信息网络安全 ›› 2020, Vol. 20 ›› Issue (12): 19-27.doi: 10.3969/j.issn.1671-1122.2020.12.003
基于改进V-detector算法的入侵检测研究与优化
- 1.北京工业大学信息学部,北京 100124
2.国核电力规划设计研究院有限公司,北京 100095
3.中国人民大学信息学院,北京 100872
-
收稿日期:2020-07-13出版日期:2020-12-10发布日期:2021-01-12 -
通讯作者:韩松 E-mail:418594110@qq.com -
作者简介:何泾沙(1961—),男,陕西,教授,博士,主要研究方向为网络安全、测试与分析、云计算|韩松(1994—),男,陕西,硕士,主要研究方向为信息安全|朱娜斐(1981—),女,河南,副教授,博士,主要研究方向为网络安全、隐私保护和区块链|葛加可(1993—),男,山西,博士研究生,主要研究方向为信息安全 -
基金资助:国家自然科学基金(61602456)
Research and Optimization of Intrusion Detection Based on Improved V-detector Algorithm
HE Jingsha1, HAN Song2( ), ZHU Nafei1, GE Jiake3
), ZHU Nafei1, GE Jiake3
- 1. Department of Information Science, Beijing University of Technology, Beijing 100124, China
2. State Nuclear Electric Power Planning Design & Research Institute Co., LTD., Beijing 100095, China
3. School of Information, Renmin University of China, Beijing 100872, China
-
Received:2020-07-13Online:2020-12-10Published:2021-01-12 -
