信息网络安全 ›› 2016, Vol. 16 ›› Issue (9): 278-284.doi: 10.3969/j.issn.1671-1122.2016.09.053
美国政企网络威胁情报现状及对我国的启示
- 公安部第一研究所,北京 100048
Analysis and Enlightenment of US Government and Enterprise Cyber Threat Intelligence
- The First Research Institute of Ministry of Public Security, Beijing 100048, China
摘要:
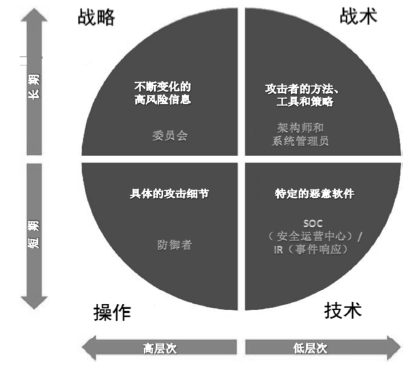
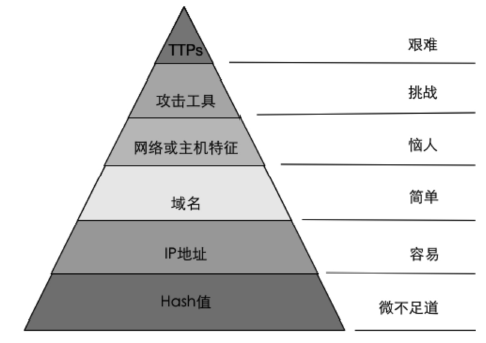
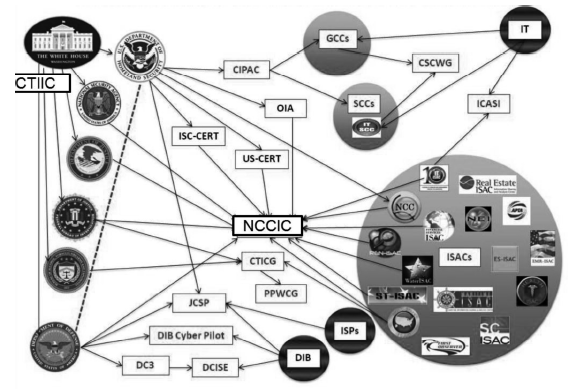
随着信息化和网络的高速发展,针对我国关键基础设施及政府网站等攻击事件高发,更为严峻的是各类网络攻击和网络威胁呈现持续性和扩大化的发展趋势。传统的被动式防御手段已经不能适应高级持续性威胁(APT)、0 day等新型网络威胁的防护,而威胁情报的出现弥补了这一不足。美国作为网络安全起步较早的国家,20世纪初就开始关注威胁情报,目前已经逐步建立起一套应对网络威胁的完整体系。文章对美国政府和企业的威胁情报现状进行系统研究,能够为我国政府和行业发展提供有益的参考和借鉴。首先,文章对威胁情报的定义和类型进行了分析。然后,围绕着美国政府针对网络威胁情报出台的相关法案和总统令、“爱因斯坦计划”、共享机制、开展的有关项目等五个方面进行了研究和分析。同时,对美国企业在威胁情报方面的开展的工作进行了概述。最后,文章在对中美网络威胁情报对比分析的基础上,提出了几点启示。
中图分类号: