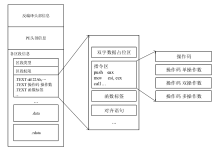
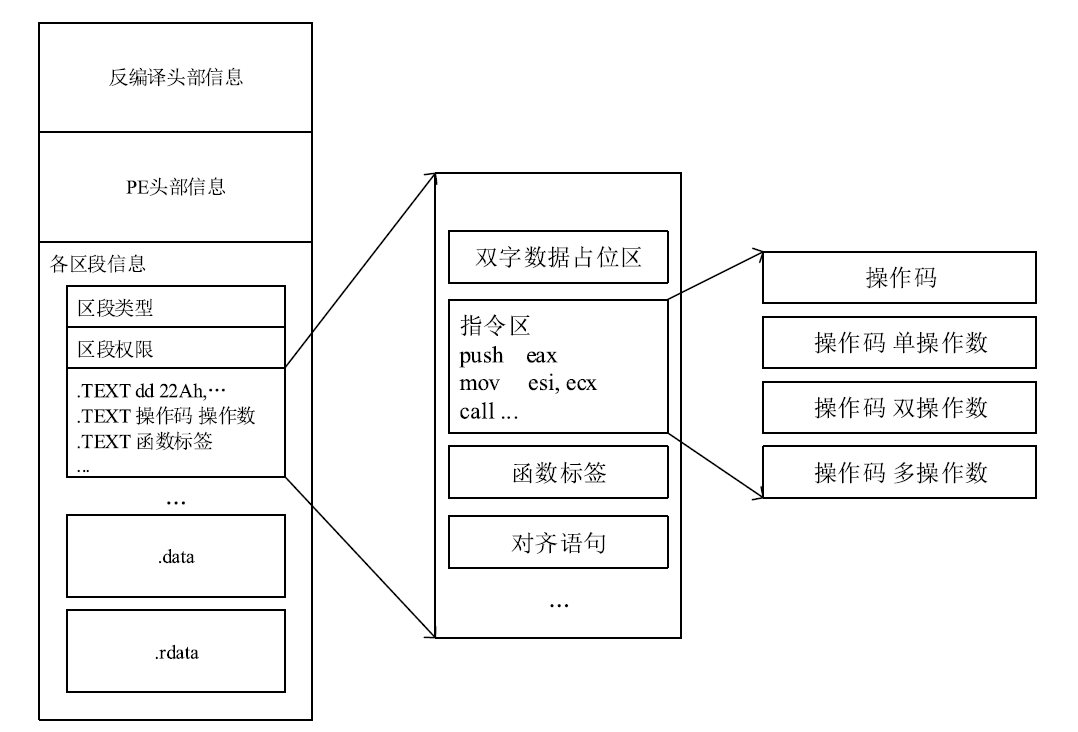
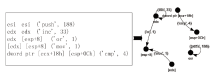
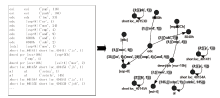
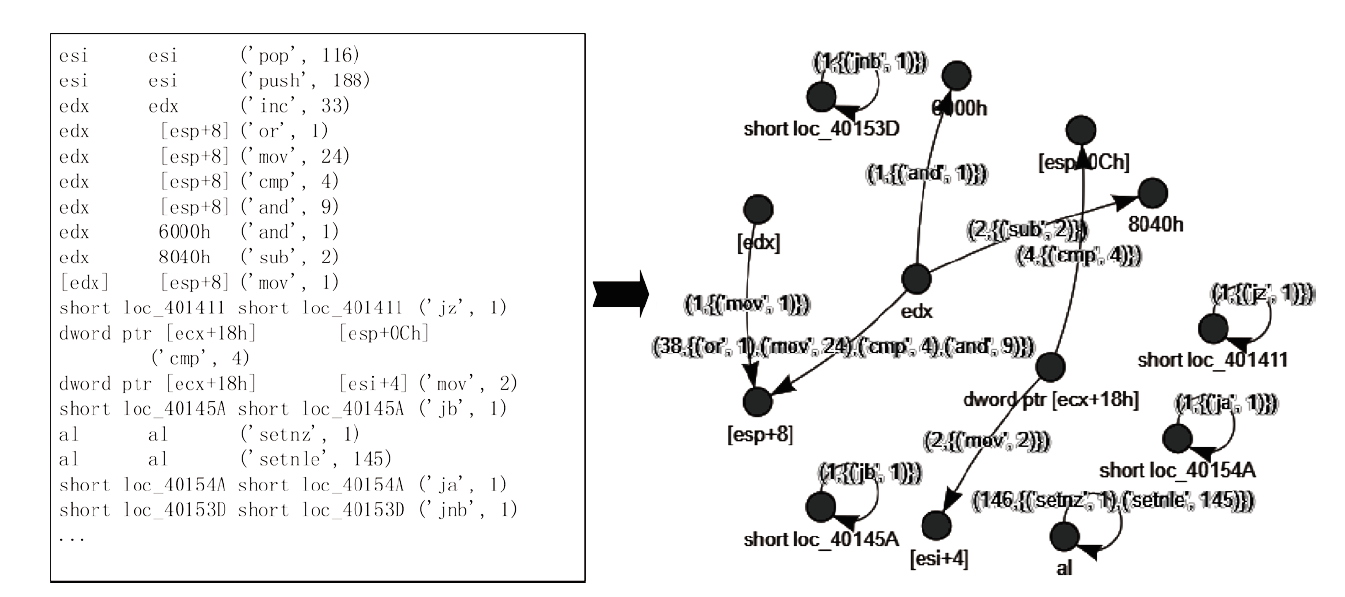
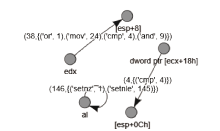
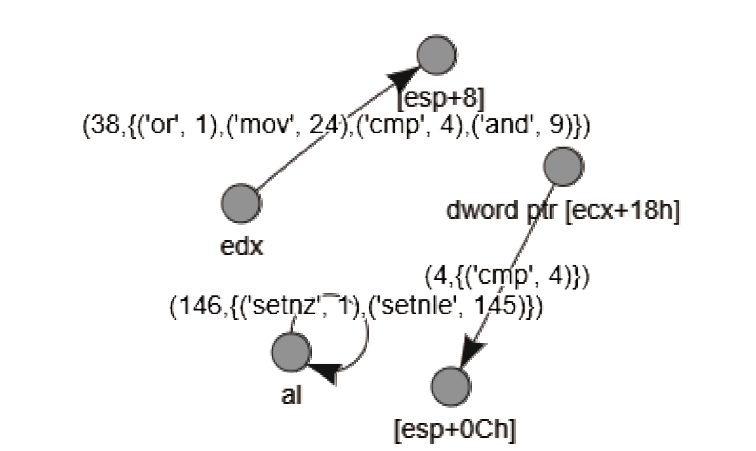
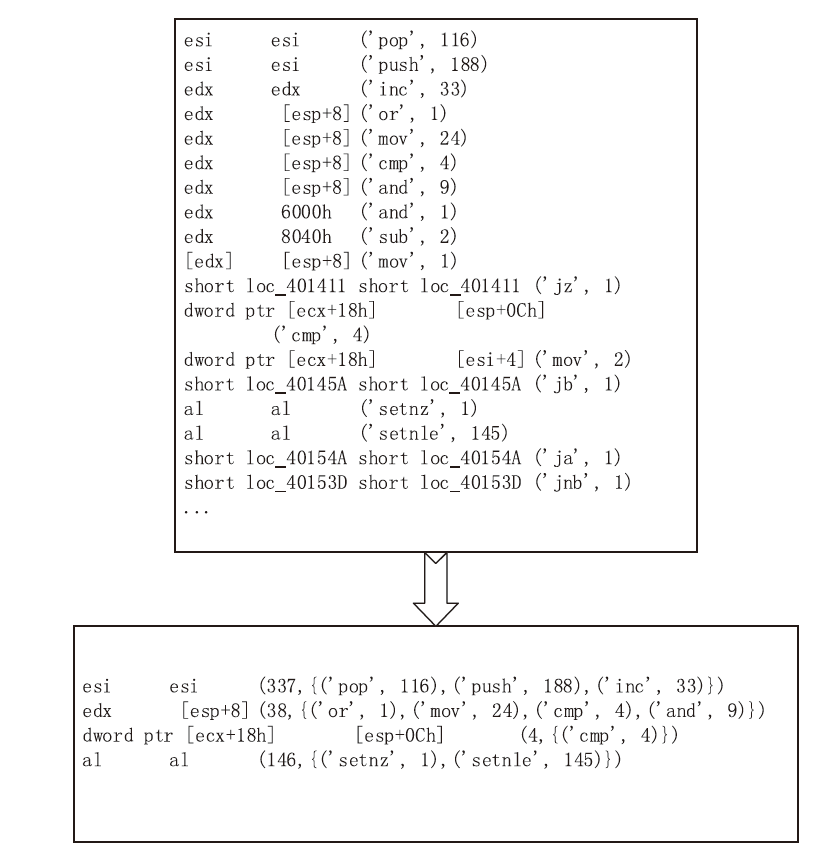
信息网络安全 ›› 2021, Vol. 21 ›› Issue (10): 54-62.doi: 10.3969/j.issn.1671-1122.2021.10.008
基于行为图谱筛的恶意代码可视化分类算法
- 1.中国电力科学研究院有限公司信息通信研究所,北京 100192
2.北京华夏信安科技有限公司,北京 100876
3.北京邮电大学移动互联网安全相关技术国家工程实验室,北京 100876
-
收稿日期:2021-06-25出版日期:2021-10-10发布日期:2021-10-14 -
通讯作者:林晴雯 E-mail:2019140856@bupt.edu.cn -
作者简介:朱朝阳(1974—),男,江西,正高级工程师,博士,主要研究方向为电力工控安全|周亮(1980—),男,湖北,高级工程师,博士,主要研究方向为电力系统信息安全|朱亚运(1990—),男,山西,高级工程师,博士,主要研究方向为电力工控安全|林晴雯(1997—),女,浙江,硕士研究生,主要研究方向为网络安全、软件安全 -
