信息网络安全 ›› 2020, Vol. 20 ›› Issue (12): 64-71.doi: 10.3969/j.issn.1671-1122.2020.12.009
基于StarGAN的生成式图像隐写方案
- 1.武警工程大学密码工程学院,西安 710086
2.网络与信息安全武警部队重点实验室,西安 710086
-
收稿日期:2020-09-27出版日期:2020-12-10发布日期:2021-01-12 -
通讯作者:杨晓元 E-mail:gcxy_xxyc@126.com -
作者简介:毕新亮(1997—),男,安徽,硕士研究生,主要研究方向为深度学习、信息隐藏|杨海滨(1982—),男,河北,讲师,博士,主要研究方向为密码学、信息安全|杨晓元(1959—),男,湖南,教授,硕士,主要研究方向为密码学、信息隐藏|黄思远(1997—),男,陕西,硕士研究生,主要研究方向为深度学习、隐写分析 -
基金资助:国家自然科学基金(61872384)
Generative Steganography Scheme Based on StarGAN
BI Xinliang1,2, YANG Haibin1, YANG Xiaoyuan1,2( ), HUANG Siyuan1
), HUANG Siyuan1
- 1. College of Cryptographic Engineering, Engineering University of PAP, Xi’an 710086, China
2. Network and Information Security Key Laboratory of PAP, Xi’an 710086, China
-
Received:2020-09-27Online:2020-12-10Published:2021-01-12 -
Contact:YANG Xiaoyuan E-mail:gcxy_xxyc@126.com
摘要:
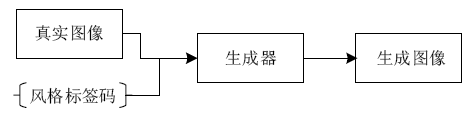
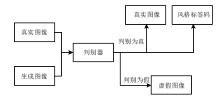
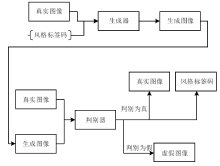
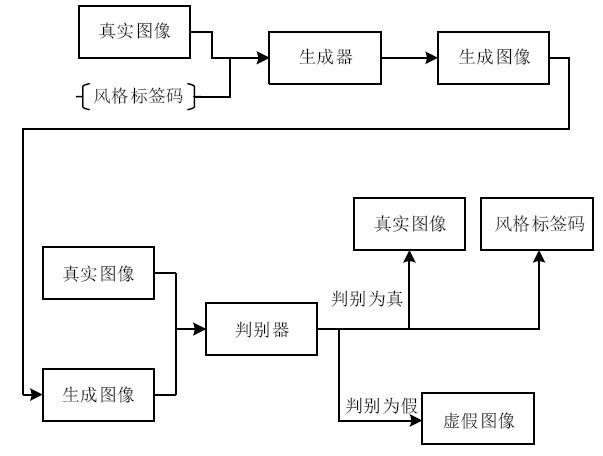
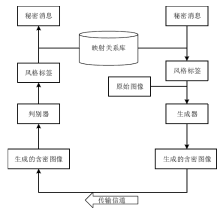
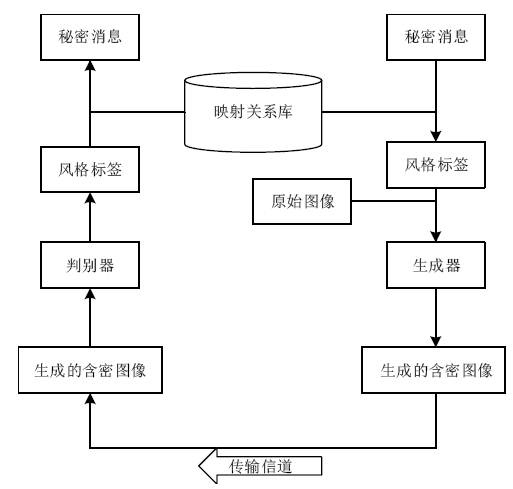
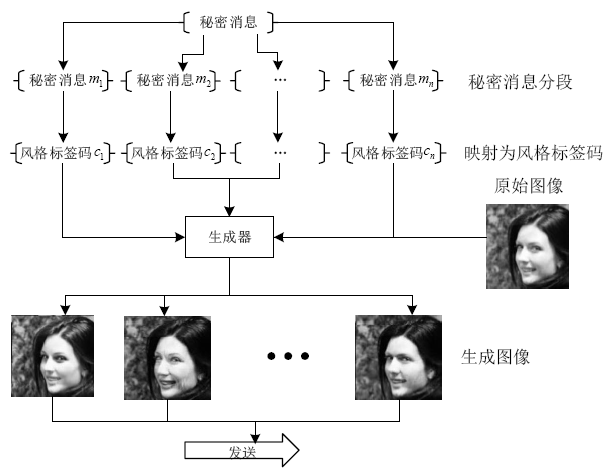
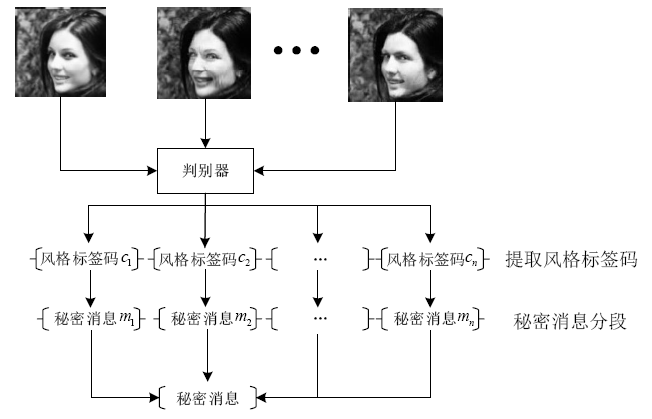
针对生成式隐写存在的生成图像与真实图像相差较大、图像翻译隐写需要训练大量模型等问题,文章提出了基于StarGAN的生成式图像隐写方案。该方案仅需一个模型即可完成多风格图像翻译任务。发送方将秘密信息进行编码,映射为图像的风格标签,然后生成相应风格的图像,发送给接收方;接收方使用秘密信道传递的提取模型,对图像进行风格标签的提取,并对照编码方式解码出秘密消息。实验结果表明,该方案在减少训练模型数量的同时,图像质量、消息提取准确性等方面均有明显提升。
中图分类号:
引用本文
毕新亮, 杨海滨, 杨晓元, 黄思远. 基于StarGAN的生成式图像隐写方案[J]. 信息网络安全, 2020, 20(12): 64-71.
BI Xinliang, YANG Haibin, YANG Xiaoyuan, HUANG Siyuan. Generative Steganography Scheme Based on StarGAN[J]. Netinfo Security, 2020, 20(12): 64-71.
| [1] | LUO Weiqi, HUANG Fangjun, HUANG Jiwu. Edge Adaptive Image Steganography Based on LSB Matching Revisited[J]. IEEE Transactions on Information Forensics & Security, 2010,5(2):201-214. |
