信息网络安全 ›› 2023, Vol. 23 ›› Issue (7): 86-97.doi: 10.3969/j.issn.1671-1122.2023.07.009
基于双通道特征融合的分布式拒绝服务攻击检测算法
- 深圳大学计算机与软件学院,深圳 518060
-
收稿日期:2023-03-27出版日期:2023-07-10发布日期:2023-07-14 -
通讯作者:闫巧 yanq@szu.edu.cn -
作者简介:蒋英肇(1999—),男,江西,硕士研究生,主要研究方向为模型反演攻击|陈雷(1996—),男,湖南,硕士研究生,主要研究方向为入侵检测|闫巧(1972—),女,广西,教授,博士,CCF会员,主要研究方向为网络安全和人工智能 -
基金资助:国家自然科学基金(61976142);深圳市科技计划项目(JCYJ20210324093609025)
Distributed Denial of Service Attack Detection Algorithm Based on Two-Channel Feature Fusion
JIANG Yingzhao, CHEN Lei, YAN Qiao( )
)
- College of Computer Science and Software Engineering, Shenzhen University, Shenzhen 518060, China
-
Received:2023-03-27Online:2023-07-10Published:2023-07-14
摘要:
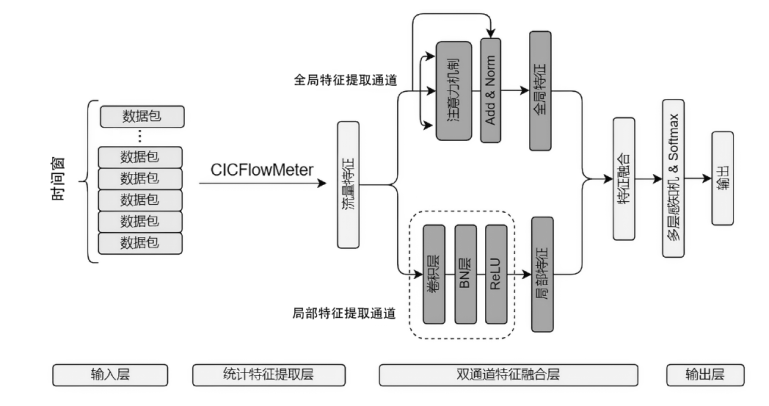
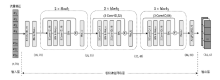
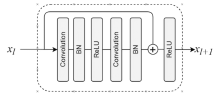
随着物联网的快速发展,接入网络的设备数量迅速增长,导致分布式拒绝服务(Distributed Denial of Service,DDoS)攻击往往具有攻击方式多样、迅速多变的特点。面对大流量且攻击方式多变的混合DDoS攻击,现有的基于统计分析的检测方法过于依赖人为设置阈值,而基于机器学习的异常检测方法存在误报率和漏报率高等问题。因此,文章提出一种基于卷积神经网络(Convolutional Neural Network,CNN)和注意力机制的双通道融合检测模型DCFD-CA,该模型将统计特征样本分别输入基于CNN的局部特征提取通道和基于注意力机制的全局特征提取通道,利用两个通道结构的差异化达到不同的效果,使用CNN可以抽象出局部特征值之间的相关关系,使用注意力机制可以对重要的特征分配更多的权重。为了融合两个通道的功能,首先对各通道输出的抽象特征进行归一化操作,然后利用堆叠方式融合两个不同通道的特征数据,最后通过三层神经网络进行检测分类。在CICIDS2017-DDoS、CICIDS2018-DDoS和CICDDoS2019公开数据集上进行实验,DCFD-CA模型的F1分数分别是0.9863、0.9996和0.9998,均优于SAE-MLP、Composite DNN等模型。
中图分类号:
引用本文
蒋英肇, 陈雷, 闫巧. 基于双通道特征融合的分布式拒绝服务攻击检测算法[J]. 信息网络安全, 2023, 23(7): 86-97.
JIANG Yingzhao, CHEN Lei, YAN Qiao. Distributed Denial of Service Attack Detection Algorithm Based on Two-Channel Feature Fusion[J]. Netinfo Security, 2023, 23(7): 86-97.
