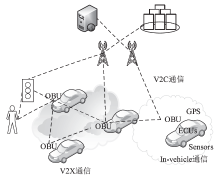
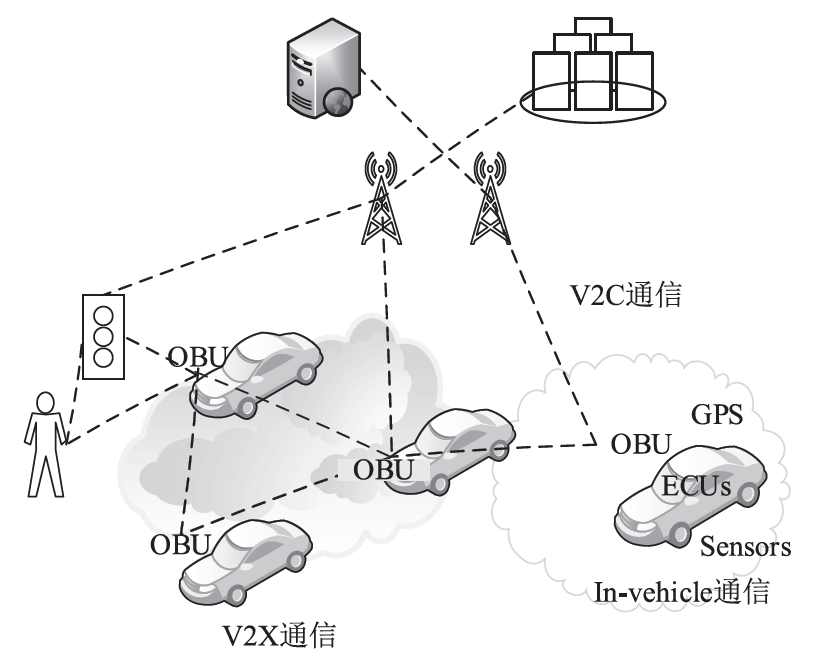
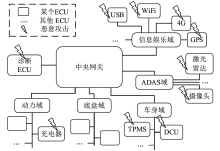
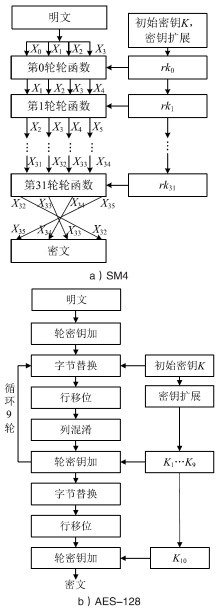
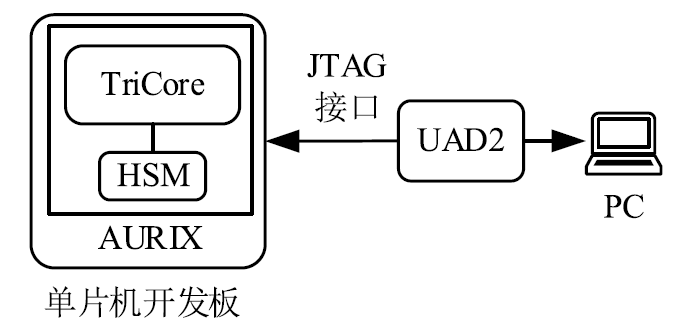
信息网络安全 ›› 2019, Vol. 19 ›› Issue (8): 68-75.doi: 10.3969/j.issn.1671-1122.2019.08.010
国密算法和国际密码算法在车载单片机上应用的对比研究
- 同济大学,上海 201800
-
收稿日期:2019-03-02出版日期:2019-08-10发布日期:2020-05-11 -
作者简介:作者简介:吴志红(1961—),男,浙江,教授,博士,主要研究方向为电机传动、嵌入式系统安防机制;赵建宁(1989—),男,河南,博士研究生,主要研究方向为汽车网络安全防护、车载安全协议、密码学应用;朱元(1976—),男,江苏,副教授,博士,主要研究方向为电机传动、汽车功能安全、信息安全;陆科(1983—),男,江苏,博士,主要研究方向为汽车功能安全、信息安全。
