信息网络安全 ›› 2023, Vol. 23 ›› Issue (6): 11-21.doi: 10.3969/j.issn.1671-1122.2023.06.002
面向网络安全开源情报的知识图谱研究综述
- 四川大学网络空间安全学院,成都 610207
-
收稿日期:2023-01-09出版日期:2023-06-10发布日期:2023-06-20 -
通讯作者:刘嘉勇ljy@scu.edu.cn -
作者简介:王晓狄(1996—),男,河南,博士研究生,主要研究方向为知识图谱、自然语言处理|黄诚(1987—),男,重庆,副教授,博士,主要研究方向为网络安全、攻防技术|刘嘉勇(1962—),男,四川,教授,博士,主要研究方向为网络信息处理与威胁情报分析、数据挖掘、隐蔽通信构建及分析、虚拟社区及社交机器人自动化分析与检测 -
基金资助:国家自然科学基金(61902265);国家重点研发计划(2019QY1405);国家重点研发计划(2021YFB3100500)
A Survey of Cyber Security Open-Source Intelligence Knowledge Graph
WANG Xiaodi, HUANG Cheng, LIU Jiayong( )
)
- School of Cyber Science and Engineering, Sichuan University, Chengdu 610207, China
-
Received:2023-01-09Online:2023-06-10Published:2023-06-20
摘要:
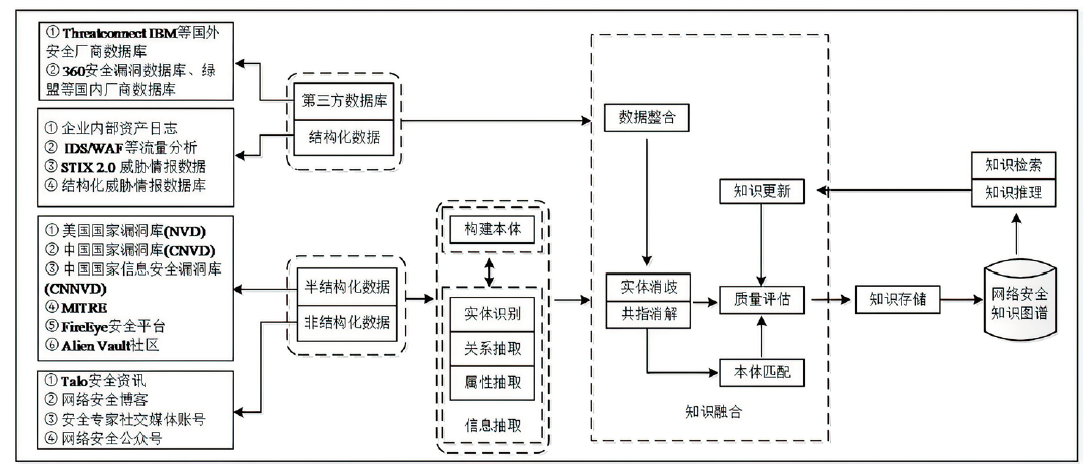
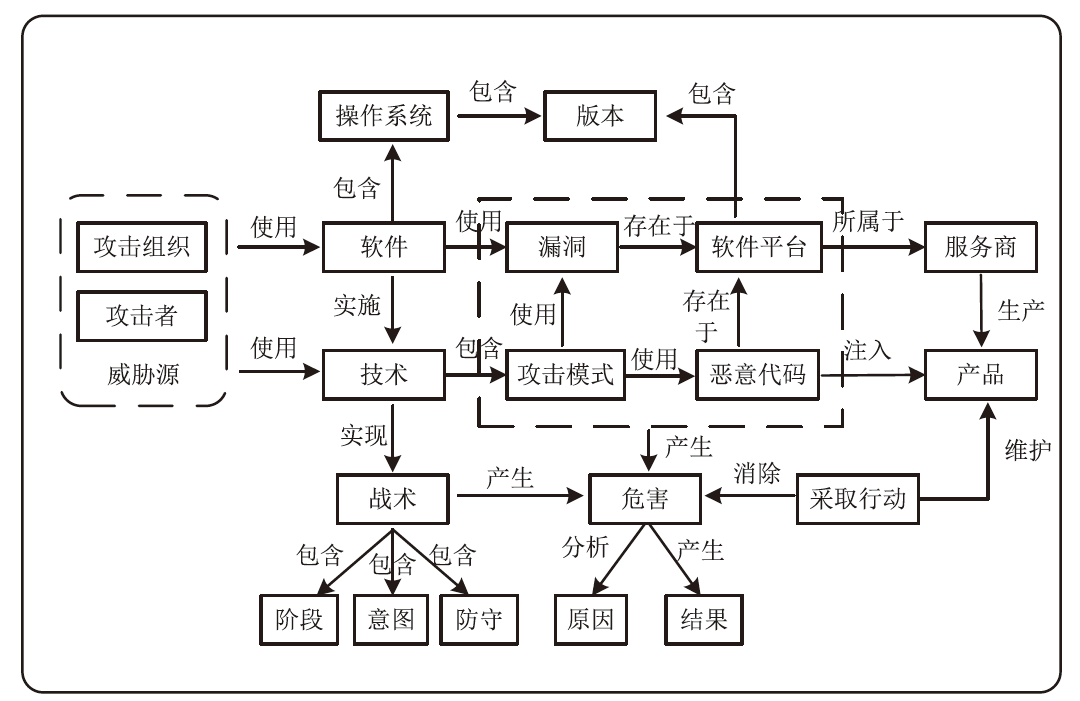
随着信息化的发展,网络上每天会产生大量的网络安全开源情报。然而,这些网络开源情报大多数都是多源异构的文本数据,并不能直接分析使用。因此,引入知识图谱的相关技术对其进行归纳整理,实现知识的深层次语义挖掘和智能推理分析极为重要。文章首先给出了网络安全情报知识图谱的构建过程,然后介绍网络安全知识图谱的关键技术以及国内外研究现状,包括信息抽取和知识推理,最后对知识图谱在网络安全领域中应用面临的挑战进行总结,并给出未来可能的工作方向。
中图分类号:
引用本文
王晓狄, 黄诚, 刘嘉勇. 面向网络安全开源情报的知识图谱研究综述[J]. 信息网络安全, 2023, 23(6): 11-21.
WANG Xiaodi, HUANG Cheng, LIU Jiayong. A Survey of Cyber Security Open-Source Intelligence Knowledge Graph[J]. Netinfo Security, 2023, 23(6): 11-21.
表1
网络安全本体构建方法对比表
| 方案 | 年份 | 方法描述 | 优点 | 缺点 |
|---|---|---|---|---|
| 文献[ | 2005 | 按照类别、目标、影响等维度对网络攻击分类,分别定义不同的概念 | 根据不同的分类细化得到的概念表示更为合理 | 领域内有些需求并未得到满足,需对定义进行细化 |
