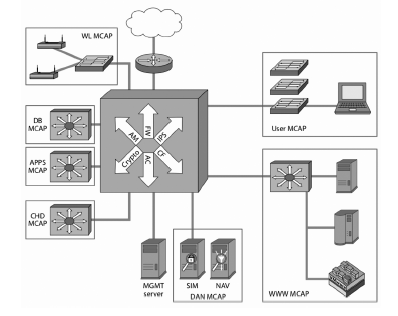
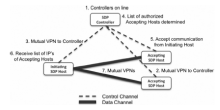
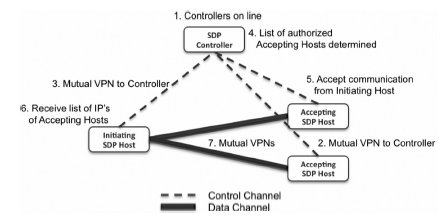
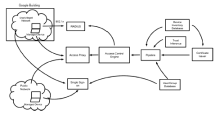
| [1] |
MORGANS.2017 Cybercrime Report[EB/OL].
|
| [2] |
Ponemon Institute.2017 Cost of Data Breach Study[EB/OL].
|
| [3] |
MOORE S. Gartner Says Worldwide Information Security Spending Will Grow 7 Percent to Reach $86.4 Billion in 2017[EB/OL]. , 2017-8-16.
|
| [4] |
KINDERVAG J. Build Security into Your Network’s Dna: The Zero Trust Network Architecture[EB/OL]. , 2010-11-5.
|
| [5] |
BILGERB, et al. Software Defined Perimeter[EB/OL]. , 2013-11-15.
|
| [6] |
GARBIS J, THAPLIYAL P, et al. Software Defined Perimeter for Infrastructure as a Service[EB/OL]. .2016-9-30.
|
| [7] |
WARD R, BETSY B.Beyondcorp: A New Approach to Enterprise Security[J]. Login, 2014, 39(6): 6-11.
|
| [8] |
OSBORN B, MCWILLIAMSJ , et al. BeyondCorp: Design to Deployment at Google[J]. Login, 2016, 41(1): 28-34.
|
| [9] |
CUNNINGHAMC. The Forrester Wave™: Zero Trust eXtended(ZTX) Ecosystem Providers, Q4 2018[EB/OL]. , 2018-11-8.
|
| [10] |
GARBISJ.BeyondCorp, Zero Trust, SDP & a Grand Unified Theory of Network Security[EB/OL]. , 2017-11-9.
|
| [11] |
Duo Security. Duo Beyond Overview[EB/OL]. 2019-4-3.
|
| [12] |
GREALISHG, Digging Deeper into Zero Trust[EB/OL]. .2019-1-8.
|
| [13] |
WRIGHT E. When Zero Trust is a Good Thing: VMware NSX Security[EB/OL]. , 2014-1-12.
|
| [14] |
MACDONALD N. Zero Trust Is an Initial Step on the Roadmap to CARTA[EB/OL]. , 2018-11-10.
|
| [15] |
Security Primer. Why Zero Trust Trumps Traditional Security[EB/OL]. , 2019-4-10.
|
| [16] |
STEVENS R.TCP/IP Illustrated vol. I: The Protocols[M]. Boston: Addison-Wesley Professional, 2011.
|
| [17] |
BELLOVIN M.Security Problems in the TCP/IP Protocol Suite[J]. ACM SIGCOMM Computer Communication Review, 2002, 19(2): 32-48.
|
| [18] |
HUNT R.Internet/Intranet Firewall Security—Policy, Architecture and Transaction Services[J]. Computer Communications, 1998, 21(13): 1107-1123.
|
| [19] |
STALLINGS W, BROWNL , BAUER M D, el al. Computer Security: Principles and Practice[M]. London: Pearson Education, 2007.
|
| [20] |
FU Z, et al.IPSec/VPN Security Policy: Correctness, Conflict Detection, and Resolution[C]//Springer. International Workshop on Policies for Distributed Systems and Networks. January 29-31, 2001, Bristol, United Kingdom. Berlin: Springer, 2001: 39-56.
|
| [21] |
HAMEDH, AL-SHEAR E, et al. Modeling and Verification of IPSec and VPN Security Policies[C]//IEEE. 13th IEEE International Conference on Network Protocols(ICNP’05). November 5-9, 2005, Boston, MA, USA. NewYork: IEEE, 2005: 259-278.
|
| [22] |
HUNYADY J, et al. Routing VoIP Calls through Multiple Security Zones. U.S. Patent No. 8,200,827[P].2012-6-12.
|
| [23] |
CHERIAN A. Why Conditional Access Is Essential to Zero Trust Security[EB/OL]. , 2019-6-19.
|
| [24] |
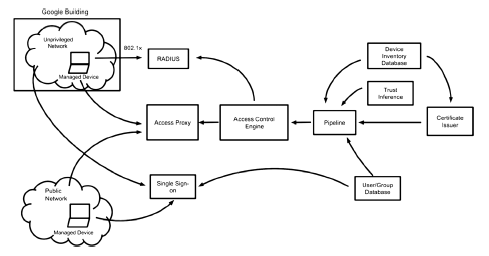
TISHBI L, GOELP, MCWILLIAMS J. How Google Adopted BeyondCorp[EB/OL]. , 2019-6-27.
|
| [25] |
ROY J, PARADIS S, et al. Threat Evaluation for Impact Assessment in Situation Analysis Systems[EB/OL]. , 2002-7-15.
|