信息网络安全 ›› 2015, Vol. 15 ›› Issue (4): 28-35.doi: 10.3969/j.issn.1671-1122.2015.04.005
基于速度动态差异的位置服务匿名算法
王勇, 高诗梦, 聂肖, 张俊浩
- 电子科技大学计算机科学与工程学院,四川成都 611731
-
收稿日期:2015-03-13出版日期:2015-04-10发布日期:2018-07-16 -
作者简介:作者简介: 王勇(1976-),男,四川,副教授,博士,主要研究方向:网络信息安全;高诗梦(1991-),女,黑龙江,硕士研究生,主要研究方向:网络信息安全;聂肖(1991-),男,安徽,硕士研究生,主要研究方向:网络信息安全;张俊浩(1992-),男,四川,硕士研究生,主要研究方向:网络信息安全。
-
基金资助:国家自然科学基金联合基金[U1230106]
A LBSs Cloaking Algorithm Based on Velocity Dynamic Variation
WANG Yong, GAO Shi-meng, NIE Xiao, ZHANG Jun-hao
- Department of Computer Science and Engineering, University of Electronic and Science Technology Chengdu Sichuan 611731, China
-
Received:2015-03-13Online:2015-04-10Published:2018-07-16
摘要:
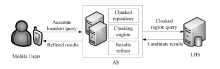
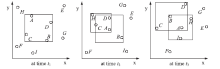
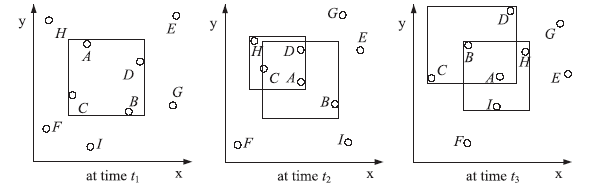
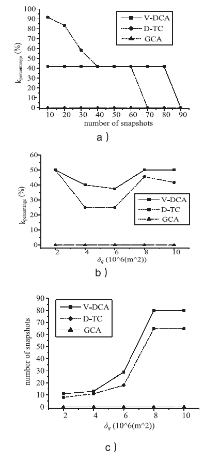