| 文献[ | 2015 | 整合大量结构化和非结构化的数据形成网络安全知识图谱数据库本体 | 本体模型中定义的概念语义信息丰富 | 并未与STIX等业界认可的标准进行相互关联,因此使用范围受限 |
| 文献[ | 2020 | 基于CVO,映射从Twitter 中提取的漏洞概念 | 根据基本规则对漏洞实时预警 | 漏洞来源单一,且情报来源并未考虑到用户推文 |
| 文献[ | 2020 | 对数据包进行分析,分析内容包括概念、属性以及约束;可捕获其它本体所没有的网络活动语义协议和端口 | 在端口和协议方面具有更广泛的覆盖范围 | 不能捕获特定集线器和交换机模型的语义信息 |
| 文献[ | 2021 | 定义了11个对社会工程领域有重要影响的核心实体概念和22种实体之间的关系 | 可通过知识模式理解、分析、重用和共享社会工程的领域知识 | 可扩展性待验证 |
表2
实体识别方法对比表
| 类型 | 方法 | 方法描述 | 性能评价 | 可操作数据 类型 | |||
|---|---|---|---|---|---|---|---|
| 准确率 | 召回率 | F1 | 非结 构化 | 半结 构化 | |||
| 基于规则 | 文献[ | 遗传算法+正则表达式+本体 | 82.79% | 78.19% | 80.42% | • | √ |
| 基于机器学习 | 文献[ | 指定种子样本 | NDR | NDR | NDR | √ | √ |
| 文献[ | 条件随机场+安全本体 | 83% | 76% | 80% | √ | √ | |
| 基于深度学习 | 文献[ | LSTM+CRF | 97.43% 97.55% | 94.13% 94.46% | 84.26% 88.83% | √ | √ |
| 文献[ | 外部词典+LSTM+自注意力机制+CRF | 90.19% | 86.60% | 88.36% | √ | √ | |
| 文献[ | LSTM(编码)+动态注意力机制+LSTM(解码) | 89.62% | 87.63% | 88.61% | √ | √ | |
表3
关系抽取方法对比表
| 类型 | 方法 | 方法描述 | 性能评价 | 操作 对象 | 可操作数据 类型 | ||||
|---|---|---|---|---|---|---|---|---|---|
| 准确率 | 召回率 | F1 | 实体 | 关系 | 非结构化 | 半结 构化 | |||
| 基于 规则 | 文献[ | 在对MUC-7的规划中改进信息抽取引擎 | 86% | 87% | 86% | • | √ | • | √ |
| 基于 机器 学习 | 文献[ | 朴素贝叶斯+感知机抽取 | 89.4% | 82% | 85.5% | • | √ | √ | √ |
| 文献[ | 模式组合聚类+依存特征、语法模板抽取 | NDR | 75.63% | NDR | • | √ | √ | √ | |
| 基于 深度 学习 | 文献[ | CNN+softmax抽取 | NDR | NDR | 82.7% | • | √ | √ | √ |
| 文献[ | CNN+负采样抽取 | NDR | NDR | 85.4% | • | √ | √ | √ | |