Contact:HAN Song E-mail:418594110@qq.com
摘要:
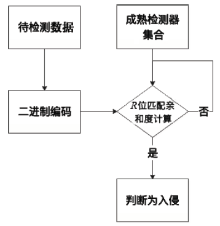
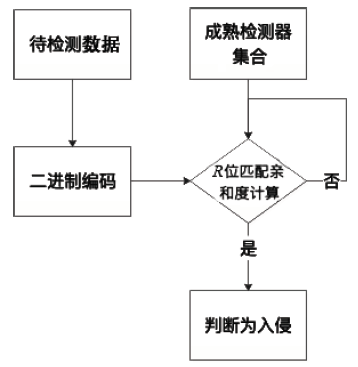
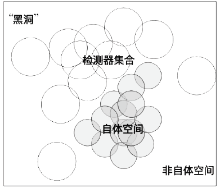
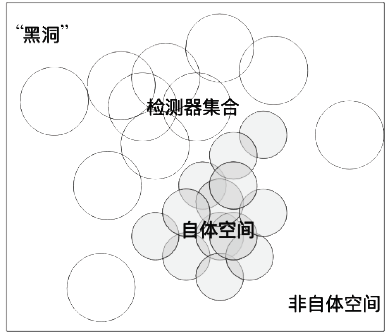
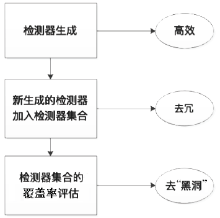
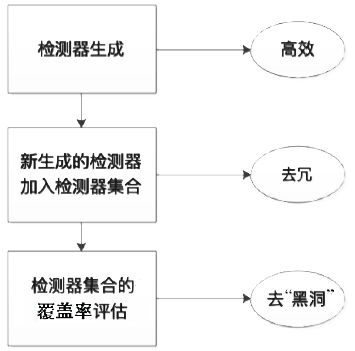
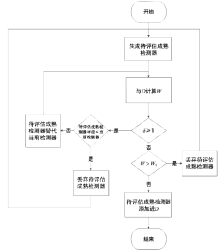
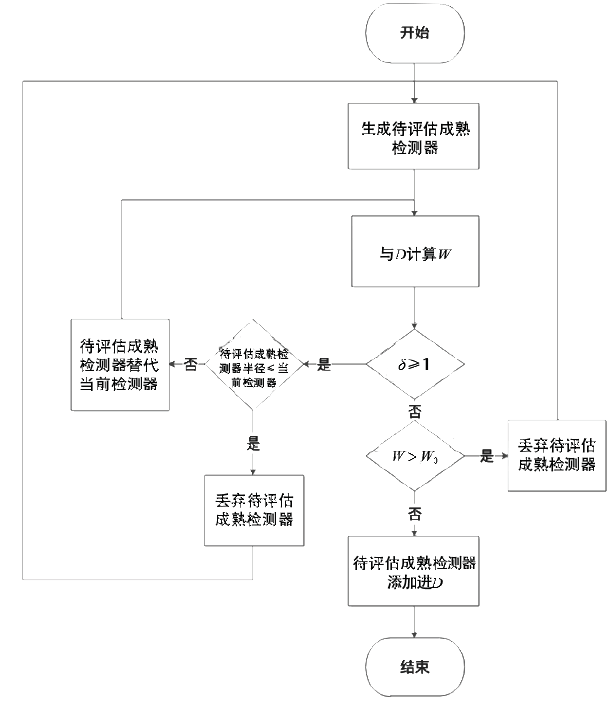
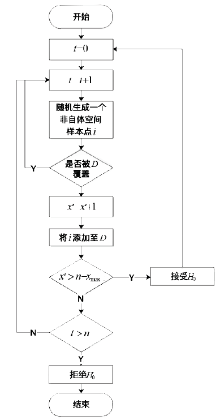
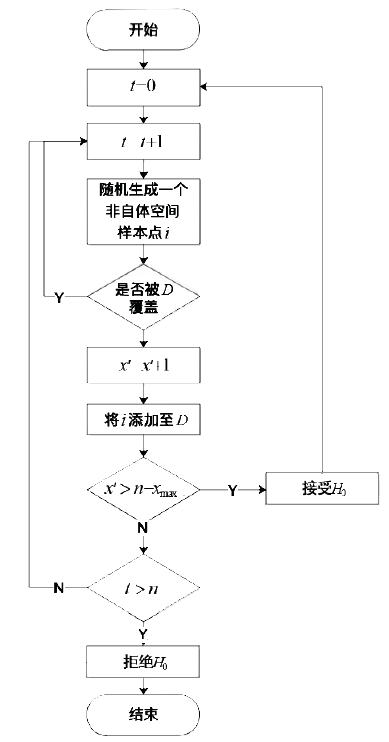
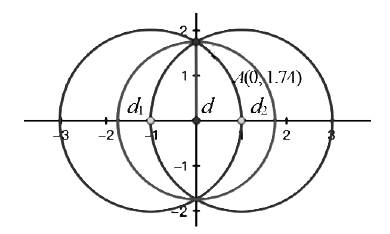
随着互联网用户数量的剧增,网络威胁也在迅速增长,传统的被动防御措施不足以防御日益多变的网络入侵。传统入侵检测系统原理是收集病毒特征再进行特征匹配,对于未知病毒,传统检测机制存在滞后性。面对日益繁杂的网络安全环境,研究基于人工免疫理论的入侵检测系统具有重要意义。文章首先介绍人工免疫理论的核心思想否定选择算法,进而介绍实值否定选择算法和V-detector算法。针对V-detector算法的不足,进行3个方面的改进:提出基于定距变异的克隆选择算法提高检测器生成效率;提出去冗算法减少检测器冗余,加快算法收敛;引入并改进假设检验方法,对检测器集合的覆盖率进行评估。实验证明,文章提出的改进V-detector算法能有效提升检测精度,减少检测黑洞,并大大缩减检测时间。
中图分类号:
引用本文
何泾沙, 韩松, 朱娜斐, 葛加可. 基于改进V-detector算法的入侵检测研究与优化[J]. 信息网络安全, 2020, 20(12): 19-27.
