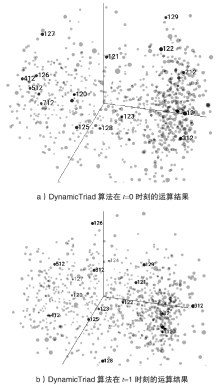
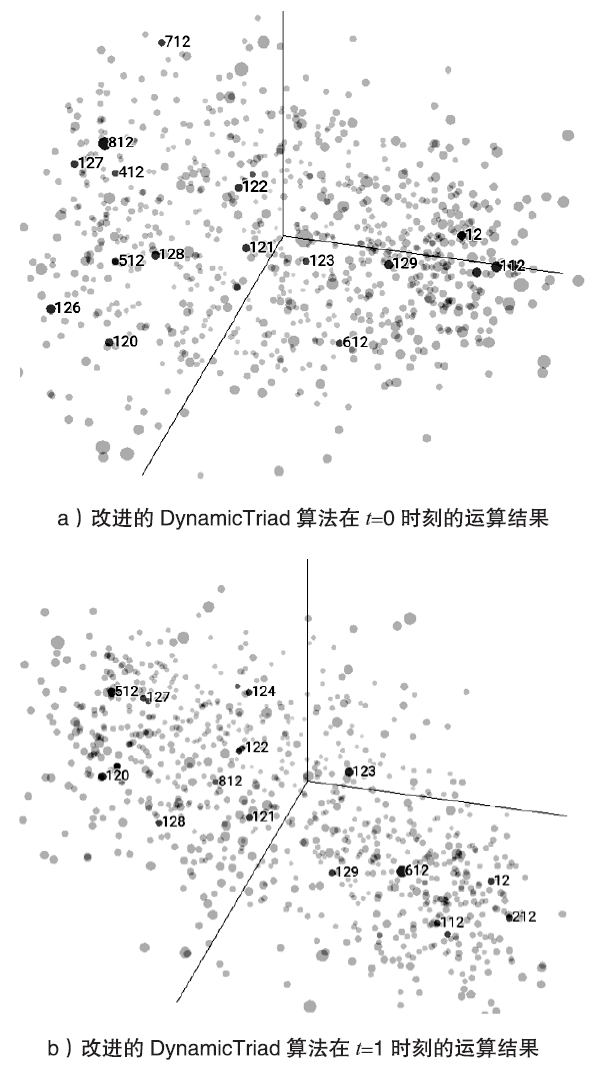
信息网络安全 ›› 2020, Vol. 20 ›› Issue (9): 97-101.doi: 10.3969/j.issn.1671-1122.2020.09.020
一种基于改进DynamicTriad模型的动态链路预测方法
- 中国人民公安大学信息网络安全学院,北京 100038
-
收稿日期:2020-07-16出版日期:2020-09-10发布日期:2020-10-15 -
通讯作者:顾益军 E-mail:guyijun@ppsuc.edu.cn -
作者简介:夏天雨(1998—),男,山东,硕士研究生,主要研究方向为网络空间安全|顾益军(1968—),男,江苏,教授,博士,主要研究方向为网络安全与执法 -
基金资助:公安部技术研究计划竞争性遴选项目(2019JZX009)
A Dynamic Link Prediction Method Based on Improved Dynamic Triad Model
- College of Information and Cyber Security, People’s Public Security University of China, Beijing 100038, China
-
Received:2020-07-16Online:2020-09-10Published:2020-10-15 -
Contact:Yijun GU E-mail:guyijun@ppsuc.edu.cn
摘要:
针对动态社交网络的链路预测,文章提出了一种改进的DynamicTriad模型,该模型以动态三元闭环结构为载体,三个顶点组成一个基本网络单元,结合网络同质性和节点相似性指标,对动态网络进行建模,跨时间片对每个节点进行向量表示,从而实现社交网络个体行为的动态预测,并通过t+1时段的嵌入向量验证t时段的预测效果。实验表明,该模型在动态表示节点关系的同时,链路预测效果优于传统算法,支持对动态社交网络的建模和分析。
中图分类号:
引用本文
夏天雨, 顾益军. 一种基于改进DynamicTriad模型的动态链路预测方法[J]. 信息网络安全, 2020, 20(9): 97-101.
