信息网络安全 ›› 2016, Vol. 16 ›› Issue (3): 77-83.doi: 10.3969/j.issn.1671-1122.2016.03.013
二进制程序动态污点分析技术研究综述
- 公安部第三研究所信息网络安全公安部重点实验室, 上海 201204
-
收稿日期:2016-01-10出版日期:2016-03-25发布日期:2020-05-13 -
作者简介:作者简介: 宋铮(1986--),男,江苏,助理研究员,硕士,主要研究方向为信息安全,软件逆向分析;王永剑(1981--),男,山西,副研究员,博士,主要研究方向为信息安全;金波(1972--),男,浙江,研究员,博士,主要研究方向为网络空间安全;林九川(1980--),男,江苏,副研究员,硕士,主要研究方向为信息安全.
-
基金资助:公安部科技强警基础工作专项 [2013GABJC039]
Review on Dynamic Taint Analysis of Binary Programs
Zheng SONG, Yongjian WANG, Bo JIN, Jiuchuan LIN( )
)
- Key Laboratory of Information, Network and Security, Ministry of Public Security, The Third Research Institute of Ministry of Public Security, Shanghai 201204, China
-
Received:2016-01-10Online:2016-03-25Published:2020-05-13
摘要:
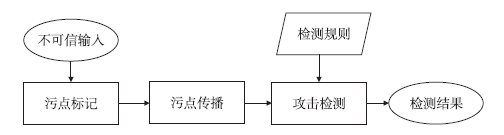
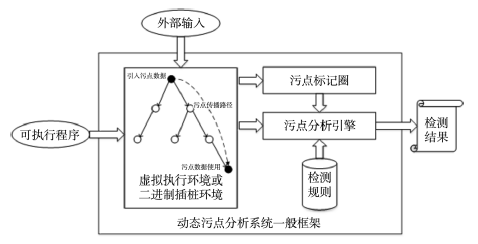
随着网络安全形势日趋严峻,针对基于漏洞利用的高级可持续威胁攻击,采用相应的攻击检测技术,及时有效地发现漏洞,进而保障网络基础设施及重要应用安全显得愈发重要.动态污点分析技术通过将非信任来源的数据标记为污点数据的方法,追踪其在程序执行过程中的传播路径,以达到获取关键位置与输入数据之间关联信息的目的,是检测漏洞利用攻击的有效技术方案之一.文章首先介绍了二进制程序动态污点分析技术的相关原理及在几种典型系统中的发展现状,随后分析了二进制程序动态污点分析技术现有的突出问题,最后介绍动态污点分析技术的应用情况.文章对二进制程序动态污点分析技术进行了系统介绍,有助于提升重要信息系统网络安全保护水平.
中图分类号:
引用本文
宋铮, 王永剑, 金波, 林九川. 二进制程序动态污点分析技术研究综述[J]. 信息网络安全, 2016, 16(3): 77-83.
Zheng SONG, Yongjian WANG, Bo JIN, Jiuchuan LIN. Review on Dynamic Taint Analysis of Binary Programs[J]. Netinfo Security, 2016, 16(3): 77-83.
| [1] | United States Federal Law. National Defense Authorization Act for Fiscal[EB/OL]. ,2015-10-15. |
| [2] | LAM M S, MARTIN M, LIVSHITS B, et al.Securing Web Applications with Static and Dynamic Information Flow Tracking[C]//ACM.The ACM SIGPLAN Symposium on Partial Evaluation and Semantics-based Program Manipulation, January 7-8, 2008,San Francisco, California, USA. New York:ACM,2008:2-3. |
| [3] | NEWSOME J, SONG D.Dynamic Taint Analysis for Automatic Detection, Analysis and Signature Generation of Exploits on Commodity Software[C]// NDSS '05. 12th Network and Distributed Systems Security Symposium, February 3-4 2005 ,San Diego,California. New York: ISOC,2005:1-14. |
| [4] | CLAUSE J, LI W, ORSO A.Dytan: A Generic Dynamic Taint Analysis Framework[C]//ACM.2007 International Symposium on Software Testing and Analysis, July 9-12, 2007,London, United Kingdom. New York:ACM,2007:196-206. |
| [5] | SONG D, BRUMLEY D, YIN H, et al.BitBlaze: A New Approach to Computer Security via Binary Analysis[C]// ICISS .4th International Conference on Information Systems Security, December 16-20, 2008, Hyderabad, India . Heidelberg:Springer,2008:1-25. |
| [6] | KEMERLIS V P, PORTOKALIDIS G, JEE K, et al.Libdft: Practical Dynamic Data Flow Tracking for Commodity Systems[J].Acm Sigplan Notices, 2002, 47(7):121-132. |
| [7] | DUMITRU C.Detecting Software Vulnerabilities Static Taint Analysis [D].Bucharest : University Politehnica of Bucharest, 2009. |
| [8] | CIFUENTES C. SCHOLZ B.Parfait-Designing a Scalable Bug Checker[C]//SAW '08. 2008 workshop on Static Analysis,June 7 - 13, 2008,Tucson, Arizona. New York:ACM,2008: 4-11. |
| [9] | JOVANOVIC N, KRUEGEL C, KIRDA E.Pixy: A Static Analysis Tool for Detecting Web Application Vulnerabilities[C]//IEEE. IEEE Symposium on Security and Privacy, May 21-24, 2006, Oakland, California . New Jersey: IEEE ,2006: 258-263. |
| [10] | DENNING D E.A Lattice Model of Secure Information Flow[J]. Communication of the ACM, 1976, 19(5):236-253. |
