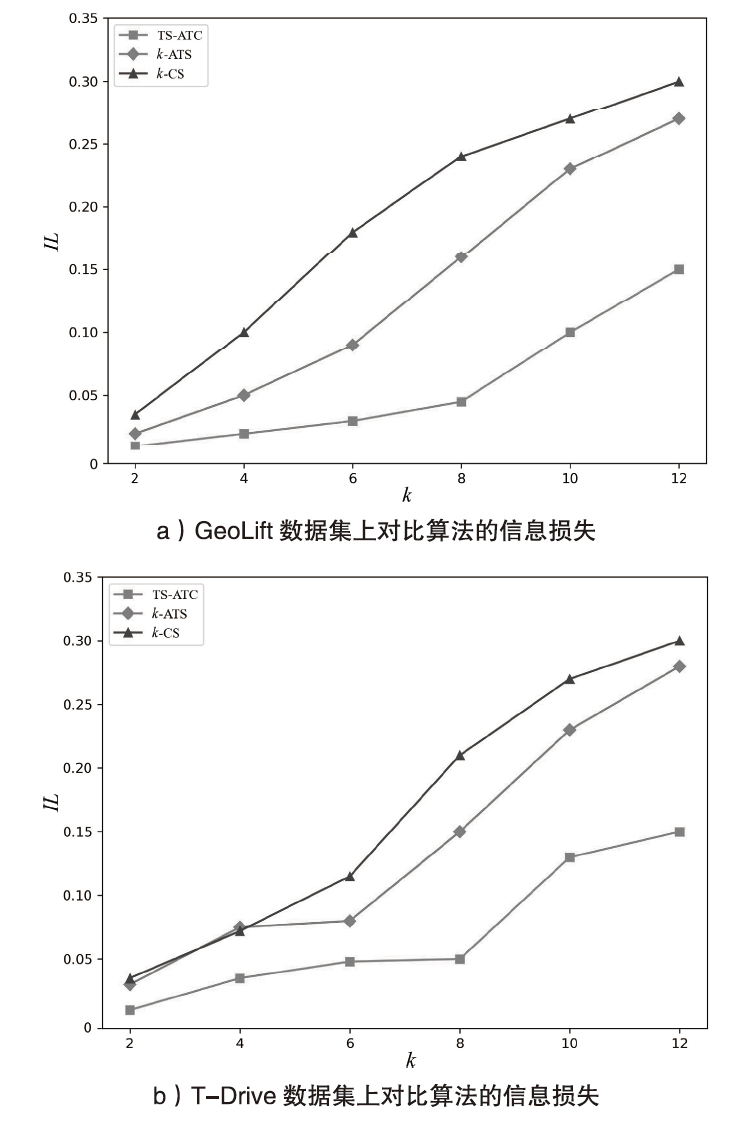
轨迹隐私保护是数据安全和个人隐私保护领域的热点问题之一。文章针对k匿名轨迹计算中可能存在匿名轨迹数量不足的问题,提出一种基于语义融合的匿名轨迹生成方法。该方法选择间距小于指定阈值且存在通路的轨迹对,进行融合和校准后生成两条具有较好语义解释性的虚拟轨迹。基于上述研究成果,文章进一步提出一种基于语义融合轨迹生成的k匿名轨迹集补全方法TS-ATC。该方法首先从匿名轨迹集中选取轨迹作为候选轨迹集;然后,从候选轨迹集中选取符合条件的轨迹对执行基于语义融合的匿名轨迹生成方法,并将符合条件的生成轨迹添加到匿名轨迹集。如果匿名轨迹集数量还达不到要求,再从k匿名轨迹计算淘汰的轨迹中选择合适的轨迹加入候选轨迹集,并进行轨迹融合生成。该步骤也将符合条件的生成轨迹再次添加入匿名轨迹集,直至匿名轨迹集的数量达到要求。文章提出的轨迹生成及匿名轨迹补全方法不但具有较好的可解释性,同时能够有效解决k匿名轨迹计算中可能遇到的轨迹数量不足的问题。
中图分类号:
引用本文
徐健锋, 张炜, 涂敏, 魏勍颋, 赖展晴, 王倩倩. 基于语义融合轨迹生成的k匿名轨迹集补全方法[J]. 信息网络安全, 2024, 24(12): 1911-1921.