| 文献[ | 完全依赖树+软剪枝技术 抽取 | NDR | NDR | NDR | • | √ | √ | √ | |
| 文献[ | BERT+双向GRU+注意力机制 | 83% | 79.09% | 80.98% | √ | √ | √ | √ | |
表4
知识推理方法对比表
| 类型 | 方法 | 推理 类型 | 方法描述 | 优点 | 缺点 |
|---|---|---|---|---|---|
| 基于规则推理 | 文献[ | 关系 | 启发式方法+无监督学习+特定规则进行推理 | 使用机器学习方法获取关系判别模型 | 构建谓词逻辑公式 难度大 |
| 文献[ | 关系 | 软推理规则(Datalog风格)+硬推理规则(互斥约束)进行推理 | 可动态解决RDF知识库的知识不一致问题 | 推理效率 较低 | |
| 文献[ | 实体 | 语义Web RDF+SWRL规则进行情报推理 | 基于UCO本体,操作相对简单 | 规则难以 制定 | |
| 文献[ | 关系 | UCO本体+结构化知识图+漏洞知识结构图进行推理 | 可充分利用知识图谱和漏洞库之间的隐层关系,推理速度快 | 推理能力有限,不能扩充到大图上 | |
| 基于深度学习 推理 | 文献[ | 实体、关系 | LSTM+图注意力机制+深度强化学习 | 扩大实体节点的搜索范围 | 不能同时学习多个查询关系的推理路径 |
| 文献[ | 实体 | 层次聚类+安全技术距离衡量进行推理 | 可深度挖掘黑客组织特征的隐式知识 | 特征的分析角度难以把握 | |
| 文献[ | 实体 | 类型信息约束+分层注意力机制进行推理 | 推理结果具有较好的 可解释性 | 只能解决单一类型实体,不能处理多粒度实体类型 | |
| 文献[ | 实体、关系 | GCN+门循环单元+静态图约束执行事实预测 | 推理准确率高,速度快 | 模型训练难度大 |
表5
知识图谱关键技术对比表
| 关键 技术 | 方法 | 优点 | 缺点 |
|---|---|---|---|
| 信息 抽取 | 基于规则模板[ | 准确率高、速度快 | 需要领域专家提前制定规则模板,耗费大量的人力和物力资源 |
| 基于统计 机器学习[ | 可将信息抽取看成是序列标记或者多分类任务,比较灵活 | 特征需要人工构建,需要标注大量的训练语料 | |
| 基于深度学习[ | 模型可自己学习特征,无需人工标注特征,效率提升明显 | 对机器算力要求高,训练代价昂贵,模型表现依赖训练数据的质量 | |
| 知识 推理 | 基于一阶谓词 逻辑[ 基于本体规则[ | 可解释性强,便于 理解 | 只适用于小规模知识图谱,且规则无法保证全面性 |
| 基于深度学习[ | 特征学习能力强,可充分利用知识图谱中的结构化信息 | 可移植性差,依赖训练语料 |
| [1] | TAVARE S, DUTTA P, DUTTA S, et al. Cyber Intelligence and Information Retrieval[EB/OL]. (2021-01-04)[2022-12-05]. https://link.springer.com/content/pdf/10.1007/978-981-16-4284-5.pdf. |
| [2] |