-
基金资助:国家重点研发计划[2017YFE0101400]
Comparative Study on Application of Chinese Cryptographic Algorithms and International Cryptographic Algorithms in Vehicle Microcotrollers
Zhihong WU, Jianning ZHAO( ), Yuan ZHU, Ke LU
), Yuan ZHU, Ke LU
- Tongji University, Shanghai 201800, China
-
Received:2019-03-02Online:2019-08-10Published:2020-05-11
摘要:
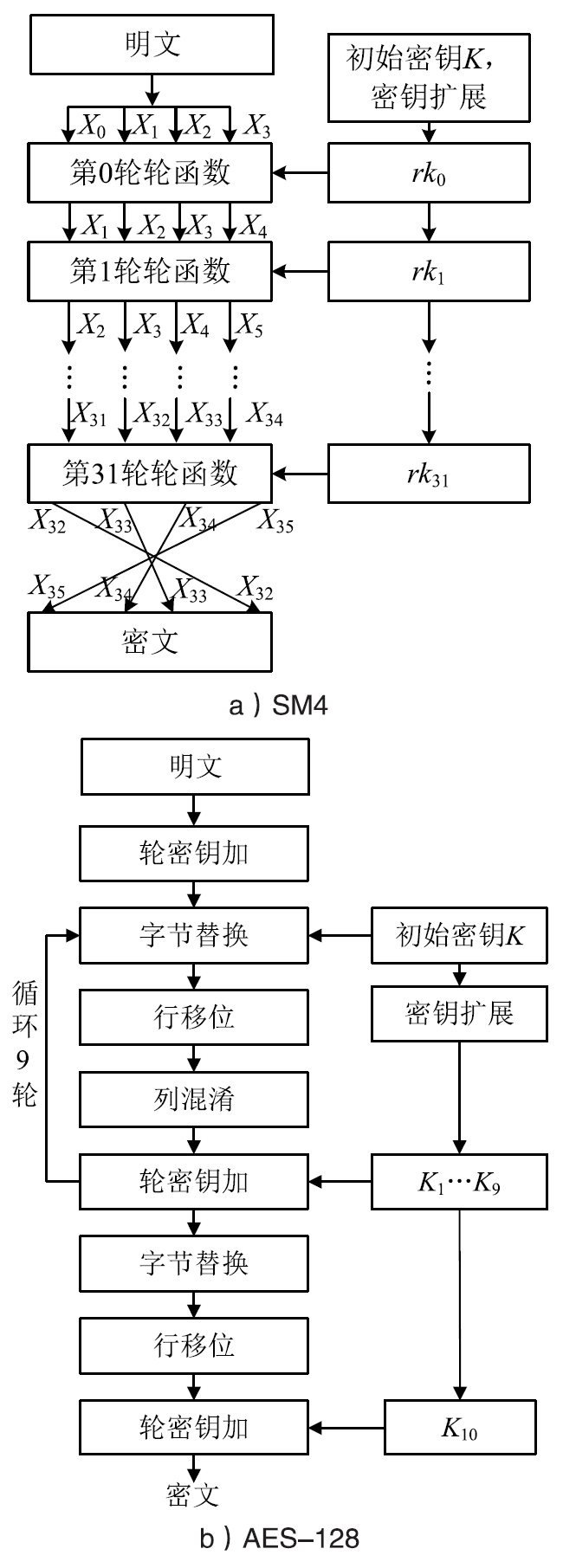
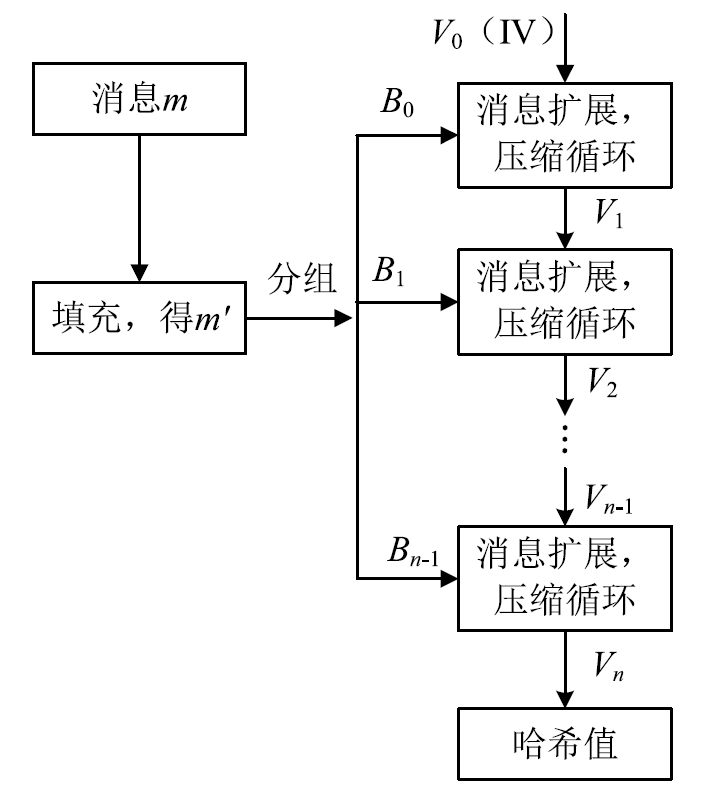