XU Jianfeng, ZHANG Wei, TU Min, WEI Qingting, LAI Zhanqing, WANG Qianqian. A k-Anonymity Completion Method Generated Based on Semantic Fusion Trajectories[J]. Netinfo Security, 2024, 24(12): 1911-1921.
| [1] | MA Chunguang, ZHANG Lei, YANG Songtao. A Review of Research on Location Trajectory Privacy Protection[J]. Netinfo Security, 2015, 15(10): 24-31. |
| 马春光, 张磊, 杨松涛. 位置轨迹隐私保护研究综述[J]. 信息网络安全, 2015, 15(10): 24-31 | |
| [2] | ZHU Lei, WU Shutan, LIU Haoyu, et al. Spatio-Temporal Load Migration Potential of Data Centers: Evaluation and Application[J]. Frontiers in Energy Research, 2023, 11: 1-14. |
| [3] | HE Yefeng, QUAN Jiahui, LIU Yan. A Location Privacy Protection Scheme Based on Hybrid Blockchain[J]. Netinfo Security, 2024, 24(2): 229-238. |
| 何业锋, 权家辉, 刘妍. 基于混合区块链的位置隐私保护方案[J]. 信息网络安全, 2024, 24(2): 229-238. | |
| [4] | SONG Shuang, WANG Yizhen, CHAUDHURI K. Pufferfish Privacy Mechanisms for Correlated Data[C]// ACM. The 2017 ACM International Conference on Management of Data. New York: ACM, 2017: 1291-1306. |
| [5] |
LIU Yang, WANG Hongsheng, PENG Mugen, et al. DeePGA: A Privacy-Preserving Data Aggregation Game in Crowdsensing via Deep Reinforcement Learning[J]. IEEE Internet of Things Journal, 2020, 7(5): 4113-4127.
doi: 10.1109/JIOT.2019.2957400 |
| [6] | FREUDIGER J, MANSHAEI M H, HUBAUX J P, et al. Non-Cooperative Location Privacy[J]. IEEE Transactions on Dependable and Secure Computing, 2013, 10(2): 84-98. |
| [7] | SUN Yiping, LU Ronxing, LIN Xiaodong, et al. A Secure and Efficient Revocation Scheme for Anonymous Vehicular Communications[C]// IEEE. 2010 IEEE International Conference on Communications. New York: IEEE, 2010: 1-6. |
| [8] | ZHU Xiaoling, LU Yang, ZHANG Benhong, et al. A Distributed Pseudonym Management Scheme in VANETs[EB/OL]. (2023-04-01)[2024-05-30]. https://api.semanticscholar.org/CorpusID:44902238. |
| [9] | SAZDAR M A, GHORASHI A S, MOGHTADAIEE V, et al. A Low-Complexity Trajectory Privacy Preservation Approach for Indoor Fingerprinting Positioning Systems[J]. Journal of Information Security and Applications, 2020, 53: 1-9. |
| [10] | WANG Jiabo, ZHAO Zemao, LI Lin. A Trajectory Privacy Protection Method Based on Fake Trajectories in Location Services[J]. Netinfo Security, 2014, 14(3): 62-67. |
| 王家波, 赵泽茂, 李林. 位置服务中一种基于假轨迹的轨迹隐私保护方法[J]. 信息网络安全, 2014, 14(3): 62-67. | |
| [11] | MA Tinghuai, SONG Fagen. A Trajectory Privacy Protection Method Based on Random Sampling Differential Privacy[J]. ISPRS International Journal of Geo-Information, 2021, 10(7): 1-22. |
| [12] |
WANG Hao, XU Zhengquan, XIONG Lizhi, et al. CLM: Differential Privacy Protection Method for Trajectory Publishing[J]. Journal on Communications, 2017, 38(6): 85-96.
doi: 10.11959/j.issn.1000-436x.2017119 |
|
王豪, 徐正全, 熊礼治, 等. CLM: 面向轨迹发布的差分隐私保护方法[J]. 通信学报, 2017, 38(6):85-96.
