信息网络安全 ›› 2022, Vol. 22 ›› Issue (11): 62-67.doi: 10.3969/j.issn.1671-1122.2022.11.008
虚拟化平台异常行为检测系统的设计与实现
- 1. 南开大学网络空间安全学院,天津 300350
2. 天津市网络与数据安全技术重点实验室,天津 300350
-
收稿日期:2022-07-10出版日期:2022-11-10发布日期:2022-11-16 -
通讯作者:张健 E-mail:zhang.jian@nankai.edu.cn -
作者简介:林发鑫(1999—),男,河南,硕士研究生,主要研究方向为网络安全|张健(1968—),男,天津,正高级工程师,博士,主要研究方向为云安全、网络安全、系统安全 -
基金资助:国家重点研发计划(2021YFF0307202);天津市新一代人工智能科技重大专项(19ZXZNGX00090);天津市重点研发计划(20YFZCGX00680)
Design and Implementation of Abnormal Behavior Detection System for Virtualization Platform
- 1. College of Cyber Science, Nankai University, Tianjin 300350, China
2. Tianjin Key Laboratory of Network and Data Security Technology, Tianjin 300350, China
-
Received:2022-07-10Online:2022-11-10Published:2022-11-16 -
Contact:ZHANG Jian E-mail:zhang.jian@nankai.edu.cn