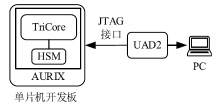
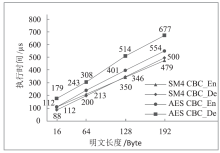
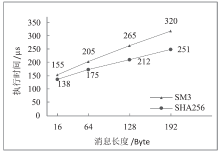
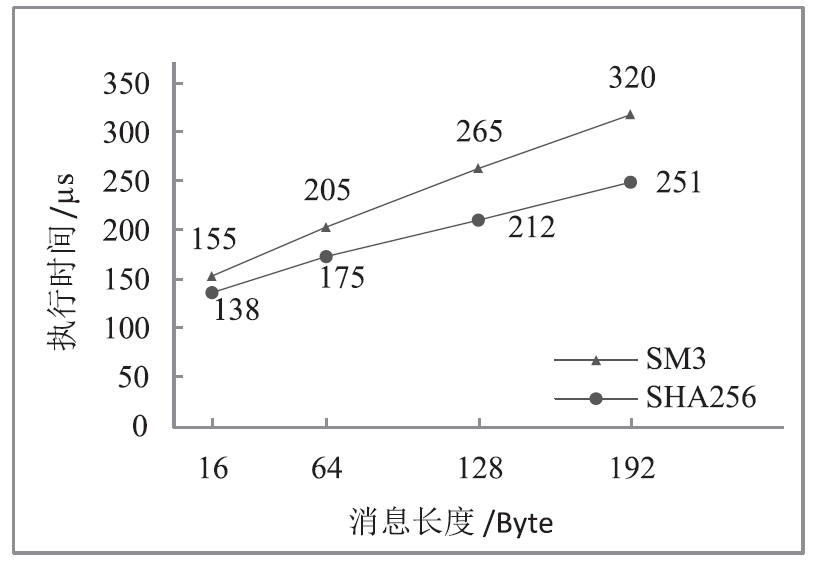
文章介绍了车载网络安全和密码学应用的研究现状,结合前人的研究分析了国密SM4、SM3、SM2算法和对应国际密码算法的差异。在可编程的硬件加密模块上进行实验,从软件执行时间、运行内存占用等方面对比了国密算法和国际密码算法的性能。结果表明,国密SM系列算法和对应国际密码算法占用大小相当的运行内存,任何一种国密算法和对应的国际密码算法在软件执行速度方面都存在差异,但算法执行时间的差别最大不超过31%。文章研究可为基于国密算法的车载和车联网安全通信提供基础,也可为开发国密算法的硬件加密模块提供参考。
中图分类号:
引用本文
吴志红, 赵建宁, 朱元, 陆科. 国密算法和国际密码算法在车载单片机上应用的对比研究[J]. 信息网络安全, 2019, 19(8): 68-75.