基金资助:国家电网公司总部科技项目(521304190004)
Malicious Code Visual Classification Algorithm Based on Behavior Knowledge Graph Sieve
ZHU Chaoyang1, ZHOU Liang1, ZHU Yayun1, LIN Qingwen2,3( )
)
- 1. Institute of Information and Communication, China Electric Power Research Institute Co., Ltd, Beijing 100192, China
2. Beijing HXIS Technology Co. Ltd, Beijing 100876, China
3. National Engineering Laboratory of Mobile Internet Security Technology, Beijing University of Posts and Telecommunications, Beijing 100876, China
-
Received:2021-06-25Online:2021-10-10Published:2021-10-14 -
Contact:LIN Qingwen E-mail:2019140856@bupt.edu.cn
摘要:
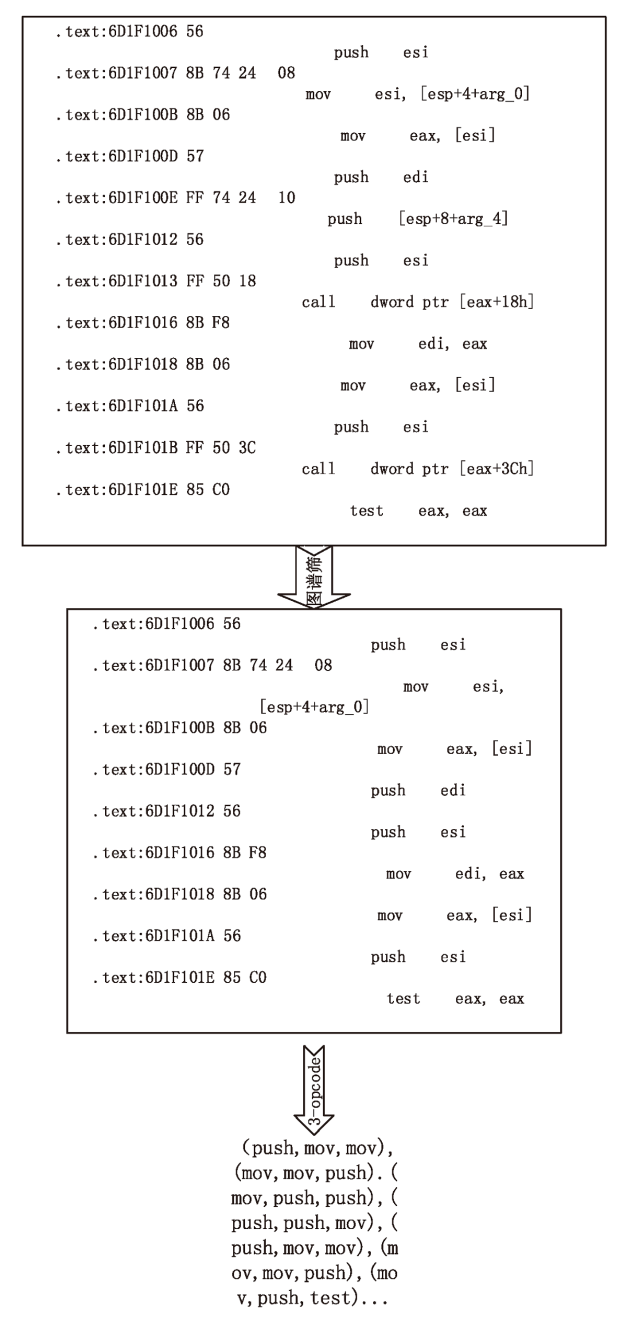
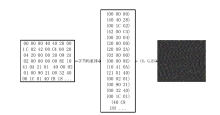
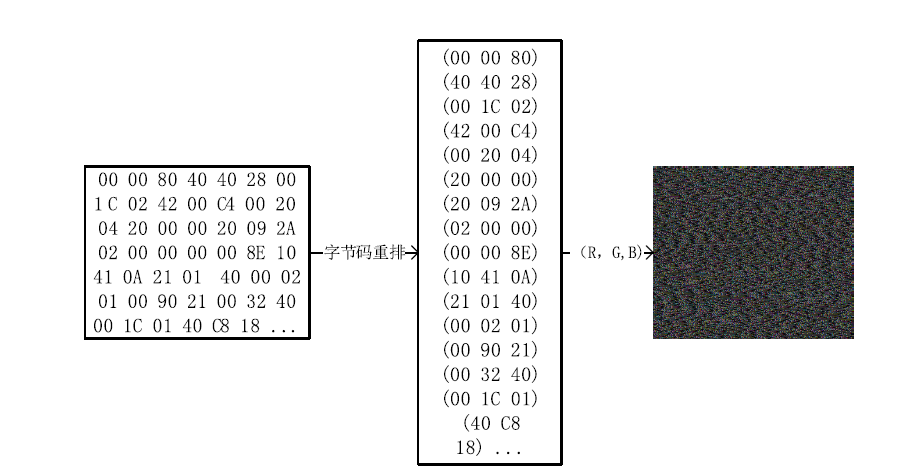