摘要:
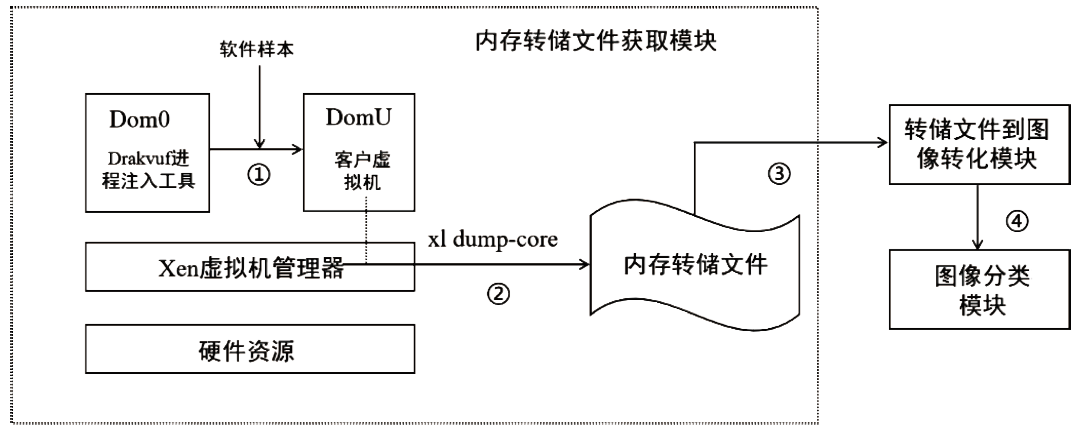
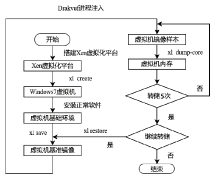
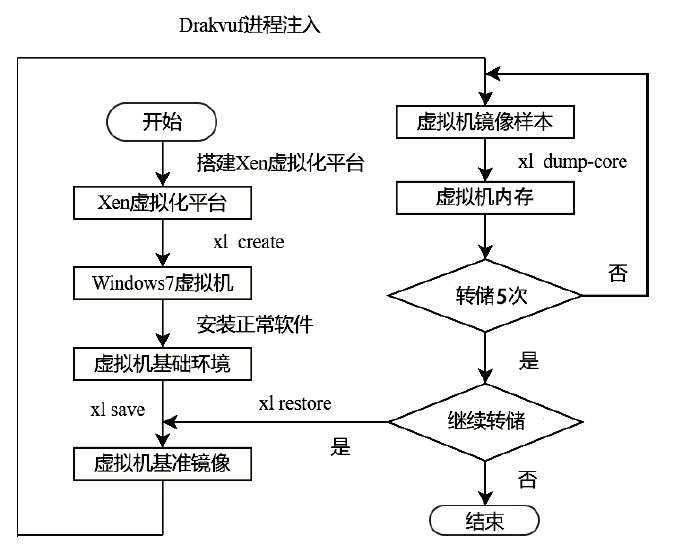
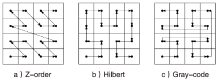
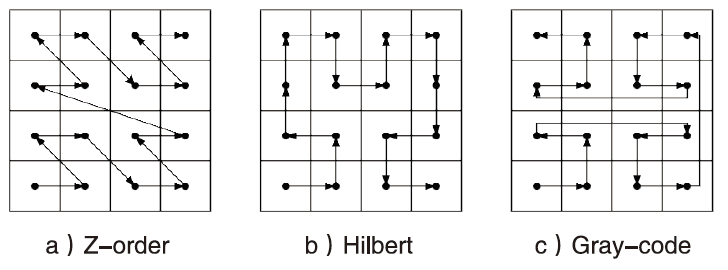
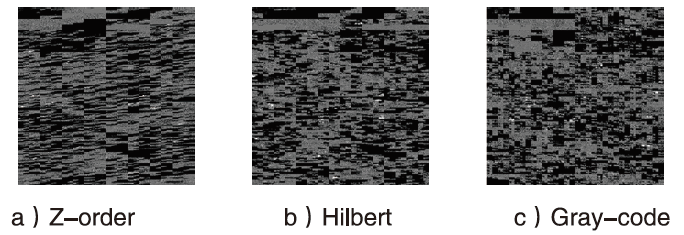
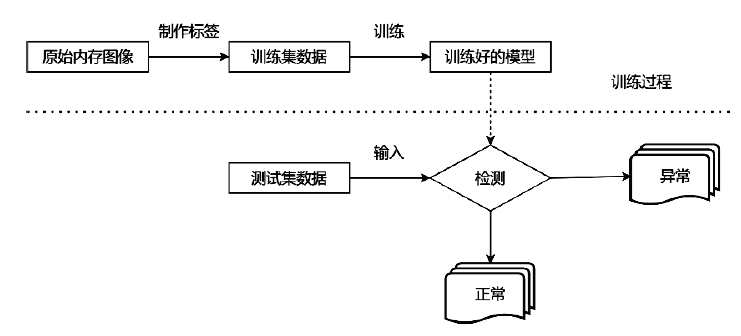
文章提出了一种基于图像和深度学习的虚拟化平台异常行为检测方法,并设计实现了系统原型。该方法借助Xen虚拟化平台分别对虚拟机运行正常软件和恶意软件过程中的系统内存进行转储,收集到包含1100个正常行为和2200个异常行为的内存转储文件。针对每个文件,提取了其前10 MB的系统敏感区域,而后利用SFC将其转换为二维图像。最后,使用卷积神经网络对内存图像进行分类,判断虚拟化平台是否存在异常行为。实验结果表明,该系统取得了98.78%的分类准确率,能够有效检测虚拟化平台中存在的异常行为。
中图分类号:
引用本文
林发鑫, 张健. 虚拟化平台异常行为检测系统的设计与实现[J]. 信息网络安全, 2022, 22(11): 62-67.
LIN Faxin, ZHANG Jian. Design and Implementation of Abnormal Behavior Detection System for Virtualization Platform[J]. Netinfo Security, 2022, 22(11): 62-67.
