信息网络安全 ›› 2024, Vol. 24 ›› Issue (12): 1882-1895.doi: 10.3969/j.issn.1671-1122.2024.12.007
基于对抗样本的流量时序特征混淆方法
- 陆军工程大学指挥控制工程学院,南京 210007
-
收稿日期:2024-05-08出版日期:2024-12-10发布日期:2025-01-10 -
通讯作者:屠智鑫tuzhixin@126.com -
作者简介:张国敏(1979—),男,山东,副教授,博士,主要研究方向为软件定义网络、网络安全、网络测量和分布式系统|屠智鑫(1997—),男,江苏,硕士研究生,主要研究方向为网络安全|邢长友(1982—),男,河南,教授,博士,CCF会员,主要研究方向为软件定义网络、网络安全和网络功能虚拟化|王梓澎(2000—),男,辽宁,硕士研究生,主要研究方向为网络安全|张俊峰(1995—),男,山东,硕士研究生,主要研究方向为网络安全 -
基金资助:国家自然科学基金(62172432)
Traffic Obfuscation Method for Temporal Features Based on Adversarial Example
ZHANG Guomin, TU Zhixin( ), XING Changyou, WANG Zipeng, ZHANG Junfeng
), XING Changyou, WANG Zipeng, ZHANG Junfeng
- Institute of Command and Control Engineering, Army Engineering University of PLA, Nanjing 210007, China