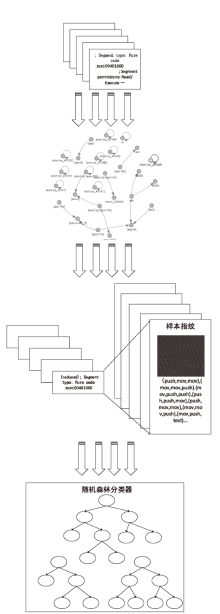
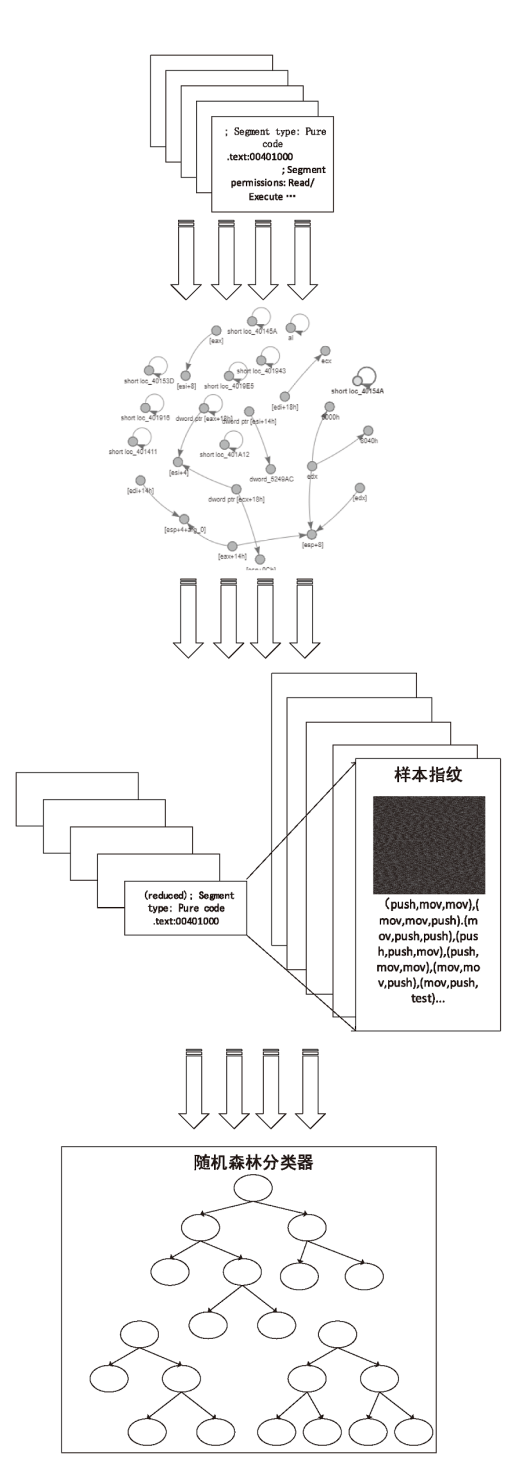
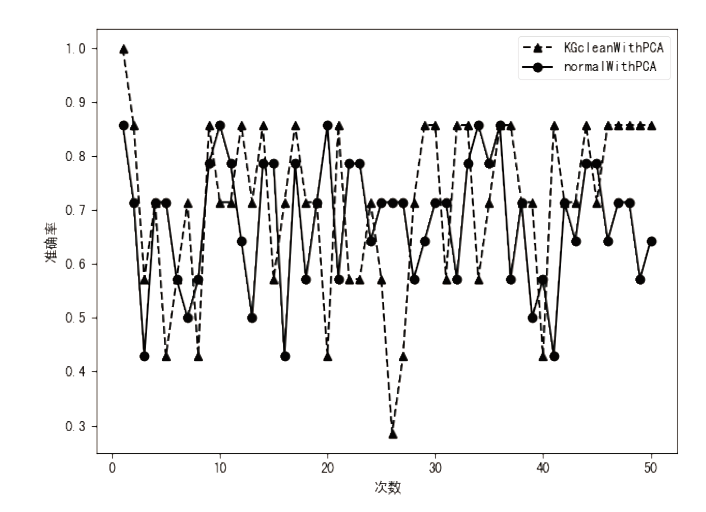
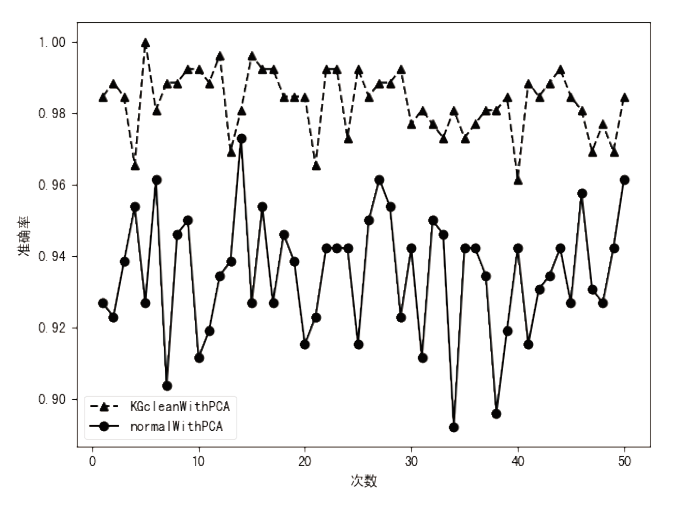
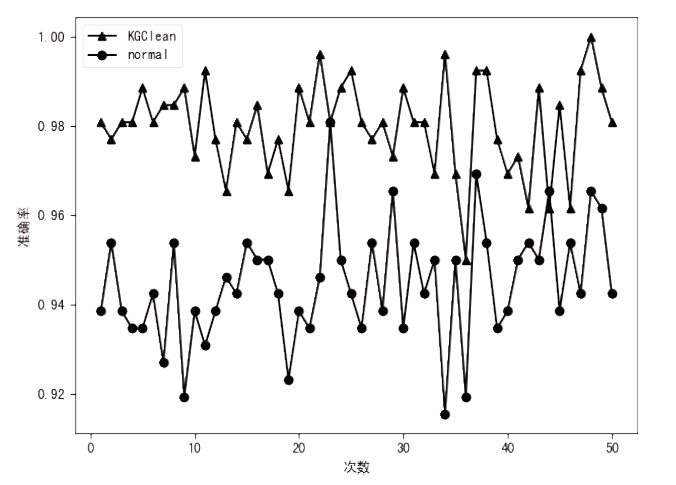
近年来,恶意病毒产业链逐渐形成一个组织良好的市场并涉及巨额的资金,反恶意软件面临的主要挑战是需要对大量的数据和文件样本进行评估,以确定潜在的恶意意图。基于此,文章提出了一种基于行为图谱筛的恶意代码可视化分类算法。该算法分析了恶意代码样本的汇编指令流,提取程序行为指纹,并利用知识图谱对指纹内容进行转义,从而生成指定样本的图谱筛。通过对图谱筛中的污点定位,该算法对恶意程序样本中的噪点进行清理,生成对应的筛后指纹。筛后指纹在保留原有指纹特征的前提下,达到了76.3%的压缩率。最后,该算法对筛后指纹进行了可视化分析和操作码序列分析,并利用随机森林算法进行分类工作,达到了98.8%的准确率。实验证明,基于行为图谱筛的恶意代码可视化分类算法,在恶意代码分类方面能达到更好的效果。
中图分类号:
引用本文
朱朝阳, 周亮, 朱亚运, 林晴雯. 基于行为图谱筛的恶意代码可视化分类算法[J]. 信息网络安全, 2021, 21(10): 54-62.
ZHU Chaoyang, ZHOU Liang, ZHU Yayun, LIN Qingwen. Malicious Code Visual Classification Algorithm Based on Behavior Knowledge Graph Sieve[J]. Netinfo Security, 2021, 21(10): 54-62.