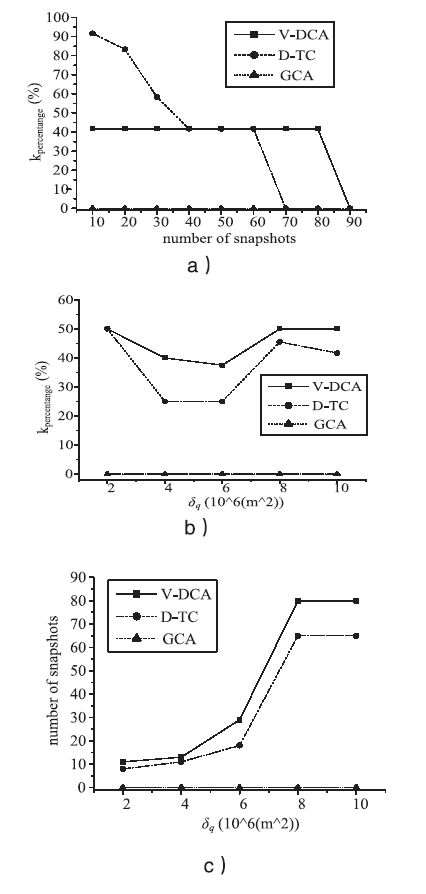
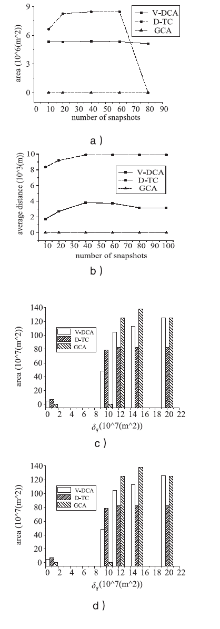
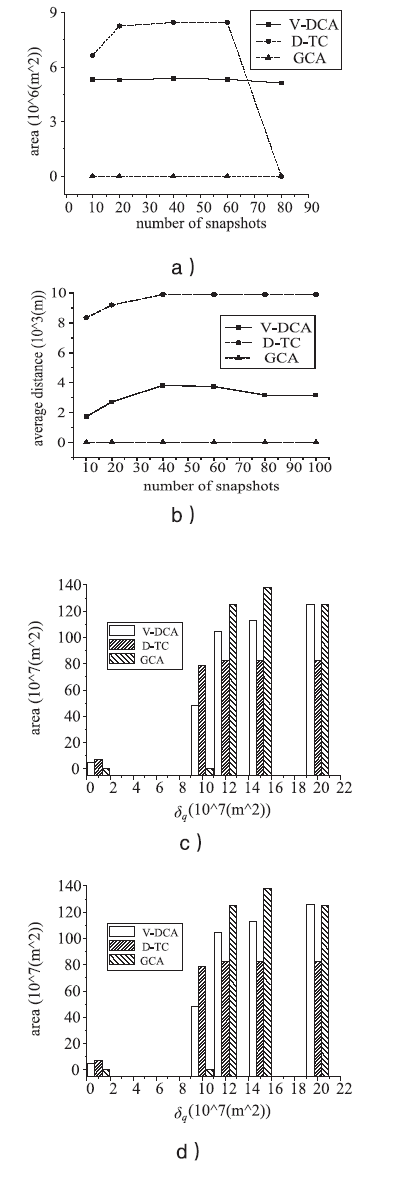
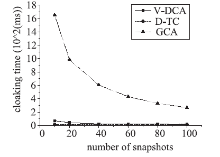
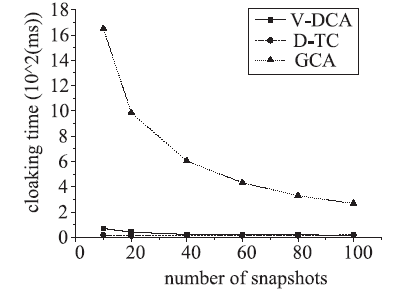
随着基于位置服务应用的日益流行,其潜在的用户隐私泄露问题也成为制约其发展的一大挑战。用户位置数据的泄露,可能导致与用户生活相关的活动、住址等隐私信息泄露,隐私问题成为位置服务中人们普遍关注的热门话题。尤其是在连续查询场景下,查询间存在着密切的联系,这就使得用户的隐私面临更大的威胁。针对这一问题,文章提出了一种连续查询下的隐私保护算法,称为基于速度的动态匿名算法(V-DCA)。在匿名处理时,考虑了用户的运动特征和趋势,也就是速度和加速度,并且利用历史匿名集合来产生新的匿名集合,在抵御查询跟踪攻击、保护隐私的同时提供了良好的服务质量。文章设计了一种连续查询隐私保护算法——基于速度的动态匿名算法(V-DCA),将用户的速度、加速度作为匿名条件之一,有效地平衡了隐私和服务质量;为了评价匿名算法,分别从隐私保障、服务质量和匿名时间3个方面提出了多个度量指标;通过在真实地图及相同环境下与其他匿名算法进行比较实验,验证了V-DCA在隐私保障、服务质量和响应时间方面的良好表现。
中图分类号:
引用本文
王勇, 高诗梦, 聂肖, 张俊浩. 基于速度动态差异的位置服务匿名算法[J]. 信息网络安全, 2015, 15(4): 28-35.
WANG Yong, GAO Shi-meng, NIE Xiao, ZHANG Jun-hao. A LBSs Cloaking Algorithm Based on Velocity Dynamic Variation[J]. Netinfo Security, 2015, 15(4): 28-35.
