信息网络安全 ›› 2023, Vol. 23 ›› Issue (3): 1-12.doi: 10.3969/j.issn.1671-1122.2023.03.001
工业物联网环境下可外包的策略隐藏属性基加密方案
- 1.西安邮电大学网络空间安全学院,西安 710121
2.西安邮电大学无线网络安全技术国家工程实验室,西安 710121
-
收稿日期:2022-10-27出版日期:2023-03-10发布日期:2023-03-14 -
通讯作者:魏鑫 E-mail:weixin1128211@163.com -
作者简介:郭瑞(1984—),男,河南,副教授,博士,主要研究方向为属性基加密、云计算及区块链安全|魏鑫(1997—),男,陕西,硕士研究生,主要研究方向为属性基加密、区块链|陈丽(1996—),女,江苏,硕士研究生,主要研究方向为属性基加密、区块链技术 -
基金资助:国家自然科学基金(62072369);陕西省重点研发计划(2020ZDLGY08-04);陕西省创新能力支持计划(2020KJXX-052)
An Outsourceable and Policy-Hidden Attribute-Based Encryption Scheme in the IIoT System
GUO Rui1,2, WEI Xin1,2( ), CHEN Li1,2
), CHEN Li1,2
- 1. School of Cyberspace Security, Xi’an University of Posts and Telecommunications, Xi’an 710121, China
2. National Engineering Laboratory for Wireless Security, Xi’an University of Posts and Telecommunications, Xi’an 710121, China
-
Received:2022-10-27Online:2023-03-10Published:2023-03-14 -
Contact:WEI Xin E-mail:weixin1128211@163.com
摘要:
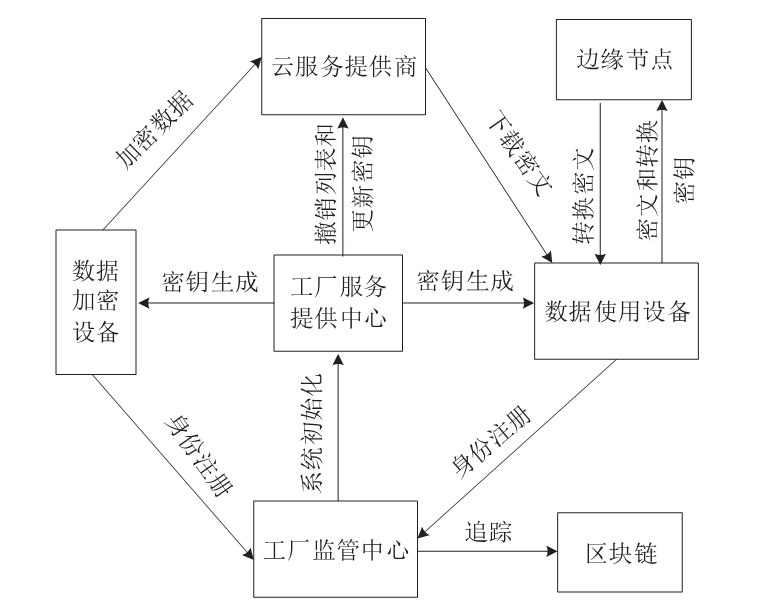
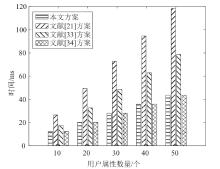