表2
CICIDS2018-DDoS数据集
| 类别 | 训练集的 数量/个 | 验证集的 数量/个 | 测试集的 数量/个 |
|---|---|---|---|
| benign | 6423367 | 1835248 | 917624 |
| DDoS attack-HOIC | 480208 | 137202 | 68602 |
| DDoS attacks-LOIC-HTTP | 403334 | 115238 | 57619 |
| DoS attacks-Hulk | 323338 | 92382 | 46192 |
| DoS attacks-SlowHTTPTest | 97923 | 27978 | 13989 |
| DoS attacks-GoldenEye | 29056 | 8302 | 4150 |
| DoS attacks-Slowloris | 7693 | 2198 | 1099 |
| DDoS attack-LOIC-UDP | 1211 | 346 | 173 |
表3
CICDDoS2019数据集
| 类别 | 训练集的数量/个 | 验证集的数量/个 | 测试集的数量/个 |
|---|---|---|---|
| benign | 159216 | 45490 | 22746 |
| ntp | 219545 | 62727 | 31364 |
| dns | 219545 | 62727 | 31364 |
| ldap | 219545 | 62727 | 31364 |
| mssql | 219545 | 62727 | 31364 |
| netbios | 219545 | 62727 | 31364 |
| snmp | 219545 | 62727 | 31364 |
| ssdp | 219545 | 62727 | 31364 |
| udp | 219545 | 62727 | 31364 |
| udplag | 219545 | 62727 | 31364 |
| syn | 219545 | 62727 | 31364 |
| tftp | 219545 | 62727 | 31364 |
| [1] | YOACHIMIK O. Mitigating a 754 Million PPS DDoS Attack Automatically[EB/OL]. (2020-07-09) [2022-05-16]. https://blog.cloudflare.com/mitigating-a-754-million-pps-ddos-attack-automatically. |
| [2] | VIJ A, PASHA S. Azure DDoS Protection-2021 Q3 and Q4 DDoS Attack Trends[EB/OL]. (2022-01-25) [2022-05-16]. https://azure.microsoft.com/zh-cn/blog/azure-ddos-protection-2021-q3-and-q4-ddos-attack-trends. |
| [3] | Tencent Cloud T-Sec DDoS Protection Team, Green Alliance Technology Threat Intelligence Team. 2021 Global DDoS Threat Report[EB/OL]. (2022-01-26) [2022-05-16]. https://cloud.tencent.com/developer/article/1936949. |
| 腾讯云T-Sec DDoS防护团队, 绿盟科技威胁情报团队. 2021年全球DDoS威胁报告[EB/OL]. (2022-01-26) [2022-05-16]. https://cloud.tencent.com/developer/article/1936949. | |
| [4] | Wangsu Science&Technology. China Internet Security Report for the First Half of 2021[EB/OL]. (2021-11-23) [2022-05-16]. https://www.vzkoo.com/document/992eef6bb162171fd39d55876bf3f19b.html. |
| 网宿科技. 2021年上半年中国互联网安全报告[EB/OL]. (2021-11-23) [2022-05-16]. https://www.vzkoo.com/document/992eef6bb162171fd39d55876bf3f19b.html. | |
| [5] | LIU Ying, ZHI Ting, SHEN Ming, et al. Software-Defined DDoS Detection with Information Entropy Analysis and Optimized Deep Learning[J]. Future Generation Computer Systems, 2022(129): 99-114. |
| [6] | LIU Zhen, HU Changzhen, SHAN Chun. Riemannian Manifold on Stream Data: Fourier Transform and Entropy-Based DDoS Attacks Detection Method[J]. Computers & Security, 2021(109): 102392-102407. |
| [7] | KOAY A, CHEN A, WELCH I, et al. A New Multi Classifier System Using Entropy-Based Features in DDoS Attack Detection[C]// IEEE. 2018 International Conference on Information Networking (ICOIN). New York: IEEE, 2018: 162-167. |
| [8] | IDHAMMAD M, AFDEL K, BELOUCH M. Detection System of HTTP DDoS Attacks in a Cloud Environment Based on Information Theoretic Entropy and Random Forest[J]. Security and Communication Networks, 2018(2): 1-13. |
| [9] | YE Jin, CHENG Xiangyang, ZHU Jian, et al. A DDoS Attack Detection Method Based on SVM in Software Defined Network[EB/OL]. (2018-01-01) [2022-05-16]. https://dl.acm.org/doi/10.1155/2018/9804061. |
| [10] |
TUAN N N, HUNG P H, NGHIA N D, et al. A DDoS Attack Mitigation Scheme in ISP Networks Using Machine Learning Based on SDN[J]. Electronics, 2020, 9(3): 413-432.