Zhihong WU, Jianning ZHAO, Yuan ZHU, Ke LU. Comparative Study on Application of Chinese Cryptographic Algorithms and International Cryptographic Algorithms in Vehicle Microcotrollers[J]. Netinfo Security, 2019, 19(8): 68-75.
| [1] | XIA Ziyan, ZHOU Zhitong, LI Xiang, et al.Feasibility Study on Automobile Electronic Control System of ECU Intrusion and Virus[J]. Netinfo Security, 2014, 14(9): 193-195. |
| 夏子焱,周之童,李响,等.汽车ECU电控系统入侵与汽车病毒编写的可行性研究[J].信息网络安全,2014,14(9):193-195. | |
| [2] | STALLINGS W.Network Security and Essentials: Applicaiotn and Standards[M]. BAI Guoqiang, et al. 5th Version. Beijing: Tsinghua University Press, 2014. |
| 威廉姆斯·斯托林斯.网络安全基础应用与标准[M].白国强,等译. 5版.北京:清华大学出版社,2014. | |
| [3] | BELLARE M, ROGAWAY P.Entity Authentication and Key Distribution[C]//IEEE. 13th Annual International Cryptology Conference, August 22-26, 1993, Santa Barbara, CA. New Jersey: IEEE, 1994: 232-249. |
| [4] | KOSCHER K, CZESKIS A, ROESNER F, et al.Experimental Security Analysis of a Modern Automobile[C]//IEEE. 31st Symposium on Security and Privacy, May 16-19, 2010, Oakland, CA. New Jersey: IEEE, 2010: 447-462. |
| [5] | LIN C W, SANGIOVANNI-VINCENTELLI A.Cyber-security for the Controller Area Network(CAN) Communication Protocol[C]//IEEE. 2012 ASE International Conference on Cyber Security, December, 14-16, 2012, Washington, DC. New Jersey: IEEE, 2012: 344-350. |
| [6] | HAMIDA E B, NOURA H, ZNAIDI W.Security of Cooperative Intelligent Transport Systems: Standards, Threats Analysis and Cryptographic Countermeasures[J]. Electronics, 2015, 4(3): 380-423. |
| [7] | WOO S, JO H J, LEE D H.A Practical Wireless Attack on the Connected Car and Security Protocol for In-vehicle CAN[J]. IEEE Transactions on Intelligent Transportation Systems, 2015, 16(2): 993-1006. |
| [8] | WOO S, JO H J, KIM I S, et al.A Practical Security Architecture for In-vehicle CAN-FD[J]. IEEE Transactions on Intelligent Transportation Systems, 2016, 17(8): 2248-2261. |
| [9] | LIU Zongbin, MA Yuan, JING Jiwu, et al.Implementation of SM3 Hash Function on FPGA[J]. Netinfo Security, 2011, 11(9): 191-193. |
| 刘宗斌,马原,荆继武,等. SM3哈希算法的硬件实现与研究[J].信息网络安全,2011,11(9):191-193. | |
| [10] | WANG Xiaoyun, YU Hongbo.SM3 Cryptographic Hash Algorithm[J]. Journal of Information Security Research, 2016, 2(11): 983-994. |
| [11] | SUN Rongyan, CAI Changshu, ZHOU Zhou, et al.The Comparision between Digital Signature Based on SM2 and ECDSA[J]. Network Security Technology & Application, 2013(2): 60-62. |
| [12] | ISO/IEC. IT Security Techniques—Digital Signatures with Appendix-Part 3: Discrete logarithm based mechanisms[EB/OL]. , 2019-1-6. |