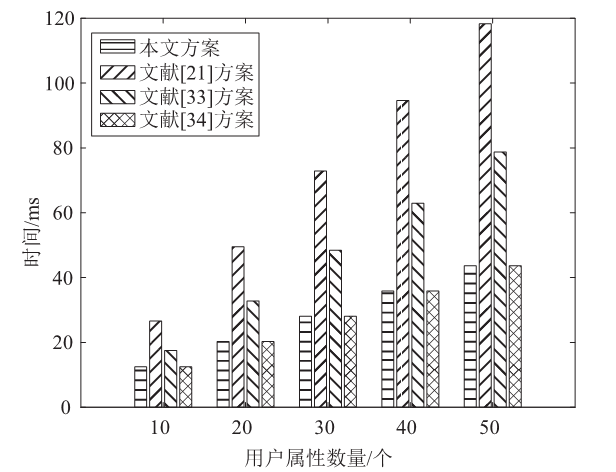
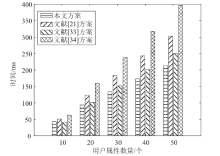
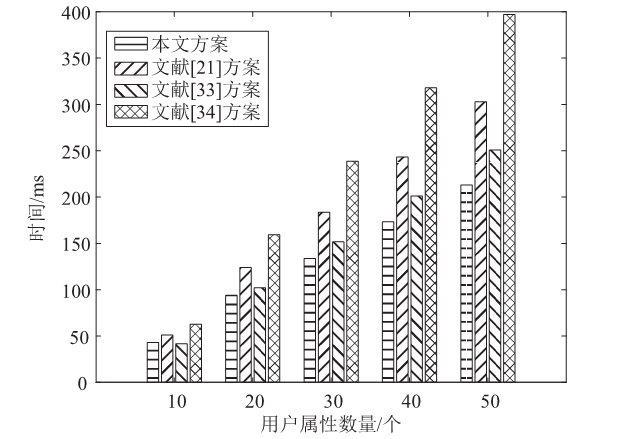
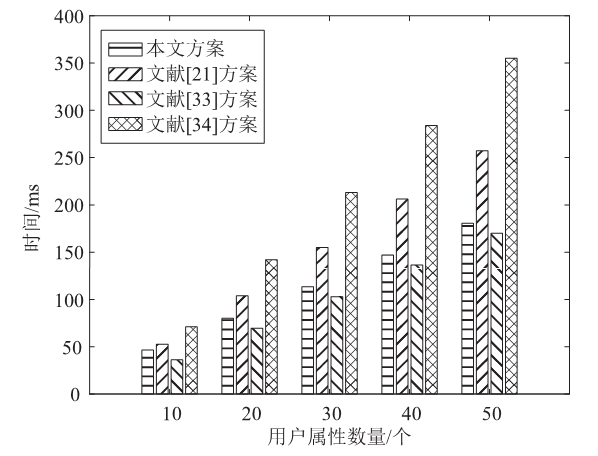
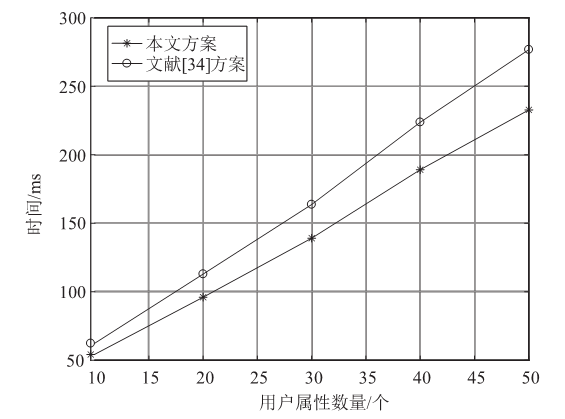
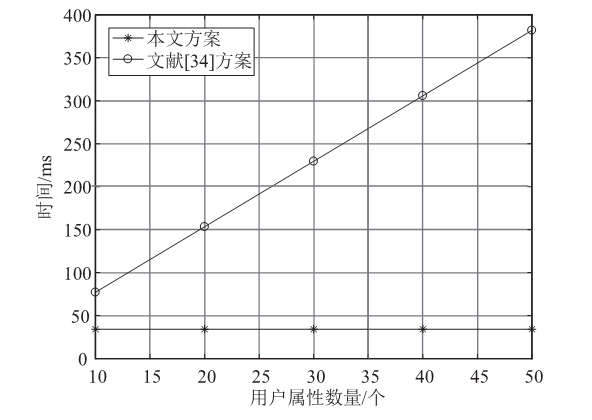
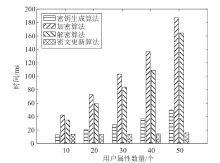
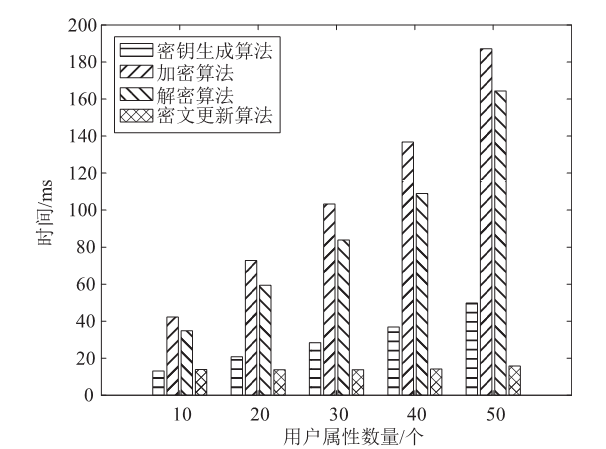
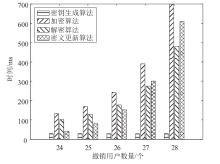
针对工业物联网环境下数据访问控制方案存在解密设备计算负担过重,无法保护解密设备隐私信息,以及不能追踪恶意设备等问题,文章提出一种工业物联网环境下可外包的策略隐藏属性基加密方案。该方案借助边缘计算技术将海量工业数据的大部分解密操作外包给边缘计算节点,极大减轻了解密设备的计算负担。该方案将属性基加密中的访问结构进行拆分,引入策略隐藏技术,在实现工业数据机密性的同时保护解密设备的隐私信息。此外,文章利用区块链技术对系统内设备进行监管和审计。安全性分析表明,该方案在选择明文攻击下是安全的。文章在PBC密码库和Hyperledger Fabric区块链平台上将该方案与同类方案进行模拟仿真,结果表明,该方案具有较高的计算效率,适用于工业物联网环境。
中图分类号:
引用本文
郭瑞, 魏鑫, 陈丽. 工业物联网环境下可外包的策略隐藏属性基加密方案[J]. 信息网络安全, 2023, 23(3): 1-12.
GUO Rui, WEI Xin, CHEN Li. An Outsourceable and Policy-Hidden Attribute-Based Encryption Scheme in the IIoT System[J]. Netinfo Security, 2023, 23(3): 1-12.
表3
计算开销
| 文献[21]方案 | 文献[33]方案 | |
|---|---|---|
| 密钥生成 | ||
| 加密 | ||
| 解密 | ||
| 外包解密 | — | — |
| 追踪 | — | |
| 密文更新 | — | — |
