信息网络安全 ›› 2022, Vol. 22 ›› Issue (6): 61-72.doi: 10.3969/j.issn.1671-1122.2022.06.007
区块链跨链安全接入与身份认证方案研究与实现
- 北京邮电大学网络空间安全学院,北京 100876
-
收稿日期:2022-02-20出版日期:2022-06-10发布日期:2022-06-30 -
通讯作者:马兆丰 E-mail:mzf@bupt.edu.cn -
作者简介:王姝爽(1998—),女,山东,硕士研究生,主要研究方向为区块链及安全技术|马兆丰(1974—),男,甘肃,副教授,博士,主要研究方向为区块链理论与技术、区块链核心创新及应用|刘嘉微(1997—),女,江西,硕士研究生,主要研究方向为区块链及安全技术|罗守山(1962—),男,安徽,教授,博士,主要研究方向为区块链、密码学、网络与信息安全 -
基金资助:国家重点研发计划(2020YFB1005500);北京市自然科学基金(M21034)
Research and Implementation of Cross-Chain Security Access and Identity Authentication Scheme of Blockchain
WANG Shushuang, MA Zhaofeng( ), LIU Jiawei, LUO Shoushan
), LIU Jiawei, LUO Shoushan
- The School of Cyberspace Security, Beijing University of Posts and Telecommunications, Beijing 100876, China
-
Received:2022-02-20Online:2022-06-10Published:2022-06-30 -
Contact:MA Zhaofeng E-mail:mzf@bupt.edu.cn
摘要:
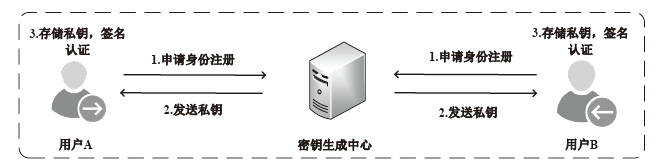
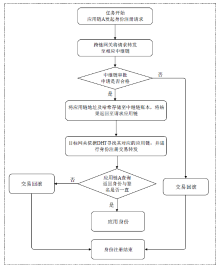
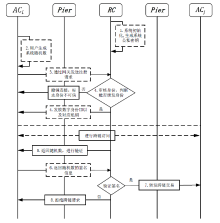
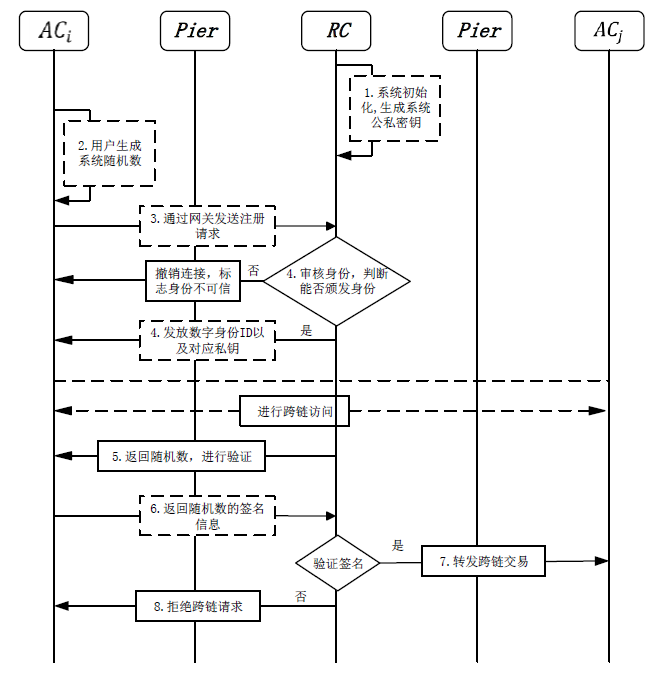
文章提出一种区块链跨链安全接入与身份认证方案,针对跨链技术中的接入链安全接入与跨链身份认证问题,设计安全的跨链模型架构,采用数字身份ID作为区块链整个跨链网络的全局标识符,完成跨链交易的身份认定。文章提出了基于中继链的IBE的跨链身份认证方案,通过中继链进行接入链安全接入与跨链身份认证,同时采用安全密钥协商策略,对进行跨链交易的两条链进行交易信息加密传输,确保交易信息的匿名安全性,解决了现有跨链模型中的安全性和数据孤岛问题。实验分析和评估表明该方案是安全可行的。
中图分类号:
引用本文
王姝爽, 马兆丰, 刘嘉微, 罗守山. 区块链跨链安全接入与身份认证方案研究与实现[J]. 信息网络安全, 2022, 22(6): 61-72.
WANG Shushuang, MA Zhaofeng, LIU Jiawei, LUO Shoushan. Research and Implementation of Cross-Chain Security Access and Identity Authentication Scheme of Blockchain[J]. Netinfo Security, 2022, 22(6): 61-72.