HE Jingsha, HAN Song, ZHU Nafei, GE Jiake. Research and Optimization of Intrusion Detection Based on Improved V-detector Algorithm[J]. Netinfo Security, 2020, 20(12): 19-27.
| [1] | LIU A X, GOUDA M G. Diverse Firewall Design[J]. IEEE Transactions on Parallel and Distributed Systems, 2008,19(9):1237-1251. |
| [2] | METTU N, SASIKALA T. Intrusion Detection in Wireless Sensor Networks[C]// IEEE. 2018 Second International Conference on Inventive Communication and Computational Technologies (ICICCT), April 20-21, 2018, Coimbatore, India. NJ: IEEE, 2018: 84-89. |
| [3] | SHAHRESTANI S A. Soft Computing in Network Intrusion Detection[EB/OL]. https://researchdirect.westernsydney.edu.au/islandora/object/uws:6925, 2020-05-25. |
| [4] | UMER M F, SHER M, BI Yaxin. A Two-stage Flow-based Intrusion Detection Model for Next-generation Networks[EB/OL]. https://journals.plos.org/plosone/article?id=10.1371/journal.pone.0180945, 2020-05-25. |
| [5] | LI Jianguo, YANG Yi. Survey of Intrusion Detection System[J]. Science&Technology Vision, 2016, 6(18) 19, 36. |
| 李建国, 杨忆. 入侵检测系统研究综述[J]. 科技视界, 2016,6(18) 19, 36. | |
| [6] | FU Longtian, YU Yumei. Research on An Improved Immune Algorithm[J]. Bulletin of Science and Technology, 2018,34(6):219-222. |
| 傅龙天, 余玉梅. 一种改进的免疫算法的研究[J]. 科技通报, 2018,34(6):219-222. | |
| [7] | LIU Pengfei, LIU Ting. Physical Intrusion Detection for Industrial Control System[C]// IEEE. 2018 IEEE Conference on Communications and Network Security (CNS), May 30-June 1, 2018, Beijing, China. NJ: IEEE, 2018: 1-2. |
| [8] | PODDEBNIAK D, SOMOROVSKY J, SCHINZEL S, et al. Attacking Deterministic Signature Schemes Using Fault Attacks[EB/OL]. https://www.researchgate.net/publication/326276966_Attacking_Deterministic_Signature_Schemes_Using_Fault_Attacks, 2020-05-25. |
| [9] | ULLAH I, MAHMOUD Q H. A Hybrid Model for Anomaly-based Intrusion Detection in SCADA Networks[C]// IEEE. 2017 IEEE International Conference on Big Data, December 11-14, 2017, Boston, MA, USA. NJ: IEEE, 2018: 2160-2167. |
| [10] | CHOUDHARY S, KESSWANI N. A Survey: Intrusion Detection Techniques for Internet of Things[J]. International Journal of Information Security & Privacy, 2019,13(1):86-105. |
| [11] | FORREST S, PERELSON A S, ALLEN L, et al. Self-nonself Discrimination in a Computer[C]// IEEE. 1994 IEEE Computer Society Symposium on Research in Security and Privacy, May 16-18, 1994, Oakland, CA, USA. NJ: IEEE, 1994: 202-212. |
| [12] | JI Zhou, DASGUPTA D. Real-valued Negative Selection Algorithm with Variable-sized Detectors[M]// Springer. Genetic and Evolutionary Computation. Heidelberg: Springer, 2004: 287-298. |
| [13] |
HART E, TIMMIS J. Application Areas of AIS: The Past, The Present and The Future[J]. Applied Soft Computing, 2008,8(1):191-201.