YAN Ke, LIU Lu, XIANG Yong, et al. Guest Editorial: AI and Machine Learning Solution Cyber Intelligence Technologies: New Methodologies and Applications[J]. IEEE Transactions on Industrial Informatics, 2020, 16(10): 6626-6631.
doi: 10.1109/TII.9424 URL |
| [3] | LIN Yankai, LIU Zhiyuan, SUN Maosong, et al. Learning Entity and Relation Embeddings for Knowledge Graph Completion[C]// AAAI. 29th AAAI Conference on Artificial Intelligence. Austin:AAAI, 2015: 2181-2187. |
| [4] | HUANG Hengqi, YU Juan, LIAO Xiao, et al. A Review of Knowledge Graph Research[J]. Application of Computer Systems, 2019, 28(6): 1-12. |
| 黄恒琪, 于娟, 廖晓, 等. 知识图谱研究综述[J]. 计算机系统应用, 2019, 28(6): 1-12. | |
| [5] | FU Leijie, CAO Yan, BAI Yu, et al. Development Status and Prospects of Knowledge Graph in Vertical Fields in China[J]. Computer Application Research, 2021, 38(11): 3201-3214. |
| 付雷杰, 曹岩, 白瑀, 等. 国内垂直领域知识图谱发展现状与展望[J]. 计算机应用研究, 2021, 38(11): 3201-3214. | |
| [6] | WANG Xiwei, WEI Ya'nan, XING Yunfei, et al. Research on the Development Dynamics and Trends of Social Network Public Opinion Knowledge Graph[J]. Journal of Information Science, 2019, 38(12): 1329-1338. |
| 王晰巍, 韦雅楠, 邢云菲, 等. 社交网络舆情知识图谱发展动态及趋势研究[J]. 情报学报, 2019, 38(12): 1329-1338. | |
| [7] | CHEN Qiang, DAI Shiya. Accounting Fraud Risk Identification Method Based on Financial Knowledge Graph[J]. Big Data, 2021, 7(3): 116-129. |
|
陈强, 代仕娅. 基于金融知识图谱的会计欺诈风险识别方法[J]. 大数据, 2021, 7(3): 116-129.