| 文献[34]方案 | 本文方案 | |
| 密钥生成 | ||
| 加密 | ||
| 解密 | ||
| 外包解密 | ||
| 追踪 | ||
| 密文更新 |
| [1] |
SISINNI E, SAIFULLAH A, HAN S, et al. Industrial Internet of Things: Challenges Opportunities and Directions[J]. IEEE Transactions on Industrial Informatics, 2018, 14(11): 4724-4734.
doi: 10.1109/TII.2018.2852491 URL |
| [2] |
BANERJEE S, BERA B, DAS A K, et al. Private Blockchain-Envisioned Multi-Authority CP-ABE-Based User Access Control Scheme in IIoT[J]. Computer Communications, 2021, 169: 99-113.
doi: 10.1016/j.comcom.2021.01.023 URL |
| [3] | KARMAKAR A, DEY N, BARAL T, et al. Industrial Internet of Things: A Review[C]// IEEE. 2019 International Conference on Opto-Electronics and Applied Optics(Optronix). New York: IEEE. 2019: 1-6. |
| [4] |
ZHENG Dong, ZHU Tianze, GUO Rui. Public Key Searchable Encryption Scheme in Blockchain-Enabled Multi-User Environment[J]. Journal on Communications, 2021, 42(10): 140-152.
doi: 10.11959/j.issn.1000-436x.2021130 |
|
郑东, 朱天泽, 郭瑞. 基于区块链的多用户环境中公钥可搜索加密方案[J]. 通信学报, 2021, 42(10):140-152.