-
Received:2024-05-08Online:2024-12-10Published:2025-01-10
摘要:
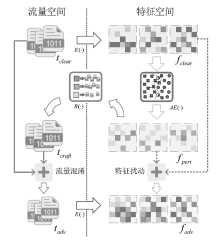
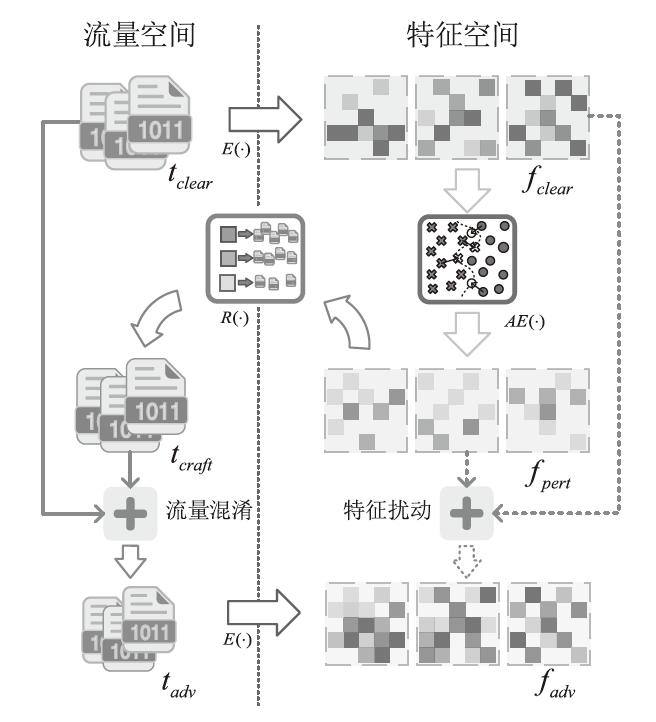
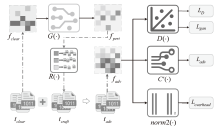
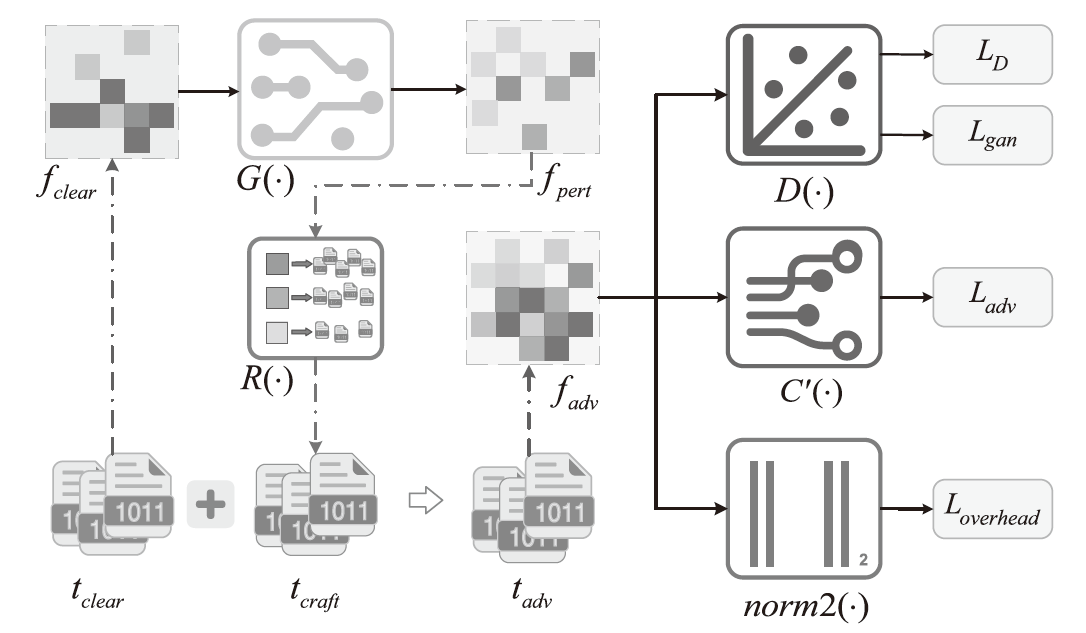
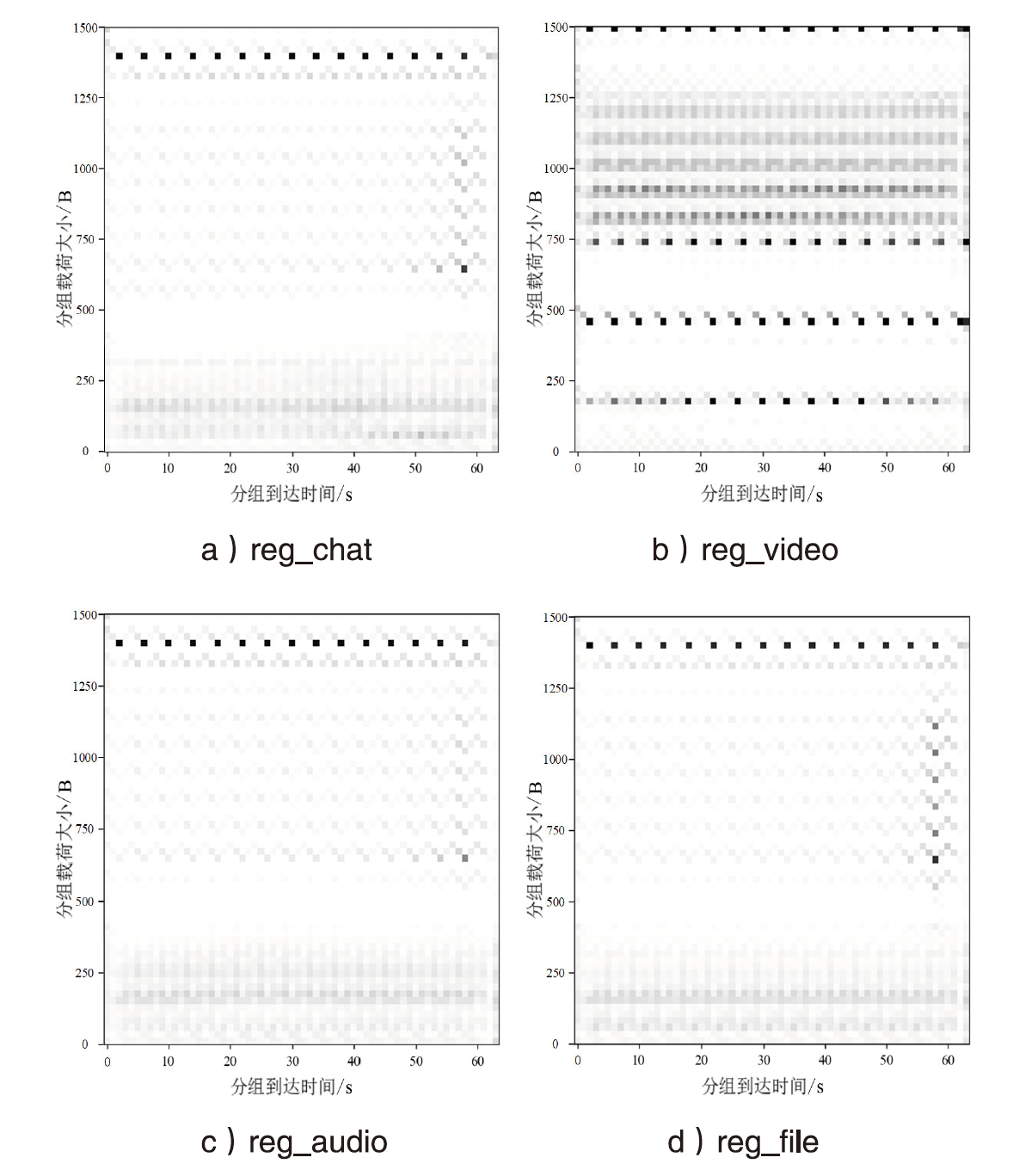
基于深度学习的流量分析技术在提高网络管理效率的同时,也为恶意攻击者提供了新的入侵途径。攻击者可通过分析加密流量的时序特征提取用户的敏感信息,严重威胁个人隐私安全。目前的防御策略主要通过对抗样本误导对手的分类器,但现有策略在现实应用中存在明显局限。一方面,现有策略仅限于特征空间的扰动,无法对真实流量产生影响;另一方面,依赖于对攻击者模型的了解,仅在白盒环境下有效。鉴于针对黑盒环境下混淆真实流量的研究不足,文章提出一种基于对抗样本的流量时序特征混淆方法TAP。该方法无需访问对手分类器,即可针对时序特征生成有效的对抗扰动,其核心在于通过向单向通信流中插入少量分组,在不影响正常通信的前提下有效抵抗基于时序特征的流量分析。实验结果表明,文章所提方法在带宽开销不超过7%的情况下,显著降低了对手流量分类的准确率。
中图分类号:
引用本文
张国敏, 屠智鑫, 邢长友, 王梓澎, 张俊峰. 基于对抗样本的流量时序特征混淆方法[J]. 信息网络安全, 2024, 24(12): 1882-1895.