doi: 10.11959/j.issn.2096-0271.2021029 |
|
| [8] | WANG Jiwei, LIANG Huaizhong, FAN Wei, et al. Design and Implementation of Intelligent Question Answering System Based on Chinese Medical Knowledge Graph[J]. Chinese Journal of Digital Medicine, 2021, 16(2): 54-58. |
| 王继伟, 梁怀众, 樊伟, 等. 基于中文医疗知识图谱的智能问答系统设计与实现方法[J]. 中国数字医学, 2021, 16(2): 54-58. | |
| [9] | WANG Senzhang, LIU Yi, ZHANG Jiaqiang, et al. Time-Aware Hierarchical Self-Attention Network for E-Commerce Platform User Intent Prediction[J]. Journal of Information Security, 2021, 6(5): 169-180. |
| 王森章, 刘毅, 张家强, 等. 面向电子商务平台用户意图预测的时间感知分层自注意力网络[J]. 信息安全学报, 2021, 6(5): 169-180. | |
| [10] | XU Zenglin, SHENG Yongpan, HE Lirong, et al. A Review of Knowledge Graph Technology[J]. Journal of University of Electronic Science and Technology of China, 2016, 45(4): 589-606. |
| 徐增林, 盛泳潘, 贺丽荣, 等. 知识图谱技术综述[J]. 电子科技大学学报, 2016, 45(4): 589-606. | |
| [11] | LIU Qiao, LI Yang, DUAN Hong, et al. A Review of Knowledge Graph Construction Technology[J]. Computer Research and Development, 2016, 53(3): 582-600. |
| 刘峤, 李杨, 段宏, 等. 知识图谱构建技术综述[J]. 计算机研究与发展, 2016, 53(3): 582-600. | |
| [12] | XIE Minrong. Research and Implementation of Network Security Knowledge Graph Construction Technology[D]. Chengdu: University of Electronic Science and Technology of China, 2020. |
| 谢敏容. 网络安全知识图谱构建技术研究与实现[D]. 成都: 电子科技大学, 2020. | |
| [13] | DING Zhaoyun, LIU Kai, LIU Bin, et al. A Review of Network Security Knowledge Graph Research[J]. Journal of Huazhong University of Science and Technology (Natural Science Edition), 2021, 49(7): 79-91. |
| 丁兆云, 刘凯, 刘斌, 等. 网络安全知识图谱研究综述[J]. 华中科技大学学报(自然科学版), 2021, 49(7): 79-91. | |
| [14] | YANG Peian, WU Yang, SU Liya, et al. A Review of Cyberspace Threat Intelligence Sharing Technology[J]. Computer Science, 2018, 45(6): 9-18. |
| 杨沛安, 武杨, 苏莉娅, 等. 网络空间威胁情报共享技术综述[J]. 计算机科学, 2018, 45(6): 9-18. | |
| [15] | OASIS S. OASIS Cyber Threat Intelligence (CTI) TC[EB/OL]. [2022-12-05]. https://cyboxproject.github.io/releases/2.1/. |
| [16] | SHI Zhixin, MA Yuru, ZHANG Yue, et al. A Review of Threat Intelligence Related Standards[J]. Information Security Research, 2019, 5(7): 560-569. |
| 石志鑫, 马瑜汝, 张悦, 等. 威胁情报相关标准综述[J]. 信息安全研究, 2019, 5(7): 560-569. | |
| [17] | PINGLE A, PIPLAI A, MITTAL S, et al. Relext: Relation Extraction Using Deep Learning Approaches for Cybersecurity Knowledge Graph Improvement[C]// ACM. Proceedings of the 2019 IEEE/ACM International Conference on Advances in Social Networks Analysis and Mining. New York: ACM, 2019: 879-886. |
| [18] |
HANSMAN S, HUNT R. A Taxonomy of Network and Computer Attacks[J]. Computers & Security, 2005, 24(1): 31-43.