doi: 10.11959/j.issn.1000-436x.2021130 |
|
| [5] |
WAN Jiafu, LI Jiapeng, IMRAN M, et al. A Blockchain-Based Solution for Enhancing Security and Privacy in Smart Factory[J]. IEEE Transactions on Industrial Informatics, 2019, 15(6): 3652-3660.
doi: 10.1109/TII.9424 URL |
| [6] |
YU Keping, TAN Liang, ALOQAILY M, et al. Blockchain-Enhanced Data Sharing with Traceable and Direct Revocation in IIoT[J]. IEEE Transactions on Industrial Informatics, 2021, 17(11): 7669-7678.
doi: 10.1109/TII.2021.3049141 URL |
| [7] | SAHAI A, WATERS B. Fuzzy Identity-Based Encryption[C]// Springer. EUROCRYPT 2005. Heidelberg: Springer, 2005: 457-473. |
| [8] | BETHENCOURT J, SAHAI A, WATERS B. Ciphertext-Policy Attribute-Based Encryption[C]// IEEE. 2007 IEEE Symposium on Security and Privacy. New York: IEEE, 2007: 321-334. |
| [9] | GOYAL V, PANDEY O, SAHAI A, et al. Attribute-Based Encryption for Fine-Grained Access Control Of Encrypted Data[C]// ACM. 13th ACM Conference on Computer and Communications Security. New York: ACM, 2006: 89-98. |
| [10] |
LI Yixin, ZHANG Yinghui, HU Lingyun, et al. Fine-Grained Bilateral Access Control Scheme in Online Consultation Environment[J]. Computer Engineering and Applications, 2022, 58(17): 139-147.
doi: 10.3778/j.issn.1002-8331.2106-0033 |
|
李艺昕, 张应辉, 胡凌云, 等. 在线问诊环境下细粒度双边访问控制方案[J]. 计算机工程与应用, 2022, 58(17):139-147.
doi: 10.3778/j.issn.1002-8331.2106-0033 |
|
| [11] |
WU Jingwen, YIN Xinchun, NING Jianting. Traceable and Revocable Multi-Authority Attribute-Based Encryption Scheme for Vehicular Ad Hoc Networks[J]. Journal of Computer Applications, 2022, 42(6): 1695-1701.
doi: 10.11772/j.issn.1001-9081.2021061449 |
|
吴静雯, 殷新春, 宁建廷. 车载自组网中可追踪可撤销的多授权中心属性基加密方案[J]. 计算机应用, 2022, 42(6):1695-1701.
doi: 10.11772/j.issn.1001-9081.2021061449 |
|
| [12] |
HAN Dezhi, PAN Nannan, LI K C. A Traceable and Revocable Ciphertext-Policy Attribute-based Encryption Scheme Based on Privacy Protection[J]. IEEE Transactions on Dependable and Secure Computing, 2022, 19(1): 316-327.
doi: 10.1109/TDSC.2020.2977646 URL |
| [13] | NING Jianting, CAO Zhenfu, DONG Xiaolei, et al. Large Universe Ciphertext-Policy Attribute-Based Encryption with White-Box Traceability[C]// Springer. Computer Security-ESORICS 2014. Heidelberg: Springer, 2014: 55-72. |
| [14] | CHEUNG L, NEWPORT C. Provably Secure Ciphertext Policy ABE[C]// ACM. 14th ACM Conference on Computer and Communications Security. New York: ACM, 2007: 456-465. |
| [15] | BEIMEL A. Secure Schemes for Secret Sharing and Key Distribution[D]. Haifa: Israel Institute of Technology, 1996. |
| [16] | ZHANG Yinghui, DENG R H, XU Shengmin, et al. Attribute-Based Encryption for Cloud Computing Access Control: A Survey[J]. Association for Computing Machinery, 2020, 53(4): 1-41. |
| [17] | ZHANG Yunru, HE Debiao, CHOO K K R. BaDS: Blockchain-Based Architecture for Data Sharing with ABS and CP-ABE in IoT[J]. Wireless Communications and Mobile Computing, 2018(2): 1-9. |
| [18] |
GUO Lifeng, YANG Xiaoli, YAU W C. TABE-DAC: Efficient Traceable Attribute-Based Encryption Scheme with Dynamic Access Control Based on Blockchain[J]. IEEE Access, 2019, 9: 8479-8490.