ZHANG Guomin, TU Zhixin, XING Changyou, WANG Zipeng, ZHANG Junfeng. Traffic Obfuscation Method for Temporal Features Based on Adversarial Example[J]. Netinfo Security, 2024, 24(12): 1882-1895.
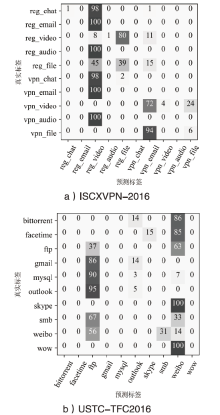
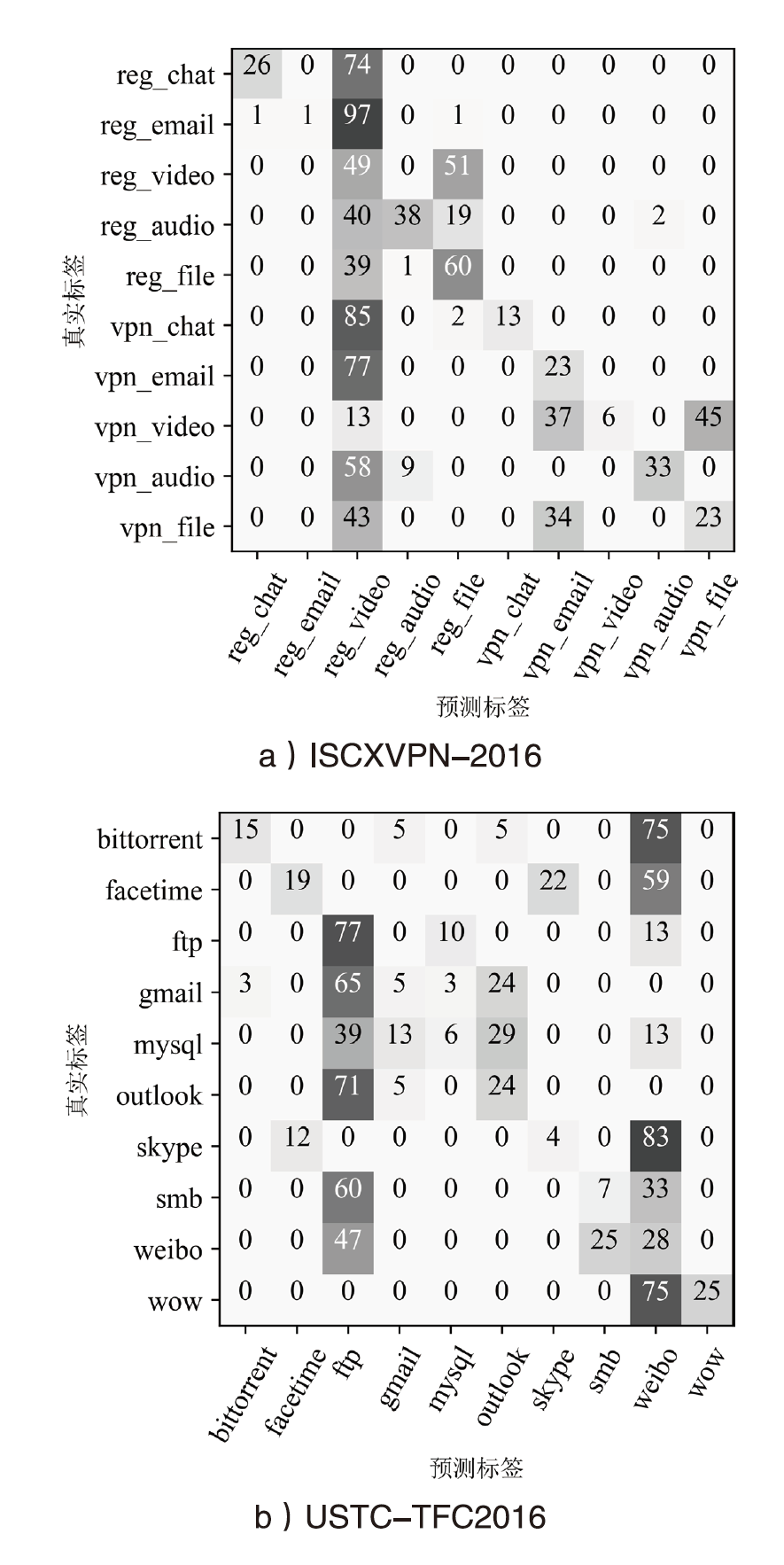
表1
针对代理分类器的混淆效果
| 数据集 | 类别 | 混淆前 | 混淆后 | |||||||
|---|---|---|---|---|---|---|---|---|---|---|
| PRC | REC | F1-Score | ACC | PRC | REC | F1-Score | ACC | OHR | ||
| ISCXVPN- 2016 | reg_chat | 98.1% | 100% | 99.0% | 95.9% | 100% | 1.0% | 2.0% | 6.4% | 5.1% |
| reg_email | 100% | 96.6% | 98.3% | 0 | 0 | 0 | ||||
| reg_video | 100% | 100% | 100% | 1.0% | 8.0% | 2.2% | ||||
| reg_audio | 91.8% | 75.0% | 82.5% | 0 | 0 | 0 | ||||
| reg_file | 98.3% | 97.4% | 97.9% | 36.5% | 39.3% | 37.9% | ||||
| vpn_chat | 96.2% | 97.2% | 96.7% | 0 | 0 | 0 | ||||
| vpn_email | 99.0% | 100% | 99.5% | 0 | 0 | 0 | ||||
| vpn_video | 100% | 100% | 100% | 100% | 4.0% | 7.4% | ||||
| vpn_audio | 76.8% | 92.5% | 83.9% | 0 | 0 | 0 | ||||
| vpn_file | 100% | 100% | 100% | 2.0% | 6.0% | 8.3% | ||||
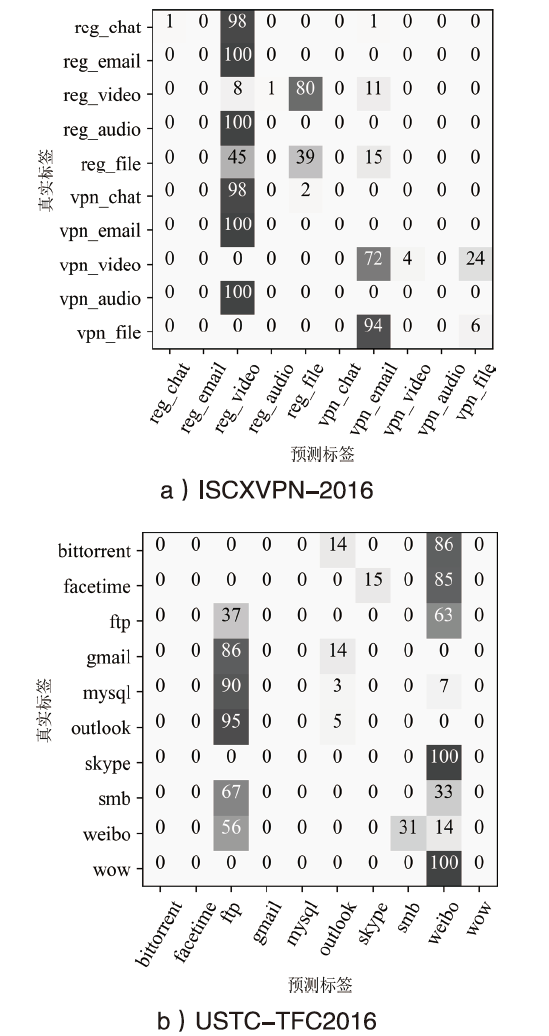
| USTC- TFC2016 | bittorrent | 90.0% | 94.7% | 92.3% | 96.7% | 0 | 0 | 0 | 6.1% | 6.6% |
| facetime | 96.7% | 100% | 98.3% | 0 | 0 | 0 | ||||
| ftp | 100% | 96.9% | 98.4% | 7.3% | 36.7% | 12.2% | ||||
| gmail | 92.1% | 94.6% | 93.3% | 0 | 0 | 0 | ||||
| mysql | 100% | 93.9% | 96.9% | 0 | 0 | 0 | ||||
| outlook | 95.5% | 95.5% | 95.5% | 18.2% | 4.8% | 7.6% | ||||
| skype | 100% | 95.8% | 97.9% | 0 | 0 | 0 | ||||
| smb | 93.8% | 96.8% | 95.2% | 0 | 0 | 0 | ||||
| 100% | 100% | 100% | 4.2% | 13.9% | 6.4% | |||||
| wow | 100% | 100% | 100% | 0 | 0 | 0 | ||||
表2
对Flowpic的防御效果
| 数据集 | 类别 | 混淆前 | 混淆后 | |||||||
|---|---|---|---|---|---|---|---|---|---|---|
| PRC | REC | F1-Score | ACC | PRC | REC | F1-Score | ACC | OHR | ||
| ISCXVPN- 2016 | reg_chat | 98.0% | 100% | 99.0% | 96.7% | 95.2% | 25.6% | 40.4% | 27.9% | 5.1% |
| reg_email | 99.3% | 98.6% | 98.9% | 100% | 1.2% | 2.4% | ||||
| reg_video | 99.4% | 99.4% | 99.4% | 8.1% | 48.9% | 13.9% | ||||
| reg_audio | 92.3% | 76.2% | 83.5% | 81.6% | 38.5% | 52.3% | ||||
| reg_file | 100% | 98.0% | 99.0% | 50.4% | 60.0% | 54.8% | ||||
| vpn_chat | 97.8% | 97.8% | 97.8% | 100% | 13.5% | 23.7% | ||||
| vpn_email | 99.4% | 100% | 99.7% | 22.7% | 22.7% | 22.7% | ||||
| vpn_video | 100% | 100% | 100% | 100% | 5.8% | 11.0% | ||||