| [1] | GRUTESER M, GRUNWALD D.Anonymous Usage of Location-Based Services through Spatial and Temporal Cloaking[C]//Proceedings of MobiSys 2003: The First International Conference on Mobile Systems, Applications, and Service, USA, 2003. |
| [2] | CHOW C Y, MOKBEL M F.Enabling Private Continuous Queries for Revealed User Locations[C]//Proceedings of the 10th international conference on Advances in spatial and temporal databases, Springer-Verlag Berlin, Heidelberg, 2007. |
| [3] | XU J, DU J, TANG Xet al. Privacy-Conscious Location-Based Queries in Mobile Environments[J]. IEEE Transactions on Parallel and Distributed Systems, 2010, 21(3): 313-326. |
| [4] | PAN X, MENG X, XU J.Protecting Location Privacy against Location-Dependent Attack in Mobile Services[J]. Knowledge and Data Engineering, IEEE Transactions on, 2011, 24(8): 1506-1519. |
| [5] | GIS Mapping[EB/OL]. . |
| [6] | STENNETH L, YU P S.Global Privacy and Transportation Mode Homogeneity Anonymization in Location Based Mobile Systems with Continuous Queries[C]//Collaborative Computing: Networking, Applications and Worksharing (CollaborateCom), 2010 6th International Conference on, Chicago, 2010: 1-10. |
| [7] | PAN, MENG X, XU J.Distortion-Based Anonymity for Continuous Queries in Location-Based Mobile Services[C]//Proceedings of the 17th ACM SIGSPATIAL International Conference on Advances in Geographic Information Systems, New York, 2009. |
| [8] | PAN X, XIAO Z, MENG X F.Survey of Location Privacy-Preserving[J]. Journal of Computer Science and Frontiers, 2007, 1(3): 268-281. |
| [9] | KIDO H, YANAGISAWA Y, SATOH T.Protection of Location Privacy Using Dummies for Location-Based Services[C]//Data Engineering Workshops, 2005, 21st International Conference on, 2005. |
| [10] | MOKBEL M F, CHOW C Y, AREF W G.The New Casper: Query Processing for Location Services without Compromising Privacy[C]//Proceedings of the 32nd international conference on Very large data bases, Korea, 2006. |
| [11] | PINGLEY A, ZHANG N, FU X W, et al.Protection of Query Privacy for Continuous Location Based Services[C]//INFOCOM, 2011 Proceedings IEEE, Shanghai, 2011. |
| [12] | GEDIK B, LIU L.A Customizable k-Anonymity Model for Protecting Location Privacy[C]//ICDCS 2015: International Conference on Distributed Computing Systems, USA, 2005. |
| [13] | GEDIK B, LIU L.Protecting Location Privacy with Personalized k-Anonymity: Architecture and Algorithms[J]. IEEE TRANSACTIONS ON MOBILE COMPUTING, 20087, (1): 1-18. |
| [14] | LIU F, HUA K A, CAI Y.Query l-diversity in Location-Based Services[C]//Mobile Data Management: Systems, Services and Middleware, 2009. MDM '09. Tenth International Conference on, Taipei, 2009. |
| [15] | CHOW C Y, MOKBEL M F, LIU X.A Peer-to-Peer Spatial Cloaking Algorithm for Anonymous Location- Based Services[C]//Proceedings of the 14th annual ACM international symposium on Advances in geographic information systems, USA, 2006. |