doi: 10.1016/j.cose.2004.06.011 URL |
| [19] | IANNACONE M, BOHN S, NAKAMURA G, et al. Developing an Ontology for Cyber Security Knowledge Graphs[C]// ACM. Proceedings of the 10th Annual Cyber and Information Security Research Conference. New York: ACM, 2015: 1-4. |
| [20] | SYED R. Cybersecurity Vulnerability Management: A Conceptual Ontology and Cyber Intelligence Alert System[EB/OL]. (2020-06-11)[2022-12-05]. https://www.sciencedirect.com/science/article/pii/S0378720620302718. |
| [21] | SIKOS L F. Knowledge Representation to Support Partially Automated Honeypot Analysis Based on Wireshark Packet Capture Files[C]// Springer. Intelligent Decision Technologies 2019: Proceedings of the 11th KES International Conference on Intelligent Decision Technologies (KES-IDT 2019). Berlin:Springer, 2020: 345-351. |
| [22] |
WANG Zuoguang, ZHU Hongsong, LIU Peipei, et al. Social Engineering in Cybersecurity: A Domain Ontology and Knowledge Graph Application Examples[J]. Cybersecurity, 2021, 4(1): 1-21.
doi: 10.1186/s42400-020-00065-3 |
| [23] |
LI Jing, SUN Aixin, HAN Jianglei, et al. A Survey on Deep Learning for Named Entity Recognition[J]. IEEE Transactions on Knowledge and Data Engineering, 2020, 34(1): 50-70.
doi: 10.1109/TKDE.2020.2981314 URL |
| [24] |
LIU Pan, GUO Yanming, WANG Fenglei, et al. Chinese Named Entity Recognition: The State of the Art[J]. Neurocomputing, 2022, 473: 37-53.
doi: 10.1016/j.neucom.2021.10.101 URL |
| [25] | BALDUCCINI M, KUSHNER S, SPECK J. Ontology-Driven Data Semantics Discovery for Cyber-Security[C]// Springer. International Symposium on Practical Aspects of Declarative Languages. Berlin:Springer, 2015: 1-16. |
| [26] | RITTER A, WRIGHT E, CASEY W, et al. Weakly Supervised Extraction of Computer Security Events from Twitter[C]// ACM. Proceedings of the 24th International Conference on World Wide Web. New York: ACM, 2015: 896-905. |
| [27] | JOSHI A, LAL R, FININ T, et al. Extracting Cybersecurity Related Linked Data from Text[C]// IEEE. 2013 IEEE Seventh International Conference on Semantic Computing. New York: IEEE, 2013: 252-259. |
| [28] | HUANG Zhiheng, XU Wei, YU Kai. Bidirectional LSTM-CRF Models for Sequence Tagging[EB/OL]. (2015-08-09)[2022-12-05]. https://arxiv.org/pdf/1508.01991.pdf. |
| [29] |
GAO Chen, ZHANG Xuan, LIU Hui. Data and Knowledge-Driven Named Entity Recognition for Cyber Security[J]. Cybersecurity, 2021, 4(1): 1-13.