表4
区块链交易查询结果
| 序号 | 交易 类型 | 交易ID | 区块Hash | 时间戳 | 交易Payload |
|---|---|---|---|---|---|
| 1 | 链内 交易 | 0c8d0734353983fdb811eca43eea4fda87e3f9370b4ee3c7b4465e0abc75b62f | 0x2D1b227D0b1Ae21C8Ba4852253101c4c25008c1873d57Da9ab10Dd73e32e1517 | 2022-01-22T13: 18:47.769 | 初始化Alice拥有资产9000元 |
| 2 | 链内 交易 | ea7e34814f930e83a7b81ee62eba4f77da93badfa7d26796059b6c134935b892 | 0xE61ED7874DA939aa4c14663d9f1902b3F3915a36B62959bF0875F89Ca476DDE8 | 2022-01-22T14: 03:47.770 | Alice向Bob转账100元 |
| 3 | 跨链 交易 | e42f1f2b280a00349aa96def72c1d08f5c7a0fb0e9c5ccb37103b4db5f46c5a | 0x7166b32Ae51CC411bC7A1AabaE9011C23d5C6c6636C351ae5D8C6463cBFe2629 | 2022-01-22T23: 16:40.59 | BobA链向BobB链转账200元 |
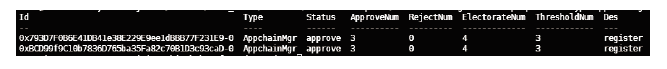
| 4 | 中继链 交易 | ee62eba4f77da93badfa7d26796059b6c134935b892e42f1f2b280a00349aa | 0x1E249da3558Da2891054e10de7B1077E49eA86d139333D6Dca49acc95F1feE5d | 2022-01-23T08: 16:40.59 | 接入链发起注册请求 |
| 5 | 中继链 交易 | 0734353983fdb811eca43eea4fda87e3f9370b4ea7e34814f930e83a7b81e | 0x336bcdBb0689d5ef70425320A5aB52de553399316Eb3f6c5c6d86c0F7B63b8Fd | 2022-01-24T11: 16:40.59 | 节点对注册请求进行投票 |
| [1] | SCHULTE S, SIGWART M, FRAUENTHALER P, et al. Towards Blockchain Interoperability[C]// Springer. International Conference on Business Process Management. Berlin: Springer, 2019: 3-10. |
| [2] | QASSE I A, ABU T M, NASIR Q. Inter Blockchain Communication: A Survey[C]// ArabWIC. Proceedings of the ArabWIC 6th Annual International Conference Research Track. Arab: ArabWIC, 2019: 1-6. |
| [3] | LI Fang, LI Zhuoran, ZHAO He. Research on the Progress of Blockchain Cross Chain Technology[J]. Journal of Software, 2019, 30(6): 1649-1660. |
| 李芳, 李卓然, 赵赫. 区块链跨链技术进展研究[J]. 软件学报, 2019, 30(6): 1649-1660. | |
| [4] | XIAO Zhifei. Design and Research of IP Secure Communication System Based on Combined Public Key[J]. Network Security Technology and Application, 2022(1): 23-24. |
| 肖智飞. 基于组合公钥的IP安全通信系统设计研究[J]. 网络安全技术与应用, 2022(1):23-24. | |
| [5] | QIU Suhua. Research and Implementation of Unified Authentication System Based on Identity Authentication Technology[J]. China Informatization, 2021(12): 59-60. |
| 邱素华. 基于身份认证技术的统一认证系统研究与实现[J]. 中国信息化, 2021(12): 59-60. | |
| [6] |
VELÁSQUEZ I, CARO A, RODRÍGUEZ A. Authentication Schemes and Methods: A Systematic Literature Review[J]. Information and Software Technology, 2018, 94: 30-37.
doi: 10.1016/j.infsof.2017.09.012 URL |
| [7] | CHEN Yuxiang, DONG Guishan, BAI Jian, et al. Trust Enhancement Scheme for Cross Domain Authentication of PKI System[C]// IEEE. 2019 International Conference on Cyber-Enabled Distributed Computing and Knowledge Discovery(CyberC). New York:IEEE, 2019: 103-110. |
| [8] |
MA Zhaofeng, WANG Xiaochang, JAIN D K, et al. A Blockchain-Based Trusted Data Management Scheme in Edge Computing[J]. IEEE Transactions on Industrial Informatics, 2019, 16(3): 2013-2021.