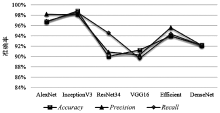
表3
模型的分类性能
| Model | Hilbert | Z-order | Gray-code | ||||||
|---|---|---|---|---|---|---|---|---|---|
| Accuracy | Precision | Recall | Accuracy | Precision | Recall | Accuracy | Precision | Recall | |
| AlexNet | 96.68% | 98.17% | 96.83% | 94.26% | 96.55% | 95.37% | 92.43% | 94.59% | 92.11% |
| InceptionV3 | 98.78% | 98.12% | 98.57% | 97.28% | 97.12% | 97.66% | 96.26% | 96.22% | 96.38% |
| ResNet34 | 90.03% | 90.87% | 94.57% | 89.68% | 90.17% | 88.25% | 88.16% | 89.18% | 88.09% |
| VGG16 | 91.25% | 90.29% | 89.66% | 88.31% | 87.64% | 89.42% | 90.17% | 90.33% | 90.59% |
| Efficient | 93.96% | 95.61% | 94.38% | 92.79% | 92.74% | 92.52% | 91.06% | 90.78% | 91.78% |
| DenseNet | 92.18% | 92.14% | 92.18% | 89.55% | 89.72% | 88.48% | 91.39% | 90.45% | 92.96% |
表3
| [1] |
MANSOURI Y, BABAR M A. A Review of Edge Computing: Features and Resource Virtualization[J]. Journal of Parallel and Distributed Computing, 2021, 150: 155-183.
doi: 10.1016/j.jpdc.2020.12.015 URL |
| [2] | UEKI K, KOURAI K. Fine-Grained Autoscaling with In-VM Containers and VM Introspection[C]//IEEE. 2020 IEEE/ACM 13th International Conference on Utility and Cloud Computing (UCC). New York:IEEE, 2020: 155-164. |
| [3] | GARFINKEL T, ROSENBLUM M. A Virtual Machine Introspection Based Architecture for Intrusion Detection[EB/OL]. [2022-06-08]. |
| [4] | CONTI G, DEAN E, SINDA M, et al. Visual Reverse Engineering of Binary and Data Files[C]// Springer. International Workshop on Visualization for Computer Security. Heidelberg: Springer, 2008: 1-17. |
| [5] | NATARAJ L, KARTHIKEYAN S, JACOB G, et al. Malware Images: Visualization and Automatic Classification[C]// ACM. Proceedings of the 8th International Symposium on Visualization for Cyber Security. New York: ACM, 2011: 1-7. |
| [6] | LUO J S, LO D C T. Binary Malware Image Classification Using Machine Learning with Local Binary Pattern[C]// IEEE. 2017 IEEE International Conference on Big Data (Big Data). New York:IEEE, 2017: 4664-4667. |
| [7] | LE Q, BOYDELL O, MAC NAMEE M B, et al. Deep Learning at the Shallow End: Malware Classification for Non-Domain Experts[J]. Digital Investigation, 2018, 26: 118-126. |
| [8] | QIAO Yanchen, JIANG Qingshan, JIANG Zhenchao, et al. A Multi-Channel Visualization Method for Malware Classification Based on Deep Learning[C]//IEEE. 2019 18th IEEE International Conference On Trust, Security And Privacy in Computing and Communications/13th IEEE International Conference On Big Data Science And Engineering (TrustCom/BigDataSE). New York:IEEE, 2019: 757-762. |
| [9] |
PINHERO A, ANUPAMA M L, VINOD P, et al. Malware Detection Employed by Visualization and Deep Neural Network[J]. Computers & Security, 2021, 105: 102247.
doi: 10.1016/j.cose.2021.102247 URL |
| [10] |
LIN W C, YEH Y R. Efficient Malware Classification by Binary Sequences with One-Dimensional Convolutional Neural Networks[J]. Mathematics, 2022, 10(4): 608.
doi: 10.3390/math10040608 URL |
| [11] |
O’SHAUGHNESSY S, SHERIDAN S. Image-Based Malware Classification Hybrid Framework Based on Space-Filling Curves[J]. Computers & Security, 2022, 116: 102660.
doi: 10.1016/j.cose.2022.102660 URL |
| [12] | O’SHAUGHNESSY S. Image-Based Malware Classification: A Space Filling Curve Approach[C]//IEEE. 2019 IEEE Symposium on Visualization for Cyber Security (VizSec). New York:IEEE, 2019: 1-10. |
| [13] | WANG Xiangyi, ZHANG Jian. Abnormal Behavior Detection of Virtualization Platform Based on Image and Machine Learning[J]. Netinfo Security, 2020, 20(9): 92-96. |
| 王湘懿, 张健. 基于图像和机器学习的虚拟化平台异常检测[J]. 信息网络安全, 2020, 20(9): 92-96. | |
| [14] |
BASU K, KRISHNAMURTHY P, KHORRAMI F, et al. A Theoretical Study of Hardware Performance Counters-Based Malware Detection[J]. IEEE Transactions on Information Forensics and Security, 2019, 15: 512-525.