doi: 10.1186/s42400-020-00065-3 |
| [30] | LI Tao, HU Yongjin, JU Ankang, et al. Adversarial Active Learning for Named Entity Recognition in Cybersecurity[J]. Cmc-Computers Materials & Continua, 2021, 66(1): 407-420. |
| [31] | AONE C, HALVERSON L, HAMPTON T, et al. SRA: Description of the IE2 System Used for MUC-7[EB/OL]. (1998-05-01)[2022-12-05]. https://aclanthology.org/M98-1012.pdf. |
| [32] | XIA Sun, LEHONG D. Feature-Based Approach to Chinese Term Relation Extraction[C]// IEEE. 2009 International Conference on Signal Processing Systems. New York: IEEE, 2009: 410-414. |
| [33] | YAN Yulan, OKAZAKI N, MATSUO Y, et al. Unsupervised Relation Extraction by Mining Wikipedia Texts Using Information from the Web[C]// ACL. Proceedings of the Joint Conference of the 47th Annual Meeting of the ACL and the 4th International Joint Conference on Natural Language Processing of the AFNLP. New York: The Association for Computational Linguistics, 2009: 1021-1029. |
| [34] | ZENG Daojian, LIU Kang, LAI Siwei, et al. Relation Classification via Convolutional Deep Neural Network[C]// ACL. Proceedings of COLING 2014, the 25th International Conference on Computational Linguistics:Technical Papers. New York: The Association for Computational Linguistics, 2014: 2335-2344. |
| [35] | XU Kun, FENG Yansong, HUANG Songfang, et al. Semantic Relation Classification via Convolutional Neural Networks with Simple Negative Sampling[C]// ACL. Proceedings of the 2015 Conference on Empirical Methods in Natural Language Processing. New York: The Association for Computational Linguistics, 2015: 536-540. |
| [36] | GUO Zhijiang, ZHANG Yan, LU Wei. Attention Guided Graph Convolutional Networks for Relation Extraction[C]// ACL. Proceedings of the 57th Annual Meeting of the Association for Computational Linguistics. New York: The Association for Computational Linguistics, 2019: 241-251. |
| [37] | GUO Yongyan, LIU Zhengyu, HUANG Cheng, et al. CyberRel: Joint Entity and Relation Extraction for Cybersecurity Concepts[C]// Springer. International Conference on Information and Communications Security. Berlin:Springer, 2021: 447-463. |
| [38] |
DONG Cong, JIANG Bo, LU Zhigang, et al. A Review of Knowledge Graphs for Cyberspace Security Intelligence[J]. Journal of Information Security, 2020, 5(5): 56-76.
doi: 10.4236/jis.2014.52006 URL |
| 董聪, 姜波, 卢志刚, 等. 面向网络空间安全情报的知识图谱综述[J]. 信息安全学报, 2020, 5(5): 56-76. | |
| [39] | SCHOENMACKERS S, DAVIS J, ETZIONI O, et al. Learning First-Order Horn Clauses from Web Text[C]// ACL. Proceedings of the 2010 Conference on Empirical Methods in Natural Language Processing. New York: The Association for Computational Linguistics, 2010: 1088-1098. |
| [40] | NAKASHOLE N, SOZIO M, SUCHANEK F M, et al. Query-Time Reasoning in Uncertain RDF Knowledge Bases with Soft and Hard Rules[J]. VLDS, 2012, 884: 15-20. |
| [41] | MITTAL S, DAS P K, MULWAD V, et al. Cybertwitter: Using Twitter to Generate Alerts for Cybersecurity Threats and Vulnerabilities[C]// IEEE. 2016 IEEE/ACM International Conference on Advances in Social Networks Analysis and Mining (ASONAM). New York:IEEE, 2016: 860-867. |
