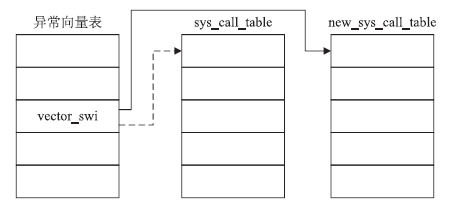
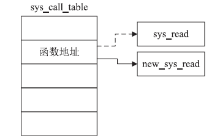
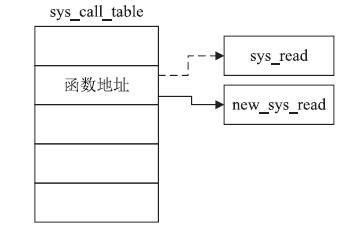
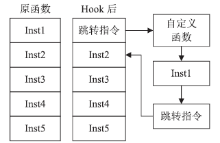
| [1] |
DANIELS T E, SPAFFORD E H.A Network Audit System for Host-based Intrusion Detection (NASHID) in Linux[C]//IEEE. 16th Annual Computer Security Applications Conference (ACSAC’00), December 11-15, 2000, New Orleans, LA. New Jersey: IEEE, 2000: 178-187.
|
| [2] |
WILLIAMS R. Performing a Successful UNIX Audit[J]. Computer Fraud & Security, 2003(8): 11-12.
|
| [3] |
ZHU Wenzheng, LEE C.Design for Security Operating System[C]//IEEE. 3rd Asia International Conference on Modelling Simulation (AMS 2009), May 25-29, 2009, Bali, Indonesia. New Jersey: IEEE, 2009: 667-670.
|
| [4] |
GUIDO M, ONDRICEK J, GROVER J, et al. Automated Identification of Installed Malicious Android Applications[EB/OL]. , 2016-2-11.
|
| [5] |
MITCHELL M, TIAN Guanyu, WANG Zhi.Systematic Audit of Third-party Android Phones[C]//ACM. 4th ACM Conference on Data and Application Security and Privacy, March 3-5, 2014, San Antonio, TX, USA. New York: ACM, 2014: 175-186.
|
| [6] |
李汶洋. Android操作系统恶意软件检测技术研究[J]. 信息网络安全,2015(9):62-65.
|
| [7] |
卢海阳. 数据完整性检测研究与实现[D]. 南京:东南大学,2014.
|
| [8] |
符蓉. Linux内核级Rootkit检测方法的研究与应用[D]. 长沙:湖南大学,2009.
|
| [9] |
刘旭. 恶意代码的检测技术研究[D].长春:吉林大学,2014.
|
| [10] |
赵光泽,李晖,孟杨. Android平台WebView组件安全及应用加固研究[J]. 信息网络安全,2015(10):61-65.
|
| [11] |
郑光明,胡博. 基于MD5的文件完整性检测软件设计[J]. 湖南理工学院学报(自然科学版),2007(1):35-38,64.
|
| [12] |
贾同彬,蔡阳,王跃武,等. 一种面向普通用户的Android APP安全性动态分析方法研究[J]. 信息网络安全,2015(9):1-5.
|
| [13] |
陈利,张利,班晓芳,等. Android下系统Rootkit检测技术研究[C]//中国信息安全测评中心.第六届信息安全漏洞分析与风险评估大会,2013-12-8,北京,中国. 北京:中国信息安全测评中心,2013:636-643.
|
| [14] |
ADAM K, BOHMAN P, SHAW E. VMM Based Rootkit Detection on Android[EB/OL]. , 2016-2-15.
|
| [15] |
杨永,钱振江,黄皓,等. 一种轻量级的Android内核保护监控器[J]. 计算机工程,2014,40(4):48-52.
|
| [16] |
孙泽民,芦天亮,周阳. 基于BGP 协议的TCP MD5加密认证的破解技术分析[J]. 信息网络安全,2015(9):37-40.
|
| [17] |
DHARMDASANI H. Android-Rootkit [EB/OL]. , 2015-11-25.
|
| [18] |
YOU D H, NOH B N.Android Platform Based Linux Kernel Rootkit[C]//IEEE. 6th International Conference on Malicious & Unwanted Software, October 18-19, 2011, Fajardo, Puerto Rico. New Jersey: IEEE, 2011: 79-87.
|
| [19] |
iRiqium, 赵润泽, 蒋旭宪. Oldboot.B:与Bootkit技术结合的木马隐藏手段的运用[EB/OL]. , 2015-11-25.
|
| [20] |
申迪. FakeDebuggerd Android rootkit分析报告[EB/OL]. , 2015-11-25.
|
| [21] |
李桂芝,韩臻,周启惠,等. 基于Binder信息流的Android恶意行为检测系统[J]. 信息网络安全,2016(2):54-59.
|
| [22] |
王松涛,吴灏. Linux下基于可执行路径分析的内核Rootkit检测技术研究[J]. 计算机工程与应用,2005,41(11):121-123.
|
| [23] |
韩芳. 基于可执行路径分析的隐藏进程检测方法[J]. 计算机与数字工程,2009,37(1):115-117.
|
| [24] |
王鼎. 高隐藏性木马的深度检测技术实现研究[D].成都:电子科技大学,2010.
|
 ), Zhipeng SUN, Shuai ZHU
), Zhipeng SUN, Shuai ZHU