| vpn_audio | 81.6% | 94.3% | 87.5% | 93.9% | 33.3% | 49.2% | ||||
| vpn_file | 100% | 100% | 100% | 30.3% | 22.7% | 26.0% | ||||
| USTC- TFC2016 | bittorrent | 86.4% | 95.1% | 90.6% | 96.4% | 75.0% | 14.3% | 24.0% | 21.9% | 6.6% |
| facetime | 100% | 96.3% | 98.1% | 62.5% | 28.5% | 28.6% | ||||
| ftp | 96.9% | 93.9% | 95.3% | 18.9% | 76.7% | 30.4% | ||||
| gmail | 94.8% | 97.3% | 96.1% | 28.6% | 8.1% | 12.6% | ||||
| mysql | 93.9% | 96.9% | 95.4% | 38.5% | 7.8% | 13.0% | ||||
| outlook | 97.7% | 95.4% | 96.5% | 36.7% | 26.2% | 30.6% | ||||
| skype | 96.1% | 100% | 98.0% | 14.3% | 4.2% | 6.5% | ||||
| smb | 96.6% | 90.3% | 93.3% | 18.2% | 6.7% | 9.8% | ||||
| 100% | 100% | 100% | 10.8% | 27.8% | 15.5% | |||||
| wow | 100% | 100% | 100% | 66.7% | 25.0% | 36.4% | ||||
表3
对FS-Net的防御效果
| 数据集 | 类别 | 混淆前 | 混淆后 | |||||||
|---|---|---|---|---|---|---|---|---|---|---|
| PRC | REC | F1-Score | ACC | PRC | REC | F1-Score | ACC | OHR | ||
| ISCXVPN- 2016 | reg_chat | 98.6% | 100% | 99.3% | 96.4% | 93.6% | 37.2% | 53.2% | 36.9% | 5.1% |
| reg_email | 96.9% | 81.6% | 88.6% | 92.6% | 28.7% | 43.9% | ||||
| reg_video | 100% | 100% | 100% | 15.1% | 51.6% | 23.4% | ||||
| reg_audio | 87.5% | 100% | 93.3% | 44.1% | 61.5% | 51.4% | ||||
| reg_file | 100% | 100% | 100% | 27.4% | 52.9% | 36.1% | ||||
| vpn_chat | 97.6% | 96.4% | 97.0% | 41.9% | 29.5% | 34.6% | ||||
| vpn_email | 86.2% | 97.4% | 91.5% | 92.9% | 52.0% | 66.7% | ||||
| vpn_video | 98.7% | 97.5% | 98.1% | 56.1% | 35.9% | 43.8% | ||||
| vpn_audio | 89.4% | 93.3% | 91.3% | 0 | 0 | 0 | ||||
| vpn_file | 100% | 100% | 100% | 29.8% | 15.7% | 20.6% | ||||
| USTC- TFC2016 | bittorrent | 96.9% | 95.0% | 95.9% | 96.8% | 100% | 28.6% | 44.4% | 26.3% | 6.6% |
| facetime | 100% | 100% | 100% | 46.2% | 25.0% | 32.4% | ||||
| ftp | 100% | 100% | 100% | 17.2% | 76.9% | 28.2% | ||||
| gmail | 100% | 90.8% | 95.2% | 6.3% | 6.1% | 6.2% | ||||
| mysql | 92.2% | 94.6% | 93.4% | 36.4% | 11.8% | 17.8% | ||||
| outlook | 100% | 99.1% | 99.6% | 66.7% | 36.4% | 47.1% | ||||
| skype | 94.2% | 93.7% | 93.9% | 0 | 0 | 0 | ||||
| smb | 94.6% | 100% | 97.2% | 100% | 31.3% | 47.6% | ||||
| 92.0% | 100% | 95.8% | 13.0% | 50.0% | 20.6% | |||||
| wow | 99.5% | 94.4% | 96.9% | 12.5% | 13.3% | 12.9% | ||||
表4
不同损失比例下的防御性能和带宽开销
| ISCXVPN-2016 | USTC-TFC2016 | ||||||||
|---|---|---|---|---|---|---|---|---|---|
| DSR: 代理 | DSR: Flowpic | DSR: FS-Net | OHR | DSR: 代理 | DSR: Flowpic | DSR: FS-Net | OHR | ||