doi: 10.1109/TIFS.2019.2924549 URL |
| [15] | KUMAR R, PATI S, LAHIRI K. Darts: Performance-Counter Driven Sampling Using Binary Translators[C]//IEEE. 2017 IEEE International Symposium on Performance Analysis of Systems and Software(ISPASS). New York:IEEE, 2017: 131-132. |
| [16] | TRIPATHI S, GRIECO G, RAWAT S. Exniffer: Learning to Prioritize Crashes by Assessing the Exploitability from Memory Dump[C]//IEEE. 2017 24th Asia-Pacific Software Engineering Conference (APSEC). New York:IEEE, 2017: 239-248. |
| [1] | 刘光杰, 段锟, 翟江涛, 秦佳禹. 基于多特征融合的移动流量应用识别[J]. 信息网络安全, 2022, 22(7): 18-26. |
| [2] | 于成丽, 张阳, 贾世杰. 云环境中数据安全威胁与防护关键技术研究[J]. 信息网络安全, 2022, 22(7): 55-63. |
| [3] | 王浩洋, 李伟, 彭思维, 秦元庆. 一种基于集成学习的列车控制系统入侵检测方法[J]. 信息网络安全, 2022, 22(5): 46-53. |
| [4] | 刘峰, 杨成意, 於欣澄, 齐佳音. 面向去中心化双重差分隐私的谱图卷积神经网络[J]. 信息网络安全, 2022, 22(2): 39-46. |
| [5] | 张郅, 李欣, 叶乃夫, 胡凯茜. 融合多重风格迁移和对抗样本技术的验证码安全性增强方法[J]. 信息网络安全, 2022, 22(10): 129-135. |
| [6] | 高昌锋, 肖延辉, 田华伟. 基于多阶段渐进式神经网络的图像相机指纹提取算法[J]. 信息网络安全, 2022, 22(10): 15-23. |
| [7] | 刘家银, 李馥娟, 马卓, 夏玲玲. 基于多尺度卷积神经网络的恶意代码分类方法[J]. 信息网络安全, 2022, 22(10): 31-38. |
| [8] | 弋晓洋, 张健. 基于图像的网络钓鱼邮件检测方法研究[J]. 信息网络安全, 2021, 21(9): 52-58. |
| [9] | 李彦霖, 蔡满春, 芦天亮, 席荣康. 遗传算法优化CNN的网站指纹攻击方法[J]. 信息网络安全, 2021, 21(9): 59-66. |
| [10] | 游文婷, 张乐友, 叶亚迪, 李晖. 多用户通信机制中支持隐私保护的属性基动态广播加密[J]. 信息网络安全, 2021, 21(4): 21-30. |
| [11] | 杨铭, 张健. 基于图像识别的恶意软件静态检测模型[J]. 信息网络安全, 2021, 21(10): 25-32. |
| [12] | 徐国天, 盛振威. 基于融合CNN与LSTM的DGA恶意域名检测方法[J]. 信息网络安全, 2021, 21(10): 41-47. |
| [13] | 马骁, 蔡满春, 芦天亮. 基于CNN改进模型的恶意域名训练数据生成技术[J]. 信息网络安全, 2021, 21(10): 69-75. |
| [14] | 李桥, 龙春, 魏金侠, 赵静. 一种基于LMDR和CNN的混合入侵检测模型[J]. 信息网络安全, 2020, 20(9): 117-121. |
| [15] | 王湘懿, 张健. 基于图像和机器学习的虚拟化平台异常检测[J]. 信息网络安全, 2020, 20(9): 92-96. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||