| [42] | QIN Shengzhi, CHOW K. Automatic Analysis and Reasoning Based on Vulnerability Knowledge Graph[C]// Springer. Cyberspace Data and Intelligence, and Cyber-Living, Syndrome, and Health. Berlin:Springer, 2019: 3-19. |
| [43] | WANG Heng, LI Shuangyin, PAN Rong, et al. Incorporating Graph Attention Mechanism into Knowledge Graph Reasoning Based on Deep Reinforcement Learning[C]// ACL. Proceedings of the 2019 Conference on Empirical Methods in Natural Language Processing and the 9th International Joint Conference on Natural Language Processing (EMNLP-IJCNLP). New York: The Association for Computational Linguistics, 2019: 2623-2631. |
| [44] | HONG Dongpao. Learning Knowledge Graph Embedding with Entity Descriptions Based on LSTM Networks[C]// IEEE. 2020 IEEE International Symposium on Product Compliance Engineering-Asia (ISPCE-CN). New York:IEEE, 2020: 1-7. |
| [45] | ZHOU Xiaojie, ZHAI Pengjun and FANG Yu. Learning Description-Based Representations for Temporal Knowledge Graph Reasoning via Attentive CNN[EB/OL]. (2021-12-03)[2022-12-05]. https://iopscience.iop.org/article/10.1088/1742-6596/2025/1/012003/pdf. |
| [46] | DING Zhaoyun, CAO Deqi, LIU Lina, et al. A Method for Discovering Hidden Patterns of Cybersecurity Knowledge Based on Hierarchical Clustering[C]// IEEE. 2021 IEEE Sixth International Conference on Data Science in Cyberspace (DSC). New York:IEEE, 2021: 334-338. |
| [47] | WANG Yuzhuo, WANG Hongzhi, HE Junwei, et al. TAGAT: Type-Aware Graph Attention Networks for Reasoning Over Knowledge Graphs[EB/OL]. (2021-09-28)[2022-12-05]. https://www.sciencedirect.com/science/article/pii/S0950705121007620. |
| [48] | LI Zixuan, JIN Xiaolong, LI Wei, et al. Temporal Knowledge Graph Reasoning Based on Evolutional Representation Learning[C]// ACM. Proceedings of the 44th International ACM SIGIR Conference on Research and Development in Information Retrieval. New York: ACM, 2021: 408-417. |
| [1] | 孙珵珵. 网络安全治理对策研究[J]. 信息网络安全, 2023, 23(6): 104-110. |
| [2] | 金志刚, 刘凯, 武晓栋. 智能电网AMI领域IDS研究综述[J]. 信息网络安全, 2023, 23(1): 1-8. |
| [3] | 孙鹏宇, 谭晶磊, 李晨蔚, 张恒巍. 基于时间微分博弈的网络安全防御决策方法[J]. 信息网络安全, 2022, 22(5): 64-74. |
| [4] | 金波, 唐前进, 唐前临. CCF计算机安全专业委员会2022年网络安全十大发展趋势解读[J]. 信息网络安全, 2022, 22(4): 1-6. |
| [5] | 陈妍, 韦湘, 陆臻. 云计算环境下网络安全产品检测方法研究[J]. 信息网络安全, 2022, 22(12): 1-6. |
| [6] | 刘忻, 王家寅, 杨浩睿, 张瑞生. 一种基于区块链和secGear框架的车联网认证协议[J]. 信息网络安全, 2022, 22(1): 27-36. |
| [7] | 白宏鹏, 邓东旭, 许光全, 周德祥. 基于联邦学习的入侵检测机制研究[J]. 信息网络安全, 2022, 22(1): 46-54. |
| [8] | 顾兆军, 姚峰, 丁磊, 隋翯. 基于半实物的机场供油自控系统网络安全测试[J]. 信息网络安全, 2021, 21(9): 16-24. |
| [9] | 蔡满春, 王腾飞, 岳婷, 芦天亮. 基于ARF的Tor网站指纹识别技术[J]. 信息网络安全, 2021, 21(4): 39-48. |
| [10] | 赵小林, 赵斌, 赵晶晶, 薛静锋. 基于攻击识别的网络安全度量方法研究[J]. 信息网络安全, 2021, 21(11): 17-27. |
| [11] | 朱朝阳, 周亮, 朱亚运, 林晴雯. 基于行为图谱筛的恶意代码可视化分类算法[J]. 信息网络安全, 2021, 21(10): 54-62. |
| [12] | 吴佳明, 熊焰, 黄文超, 武建双. 一种基于距离导向的模糊测试变异方法[J]. 信息网络安全, 2021, 21(10): 63-68. |
| [13] | 金志刚, 王新建, 李根, 岳顺民. 融合攻击图和博弈模型的网络防御策略生成方法[J]. 信息网络安全, 2021, 21(1): 1-9. |
| [14] | 刘大恒, 李红灵. QR码网络钓鱼检测研究[J]. 信息网络安全, 2020, 20(9): 42-46. |
| [15] | 李世斌, 李婧, 唐刚, 李艺. 基于HMM的工业控制系统网络安全状态预测与风险评估方法[J]. 信息网络安全, 2020, 20(9): 57-61. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||