信息网络安全 ›› 2023, Vol. 23 ›› Issue (1): 73-83.doi: 10.3969/j.issn.1671-1122.2023.01.009
基于图注意力网络的DNS隐蔽信道检测
- 1.国防科技大学电子对抗学院,合肥 230037
2.网络空间安全态势感知与评估安徽省重点实验室,合肥 230037
-
收稿日期:2022-06-13出版日期:2023-01-10发布日期:2023-01-19 -
通讯作者:王永杰 E-mail:wangyongjie17@nudt.edu.cn -
作者简介:沈传鑫(1996—),男,山东,硕士研究生,主要研究方向为网络空间安全|王永杰(1974—),男,河南,教授,博士,主要研究方向为网络安全建模与仿真、网络空间安全|熊鑫立(1991—),男,北京,讲师,博士,主要研究方向为移动目标防御
DNS Covert Channel Detection Based on Graph Attention Network
SHEN Chuanxin1,2, WANG Yongjie1,2( ), XIONG Xinli1,2
), XIONG Xinli1,2
- 1. College of Electronic Engineering, National University of Defense Technology, Hefei 230037, China
2. Anhui Province Key Laboratory of Cyberspace Security Situation Awareness and Evaluation, Hefei 230037, China
-
Received:2022-06-13Online:2023-01-10Published:2023-01-19 -
Contact:WANG Yongjie E-mail:wangyongjie17@nudt.edu.cn
摘要:
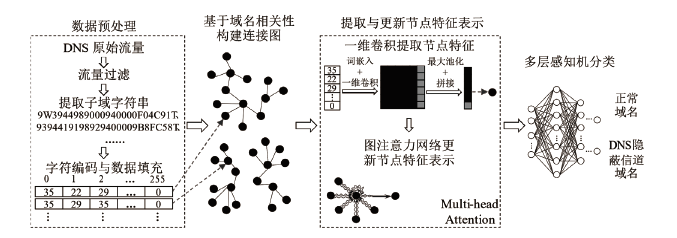
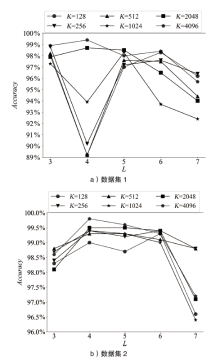
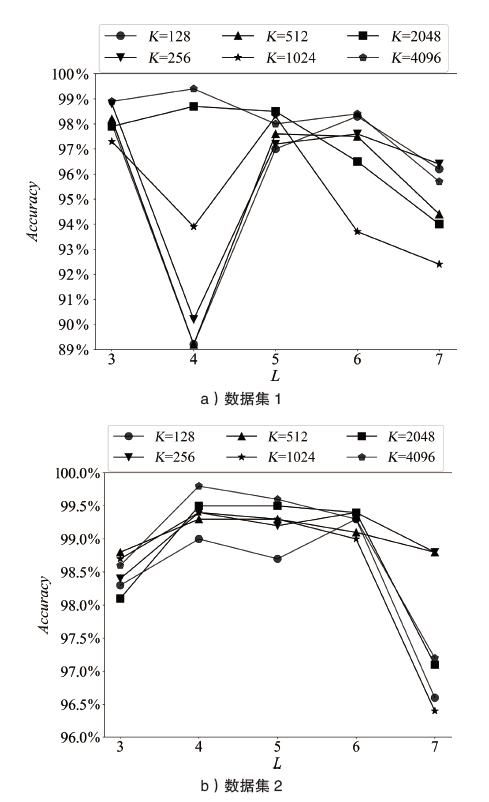
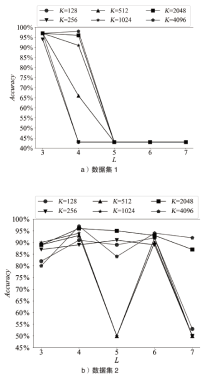
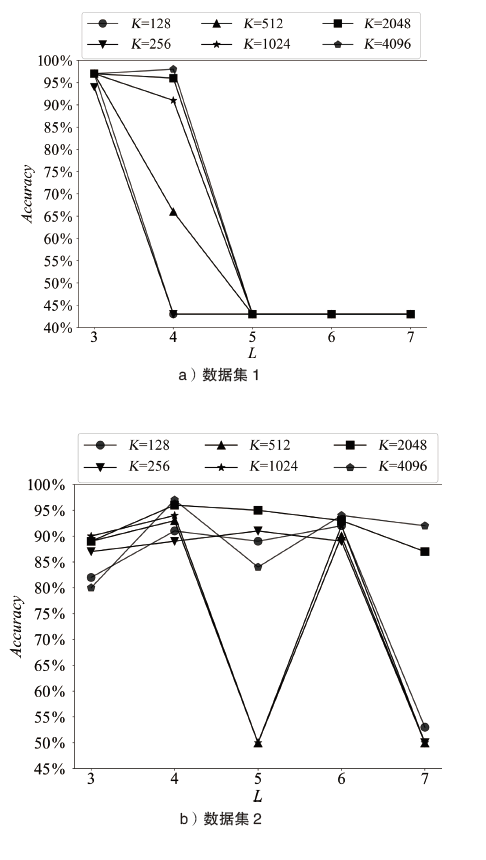
域名系统(Domain Name System,DNS)隐蔽信道在高级持续性威胁 (Advanced Persistent Threat,APT)攻击中呈频发态势,对网络空间安全具有潜在威胁。文章提出基于域名语义表示(Domain Semantic Representation,DSR)和图注意力网络(Graph Attention Network,GAT)的DNS隐蔽信道检测方法DSR-GAT,将域名级别的DNS隐蔽信道检测转化为一种无向图的节点分类任务。首先基于域名的相关性采用无向图构建域名图(Domain Graph,DG);然后利用域名的文本数据属性,采用一维卷积神经网络提取的语义表示作为DG节点的特征表示;最后通过图注意力网络的消息传播机制及多头自注意力机制,增强每个域名的特征表示。在公开数据集与基于真实APT样本Glimpse的自建数据集上进行实验,实验结果表明,文章提出的DSR-GAT方法检测效果较好,在解决上述问题的同时降低了漏报率,在一定程度上减小了安全风险。
中图分类号:
引用本文
沈传鑫, 王永杰, 熊鑫立. 基于图注意力网络的DNS隐蔽信道检测[J]. 信息网络安全, 2023, 23(1): 73-83.
SHEN Chuanxin, WANG Yongjie, XIONG Xinli. DNS Covert Channel Detection Based on Graph Attention Network[J]. Netinfo Security, 2023, 23(1): 73-83.
| [1] | WANG Wentong, HU Ning, LIU Bo, et al. A Survey on Technology of Security Enhancement for DNS[J]. Journal of Software, 2020, 31(7): 2205-2220. |
| 王文通, 胡宁, 刘波, 等. DNS安全防护技术研究综述[J]. 软件学报, 2020, 31(7): 2205-2220. | |