doi: 10.1016/j.asoc.2006.12.004 URL |
| [14] | GONZALEZ F A, DASGUPTA D. Anomaly Detection Using Real-valued Negative Selection[J]. Genetic Programming & Evolvable Machines, 2003,4(4):383-403. |
| [15] | JI Zhou, DASGUPTA D. V-detector: An Efficient Negative Selection Algorithm with "Probably Adequate" Detector Coverage[J]. Information Sciences, 2009,179(10):1390-1406. |
| [16] | DE CASTRO L N, VON ZUBEN F J. Learning and Optimization Using the Clonal Selection Principle[J]. IEEE Transactions on Evolutionary Computation, 2002,6(3):239-251. |
| [17] | LIU Haiyan, LI Yuqi. The Theory of Probability and Statistics[M]. Beijing: National Defense Industry Press, 2001. |
| 刘海燕, 李裕奇. 概率论与数理统计[M]. 北京: 国防工业出版社, 2001. | |
| [18] | DHANABAL L, SHANTHARAJAH S. A Study on NSL-KDD Dataset for Intrusion Detection System Based on Classification Algorithms[J]. International Journal of Advanced Research in Computer and Communication Engineering, 2015,4(6):446-452. |
| [19] | INGRE B, YADAV A, SONI A K. Decision Tree-based Intrusion Detection System for NSL-KDD Dataset[M]// Springer. Information & Communication Technology for Intelligent Systems. Cham: Springer, Cham, 2017: 207-218. |
| [20] | LEI Shihua, DING Lei, LI Jianfeng, et al. Improved Intrusion Detection Algorithm Based on DCA[J]. Journal of Jishou University, 2015,36(6):27-29. |
| [1] | 李桥, 龙春, 魏金侠, 赵静. 一种基于LMDR和CNN的混合入侵检测模型[J]. 信息网络安全, 2020, 20(9): 117-121. |
| [2] | 徐国天. 网络入侵检测中K近邻高速匹配算法研究[J]. 信息网络安全, 2020, 20(8): 71-80. |
| [3] | 姜楠, 崔耀辉, 王健, 吴晋超. 基于上下文特征的IDS告警日志攻击场景重建方法[J]. 信息网络安全, 2020, 20(7): 1-10. |
| [4] | 张晓宇, 王华忠. 基于改进Border-SMOTE的不平衡数据工业控制系统入侵检测[J]. 信息网络安全, 2020, 20(7): 70-76. |
| [5] | 彭中联, 万巍, 荆涛, 魏金侠. 基于改进CGANs的入侵检测方法研究[J]. 信息网络安全, 2020, 20(5): 47-56. |
| [6] | 王蓉, 马春光, 武朋. 基于联邦学习和卷积神经网络的入侵检测方法[J]. 信息网络安全, 2020, 20(4): 47-54. |
| [7] | 罗文华, 许彩滇. 基于改进MajorClust聚类的网络入侵行为检测[J]. 信息网络安全, 2020, 20(2): 14-21. |
| [8] | 康健, 王杰, 李正旭, 张光妲. 物联网中一种基于多种特征提取策略的入侵检测模型[J]. 信息网络安全, 2019, 19(9): 21-25. |
| [9] | 冯文英, 郭晓博, 何原野, 薛聪. 基于前馈神经网络的入侵检测模型[J]. 信息网络安全, 2019, 19(9): 101-105. |
| [10] | 饶绪黎, 徐彭娜, 陈志德, 许力. 基于不完全信息的深度学习网络入侵检测[J]. 信息网络安全, 2019, 19(6): 53-60. |
| [11] | 刘敬浩, 毛思平, 付晓梅. 基于ICA算法与深度神经网络的入侵检测模型[J]. 信息网络安全, 2019, 19(3): 1-10. |
| [12] | 陈虹, 肖越, 肖成龙, 陈建虎. 融合最大相异系数密度的SMOTE算法的入侵检测方法[J]. 信息网络安全, 2019, 19(3): 61-71. |
| [13] | 田峥, 李树, 孙毅臻, 黎曦. 一种面向S7协议的工控系统入侵检测模型[J]. 信息网络安全, 2019, 19(11): 8-13. |
| [14] | 张良峰, 汪毅, 吴源燚, 孔睿. 基于统计的浏览器指纹采集技术[J]. 信息网络安全, 2019, 19(11): 49-55. |
| [15] | 张阳, 姚原岗. 基于Xgboost算法的网络入侵检测研究[J]. 信息网络安全, 2018, 18(9): 102-105. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||