| [1] | JI Tiantian, FANG Binxing, CUI Xiang, et al. Research Progress of Deep Learning Enabled Attack and Defense of Malicious Code[J]. Chinese Journal of Computers, 2021, 44(4):669-695. |
| 冀甜甜, 方滨兴, 崔翔, 等. 深度学习赋能的恶意代码攻防研究进展[J]. 计算机学报, 2021, 44(4):669-695. | |
| [2] | REN Zhuojun, CHEN Guang, LU Wenke. Research on Visualization Method of Malware Opcode[EB/OL]. http://kns.cnki.net/kcms/detail/11.2127.TP.20201126.0907.002.html, 2021-06-20. |
| 任卓君, 陈光, 卢文科. 恶意软件的操作码可视化方法研究[EB/OL]. http://kns.cnki.net/kcms/detail/11.2127.TP.20201126.0907.002.html, 2021-06-20. | |
| [3] | HE Tong, ZHANG Zhi, ZHANG Hang, et al. Bag of Tricks for Image Classification with Convolutional Neural Networks [C]//IEEE. 2019 IEEE/CVF Conference on Computer Vision and Pattern Recognition (CVPR), June 15-20, 2019, Long Beach, CA, USA. New York: IEEE, 2019: 558-567. |
| [4] | TAN Yang, LIU Jiayong, ZHANG Lei. Malware Family Classification of Deep Self Encoder Based on Mixed Features[J]. Information Network Security, 2020, 20(12):72-82. |
| 谭杨, 刘嘉勇, 张磊. 基于混合特征的深度自编码器的恶意软件家族分类[J]. 信息网络安全, 2020, 20(12):72-82. | |
| [5] | LIU Yashu, WANG Zhihai, HOU Yueran, et al. Visualization and Automatic Classification of Malicious Code with Enhanced Information Density[J]. Journal of Tsinghua University (Natural Science Edition), 2019, 59(1):9-14. |
| 刘亚姝, 王志海, 侯跃然, 等. 信息密度增强的恶意代码可视化与自动分类方法[J]. 清华大学学报(自然科学版), 2019, 59(1):9-14. | |
| [6] | ZENG Yaqin, ZHANG Linlin, ZHANG Ruonan, et al. Classification Model of Malware Family Based on Mobile Net[J]. Computer Engineering, 2020, 46(4):162-168. |
| 曾娅琴, 张琳琳, 张若楠, 等. 基于MobileNet的恶意软件家族分类模型[J]. 计算机工程, 2020, 46(4):162-168. | |
| [7] | RAMAN K. Selecting Features to Classify Malware[EB/OL]. https://2012.infosecsouthwest.com/files/speaker_materials/ISSW2012_Selecting_Features_to_Classify_Malware.pdf, 2021-06-01. |
| [8] | KIM C H, KABANGA E K, KANG S J. Classifying Malware Using Convolutional Gated Neural Network [C]//ICACT. 2018 20th International Conference on Advanced Communication Technology (ICACT), February 11-14, 2018, Chuncheon, Korea (South). New York: IEEE, 2018: 40-44. |
| [9] |
MA Xin, GUO Shize, LI Haiying, et al. How to Make Attention Mechanisms More Practical in Malware Classification[J]. IEEE Access, 2019, 7(10):155270-155280.