| [16] | GHINITA G, KALNIS P, SKIADOPOULOS S.PRIVE: Anonymous Location-Based Queries in Distributed Mobile Systems[C]//In WWW ' 07: Proceedings of the 16th International Conference on World Wide Web, Canada, 2007. |
| [17] | DURR F, SKVORTSOV P, ROTHEMEL K.Position Sharing for Location Privacy in Non-trusted Systems[C]//Pervasive Computing and Communications (PerCom), 2011 IEEE International Conference on, Seattle, WA, 2011. |
| [18] | ZHONG S S, WU Y J, LUO Z, et al.A Two-tie Interaction Approach for Generating Cloaked Region in Location-Based Services[C]//Multimedia Information Networking and Security (MINES), 2011 Third International Conference on, SHANGHAI, 2011. |
| [19] | YIU M L, JENSEN C, HUANG X, et al.SpaceTwist: Managing the Trade-Offs Among Location Privacy, Query Performance, and Query Accuracy in Mobile Services[C]//Data Engineering, 2008. ICDE 2008, IEEE 24th International Conference on, Cancun, 2008. |
| [20] | XU T, CAI Y.Location Anonymity in Continuous Location Based Services[C]//Proceedings of the 15th annual ACM international symposium on Advances in geographic information systems, USA, 2007. |
| [21] | WANG Y, WANG L Y, FUNG B.Preserving Privacy for Location-Based Services with Continuous Queries[C]//Communications, 2009, ICC '09, IEEE International Conference on, Dresden, 2009. |
| [22] | SHOKRI R, THEODORAKOPOULOS G, BOUDEC J Y L, et al. Quantifying location privacy[C]//Security and Privacy (SP), 2011 IEEE Symposium on, Berkeley, 2011. |
| [23] | SHOKRI R, THEODORAKOPOULOS G, DANEZIS G, et al.Quantifying location privacy: The case of sporadic location exposure[C]// 11th International Symposium, PETS 2011, Canada, 2011. |
| [24] | CHEN X H, PANG J.Measuring Query Privacy in Location-Based Services[C]//CODASPY, USA, 2012. |
| [25] | Thomas Brinkhoff: Network-based Generator of Moving Objects[EB/OL]. . |
| [1] | 李增鹏, 王思旸, 王梅. 隐私保护近邻检测研究[J]. 信息网络安全, 2024, 24(6): 817-830. |
| [2] | 傅彦铭, 陆盛林, 陈嘉元, 覃华. 基于深度强化学习和隐私保护的群智感知动态任务分配策略[J]. 信息网络安全, 2024, 24(3): 449-461. |
| [3] | 宋玉涵, 祝跃飞, 魏福山. 一种基于AdaBoost模型的区块链异常交易检测方案[J]. 信息网络安全, 2024, 24(1): 24-35. |
| [4] | 许可, 李嘉怡, 蒋兴浩, 孙锬锋. 一种基于轮廓稀疏对抗的视频步态隐私保护算法[J]. 信息网络安全, 2024, 24(1): 48-59. |
| [5] | 赖成喆, 赵益宁, 郑东. 基于同态加密的隐私保护与可验证联邦学习方案[J]. 信息网络安全, 2024, 24(1): 93-105. |
| [6] | 俞惠芳, 乔一凡, 孟茹. 面向区块链金融的抗量子属性基门限环签密方案[J]. 信息网络安全, 2023, 23(7): 44-52. |
| [7] | 唐雨, 张驰. 一种基于Intel SGX的信息中心网络隐私保护方案[J]. 信息网络安全, 2023, 23(6): 55-65. |
| [8] | 杜卫东, 李敏, 韩益亮, 王绪安. 基于密文转换的高效通用同态加密框架[J]. 信息网络安全, 2023, 23(4): 51-60. |
| [9] | 尹曙, 陈兴蜀, 朱毅, 曾雪梅. 基于字符空间构造的域名匿名化算法[J]. 信息网络安全, 2023, 23(4): 80-89. |
| [10] | 郭瑞, 魏鑫, 陈丽. 工业物联网环境下可外包的策略隐藏属性基加密方案[J]. 信息网络安全, 2023, 23(3): 1-12. |
| [11] | 李晓华, 王苏杭, 李凯, 徐剑. 一种支持隐私保护的传染病人际传播分析模型[J]. 信息网络安全, 2023, 23(3): 35-44. |
| [12] | 张学旺, 张豪, 姚亚宁, 付佳丽. 基于群签名和同态加密的联盟链隐私保护方案[J]. 信息网络安全, 2023, 23(3): 56-61. |
| [13] | 王晶宇, 马兆丰, 徐单恒, 段鹏飞. 支持国密算法的区块链交易数据隐私保护方案[J]. 信息网络安全, 2023, 23(3): 84-95. |
| [14] | 李家辉, 秦素娟, 高飞, 孙东旭. 基于属性加密的区块链组织交易可控可监管隐私保护方案[J]. 信息网络安全, 2023, 23(12): 103-112. |
| [15] | 孙永奇, 宋泽文, 朱卫国, 赵思聪. 基于安全多方计算的图像分类方法[J]. 信息网络安全, 2023, 23(11): 27-37. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||