| [2] | FILLER T, JUDAS J, FRIDRICH J. Minimizing Additive Distortion in Steganography Using Syndrome-Trellis Codes[J]. IEEE Transactions on Information Forensics & Security, 2011,6(3):920-935. |
| [3] | GOODFELLOW I J, POUGET-ABADIE J, MIRZA M, et al. Generative Adversarial Networks[EB/OL]. https://arxiv.org/abs/1406.2661, 2014-06-10. |
| [4] | ZHANG Zhu, LIU Jia, KE Yan, et al. Generative Steganography by Sampling[J]. IEEE Access, 2019,19(7):118586-118597. |
| [5] | HUSSAIN I, ZENG Jishen, TAN Sunquan. A Survey on Deep Convolutional Neural Networks for Image Steganographyand Steganalysis[J]. KSII Trans on Internet and Information Systems, 2020,14(3):1228-1248. |
| [6] | VOLKHONSKIY D, BORISENKO B, BURNAEV E. Generative Dversarial Networks for Image Steganography[EB/OL]. https://openreview.net/pdf?id=H1hoFU9xe, 2020-08-09. |
| [7] | ZHU Junyan, PARK T, ISOLA P, et al. Unpaired Image-to-Image Translation Using Cycle-Consistent Adversarial Networks[C]// IEEE. Proceedings of the IEEE International Conference on Computer Vision, October 22-29, 2017, Venice, Italy. NJ: IEEE, 2017: 2223-2232. |
| [8] | HAYES J, DANEZIS G. Generating Steganographic Images via Adversarial Training[EB/OL]. https://arxiv.org/abs/1703.00371, 2014-7-13. |
| [9] | HU Donghui, WANG Liang, JIANG Wenjie, et al. A Novel Image Steganography Method via Deep Convolutional Generative Adversarial Networks[J]. IEEE Access, 2018,18(6):38303-38314. |
| [10] |
ZHANG Zhuo, FU Guangyuan, NI Rongrong, et al. A Generative Method for Steganography by Cover Synjournal with Auxiliary Semantics[J]. Tsinghua Science and Technology, 2020,25(4):516-527.
doi: 10.1109/TST.5971803 URL |
| [11] |
TANG Weixuan, TAN Shunquan, LI Bin, et al. Automatic Steganographic Distortion Learning Using a Generative Adversarial Network[J]. IEEE Signal Processing Letters, 2017,24(10):1547-1551.