XIA Tianyu, GU Yijun. A Dynamic Link Prediction Method Based on Improved Dynamic Triad Model[J]. Netinfo Security, 2020, 20(9): 97-101.
| [1] | CALDERONI F, CATANESE S, MEO D P, et al. Robust Link Prediction in Criminal Networks: A Case Study of the Sicilian Mafia[J]. Expert Systems with Applications, 2020(161):113666. |
| [2] | ZHOU Lekui, YANG Yang, REN Xiang, et al. Dynamic Network Embedding by Modeling Triadic Closure Process[C]// AAAI. 32nd AAAI Conference on Artificial Intelligence, February 2-7, 2018, New Orleans, Louisiana, USA. California: AAAI, 2018: 571-578. |
| [3] |
KOSSINETS G, WATTS D J. Origins of Homophily in an Evolving Social Network[J]. American Journal of Sociology, 2009,115(2):405-450.
doi: 10.1086/599247 URL |
| [4] |
ZHOU Tao, LÜ Linyuan, ZHANG Yicheng. Predicting Missing Links via Local Information[J]. The European Physical Journal B, 2009,71(4):623-630.
doi: 10.1140/epjb/e2009-00335-8 URL |
| [5] | LIN Dekang. An Information-theoretic Definition of Similarity[C]// ACM. 15th International Conference on Machine Learning, July 24-27, 1998, San Francisco, California, USA. New York: ACM, 1998: 296-304. |
| [6] | LESKOVEC J, HORVITZ E. Planetary-scale Views on an Instant-Messaging Network[C]// ACM. 17th International Conference on World Wide Web, April 21-25, 2008, Beijing, China. New York: ACM, 2008: 915-924. |
| [7] |
LÜ Linyuan, ZHOU Tao. Link Prediction in Complex Networks: A Survey[J]. Physica A: Statistical Mechanics and its Applications, 2011,390(6):1150-1170.
doi: 10.1016/j.physa.2010.11.027 URL |
| [8] | HASAN M AL, CHAOJI V, SALEM S, et al. Link Prediction Using Supervised Learning[C]// SIAM. SIAM International Conference on Data Mining, April 20-22, 2006, Bethesda, Maryland, USA. Pennsylvania: SIAM, 2006: 798-805. |
| [9] | YUAN Guangchao, MURUKANNAIAH P K, ZHANG Zhe, et al. Exploiting Sentiment Homophily for Link Prediction[C]// ACM. 8th ACM Conference on Recommender Systems,October 6-10, 2014, Foster City, Silicon Valley, California, USA. New York: ACM, 2014: 17-24. |
| [10] | KUNEGIS J, LOMMATZSCH A. Learning Spectral Graph Transformations for Link Prediction[C]// ACM. 26th Annual International Conference on Machine Learning,June 14-18, 2009, Montreal, Quebec, Canada. New York: ACM, 2009: 561-568. |
| [11] |
CLAUSET A, MOORE C, NEWMAN M. Hierarchical Structure and the Prediction of Missing Links in Networks[J]. Nature, 2008,453(7191):98-101.
doi: 10.1038/nature06830 URL pmid: 18451861 |
| [12] | PEROZZI B, Al-RFOU R, SKIENA S. Deepwalk: Online Learning of Social Representations[C]// ACM. 20th ACM SIGKDD International Conference on Knowledge Discovery and Data Mining,August 24-27, 2014, New York, USA. New York: ACM, 2009: 701-710. |
| [13] | TANG Jian, QU Meng, WANG Mingzhe, et al. Line: Large-Scale Information Network Embedding[C]// ACM. 24th International Conference on World Wide Web, May 18-22, 2015, Florence, Italy. New York: ACM, 2015: 1067-1077. |
| [14] | WANG Daxin, CUI Peng, ZHU Wenwu. Structural Deep Network Embedding[C]// ACM. 22nd ACM SIGKDD International Conference on Knowledge Discovery and Data Mining,August 13-17, 2016, San Francisco, California, USA. New York: ACM, 2016: 1225-1234. |
| [15] | GROVER A, LESKOVEC J. Node2vec: Scalable Feature Learning for Networks[C]// ACM. 22nd ACM SIGKDD International Conference on Knowledge Discovery and Data Mining,August 13-17, 2016, San Francisco, California, USA. New York: ACM, 2016: 855-864. |
| [16] | RIBEIRO L F R, SAVERESE P H P, FIGUEIREDO D R. Struc2vec: Learning Node Representations from Structural Identity[C]// ACM. 23rd ACM SIGKDD International Conference on Knowledge Discovery and Data Mining,August 13-17, 2017, Halifax, Nova Scotia, Canada. New York: ACM, 2017: 385-394. |
| [17] |
WHITE H. Maximum Likelihood Estimation of Misspecified Models[J]. Econometrica: Journal of the Econometric Society, 1982,50(1):1-25.