doi: 10.1109/Access.6287639 URL |
| [19] | LIU Zechao, WANG Xuan, CUI Lei, et al. White-Box Traceable Dynamic Attribute Based Encryption[C]// IEEE. 2017 International Conference on Security, Pattern Analysis, and Cybernetics(SPAC). New York: IEEE, 2017: 526-530. |
| [20] |
LAI Junzuo, DENG R H, GUAN Chaowen, et al. Attribute-Based Encryption with Verifiable Outsourced Decryption[J]. IEEE Transactions on Information Forensics and Security, 2013, 8(8): 1343-1354.
doi: 10.1109/TIFS.2013.2271848 URL |
| [21] |
ZHANG Yinghui, ZHENG Dong, DENG R H. Security and Privacy in Smart Health: Efficient Policy-Hiding Attribute-Based Access Control[J]. IEEE Internet of Things Journal, 2018, 5(3): 2130-2145.
doi: 10.1109/JIOT.2018.2825289 URL |
| [22] |
LIU Zhenhua, XU Jing, LIU Yan, et al. Updatable Ciphertext-Policy Attribute-Based Encryption Scheme with Traceability and Revocability[J]. IEEE Access, 2019, 7: 66832-66844.
doi: 10.1109/ACCESS.2019.2918434 |
| [23] | PAN Jingwen, CUI Jie, WEI Lu, et al. Secure Data Sharing Scheme for VANETs Based on Edge Computing[J]. EURASIP Journal on Wireless Communications and Networking, 2019(1): 1-11. |
| [24] |
CUI Hui, YI Xun, NEPAL S. Achieving Scalable Access Control over Encrypted Data for Edge Computing Networks[J]. IEEE Access, 2018, 6: 30049-30059.
doi: 10.1109/Access.6287639 URL |
| [25] |
ZHANG Peng, CHEN Zehong, LIU J K, et al. An Efficient Access Control Scheme with Outsourcing Capability and Attribute Update for Fog Computing[J]. Future Generation Computer Systems, 2018, 78: 753-762.
doi: 10.1016/j.future.2016.12.015 URL |
| [26] |
ZUO Cong, SHAO Jun, WEI Guiyi, et al. CCA-Secure ABE with Outsourced Decryption for Fog Computing[J]. Future Generation Computer Systems, 2018, 78: 730-738.
doi: 10.1016/j.future.2016.10.028 URL |
| [27] |
LIU C H, LIN Qiuxia, WEN Shilin. Blockchain-Enabled Data Collection and Sharing for Industrial IoT with Deep Reinforcement Learning[J]. IEEE Transactions on Industrial Informatics, 2019, 15(6): 3516-3526.
doi: 10.1109/TII.9424 URL |
| [28] |
HUANG Junqin, KONG Linghe, CHEN Guihai, et al. Towards Secure Industrial IoT: Blockchain System with Credit-Based Consensus Mechanism[J]. IEEE Transactions on Industrial Informatics, 2019, 15(6): 3680-3689.
doi: 10.1109/TII.9424 URL |
| [29] | TESLYA N, RYABCHIKOV I. Blockchain-Based Platform Architecture for Industrial IoT[C]// IEEE. 21st Conference of Open Innovations Association(FRUCT). New York:IEEE, 2017: 321-329. |
| [30] | ROUSELAKIS Y, WATERS B. Practical Constuctions and New Proof Methods for Large Universe Attribute-Based Encryption[C]// ACM. 2013 ACM SIGSAC Conference on Computer & Communications Security. New York: ACM, 2013: 463-474. |
| [31] |
GOLDWASSER S, MICALI S. Probabilistic Encryption[J]. Journal of Computer and System Science, 1984, 28(2): 270-299.