doi: 10.1109/TII.2019.2933482 URL |
| [9] | LIU Mingda, CHEN Zuoling, SHI Yijuan, et al. Research Progress of Blockchain in the Field of Data Security[J]. Journal of Computer Science, 2021, 44(1): 1-27. |
| 刘明达, 陈左宁, 拾以娟, 等. 区块链在数据安全领域的研究进展[J]. 计算机学报, 2021, 44(1):1-27. | |
| [10] | GU Yan. Design and Implementation of Identity Authentication System Based on Blockchain[D]. Beijing: Beijing University of Posts and Telecommunications, 2018. |
| 顾燕. 基于区块链的身份认证系统的设计与实现[D]. 北京: 北京邮电大学, 2018. | |
| [11] |
MA Zhaofeng, WANG Lingyun, WANG Xiaochang, et al. Blockchain-Enabled Decentralized Trust Management and Secure Usage Control of IoT Big Data[J]. IEEE Internet of Things Journal, 2019, 7(5): 4000-4015.
doi: 10.1109/JIOT.2019.2960526 URL |
| [12] | DONG Guishan, CHEN Yuxiang, FAN Jia, et al. Research on Privacy Protection Strategies in Blockchain Applications[J] Computer Science, 2019, 46(5): 29-35. |
| 董贵山, 陈宇翔, 范佳, 等. 区块链应用中的隐私保护策略研究[J]. 计算机科学, 2019, 46(5):29-35. | |
| [13] | ZHANG Linlin, ZOU Xiang, YANG Minghui. Identity Authentication Chain Based on Encrypted Database in Heterogeneous Alliance Network[C]// IEEE. Proceedings of the 2019 7th International Conference on Information Technology:IoT and Smart City. New York: IEEE, 2019: 353-356. |
| [14] |
SHAO Sisi, CHEN Fei, XIAO Xiaoying, et al. IBE-BCIOT: An IBE Based Cross-Chain Communication Mechanism of Blockchain in IoT[J]. World Wide Web, 2021, 24(5): 1665-1690.
doi: 10.1007/s11280-021-00864-9 URL |
| [15] | WANG Xiaoyi, QIU Weiwei, ZENG Lei, et al. A Credible Transfer Method of Cross-Chain Assets Based on DID and VC[C]// IEEE. 2021 IEEE 4th International Conference on Information Systems and Computer Aided Education(ICISCAE). New York:IEEE, 2021: 238-242. |
| [16] | XIE Tianxiu, ZHANG Yue, GAI Keke, et al. Cross-Chain-Based Decentralized Identity for Mortgage Loans[C]// Springer. International Conference on Knowledge Science, Engineering and Management. Berlin: Springer, 2021: 619-633. |
| [17] |
MA Zhaofeng, MENG Jialin, WANG Jihui, et al. Blockchain-Based Decentralized Authentication Modeling Scheme in Edge and IoT Environment[J]. IEEE Internet of Things Journal, 2020, 8(4): 2116-2123.
doi: 10.1109/JIOT.2020.3037733 URL |
| [18] | ZHANG Hongxia, CHEN Xingshu, LAN Xiao, et al. BTCAS: A Blockchain-Based Thoroughly Cross-Domain Authentication Scheme[EB/OL]. [2021-12-16]. https://xueshu.baidu.com/usercenter/paper/show?paperid=11550m20k01p0gq0tp480vd01d695917. |
| [19] |
SHEN Meng, LIU Huisen, ZHU Liehuang, et al. Blockchain-Assisted Secure Device Authentication for Cross-Domain Industrial IoT[J]. IEEE Journal on Selected Areas in Communications, 2020, 38(5): 942-954.
doi: 10.1109/JSAC.2020.2980916 URL |
| [20] | CONTI M, HASSAN M, LAL C. BlockAuth: BlockChain Based Distributed Producer Authentication in ICN[EB/OL]. [2021-12-20]. https://xueshu.baidu.com/usercenter/paper/show?paperid=103n0xt0mk0u0ed0yy5p04e0fm076091. |
| [21] | YANG Chun, LI Jingwei, LI Hongwei, et al. Research on Unified Identity Model of Heterogeneous Identity Alliance[J]. Information Security and Communication Confidentiality, 2019(6): 27-35. |
| 杨淳, 李经纬, 李洪伟, 等. 异构身份联盟统一身份标识模型研究[J]. 信息安全与通信保密, 2019(6):27-35. | |
| [22] | YANG Guanqun, LIU Yin, XU Hao, et al. Power Grid Trusted Distributed Identity Authentication System Based on Blockchain[J]. Journal of Network and Information Security, 2021, 7(6): 88-98. |
| 杨冠群, 刘荫, 徐浩, 等. 基于区块链的电网可信分布式身份认证系统[J]. 网络与信息安全学报, 2021, 7(6):88-98. | |
| [23] | WANG Sasa, DAI Bingrong, ZHU Menglu, et al. User Identity Authentication Model for Cross Chain System[J]. Computer Engineering and Application, 2021(11):1-8. |
| 王洒洒, 戴炳荣, 朱孟禄, 等. 面向跨链系统的用户身份标识认证模型[J]. 计算机工程与应用, 2021(11):1-8. | |
| [24] | MICHAEL J, COHN A, BUTCHER J R. Convergence of Blockchain and IoT: An Edge Over Technologies[EB/OL]. [2021-12-15]. https://link.springer.com/chapter/10.1007/978-3-030-24513-9_17. |
| [25] | PILKINGTON M. Blockchain Technology: Principles and Applications[M]. UK: Edward Elgar Publishing, 2016. |
| [26] |
CASINO F, DASAKLIS T K, PATSAKIS C. A Systematic Literature Review of Blockchain-Based Applications: Current Status, Classification and Open Issues[J]. Telematics and Informatics, 2019, 36: 55-81.