doi: 10.2307/1912526 URL |
| [18] | SALTON G, MCGILL M J. Introduction to Modern Information Retrieval[M]. Auckland: MuGraw-Hill, 1983. |
| [19] | ROSSI R A, AHMED N K. The Network Data Repository with Interactive Graph Analytics and Visualization[C]// AAAI. 29th AAAI Conference on Artificial Intelligence, January 25-30, 2015, Austin, Texas, USA. California: AAAI, 2015: 4292-4293. |
| [20] | BROWN J D. Principal Components Analysis and Exploratory Factor Analysis-Definitions, Differences, and Choices[J]. JALT Testing & Evaluation SIG Newsletter, 2009,13(1):26-30. |
| [1] | 莫靖杰, 屠晨阳, 彭佳, 袁珺. 基于多源信息融合的社交网络挖掘[J]. 信息网络安全, 2017, 17(9): 73-76. |
| [2] | 马国峻, 李凯, 裴庆祺, 詹阳. 一种社交网络中细粒度人脸隐私保护方案[J]. 信息网络安全, 2017, 17(8): 26-32. |
| [3] | 刘浩, 陈志刚, 张连明. 基于社区的移动社交网络安全路由算法设计与实现[J]. 信息网络安全, 2017, 17(7): 25-31. |
| [4] | 杨艳萍. 基于双向加权图的社交网络用户可信度算法研究[J]. 信息网络安全, 2017, 17(7): 40-44. |
| [5] | 李晴, 叶阿勇, 许力. 社交网络中基于定位欺骗的隐私攻击研究[J]. 信息网络安全, 2017, 17(5): 51-56. |
| [6] | 熊金波, 马蓉, 张媛媛, 戴睿煜. 面向社交网络的图片信息隐藏方法与实现[J]. 信息网络安全, 2017, 17(3): 6-8. |
| [7] | 罗梁, 王文贤, 钟杰, 王海舟. 跨社交网络的实体用户关联技术研究[J]. 信息网络安全, 2017, 17(2): 51-58. |
| [8] | 许为, 林柏钢, 林思娟, 杨旸. 一种基于用户交互行为和相似度的社交网络社区发现方法研究[J]. 信息网络安全, 2015, 15(7): 77-83. |
| [9] | 李旬, 徐剑, 焦英楠, 严寒冰. 基于异常特征的社交网页检测技术研究[J]. 信息网络安全, 2015, 15(5): 41-46. |
| [10] | 王乐, 王勇, 王东安, 徐小琳. 社交网络中信息传播预测的研究综述[J]. 信息网络安全, 2015, 15(5): 47-55. |
| [11] | 陈学敏, 沙灜. 基于浏览器测试组件的社交网络数据获取技术研究[J]. 信息网络安全, 2015, 15(5): 56-61. |
| [12] | . 社交网Twitter平台的人物关系网社区发现[J]. , 2014, 14(5): 32-. |
| [13] | 薛一波;鲍媛媛;易成岐. SPNR:社交网络中的新型谣言传播模型[J]. , 2014, 14(1): 0-0. |
| [14] | 吴成钢;杨光;张翔;王晓欢. 推荐系统的应用及其安全性研究[J]. , 2011, 11(8): 0-0. |
| [15] | 单成现. Web2.0时代SNS与国家安全问题研究[J]. , 2011, 11(6): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||