| 1 | 1 | 83.26% | 36.69% | 31.43% | 3.77% | 81.85% | 39.49% | 36.27% | 4.26% |
| 5 | 2 | 93.60% | 72.07% | 63.13% | 5.05% | 93.92% | 78.10% | 73.68% | 6.64% |
| 5 | 1 | 93.75% | 81.68% | 75.52% | 18.84% | 95.19% | 85.67% | 82.59% | 22.26% |
| 10 | 1 | 94.63% | 88.07% | 84.82% | 25.36% | 96.20% | 89.21% | 87.74% | 29.78% |
| 20 | 1 | 96.85% | 90.33% | 89.61% | 44.13% | 96.52% | 92.86% | 91.05% | 46.58% |
表5
TAP对比其他防御方案
| 方法 | ISCXVPN-2016 | USTC-TFC2016 | ||||
|---|---|---|---|---|---|---|
| DSR: Flowpic | DSR: FS-Net | OHR | DSR: Flowpic | DSR: FS-Net | OHR | |
| WTF-PAD[ | 36.32% | 35.01% | 57.95% | 35.77% | 38.19% | 54.68% |
| Manipulator[ | 65.83% | 62.75% | 26.10% | 73.13% | 71.81% | 24.41% |
| Prism[ | 87.08% | 85.73% | 19.26% | 82.75% | 86.15% | 20.37% |
| TAP | 72.07% | 63.13% | 5.05% | 78.10% | 73.68% | 6.64% |
| TAP | 88.07% | 84.82% | 25.36% | 89.21% | 87.74% | 29.78% |
| [1] | WANG Chenggang, DANI J, LI Xiang, et al. Adaptive Fingerprinting: Website Fingerprinting over Few Encrypted Traffic[C]// ACM. Proceedings of the Eleventh ACM Conference on Data and Application Security and Privacy. New York: ACM, 2021: 149-160. |
| [2] | SIRINAM P, IMANI M, JUAREZ M, et al. Deep Fingerprinting: Undermining Website Fingerprinting Defenses with Deep Learning[C]// ACM. Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2018: 1928-1943. |
| [3] | BHAT S, LU D, KWON A, et al. Var-CNN: A Data-Efficient Website Fingerprinting Attack Based on Deep Learning[J]. Proceedings on Privacy Enhancing Technologies, 2019(4): 292-310. |
| [4] | TAYLOR V F, SPOLAOR R, CONTI M, et al. AppScanner: Automatic Fingerprinting of Smartphone Apps from Encrypted Network Traffic[C]// IEEE. 2016 IEEE European Symposium on Security and Privacy (EuroS&P). New York: IEEE, 2016: 439-454. |
| [5] | VAN E T, BORTOLAMEOTTI R, CONTINELLA A, et al. FlowPrint: Semi-Supervised Mobile-App Fingerprinting on Encrypted Network Traffic[EB/OL]. (2020-02-26)[2024-04-22]. https://www.ndss-symposium.org/ndss-paper/flowprint-semi-supervised-mobile-app-fingerprinting-on-encrypted-network-traffic/. |
| [6] | SHAPIRA T, SHAVITT Y. FlowPic: Encrypted Internet Traffic Classification is as Easy as Image Recognition[C]// IEEE. IEEE INFOCOM 2019-IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS). New York: IEEE, 2019: 680-687. |
