信息网络安全 ›› 2023, Vol. 23 ›› Issue (6): 1-10.doi: 10.3969/j.issn.1671-1122.2023.06.001
基于软件定义边界的服务保护方案
- 1.东南大学网络空间安全学院,南京 211189
2.网络通信与安全紫金山实验室,南京 211189
-
收稿日期:2023-02-10出版日期:2023-06-10发布日期:2023-06-20 -
通讯作者:何城鋆hechengjunfox@gmail.com -
作者简介:黄杰(1970—),男,湖北,教授,博士,主要研究方向为物联网安全、无线网络安全、大数据安全|何城鋆(1998—),男,江苏,硕士研究生,主要研究方向为访问控制 -
基金资助:国家重点研发计划(2018YFB2100400)
Service Protection Scheme Based on Software Defined Perimeter
- 1. School of Cyber Science and Engineering, Southeast University, Nanjing 211189, China
2. Purple Mountain Laboratories for Network and Communication Security, Nanjing 211189, China
-
Received:2023-02-10Online:2023-06-10Published:2023-06-20
摘要:
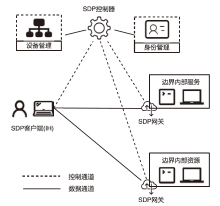
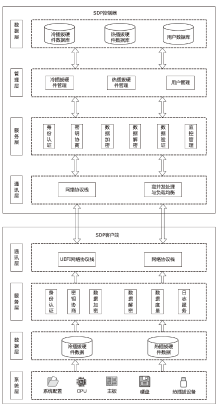
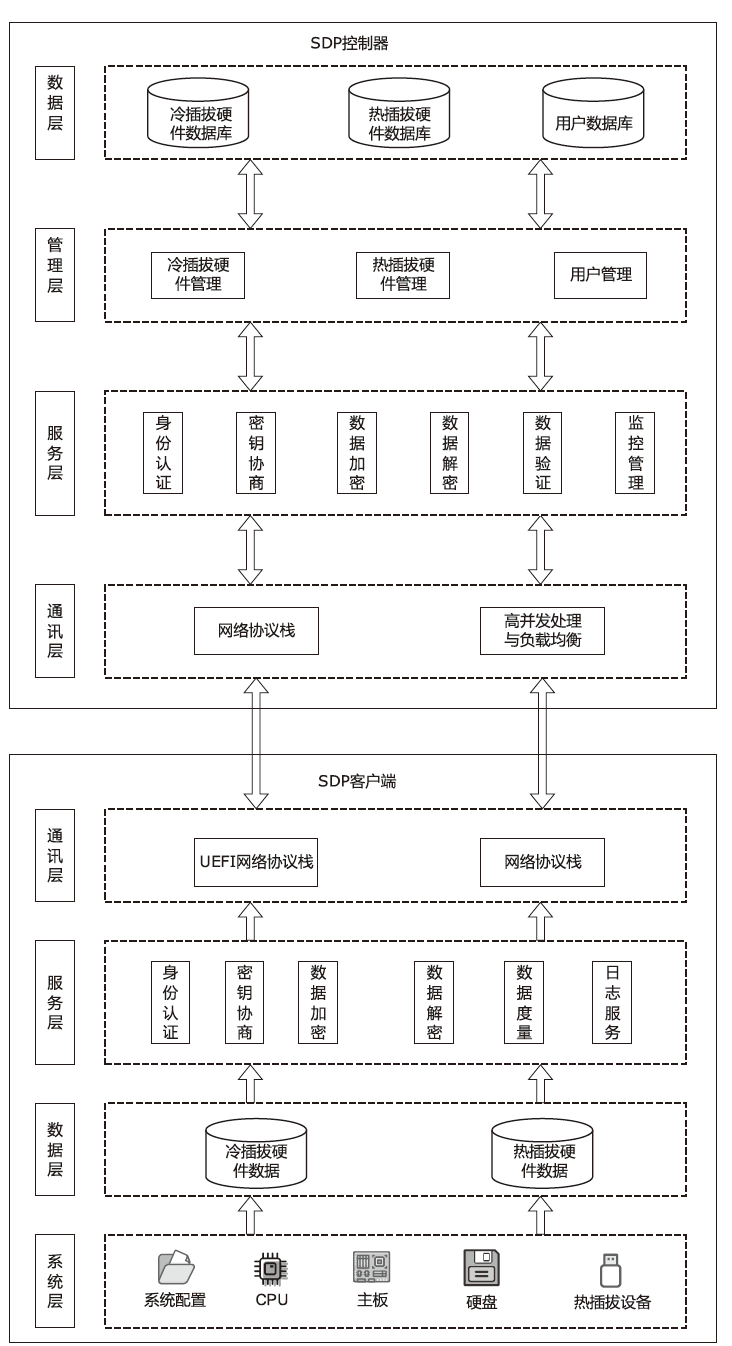
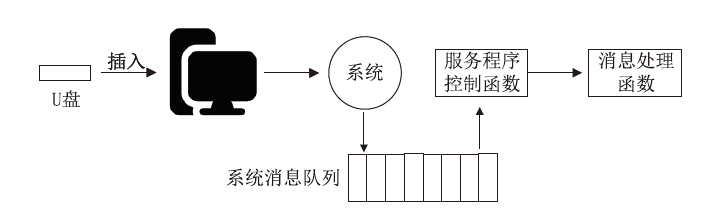
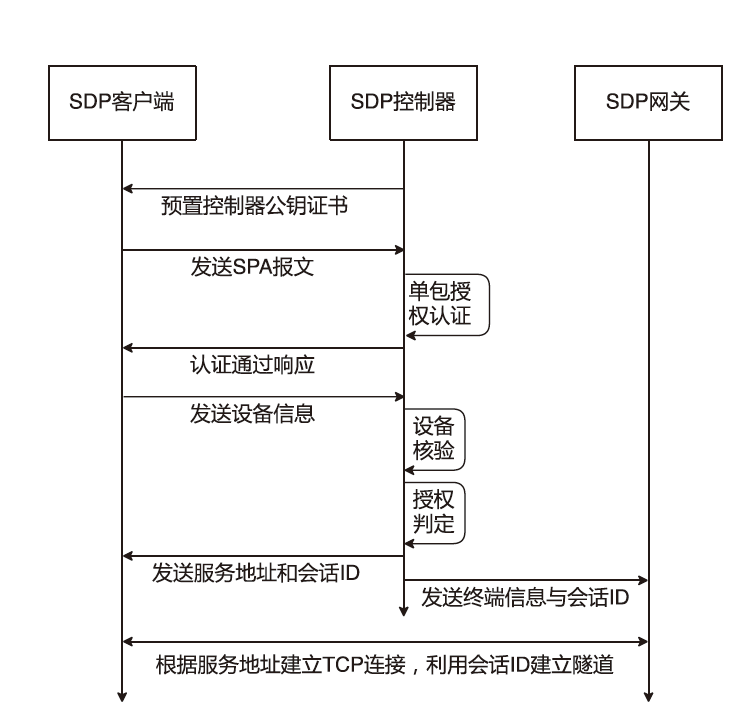
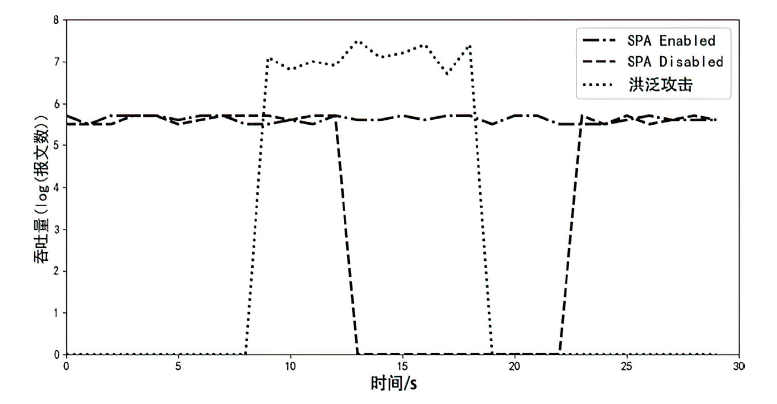
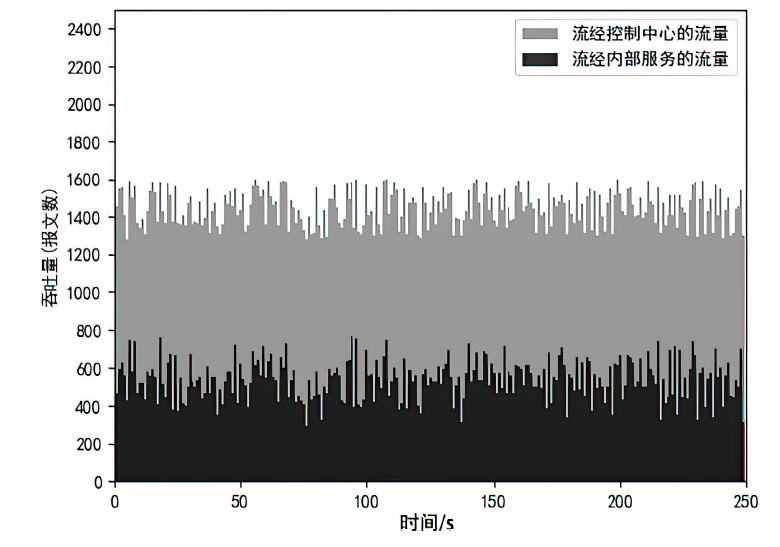
针对在零信任环境下,基于物理边界防护的传统网络安全架构逐渐被瓦解而导致的服务暴露问题,文章提出一种基于软件定义边界的服务保护方案。通过收集请求终端的用户属性和设备属性以对终端进行授权判定;使用单包授权认证机制进行先认证后连接,实现服务隐藏、身份认证及访问控制等功能;基于零信任持续认证的思想,在操作系统启动前基于固件层对访问终端进行初始度量,在操作系统启动后基于服务进行持续度量;最后,基于AHP设计信任评估算法对终端进行安全评估。从性能与安全性两方面进行分析,结果证明该方案能有效提高通信效率并抵御多种网络安全攻击。
中图分类号:
引用本文
黄杰, 何城鋆. 基于软件定义边界的服务保护方案[J]. 信息网络安全, 2023, 23(6): 1-10.