doi: 10.3390/electronics9030413 URL |
| [11] | DE-MIRANDA V R, INÁCIO P R M, MAGONI D, et al. Detection of Reduction-of-Quality DDoS Attacks Using Fuzzy Logic and Machine Learning Algorithms[J]. Computer Networks, 2021(186): 107792-107811. |
| [12] | MIN Erxue, CHEN Wei, LONG Jun, et al. TR-IDS: Anomaly-Based Intrusion Detection Through Text-Convolutional Neural Network and Random Forest[EB/OL]. (2018-12-16) [2023-01-13]. https://dl.acm.org/doi/10.1155/2018/4943509. |
| [13] | CHOLLET F. Xception: Deep Learning with Depthwise Separable Convolutions[C]// IEEE. 2017 IEEE Conference on Computer Vision and Pattern Recognition (CVPR). New York: IEEE, 2017: 1251-1258. |
| [14] | GIRSHICK R. Fast R-CNN[C]// IEEE. Proceedings of the IEEE International Conference on Computer Vision. New York: IEEE, 2015: 1440-1448. |
| [15] |
REN A, LI Zhe, DING Caiwen, et al. SC-DCNN: Highly-Scalable Deep Convolutional Neural Network Using Stochastic Computing[J]. ACM SIGPLAN Notices, 2017, 52(4): 405-418.
doi: 10.1145/3093336.3037746 URL |
| [16] | SHAHRIAR M H, HAQUE N I, RAHMAN M A, et al. G-IDS: Generative Adversarial Networks Assisted Intrusion Detection System[C]// IEEE. 2020 IEEE 44th Annual Computers, Software, and Applications Conference (COMPSAC). New York: IEEE, 2020: 376-385. |
| [17] | AHUJA N, SINGAL G, MUKHOPADHYAY D. DLSDN: Deep Learning for DDoS Attack Detection in Software Defined Networking[C]// IEEE. 2021 11th International Conference on Cloud Computing, Data Science & Engineering (Confluence). New York: IEEE, 2021: 683-688. |
| [18] | YANG Kun, ZHANG Junjie, XU Yang, et al. DDoS Attacks Detection with Autoencoder[C]// IEEE. NOMS 2020-2020 IEEE/IFIP Network Operations and Management Symposium. New York: IEEE, 2020: 1-9. |
| [19] | SALAHUDDIN M A, BARI M F, ALAMEDDINE H A, et al. Time-Based Anomaly Detection Using Autoencoder[C]// IEEE. 2020 16th International Conference on Network and Service Management (CNSM). New York: IEEE, 2020: 1-9. |
| [20] | AMAIZU G C, NWAKANMA C I, BHARDWAJ S, et al. Composite and Efficient DDoS Attack Detection Framework for B5G Networks[J]. Computer Networks, 2021(188): 107871-107881. |
| [21] | MA Li, CHAI Ying, CUI Lei, et al. A Deep Learning-Based DDoS Detection Framework for Internet of Things[C]// IEEE. ICC 2020-2020 IEEE International Conference on Communications (ICC). New York: IEEE, 2020: 1-6. |
| [22] |
DORIGUZZI-CORIN R, MILLAR S, SCOTT-HAYWARD S, et al. LUCID: A Practical, Lightweight Deep Learning Solution for DDoS Attack Detection[J]. IEEE Transactions on Network and Service Management, 2020, 17(2): 876-889.