| [7] | HOROWICZ E, SHAPIRA T, SHAVITT Y. A Few Shots Traffic Classification with Mini-FlowPic Augmentations[C]// ACM. Proceedings of the 22nd ACM Internet Measurement Conference. New York: ACM, 2022: 647-654. |
| [8] | LIU Chang, HE Longtao, XIONG Gang, et al. FS-Net: A Flow Sequence Network for Encrypted Traffic Classification[C]// IEEE. IEEE INFOCOM 2019-IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS). New York: IEEE, 2019: 1171-1179. |
| [9] | GOODFELLOW I J, SHLENS J, SZEGEDY C. Explaining and Harnessing Adversarial Examples[EB/OL]. (2022-11-02)[2024-04-22]. http://arxiv.org/abs/1412.6572. |
| [10] | MADRY A, MAKELOV A, SCHMIDT L, et al. Towards Deep Learning Models Resistant to Adversarial Attacks[EB/OL]. (2019-09-04)[2024-04-22]. https://arxiv.org/abs/1706.06083v4. |
| [11] | BROWN T B, MANÉ D, ROY A, et al. Adversarial Patch[EB/OL]. (2018-05-16)[2024-04-22]. https://doi.org/10.48550/arXiv.1712.09665. |
| [12] | MOOSAVI-DEZFOOLI S M, FAWZI A, FROSSARD P. DeepFool: A Simple and Accurate Method to Fool Deep Neural Networks[C]// IEEE. 2016 IEEE Conference on Computer Vision and Pattern Recognition (CVPR). New York: IEEE, 2016: 2574-2582. |
| [13] | XIAO Chaowei, LI Bo, ZHU Junyan, et al. Generating Adversarial Examples with Adversarial Networks[EB/OL]. (2023-03-14)[2024-04-22]. http://arxiv.org/abs/1801.02610. |
| [14] | RAHMAN M S, IMANI M, MATHEWS N, et al. Mockingbird: Defending against Deep-Learning-Based Website Fingerprinting Attacks with Adversarial Traces[J]. IEEE Transactions on Information Forensics and Security, 2020(16): 1594-1609. |
| [15] | HOU Chengshang, GOU Gaopeng, SHI Junzheng, et al. WF-GAN: Fighting Back against Website Fingerprinting Attack Using Adversarial Learning[C]// IEEE. 2020 IEEE Symposium on Computers and Communications (ISCC). New York: IEEE, 2020: 1-7. |
| [16] | LIU Hao, DANI J, YU Hongkai, et al. AdvTraffic: Obfuscating Encrypted Traffic with Adversarial Examples[C]// IEEE. 2022 IEEE/ACM 30th International Symposium on Quality of Service (IWQoS). New York: IEEE, 2022: 1-10. |
| [17] | LI Wenhao, ZHANG Xiaoyu, BAO Huaifeng, et al. Prism: Real-Time Privacy Protection against Temporal Network Traffic Analyzers[J]. IEEE Transactions on Information Forensics and Security, 2023, 18: 2524-2537. |
| [18] |
YANG Youhuan, SUN Lei, DAI Leyu, et al. Generate Transferable Adversarial Network Traffic Using Reversible Adversarial Padding[J]. Computer Science, 2023, 50(12): 359-367.