| [2] | 360 Advanced Threat Institute. 2020 Global Advanced Persistent Threat APT Research Report[EB/OL]. (2021-02-07)[2022-04-13]. https://www.sohu.com/a/449213257653604. |
| 360高级威胁研究院. 2020全球高级持续性威胁APT研究报告[EB/OL]. (2021-02-07)[2022-04-13]. https://www.sohu.com/a/449213257653604. | |
| [3] | FALCONE R. DNS Tunneling in the Wild: Overview of OilRig's DNS Tunneling[EB/OL]. (2019-04-16)[2022-04-13]. https://unit42.paloaltonetworks.com/dns-tunneling-in-the-wild-overview-of-oilrigs-dns-tunneling/. |
| [4] | AHMED J, GHARAKHEILI H H, RAZA Q, et al. Real-Time Detection of DNS Exfiltration and Tunneling from Enterprise Networks[C]// IEEE. 2019 IFIP/IEEE Symposium on Integrated Network and Service Management (IM). New York: IEEE, 2019: 649-653. |
| [5] | WU Kemeng, ZHANG Yongzheng, YIN Tao. TDAE: Autoencoder-Based Automatic Feature Learning Method for the Detection of DNS Tunnel[C]// IEEE. ICC 2020 IEEE International Conference on Communications (ICC). New York: IEEE, 2020: 215-223. |
| [6] | CHOWDHARY A, BHOWMIK M, RUDRA B. DNS Tunneling Detection Using Machine Learning and Cache Miss Properties[C]// IEEE. 5th International Conference on Intelligent Computing and Control Systems (ICICCS 2021). New York: IEEE, 2021: 633-645. |
| [7] | BORN K, GUSTAFSON D. Detecting DNS Tunnels Using Character Frequency Analysis[EB/OL]. (2010-04-25)[2022-05-13]. https://arxiv.org/abs/1004.4358. |
| [8] |
QI Cheng, CHEN Xiaojun, XU Cui, et al. A Bigram Based Real Time DNS Tunnel Detection Approach[J]. Procedia Computer Science, 2013, 17: 852-860.
doi: 10.1016/j.procs.2013.05.109 URL |
| [9] | WU Kemeng, ZHANG Yongzheng, YIN Tao. FTPB: A Three-Stage DNS Tunnel Detection Method Based on Character Feature Extraction[C]// IEEE. 2020 IEEE 19th International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom). New York: IEEE, 2020: 552-563. |
| [10] |
YANG Peng, WAN Xinxin, GUANG Shi, et al. Identification of DNS Covert Channel Based on Stacking Method[J]. International Journal of Computer and Communication Engineering, 2021, 10(2): 1-15.