doi: 10.1109/Access.6287639 URL |
| [10] |
SHABTAI A, MOSKOVITCH R, FEHER C, et al. Detecting Unknown Malicious Code by Applying Classification Techniques on Opcode Patterns[J]. Security Informatics, 2012, 1(1):1-22.
doi: 10.1186/2190-8532-1-1 URL |
| [11] |
SUN Guosong, QIAN Quan. Deep Learning and Visualization for Identifying Malware Families[J]. IEEE Transactions on Dependable and Secure Computing, 2021, 18(1):283-295.
doi: 10.1109/TDSC.8858 URL |
| [12] |
ANDERSON B, QUIST D, NEIL J, et al. Graph-based Malware Detection Using Dynamic Analysis[J]. Journal in Computer Virology, 2011, 7(4):247-258.
doi: 10.1007/s11416-011-0152-x URL |
| [13] | KOLOSNJAJI B, DEMONTIS A, BIGGIO B, et al. Adversarial Malware Binaries: Evading Deep Learning for Malware Detection in Executables [C]//IEEE. 2018 26th European Signal Processing Conference (EUSIPCO), September 3-7, 2018, Rome, Italy. Italy: IEEE, 2018: 533-537. |
| [14] | LIU Weijie, ZHOU Peng, ZHAO Zhe, et al. K-bert: Enabling Language Representation with Knowledge Graph[EB/OL]. https://ojs.aaai.org/index.php/AAAI/article/view/5681, 2021-06-01. |
| [15] | KANG B J, YERIMA S Y, SEZER S, et al. N-gram Opcode Analysis for Android Malware Detection[EB/OL].https://arxiv.org/abs/1612.01445, 2021-06-01. |
| [16] | LUO J S, LO D C T. Binary Malware Image Classification Using Machine Learning with Local Binary Pattern [C]//IEEE. 2017 IEEE International Conference on Big Data (Big Data). December 11-14, 2017, Boston, MA, USA. New York: IEEE, 2017: 4664-4667. |
| [17] | NATARAJ L, KARTHIKEYAN S, JACOB G, et al. Malware Images: Visualization and Automatic Classification [C]//ACM. Proceedings of the 8th International Symposium on Visualization for Cyber Security (VizSec ’11), July 20, 2011, New York, USA. USA: Association for Computing Machinery, 2011: 1-7. |
| [18] | LU Xidong, DUAN Zhemin, QIAN yekui, et al. A Malicious Code Classification Method Based on Deep Forest[J]. Journal of Software, 2020, 31(5):1454-1464. |
| 卢喜东, 段哲民, 钱叶魁, 等. 一种基于深度森林的恶意代码分类方法[J]. 软件学报, 2020, 31(5):1454-1464. |
| [1] | 刘红, 谢永恒, 王国威, 蒋帅. 基于跨领域本体的信息安全分析[J]. 信息网络安全, 2020, 20(9): 82-86. |
| [2] | 陶源, 黄涛, 李末岩, 胡巍. 基于知识图谱驱动的网络安全等级保护日志审计分析模型研究[J]. 信息网络安全, 2020, 20(1): 46-51. |
| [3] | 高孟茹, 谢方军, 董红琴, 林祥. 面向关键信息基础设施的网络安全评价体系研究[J]. 信息网络安全, 2019, 19(9): 111-114. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||