doi: 10.11896/jsjkx.221000155 |
|
杨有欢, 孙磊, 戴乐育, 等. 使用RAP生成可传输的对抗网络流量[J]. 计算机科学, 2023, 50(12): 359-367.
doi: 10.11896/jsjkx.221000155 |
|
| [19] | HAN Dongqi, WANG Zhiliang, ZHONG Ying, et al. Evaluating and Improving Adversarial Robustness of Machine Learning-Based Network Intrusion Detectors[J]. IEEE Journal on Selected Areas in Communications, 2021, 39(8): 2632-2647. |
| [20] | QIAO Litao, WU Bang, YIN Shuijun, et al. Resisting DNN-Based Website Fingerprinting Attacks Enhanced by Adversarial Training[J]. IEEE Transactions on Information Forensics and Security, 2023, 18: 5375-5386. |
| [21] | GONG Jiajun, ZHANG Wuqi, ZHANG C, et al. Surakav: Generating Realistic Traces for a Strong Website Fingerprinting Defense[C]// IEEE. 2022 IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2022: 1558-1573. |
| [22] | SHAN S, BHAGOJI A N, ZHENG Haitao, et al. A Real-Time Defense against Website Fingerprinting Attacks[EB/OL]. (2021-02-08)[2024-04-22]. https://doi.org/10.48550/arXiv.2102.04291. |
| [23] | ZHU Ye, FU Xinwen, GRAHAM B, et al. Correlation-Based Traffic Analysis Attacks on Anonymity Networks[J]. IEEE Transactions on Parallel and Distributed Systems, 2010, 21(7): 954-967. |
| [24] | LI Huaxin, ZHU Haojin, MA Di. Demographic Information Inference through Meta-Data Analysis of Wi-Fi Traffic[J]. IEEE Transactions on Mobile Computing, 2018, 17(5): 1033-1047. |
| [25] | LI Huaxin, XU Zheyu, ZHU Haojin, et al. Demographics Inference through Wi-Fi Network Traffic Analysis[C]// IEEE. IEEE INFOCOM 2016-The 35th Annual IEEE International Conference on Computer Communications. New York: IEEE, 2016: 1-9. |
| [26] | YANG Bowen, LIU Dong. Research on Network Traffic Identification Based on Machine Learning and Deep Packet Inspection[C]// IEEE. 2019 IEEE 3rd Information Technology, Networking, Electronic and Automation Control Conference (ITNEC). New York: IEEE, 2019: 1887-1891. |
| [27] | LOTFOLLAHI M, JAFARI S M, SHIRALI H Z R, et al. Deep Packet: A Novel Approach for Encrypted Traffic Classification Using Deep Learning[J]. Soft Computing, 2020, 24(3): 1999-2012. |
| [28] | WANG Wei, ZHU Ming, ZENG Xuewen, et al. Malware Traffic Classification Using Convolutional Neural Network for Representation Learning[C]// IEEE. 2017 International Conference on Information Networking (ICOIN). New York: IEEE, 2017: 712-717. |
| [29] | CHEN Zihan, CHENG Guang, XU Ziheng, et al. A Survey on Internet Encrypted Traffic Detection, Classification and Identification[J]. Chinese Journal of Computers, 2023, 46(5): 1060-1085. |
| 陈子涵, 程光, 徐子恒, 等. 互联网加密流量检测、分类与识别研究综述[J]. 计算机学报, 2023, 46(5): 1060-1085. | |
| [30] | DONG Cong, LU Zhigang, CUI Zelin, et al. MBTree: Detecting Encryption RATs Communication Using Malicious Behavior Tree[J]. IEEE Transactions on Information Forensics and Security, 2021, 16: 3589-3603. |
| [31] | SHAPIRA T, SHAVITT Y. FlowPic: A Generic Representation for Encrypted Traffic Classification and Applications Identification[J]. IEEE Transactions on Network and Service Management, 2021, 18(2): 1218-1232. |
| [32] | SZEGEDY C, ZAREMBA W, SUTSKEVER I, et al. Intriguing Properties of Neural Networks[EB/OL]. (2022-12-20)[2024-04-22]. https://doi.org/10.48550/arXiv.1312.6199. |
| [33] | CARLINI N, WAGNER D. Towards Evaluating the Robustness of Neural Networks[C]// IEEE. 2017 IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2017: 39-57. |