| [13] | ISO/IEC. IT Security Techniques-Hash-functions-Part 3: Dedicated hash-functions[EB/OL]. , 2019-1-6. |
| [14] | GB/T 32918B/T 32918.1-2016. Information Security Technology—Public key Cryptographic Algorithm SM2 Based on Elliptic Curves[S]. Beijing: China Standards Press, 2017. |
| GB/T 32918B/T 32918.1-2016.信息安全技术 SM2椭圆曲线公钥密码算法[S].北京:中国标准出版社,2017. | |
| [15] | GB/T 32905-2016B/T 32905-2016. Information Security Technology—SM3 Crytographic Hash Algorithm[S]. Beijing: China Standards Press, 2016. |
| GB/T 32905-2016B/T 32905-2016.信息安全技术 SM3密码杂凑算法[S].北京:中国标准出版社,2016. | |
| [16] | GB/T 32907-2016 Information Security Technology—SM4 Block Cipher Algorthm[S]. Beijing: China Standards Press, 2016. |
| GB/T 32907-2016B/T 32907-2016.信息安全技术 SM4分组密码算法[S].北京:中国标准出版社,2016. | |
| [17] | YUKI H.Graphical Cryptography[M]. ZHOU Ziheng. 3nd Version. Beijing: Posts & Telecom Press, 2016. |
| 结城浩. 图解密码技术[M].周自恒,译. 3版.北京:人民邮电出版社,2016. | |
| [18] | PAAR C, PELZL J.Understanding Cryptography: A Textbook for Students and Practitioners[M]. MA Xiaoting. 1st Version. Beijing: Tsinghua University Press, 2012. |
| 克里斯托弗·帕尔,丹·佩尔茨尔.深入浅出密码学:常用密码技术原理及应用[M].马小婷,译. 1版.北京:清华大学出版社,2012. | |
| [19] | ANSI. Public Key Cryptography for the Financial Services Industry—The Elliptic Curve Digital Signature Algorithm[EB/OL]. , 2019-1-6. |
| [20] | ARTHUR W, CHANLLENER D.A Practical Guide to TPM 2.0: Using the Trusted Platform Module in the New Age of Security[M]. WANG Juan, YU Fajiang, YAN Fei, et al. Beijing: China Machine Press, 2017. |
| 威尔·亚瑟,大卫·查林纳. TPM 2.0原理及应用指南:新安全时代的可信平台模块[M].王娟,余发江,严飞,等译.北京:机械工业出版社,2017. | |
| [21] | HENNIGER O, RUDDLE A, SEUDIE H, et al. Securing Vehicular On-board IT Systems: The EVITA Project[EB/OL]. , 2019-1-3. |
| [22] | GB/T 32918B/T 32918.5-2017. Information Security Technology—Public Key Cryptographic Algorithm SM2 Based on Elliptic Curves—Part 5: Parameter Definition[S]. Beijing: China Standards Press, 2017. |
| GB/T 32918B/T 32918.5-2017.信息安全技术 SM2椭圆曲线公钥密码算法第5部分参数定义[S].北京:中国标准出版社,2017. | |
| [23] | Certicom Research. SEC 2: Recommended Elliptic Curve Domain Parameters[EB/OL]. . |
| [1] | 汪金苗, 王国威, 王梅, 朱瑞瑾. 面向雾计算的隐私保护与访问控制方法[J]. 信息网络安全, 2019, 19(9): 41-45. |
| [2] | 袁超, 张浩. 车联网中协作车--车通信系统在N-Rayleigh信道下ASEP性能分析[J]. 信息网络安全, 2016, 16(3): 40-46. |
| [3] | 李兆斌, 刘丹丹, 黄鑫, 曹浩. 基于国密算法的安全接入设备设计与实现[J]. 信息网络安全, 2016, 16(11): 19-27. |
| [4] | 徐凌伟, 张浩, 王景景, 吴春雷. 车联网中车—车通信系统在n-Rayleigh信道下的性能分析[J]. 信息网络安全, 2014, 14(12): 65-70. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||