doi: 10.11959/j.issn.1000-436x.2017119 |
|
| [13] | GUO Junqi, YANG Minghui, WAN Boxin. A Practical Privacy-Preserving Publishing Mechanism Based on Personalized k-Anonymity and Temporal Differential Privacy for Wearable IoT Applications[J]. Symmetry, 2021, 13(6): 85-96. |
| [14] | YOU T, PENG W, LEE W. Protecting Moving Trajectories with Dummies[C]// IEEE. 2007 International Conference on Mobile Data Management. New York: IEEE, 2007: 278-282. |
| [15] |
LI Fenghua, ZHANG Cui, NIU Ben, et al. Efficient Scheme for User’s Trajectory Privacy[J]. Journal on Communications, 2015, 36(12): 114-123.
doi: 10.11959/j.issn.1000-436x.2015320 |
|
李凤华, 张翠, 牛犇, 等. 高效的轨迹隐私保护方案[J]. 通信学报, 2015, 36(12):114-123.
doi: 10.11959/j.issn.1000-436x.2015320 |
|
| [16] | SWEENEY L. k-Anonymity: A Model for Protecting Privacy[J]. International Journal of Uncertainty, Fuzziness and Knowledge-Based Systems, 2002, 10(5): 557-570. |
| [17] | GRUTESER M, GRUNWALD D. Anonymous Usage of Location-Based Services through Spatial and Temporal Cloaking[C]// ACM. The 1st International Conference on Mobile Systems, Applications and Services. New York: ACM, 2003: 31-42. |
| [18] | ABUL O, BONCHI F, NANNI M. Anonymization of Moving Objects Databases by Clustering and Perturbation[J]. Information Systems, 2010, 35(8): 884-910. |
| [19] |
XU Huajie, WU Qinghua, HU Xiaoming. Privacy Protection Algorithm Based on Multi-Characteristics of Trajectory[J]. Computer Science, 2019, 46(1): 190-195.
doi: 10.11896/j.issn.1002-137X.2019.01.029 |
|
许华杰, 吴青华, 胡小明. 基于轨迹多特性的隐私保护算法[J]. 计算机科学, 2019, 46(1):190-195.
doi: 10.11896/j.issn.1002-137X.2019.01.029 |
|
| [20] | DOMINGO-FERRER J, TRUJILLO-RASUA R. Microaggregation-and Permutation-Based Anonymization of Movement Data[J]. Information Sciences, 2012, 208: 55-80. |
| [21] | HUO Zheng, MENG Xiaofeng, HU Haibo, et al. You Can Walk Alone: Trajectory Privacy-Preserving through Significant Stays Protection[C]// Springer. Lecture Notes in Computer Science. Heidelberg: Springer, 2012: 351-366. |
| [22] | YANG Jing, ZHANG Bing, ZHANG Jianpei, et al. Personalized Trajectory Privacy Preserving Method Based on Graph Partition[J]. Journal on Communications, 2015, 36(3): 5-15. |
| 杨静, 张冰, 张健沛, 等. 基于图划分的个性化轨迹隐私保护方法[J]. 通信学报, 2015, 36(3):5-15. | |
| [23] | WANG Chao, YANG Jing, ZHANG Jianpei. Research on Trajectory Privacy Preserving Method Based on Trajectory Characteristics and Dynamic Proximity[J]. Acta Automatica Sinica, 2015, 41(2): 330-341. |
| 王超, 杨静, 张健沛. 基于轨迹特征及动态邻近性的轨迹匿名方法研究[J]. 自动化学报, 2015, 41(2):330-341. | |
| [24] | HUO Zheng, WANG Teng. A Trajectory Privacy Protection Technology in Road Network Environment[J]. Computer Applications and Software, 2017, 34(7): 308-313. |
| 霍峥, 王腾. 一种路网环境中的轨迹隐私保护技术[J]. 计算机应用与软件, 2017, 34(7): 308-313. | |
| [25] | ZHOU Kexin, WANG Jian. Trajectory Protection Scheme Based on Fog Computing and k-Anonymity in IoT[C]// IEEE. 2019 20th Asia-Pacific Network Operations and Management Symposium (APNOMS). New York: IEEE, 2019: 1-6. |
| [26] | PAN Xiao, MENG Xiaofeng, XU Jianliang. Distortion-Based Anonymity for Continuous Queries in Location-Based Mobile Services[C]// ACM. The 17th ACM SIGSPATIAL International Conference on Advances in Geographic Information Systems. New York: ACM, 2009: 256-265. |
| [27] | POULIS G, SKIADOPOULOS S, LOUKIDES G, et al. Distance-Based k^m-Anonymization of Trajectory Data[C]// IEEE. 2013 IEEE 14th International Conference on Mobile Data Management. New York: IEEE, 2013: 57-62. |
| [28] | LEI P, PENG W, SU I, et al. Dummy-Based Schemes for Protecting Movement Trajectories[J]. Journal of Information Science and Engineering, 2012, 28(2): 335-350. |
| [29] | DAI Jiazhu, HUA Liang. A Method for the Trajectory Privacy Protection Based on the Segmented Fake Trajectory under Road Networks[C]// IEEE. 2015 2nd International Conference on Information Science and Control Engineering. New York: IEEE, 2015: 13-17. |
| [30] | KONG Xiangjie, CHEN Qiao, HOU Mingliang, et al. Mobility Trajectory Generation: A Survey[J]. Artificial Intelligence Review, 2023, 56: 3057-3098. |
| [31] |
SONG Fagen, MA Tinghuai, TIAN Yuan, et al. A New Method of Privacy Protection: Random k-Anonymous[J]. IEEE Access, 2019, 7: 75434-75445.