HUANG Jie, HE Chengjun. Service Protection Scheme Based on Software Defined Perimeter[J]. Netinfo Security, 2023, 23(6): 1-10.
表1
符号对照表
| 符号 | 说明 |
|---|---|
| ${{H}_{x}}$ | 哈希数据 |
| $T{{s}_{x}}$ | 时间戳数据 |
| $Pu{{b}_{c}}$ | SDP控制器公钥 |
| $Pr{{i}_{c}}$ | SDP控制器私钥 |
| ${{P}_{k}}$ | 会话密钥 |
| $P{{W}_{x}}$ | 用户口令 |
| $C\_I{{N}_{x}}$ | 冷插拔设备信息 |
| $H\_I{{N}_{x}}$ | 热插拔设备信息 |
| $An{{s}_{x}}$ | 授权判定结果 |
| $St{{d}_{x}}$ | 冷插拔设备指纹值 |
| $D{{N}_{x}}$ | 设备标识名 |
| $Toke{{n}_{x}}$ | 令牌信息 |
| $Verif{{y}_{x}}$ | 验证码 |
| $Type$ | 数据类型 |
| $Cer{{t}_{x}}$ | 设备证书 |
| $SM2$ | 国密椭圆曲线公钥密码算法 |
| $SM3$ | 国密密码杂凑算法 |
| $SM4$ | 国密分组密码算法 |
表1
| [1] | SAMANIEGO M, DETERS R. Zero-Trust Hierarchical Management in IoT[C]// IEEE. 2018 IEEE International Congress on Internet of Things (ICIOT). IEEE, 2018: 88-95. |
| [2] | ROSE S, BORCHERT O, MITCHELL S, et al. Zero Trust Architecture[EB/OL]. (2020-08-16)[2023-01-30]. https://csrc.nist.gov/publications/detail/sp/800-207/final?ref=hackernoon.com. |
| [3] | BARTH D, GILMAN E. Zero Trust Networks: Building Trusted Systems in Untrusted Networks[M]. Sebastopol: O’Reilly Media, 2017. |
| [4] |
MOUBAYED A, REFAEY A, SHAMI A. Software-Defined Perimeter (Sdp): State of the Art Secure Solution for Modern Networks[J]. IEEE Network, 2019, 33(5): 226-233.
doi: 10.1109/MNET.65 URL |
| [5] | INDU I, ANAND P, BHASKAR V. Identity and Access Management in Cloud Environment: Mechanisms and Challenges[J]. Engineering Science and Technology, 2018, 21(4): 574-588. |
| [6] |
SHARMA D H, DHOTE C A, POTEY M M. Identity and Access Management As Security-as-a-Service From Clouds[J]. Procedia Computer Science, 2016, 79: 170-174.
doi: 10.1016/j.procs.2016.03.117 URL |
| [7] | SHEIKH N, PAWAR M, LAWRENCE V. Zero Trust Using Network Micro Segmentation[C]// IEEE. IEEE INFOCOM 2021-IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS). New York: IEEE 2021: 1-6. |
| [8] |
SALLAM A, REFAEY A, SHAMI A. On the Security of SDN: A Completed Secure and Scalable Framework Using the Software-Defined Perimeter[J]. IEEE access, 2019, 7: 146577-146587.