doi: 10.17706/IJCCE.2021.10.1.1-8 URL |
| [11] | ZHANG Jiacheng, LI Yang, YU Shui, et al. A DNS Tunneling Detection Method Based on Deep Learning Models to Prevent Data Exfiltration[M]. Berlin: Springer, 2019. |
| [12] | LIU Chang, DAI Liang, CUI Wenjing, et al. A Byte-Level CNN Method to Detect DNS Tunnels[C]// IEEE. 2019 IEEE 38th International Performance Computing and Communications Conference (IPCCC). New York: IEEE, 2019: 1-8. |
| [13] |
SPERDUTI A, STARITA A. Supervised Neural Networks for the Classification of Structures[J]. IEEE Transactions on Neural Networks, 1997, 8(3): 714-735.
pmid: 18255672 |
| [14] | GORI M, MONFARDINI G, SCARSELLI F. A New Model for Learning in Graph Domains[J]. Joint Conference on Neural Networks, 2005(2): 729-734. |
| [15] | JIA Zhuosheng, HAN Zhen. Research and Analysis of User Behavior Fingerprint on Security Situational Awareness Based on DNS Log[C]// IEEE. 2019 6th International Conference on Behavioral, Economic and Socio-Cultural Computing (BESC). New York: IEEE, 2019: 1-4. |
| [16] | SUN Xiaoqing, WANG Zhiliang, YANG Jiahai, et al. Deepdom: Malicious Domain Detection with Scalable and Heterogeneous Graph Convolutional Networks[EB/OL]. (2020-12-01)[2022-04-13]. https://www.sciencedirect.com/science/article/pii/S0167404820303308. |
| [17] | VELICKOVIC P, CUCURULL G, CASANOVA A, et al. Graph Attention Networks[EB/OL]. (2017-02-04)[2022-04-13]. https://www.semanticscholar.org/reader/33998aff64ce51df8dee45989cdca4b6b1329ec4. |
| [18] | WANG Yue, ZHOU Anmin, LIAO Shan, et al. A Comprehensive Survey on DNS Tunnel Detection[J]. Computer Networks, 2021, 197(3): 108-122. |
| [19] | CHEN Shaojie, LANG Bo, LIU Hongyu, et al. DNS Covert Channel Detection Method Using the LSTM Model[EB/OL]. (2021-05-21)[2022-04-13]. https://www.sciencedirect.com/science/article/pii/S0167404820303680. |
| [20] | Stratosphere. Stratosphere Laboratory Datasets[EB/OL]. (2020-03-13)[2022-04-13]. https://www.stratosphereips.org/datasets-normal. |
| [21] | ALENAZI A, TRAORE I, GANAME K, et al. Holistic Model for HTTP Botnet Detection Based on DNS Traffic Analysis[EB/OL]. (2017-10-11)[2022-04-13]. https://link.springer.com/chapter/10.1007/978-3-319-69155-8_1. |
| [1] | 李元诚, 罗昊, 王庆乐, 李建彬. 一种基于ATT&CK的新型电力系统APT攻击建模[J]. 信息网络安全, 2023, 23(2): 26-34. |
| [2] | 张郅, 李欣, 叶乃夫, 胡凯茜. 融合多重风格迁移和对抗样本技术的验证码安全性增强方法[J]. 信息网络安全, 2022, 22(10): 129-135. |
| [3] | 邓凯, 田志宏, 马丹阳. 一种基于wirehair码的高可靠分布式存储方案的研究与实现[J]. 信息网络安全, 2018, 18(2): 20-26. |
| [4] | 王玉辉, 曾泽华, 沈嘉荟, 符天枢. 基于APT逻辑的恐怖事件因果关系分析[J]. 信息网络安全, 2017, 17(9): 93-97. |
| [5] | 张家伟, 张冬梅, 黄偲琪. 一种抗APT攻击的可信软件基设计与实现[J]. 信息网络安全, 2017, 17(6): 49-55. |
| [6] | 程三军, 王宇. APT攻击原理及防护技术分析[J]. 信息网络安全, 2016, 16(9): 118-123. |
| [7] | 谈诚, 邓入弋, 王丽娜, 马婧. 针对APT攻击中恶意USB存储设备的防护方案研究[J]. 信息网络安全, 2016, 16(2): 7-8. |
| [8] | 陈晨, 王奕钧, 胡光俊, 郭燕慧. 针对手机的APT攻击方式的研究[J]. 信息网络安全, 2015, 15(3): 33-37. |
| [9] | 李凤海, 李爽, 张佰龙, 宋衍. 高等级安全网络抗APT攻击方案研究[J]. 信息网络安全, 2014, 14(9): 109-114. |
| [10] | . 基于虚拟机与API调用监控技术的APT木马取证研究[J]. , 2014, 14(4): 78-. |
| [11] | 权乐;高姝;徐松. APT攻击行动研究[J]. , 2013, 13(4): 0-0. |
| [12] | 翟立东;李跃;贾召鹏;郭莉. 融合网络空间的APT威胁检测与防护[J]. , 2013, 13(3): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||