doi: 10.1109/LSP.2017.2745572 URL |
| [12] | YANG Jianhua, LIU Kai, KANG Xiangui, et al. Spatial Image Steganography Based on Generative Adversarial Network[EB/OL]. https://arxiv.org/abs/1804.07939, 2018-04-21. |
| [13] | RONNEBERGER O, FISCHER P, BROX T. U-net: Convolutional Networks for Biomedical Image Segmentation[C]// TUM & FAU. International Conference on Medical Image Computing and Computer-assisted Intervention, October 5-9, 2015, Munich, Germany. Cham: Springer, 2015: 234-241. |
| [14] | HOLUB V, FRIDRICH J, DENEMARK T. Universal Distortion Function for Steganography in an Arbitrary Domain[J]. EURASIP Journal on Information Security, 2014,14(1):1. |
| [15] | CHOI Y, CHOI M, KIM M, et al. Stargan: Unified Generative Adversarial Networks for Multi-Domain Image-to-Imagetranslation[C]// IEEE. Proc of the IEEE Conference on Computer Vision and Pattern Recognition, June 18-22, 2018, Salt Lake City, Utah, USA. NJ: IEEE, 2018: 8789-8797. |
| [16] | PERARNAU G, VAN D J, RADUCANU B, et al. Invertible Conditional Gans for Image Editing[EB/OL]. https://arxiv.org/abs/1611.06355, 2016-11-19. |
| [17] | LIU Jia, KE Yan, ZHANG Zhuo, et al. Recent Advances of Image Steganography with Generative Adversarial Networks[J]. IEEE Access, 2020,20(8):60575-60597. |
| [18] | HICSONMEZ S, SAMET N, AKBAS E, et al. GANILLA: Generative Adversarial Networks for Image to Illustration Translation[EB/OL]. https://arxiv.org/abs/2002.05638, 2020-02-14. |
| [19] | ISOLA P, ZHU Junyan, ZHOU Tinghui, et al. Image-to-Image Translation with Conditional Adversarial Networks[C]// IEEE. Proc of The IEEE Conference on Computer Visionan Dpattern Recognition, July 21-26, 2017, Honolulu, Hawaii, USA. NJ: IEEE, 2017: 1125-1134. |
| [20] | HEUSEL M, RAMSAUER H, UNTERTHINER T, et al. Gans Trainedbya Two Time-Scale Update Rule Converge to ALocal Nash Equilibrium[EB/OL]. https://arxiv.org/abs/1706.08500v6, 2018-01-12. |
| [21] | KE Yan, LIU Jia, ZHANG Minqing, et al. Steganography Security: Princip leand Practice[J]. IEEE Access, 2018,18(6):73009-73022. |
| [1] | 吴警, 芦天亮, 杜彦辉. 基于Char-RNN改进模型的恶意域名训练数据生成技术[J]. 信息网络安全, 2020, 20(9): 6-11. |
| [2] | 王文华, 郝新, 刘焱, 王洋. AI系统的安全测评和防御加固方案[J]. 信息网络安全, 2020, 20(9): 87-91. |
| [3] | 张敏情, 周能, 刘蒙蒙, 柯彦. 同态加密域可逆信息隐藏技术研究[J]. 信息网络安全, 2020, 20(8): 25-36. |
| [4] | 张蕾华, 黄进, 张涛, 王生玉. 视频侦查中人像智能分析应用及算法优化[J]. 信息网络安全, 2020, 20(5): 88-93. |
| [5] | 王蓉, 马春光, 武朋. 基于联邦学习和卷积神经网络的入侵检测方法[J]. 信息网络安全, 2020, 20(4): 47-54. |
| [6] | 程洋, 雷敏, 罗群. 基于深度学习的物联网终端设备接入认证方法[J]. 信息网络安全, 2020, 20(11): 67-74. |
| [7] | 谢永恒, 冯宇波, 董清风, 王梅. 基于深度学习的数据接入方法研究[J]. 信息网络安全, 2019, 19(9): 36-40. |
| [8] | 唐洪琼, 钮可, 张英男, 杨晓元. 自适应二维直方图迁移的视频可逆隐写算法[J]. 信息网络安全, 2019, 19(9): 106-110. |
| [9] | 马春光, 郭瑶瑶, 武朋, 刘海波. 生成式对抗网络图像增强研究综述[J]. 信息网络安全, 2019, 19(5): 10-12. |
| [10] | 王耀杰, 钮可, 杨晓元. 基于生成对抗网络的图像隐藏方案[J]. 信息网络安全, 2019, 19(5): 54-60. |
| [11] | 方勇, 朱光夏天, 刘露平, 贾鹏. 基于深度学习的浏览器Fuzz样本生成技术研究[J]. 信息网络安全, 2019, 19(3): 26-33. |
| [12] | 朱海麒, 姜峰. 人工智能时代面向运维数据的异常检测技术研究与分析[J]. 信息网络安全, 2019, 19(11): 24-35. |
| [13] | 欧博, 石向莲. 基于深度无合成误差模型的三维图像可逆信息隐藏方法研究[J]. 信息网络安全, 2018, 18(5): 24-31. |
| [14] | 段大高, 谢永恒, 盖新新, 刘占斌. 基于神经网络的微博虚假消息识别模型[J]. 信息网络安全, 2017, 17(9): 134-137. |
| [15] | 熊金波, 马蓉, 张媛媛, 戴睿煜. 面向社交网络的图片信息隐藏方法与实现[J]. 信息网络安全, 2017, 17(3): 6-8. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||