doi: 10.1109/Access.6287639 URL |
| [9] | ZAHEER Z, CHANG H, MUKHERJEE S, et al. Eztrust: Network-Independent Zero-Trust Perimeterization for Microservices[C]// ACM. Proceedings of the 2019 ACM Symposium on SDN Research. New York: ACM, 2019: 49-61. |
| [10] | WARD R, BEYER B. Beyondcorp: A New Approach to Enterprise Security[EB/OL]. (2014-04-08)[2023-01-30]. https://research.google/pubs/pub43231/. |
| [11] | DECUSATIS C, LIENGTIRAPHAN P, SAGER A, et al. Implementing Zero Trust Cloud Networks with Transport Access Control and First Packet Authentication[C]// IEEE. 2016 IEEE International Conference on Smart Cloud. New York: IEEE, 2016: 5-10. |
| [12] | Cloud Security Alliance (CSA). Software-Defined Perimeter (SDP) Specification v2.0[EB/OL]. (2022-10-03)[2023-01-30]. https://cloudsecurityalliance.org/artifacts/software-defined-perimeter-zero-trust-specification-v2/. |
| [13] | BRICKER G. Unified Extensible Firmware interface (UEFI) and Secure Boot: Promise and Pitfalls[J]. Journal of Computing Sciences in Colleges, 2013, 29(1): 60-63. |
| [14] | YAO Q, WANG Q, ZHANG X, et al. Dynamic Access Control and Authorization System Based on Zero-Trust Architecture[C]// RIS. Proceedings of the 2020 1st International Conference on Control, Robotics and Intelligent System. New York: RIS, 2020: 123-127. |
| [15] |
SAATY R W. The Analytic Hierarchy Process—What it is and How it is Used[J]. Mathematical Modelling, 1987, 9(3): 161-176.
doi: 10.1016/0270-0255(87)90473-8 URL |
| [16] | WU Kehe, CHENG Rui, JIANG Xiaochen, et al. Security Protection Scheme of Power IoT Based on SDP[J]. Netinfo Security, 2022, 22(2): 32-38. |
| 吴克河, 程瑞, 姜啸晨, 等. 基于SDP的电力物联网安全防护方案[J]. 信息网络安全, 2022, 22(2): 32-38. |
| [1] | 张征辉, 陈兴蜀, 罗永刚, 吴天雄. 一种Spark平台下的作业性能评估方法[J]. 信息网络安全, 2022, 22(9): 86-95. |
| [2] | 郭宝霞, 王佳慧, 马利民, 张伟. 基于零信任的敏感数据动态访问控制模型研究[J]. 信息网络安全, 2022, 22(6): 86-93. |
| [3] | 吴克河, 程瑞, 姜啸晨, 张继宇. 基于SDP的电力物联网安全防护方案[J]. 信息网络安全, 2022, 22(2): 32-38. |
| [4] | 高见, 王凯悦, 黄淑华. 面向视频监控网络的安全评估指标体系研究[J]. 信息网络安全, 2021, 21(12): 78-85. |
| [5] | 吴云坤, 姜博, 潘瑞萱, 刘玉岭. 一种基于零信任的SDN网络访问控制方法[J]. 信息网络安全, 2020, 20(8): 37-46. |
| [6] | 刘远, 孙晨, 张嫣玲. 基于Overlay技术的零信任网络研究[J]. 信息网络安全, 2020, 20(10): 83-91. |
| [7] | 梁智强, 林丹生. 基于电力系统的信息安全风险评估机制研究[J]. 信息网络安全, 2017, 17(4): 86-90. |
| [8] | 章清亮, 秦元庆. 基于DDS通信的舰载网络安全评估指标及应用研究[J]. 信息网络安全, 2017, 17(2): 73-78. |
| [9] | 张海川, 赵泽茂, 田玉杰, 李学双. 基于个性化空间匿名算法最优化选择研究[J]. 信息网络安全, 2015, 15(3): 23-27. |
| [10] | 肖传奇, 陈明志. 云环境下基于IFAHP的用户行为信任模型研究[J]. 信息网络安全, 2015, 26(12): 14-20. |
| [11] | 王星河, 余洋, 夏春和. 面向网络协同防御的动态风险评估模型[J]. 信息网络安全, 2014, 14(9): 39-43. |
| [12] | 李增鹏;马春光;李迎涛. 基于层次分析涉密信息系统风险评估[J]. , 2014, 14(3): 0-0. |
| [13] | . 基于层次分析涉密信息系统风险评估[J]. , 2014, 14(3): 80-. |
| [14] | 胡刚;罗皓;梅越. 基于FMEA的OLTP系统可靠性设计与评价[J]. , 2013, 13(5): 0-0. |
| [15] | 许子先;陈燕. WLAN无线接入设备安全研究[J]. , 2013, 13(4): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||