doi: 10.1016/0022-0000(84)90070-9 URL |
| [32] | ZHUANG Chaoyuan, GUO Rui, YANG Geng. Anonymous Attribute-Based Encryption Scheme with Verifiable Outsourcing Decryption in Blockchain[J] Journal of Computer Applications, 2022, 58(19): 124-134. |
|
庄朝源, 郭瑞, 杨耿. 区块链中可验证外包解密的匿名属性加密方案[J]. 计算机工程与应用, 2022, 58(19):124-134.
doi: 10.3778/j.issn.1002-8331.2107-0487 |
|
| [33] |
LI Jiguo, YAO Wei, HAN Jinguang, et al. User Collusion Avoidance CP-ABE with Efficient Attribute Revocation for Cloud Storage[J]. IEEE Systems Journal, 2018, 12(2): 1767-1777.
doi: 10.1109/JSYST.4267003 URL |
| [34] |
SETHI K, PRADHAN A, BERA P. PMTER-ABE: A Practical Multi-Authority CP-ABE with Traceability, Revocation and Outsourcing Decryption for Secure Access Control in Cloud Systems[J]. Cluster Computing, 2021, 24: 1-26.
doi: 10.1007/s10586-020-03165-4 |
| [1] | 李春晓, 王耀飞, 徐恩亮, 赵钰. 基于双线性映射的区块链安全范围搜索技术研究[J]. 信息网络安全, 2023, 23(3): 22-34. |
| [2] | 李晓华, 王苏杭, 李凯, 徐剑. 一种支持隐私保护的传染病人际传播分析模型[J]. 信息网络安全, 2023, 23(3): 35-44. |
| [3] | 张学旺, 张豪, 姚亚宁, 付佳丽. 基于群签名和同态加密的联盟链隐私保护方案[J]. 信息网络安全, 2023, 23(3): 56-61. |
| [4] | 王晶宇, 马兆丰, 徐单恒, 段鹏飞. 支持国密算法的区块链交易数据隐私保护方案[J]. 信息网络安全, 2023, 23(3): 84-95. |
| [5] | 冯怡婷, 马兆丰, 徐单恒, 段鹏飞. 跨链接入的区块链安全强度评估方法[J]. 信息网络安全, 2023, 23(1): 84-92. |
| [6] | 于晶, 袁曙光, 袁煜琳, 陈驰. 基于k匿名数据集的鲁棒性水印技术研究[J]. 信息网络安全, 2022, 22(9): 11-20. |
| [7] | 张光华, 刘永升, 王鹤, 于乃文. 基于BiLSTM和注意力机制的智能合约漏洞检测方案[J]. 信息网络安全, 2022, 22(9): 46-54. |
| [8] | 张学旺, 刘宇帆. 可追踪身份的物联网感知层节点匿名认证方案[J]. 信息网络安全, 2022, 22(9): 55-62. |
| [9] | 胡艺, 佘堃. 基于区块链和智能合约的双链车联网系统[J]. 信息网络安全, 2022, 22(8): 26-35. |
| [10] | 黄保华, 赵伟宏, 彭丽, 谢统义. 基于MPT索引的高效链上PKI模型[J]. 信息网络安全, 2022, 22(8): 72-80. |
| [11] | KELEKET GOMA Christy Junior Yannick, 易文哲, 王鹃. 一种基于SGX的轻量Fabric链码可信执行环境构建方法[J]. 信息网络安全, 2022, 22(7): 73-83. |
| [12] | 秦宝东, 余沛航, 郑东. 基于双陷门同态加密的决策树分类模型[J]. 信息网络安全, 2022, 22(7): 9-17. |
| [13] | 王姝爽, 马兆丰, 刘嘉微, 罗守山. 区块链跨链安全接入与身份认证方案研究与实现[J]. 信息网络安全, 2022, 22(6): 61-72. |
| [14] | 于克辰, 郭莉, 阴宏伟, 燕雪松. 面向数据中心场景的基于区块链与博弈论的高价值数据共享模型[J]. 信息网络安全, 2022, 22(6): 73-85. |
| [15] | 冯景瑜, 张琪, 黄文华, 韩刚. 基于跨链交互的网络安全威胁情报共享方案[J]. 信息网络安全, 2022, 22(5): 21-29. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||