doi: 10.1109/ACCESS.2019.2919165 |
| [1] | 温金明, 刘庆, 陈洁, 吴永东. 基于错误学习的全同态加密技术研究现状与挑战[J]. 信息网络安全, 2024, 24(9): 1328-1351. |
| [2] | 林湛航, 向广利, 李祯鹏, 徐子怡. 基于同态加密的前馈神经网络隐私保护方案[J]. 信息网络安全, 2024, 24(9): 1375-1385. |
| [3] | 郭倩, 赵津, 过弋. 基于分层聚类的个性化联邦学习隐私保护框架[J]. 信息网络安全, 2024, 24(8): 1196-1209. |
| [4] | 李增鹏, 王思旸, 王梅. 隐私保护近邻检测研究[J]. 信息网络安全, 2024, 24(6): 817-830. |
| [5] | 傅彦铭, 陆盛林, 陈嘉元, 覃华. 基于深度强化学习和隐私保护的群智感知动态任务分配策略[J]. 信息网络安全, 2024, 24(3): 449-461. |
| [6] | 顾海艳, 柳琪, 马卓, 朱涛, 钱汉伟. 基于可用性的数据噪声添加方法研究[J]. 信息网络安全, 2024, 24(11): 1731-1738. |
| [7] | 宋玉涵, 祝跃飞, 魏福山. 一种基于AdaBoost模型的区块链异常交易检测方案[J]. 信息网络安全, 2024, 24(1): 24-35. |
| [8] | 许可, 李嘉怡, 蒋兴浩, 孙锬锋. 一种基于轮廓稀疏对抗的视频步态隐私保护算法[J]. 信息网络安全, 2024, 24(1): 48-59. |
| [9] | 赖成喆, 赵益宁, 郑东. 基于同态加密的隐私保护与可验证联邦学习方案[J]. 信息网络安全, 2024, 24(1): 93-105. |
| [10] | 俞惠芳, 乔一凡, 孟茹. 面向区块链金融的抗量子属性基门限环签密方案[J]. 信息网络安全, 2023, 23(7): 44-52. |
| [11] | 唐雨, 张驰. 一种基于Intel SGX的信息中心网络隐私保护方案[J]. 信息网络安全, 2023, 23(6): 55-65. |
| [12] | 杜卫东, 李敏, 韩益亮, 王绪安. 基于密文转换的高效通用同态加密框架[J]. 信息网络安全, 2023, 23(4): 51-60. |
| [13] | 尹曙, 陈兴蜀, 朱毅, 曾雪梅. 基于字符空间构造的域名匿名化算法[J]. 信息网络安全, 2023, 23(4): 80-89. |
| [14] | 郭瑞, 魏鑫, 陈丽. 工业物联网环境下可外包的策略隐藏属性基加密方案[J]. 信息网络安全, 2023, 23(3): 1-12. |
| [15] | 李晓华, 王苏杭, 李凯, 徐剑. 一种支持隐私保护的传染病人际传播分析模型[J]. 信息网络安全, 2023, 23(3): 35-44. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||