doi: 10.1109/TNSM.4275028 URL |
| [23] | LASHKARI A H, DRAPER-GIL G, MAMUN M S I, et al. Characterization of Tor Traffic Using Timebased Features[C]// SciTePress. Proceedings of the 3rd International Conference on Information Systems Security and Privacy. San Francisco: SciTePress, 2017: 253-262. |
| [24] | HE Kaiming, ZHANG Xiangyu, REN Shaoqing, et al. Deep Residual Learning for Image Recognition[C]// IEEE. Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition. New York: IEEE, 2016: 770-778. |
| [25] | VASWANI A, SHAZEER N, PARMAR N, et al. Attention Is All You Need[EB/OL]. (2017-06-12) [2023-01-17]. https://arxiv.org/abs/1706.03762. |
| [26] | SHARAFALDIN I, LASHKARI A H, GHORBANI A A. Toward Generating a New Intrusion Detection Dataset and Intrusion Traffic Characterization[J]. ICISSP, 2018(1): 108-116. |
| [27] | SHARAFALDIN I, LASHKARI A H, HAKAK S, et al. Developing Realistic Distributed Denial of Service (DDoS) Attack Dataset and Taxonomy[C]// IEEE. 2019 International Carnahan Conference on Security Technology (ICCST). New York: IEEE, 2019: 1-8. |
| [1] | 刘刚, 杨雯莉, 王同礼, 李阳. 基于云联邦的差分隐私保护动态推荐模型[J]. 信息网络安全, 2023, 23(7): 31-43. |
| [2] | 苑文昕, 陈兴蜀, 朱毅, 曾雪梅. 基于深度学习的HTTP负载隐蔽信道检测方法[J]. 信息网络安全, 2023, 23(7): 53-63. |
| [3] | 刘宇啸, 陈伟, 张天月, 吴礼发. 基于稀疏自动编码器的可解释性异常流量检测[J]. 信息网络安全, 2023, 23(7): 74-85. |
| [4] | 李志华, 王志豪. 基于LCNN和LSTM混合结构的物联网设备识别方法[J]. 信息网络安全, 2023, 23(6): 43-54. |
| [5] | 赵小林, 王琪瑶, 赵斌, 薛静锋. 基于机器学习的匿名流量分类方法研究[J]. 信息网络安全, 2023, 23(5): 1-10. |
| [6] | 赵彩丹, 陈璟乾, 吴志强. 基于多通道联合学习的自动调制识别网络[J]. 信息网络安全, 2023, 23(4): 20-29. |
| [7] | 施园, 李杨, 詹孟奇. 一种面向微服务的多维度根因定位算法[J]. 信息网络安全, 2023, 23(3): 73-83. |
| [8] | 谭柳燕, 阮树骅, 杨敏, 陈兴蜀. 基于深度学习的教育数据分类方法[J]. 信息网络安全, 2023, 23(3): 96-102. |
| [9] | 徐占洋, 程洛飞, 程建春, 许小龙. 一种使用Bi-ADMM优化深度学习模型的方案[J]. 信息网络安全, 2023, 23(2): 54-63. |
| [10] | 陈得鹏, 刘肖, 崔杰, 仲红. 一种基于双阈值函数的成员推理攻击方法[J]. 信息网络安全, 2023, 23(2): 64-75. |
| [11] | 贾凡, 康舒雅, 江为强, 王光涛. 基于NLP及特征融合的漏洞相似性算法评估[J]. 信息网络安全, 2023, 23(1): 18-27. |
| [12] | 李季瑀, 付章杰, 张玉斌. 一种基于跨域对抗适应的图像信息隐藏算法[J]. 信息网络安全, 2023, 23(1): 93-102. |
| [13] | 张光华, 刘永升, 王鹤, 于乃文. 基于BiLSTM和注意力机制的智能合约漏洞检测方案[J]. 信息网络安全, 2022, 22(9): 46-54. |
| [14] | 高博, 陈琳, 严迎建. 基于CNN-MGU的侧信道攻击研究[J]. 信息网络安全, 2022, 22(8): 55-63. |
| [15] | 顾兆军, 刘婷婷, 高冰, 隋翯. 基于GAN-Cross的工控系统类不平衡数据异常检测[J]. 信息网络安全, 2022, 22(8): 81-89. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||