doi: 10.1016/j.tele.2018.11.006 URL |
| [27] | YE Shaojie, WANG Xiaoyi, XU Caichao, et al. Bitxhub: Heterogeneous Blockchain Interoperability Platform Based on Side Chain Relay[J]. Computer Science, 2020, 47(6): 294-302. |
| 叶少杰, 汪小益, 徐才巢, 等. BitXHub: 基于侧链中继的异构区块链互操作平台[J]. 计算机科学, 2020, 47(6):294-302. | |
| [28] | ZHAO Dongfang. Li T. Distributed Cross-Blockchain Transactions[EB/OL]. [2021-12-18]. https://xueshu.baidu.com/usercenter/paper/show?paperid=1a3v00706k6s0mv0k95e0gj05j583896. |
| [29] | SHAMIR A. Identity-Based Cryptosystems and Signature Schemes[C]// Springer. Workshop on the Theory and Application of Cryptographic Techniques. Heidelberg: Springer, 1984: 47-53. |
| [30] |
DENG H, QIN Z, WU Q, et al. Identity-Based Encryption Transformation for Flexible Sharing of Encrypted Data in Public Cloud[J]. IEEE Transactions on Information Forensics and Security, 2020, 15: 3168-3180.
doi: 10.1109/TIFS.2020.2985532 URL |
| [1] | 沈延, 姚萌萌. 基于事件的群组密钥协商协议形式化分析研究[J]. 信息网络安全, 2022, 22(5): 30-36. |
| [2] | 吴克河, 程瑞, 姜啸晨, 张继宇. 基于SDP的电力物联网安全防护方案[J]. 信息网络安全, 2022, 22(2): 32-38. |
| [3] | 吴克河, 程瑞, 郑碧煌, 崔文超. 电力物联网安全通信协议研究[J]. 信息网络安全, 2021, 21(9): 8-15. |
| [4] | 沈卓炜, 高鹏, 许心宇. 基于安全协商的DDS安全通信中间件设计[J]. 信息网络安全, 2021, 21(6): 19-25. |
| [5] | 张昱, 孙光民, 李煜. 基于SM9算法的移动互联网身份认证方案研究[J]. 信息网络安全, 2021, 21(4): 1-9. |
| [6] | 王健, 赵曼莉, 陈志浩, 石波. 基于假名的智能交通条件隐私保护认证协议[J]. 信息网络安全, 2021, 21(4): 49-61. |
| [7] | 李桐, 周小明, 任帅, 徐剑. 轻量化移动边缘计算双向认证协议[J]. 信息网络安全, 2021, 21(11): 58-64. |
| [8] | 肖帅, 张翰林, 咸鹤群, 陈飞. 一种面向物联网设备的口令认证密钥协商协议[J]. 信息网络安全, 2021, 21(10): 83-89. |
| [9] | 董锵, 罗国明, 史宏逵, 张永跃. 基于IMS的移动通信专网认证和密钥协商方法研究[J]. 信息网络安全, 2021, 21(1): 88-96. |
| [10] | 张骁, 刘吉强. 基于硬件指纹和生物特征的多因素身份认证协议[J]. 信息网络安全, 2020, 20(8): 9-15. |
| [11] | 刘晓芬, 陈晓峰, 连桂仁, 林崧. 基于d级单粒子的可认证多方量子秘密共享协议[J]. 信息网络安全, 2020, 20(3): 51-55. |
| [12] | 赵国锋, 周文涛, 徐川, 徐磊. 一种基于双线性配对的天地一体化网络安全身份认证方案[J]. 信息网络安全, 2020, 20(12): 33-39. |
| [13] | 刘利娟, 李志慧, 支丹利. 可实现身份认证的多方量子密钥分发协议[J]. 信息网络安全, 2020, 20(11): 59-66. |
| [14] | 张富友, 王琼霄, 宋利. 基于生物特征识别的统一身份认证系统研究[J]. 信息网络安全, 2019, 19(9): 86-90. |
| [15] | 陈瑞滢, 陈泽茂, 王浩. 工业控制系统安全监控协议的设计与优化研究[J]. 信息网络安全, 2019, 19(2): 60-69. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||