| [34] | GOODFELLOW I, POUGET-ABADIE J, MIRZA M, et al. Generative Adversarial Networks[J]. Communications of the ACM, 2020, 63(11): 139-144. |
| [35] | PAPERNOT N, MCDANIEL P, GOODFELLOW I, et al. Practical Black-Box Attacks against Machine Learning[C]// ACM. Proceedings of the 2017 ACM on Asia Conference on Computer and Communications Security. New York: ACM, 2017: 506-519. |
| [36] | HU Yongjin, TIAN Jin, MA Jun. A Novel Way to Generate Adversarial Network Traffic Samples against Network Traffic Classification[EB/OL]. (2021-01-01)[2024-04-22]. https://doi.org/10.1155/2021/7367107. |
| [37] | JUAREZ M, IMANI M, PERRY M, et al. Toward an Efficient Website Fingerprinting Defense[M]. Heidelberg: Springer, 2016. |
| [38] | WANG Tao, GOLDBERG I. Walkie-Talkie: An Efficient Defense against Passive Website Fingerprinting Attacks[C]// USENIX. Proceedings of the 26th USENIX Conference on Security Symposium. Berkeley: USENIX, 2017: 1375-1390. |
| [39] | ABUSNAINA A, JANG R, KHORMALI A, et al. DFD: Adversarial Learning-Based Approach to Defend against Website Fingerprinting[C]// IEEE. IEEE INFOCOM 2020-IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS). New York: IEEE, 2020: 2459-2468. |
| [40] | YIN Haoyu, LIU Yingjian, LI Yue, et al. Defeating Deep Learning Based De-Anonymization Attacks with Adversarial Example[EB/OL]. (2023-11-01)[2024-04-22]. https://doi.org/10.1016/j.jnca.2023.103733. |
| [41] | NASR M, BAHRAMALI A, HOUMANSADR A. Defeating DNN-Based Traffic Analysis Systems in Real-Time with Blind Adversarial Perturbations[EB/OL]. (2021-07-10)[2024-04-22]. https://www.usenix.org/conference/usenixsecurity21/presentation/nasr. |
| [42] | QIN Tao, WANG Lei, LIU Zhaoli, et al. Robust Application Identification Methods for P2P and VoIP Traffic Classification in Backbone Networks[J]. Knowledge-Based Systems, 2015, 82: 152-162. |
| [43] | DRAPER-GIL G, LASHKARI A H, MAMUN M S I, et al. Characterization of Encrypted and VPN Traffic Using Time-Related Features[C]// IEEE. The 2nd International Conference on Information Systems Security and Privacy. New York: IEEE, 2016: 407-414. |
| [1] | 徐茹枝, 张凝, 李敏, 李梓轩. 针对恶意软件的高鲁棒性检测模型研究[J]. 信息网络安全, 2024, 24(8): 1184-1195. |
| [2] | 徐子荣, 郭焱平, 闫巧. 基于特征恶意度排序的恶意软件对抗防御模型[J]. 信息网络安全, 2024, 24(4): 640-649. |
| [3] | 冯光升, 蒋舜鹏, 胡先浪, 马明宇. 面向物联网的入侵检测技术研究新进展[J]. 信息网络安全, 2024, 24(2): 167-178. |
| [4] | 李奕轩, 贾鹏, 范希明, 陈尘. 基于控制流变换的恶意程序检测GNN模型对抗样本生成方法[J]. 信息网络安全, 2024, 24(12): 1896-1910. |
| [5] | 张选, 万良, 罗恒, 杨阳. 基于两阶段图学习的僵尸网络自动化检测方法[J]. 信息网络安全, 2024, 24(12): 1933-1947. |
| [6] | 王强, 刘奕智, 李涛, 贺小川. 网络流量密态匿迹与体系对抗综述[J]. 信息网络安全, 2024, 24(10): 1484-1492. |
| [7] | 许可, 李嘉怡, 蒋兴浩, 孙锬锋. 一种基于轮廓稀疏对抗的视频步态隐私保护算法[J]. 信息网络安全, 2024, 24(1): 48-59. |
| [8] | 沈华, 田晨, 郭森森, 慕志颖. 基于对抗性机器学习的网络入侵检测方法研究[J]. 信息网络安全, 2023, 23(8): 66-75. |
| [9] | 李晨蔚, 张恒巍, 高伟, 杨博. 基于AdaN自适应梯度优化的图像对抗迁移攻击方法[J]. 信息网络安全, 2023, 23(7): 64-73. |
| [10] | 蒋曾辉, 曾维军, 陈璞, 武士涛. 面向调制识别的对抗样本研究综述[J]. 信息网络安全, 2023, 23(6): 74-90. |
| [11] | 仝鑫, 金波, 王斌君, 翟晗名. 融合对抗增强和多任务优化的恶意短信检测方法[J]. 信息网络安全, 2023, 23(10): 21-30. |
| [12] | 李季瑀, 付章杰, 张玉斌. 一种基于跨域对抗适应的图像信息隐藏算法[J]. 信息网络安全, 2023, 23(1): 93-102. |
| [13] | 胡卫, 赵文龙, 陈璐, 付伟. 基于Logits向量的JSMA对抗样本攻击改进算法[J]. 信息网络安全, 2022, 22(3): 62-69. |
| [14] | 郑耀昊, 王利明, 杨婧. 基于网络结构自动搜索的对抗样本防御方法研究[J]. 信息网络安全, 2022, 22(3): 70-77. |
| [15] | 夏强, 何沛松, 罗杰, 刘嘉勇. 基于普遍对抗噪声的高效载体图像增强算法[J]. 信息网络安全, 2022, 22(2): 64-75. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||