| [11] | 代伟,刘智,刘益和. 基于二进制代码的动态污点分析[J]. 计算机应用与研究, 2014, 31(8):2497-2505. |
| [12] | NETHERCOTE N, SEWARD J.Valgrind: A Framework for Heavyweight Dynamic Binary Instrumentation[J]. ACM Sigplan Notices,2007, 42(6):89-100. |
| [13] | NEWSOME J, MCCAMANT S, SONG D.Measuring Channel Capacity to Distinguish Undue Influence[C]// ACM .2009 ACM SIGPLAN Fourth Workshop on Programming Languages and Analysis for Security(PLAS), June 15-20,2009,Dublin, Ireland. New York:ACM,2009: 73-85. |
| [14] | YIN H, SONG D, EGELE M, et al.Panorama: Capturing System-wide Information Flow for Malware Detection and Analysis[C]//ACM.14th ACM conference on Computer and Communications Security,October 29,2007,Alexandria,VA. New York:ACM,2007:116-127. |
| [15] | PORTOKALIDIS G, SLOWINSKA A, BOS H. Argos: An Emulator for Fingerprinting Zero-Day Attacks[EB/OL].. |
| [16] | PORTOKALIDIS G, BOS H.Eudaemon: Involuntary and On-Demand Emulation Against Zero-Day Exploits[C]// ACM. EuroSys 2008,April 2-4,2008,Glasgow, Scotland. New York:ACM,2008:287-299. |
| [17] | CHOW J, PFAFF B, GARFINKEL T, et al.Understanding Data Lifetime via Whole System Simulation[C]//Usenix. 13th Usenix Security Symposium, August 9-13, 2004, San Diego, CA. Berkeley:Usenix , 2004: 321-336. |
| [18] | ZHU D, JUNG J, SONG D, et al.TaintEraser: Protecting Sensitive Data Leaks Using Application-Level Taint Tracking[J].Acm Sigops Operating Systems Review, 2011, 45(1):142-154 |
| [19] | EGELE M, KRUEGEL C, KIRDA E, et al. Dynamic Spyware Analysis[EB/OL]. . |
| [20] | SUH G E, LEE J W, ZHANG D, et al. Secure Program Execution via Dynamic Information Flow Tracking[EB/OL]. . |
| [21] | SHIYI W, RYDER B G.Practical Blended Taint Analysis for JavaScript[C]// ACM.2013 International Symposium on Software Testing and Analysis,July 15-20,2013,Lugano,Switzerland. New York:ACM,2013:336-346. |
| [22] | INIAN P, ENRICO B, SHWETA S, et al.DexterJS: Robust Testing Platform for DOM-based XSS Vulnerabilities[C]//ESEC/FSE,2015 10th Joint Meeting on Foundations of Software Engineering, August 30- September 4, 2015, Bergamo,Italy. New York:ACM, 2015:946-949. |
| [23] | NENTWICH F, JOVANOVIC N, KIRDA E, et al. Cross-site Scripting Prevention with Dynamic Data Tainting and Static Analysis[EB/OL].,2015-10-15. |
| [24] | JONATHAN B, GAIL K. Phosphor: Illuminating Dynamic Data Flow in Commodity JVMs[EB/OL].,2015-1-11. |
| [25] | ERIKA C, DAVID W, Efficient Character-level Taint Tracking for Java[C]//ACM.2009 ACM Workshop on Secure Web Services,November 9-13, 2009,Chicago, IL. New York:ACM,2009:3-12. |
| [26] | MCCLURG J, FRIEDMAN J, NG W. Android Privacy Leak Detection via Dynamic Taint Analysis[EB/OL].. |
| [27] | WILLIAM E, PETER G, BYUNG-GON C, et al.TaintDroid: An Information-flow Tracking System for Realtime Privacy Monitoring on Smartphones[J]. ACM Transactions on Computer Systems, 2010, 57(3):393-407. |
| [28] | GANESH V, LEEK T, RINARD M.Taint-based Directed Whitebox Fuzzing[C]//IEEE.31st International Conference on Software Engineering( ICSE), May 16-24 2009, Vancouver, BC. New Jersey:IEEE, 2009: 474-484 |
| [29] | WANG T L, WEI T, GU G, ZOU W.Checksum-Aware Fuzzing Combined with Dynamic Taint Analysis and Symbolic Execution[J]. ACM Transactions on Information and System Security (TISSEC), 2011, 14(2):613. |
| [30] | 陈力波,诸葛建伟,田繁,等.基于类型的动态污点分析技术研究[C]//中国信息安全测评中心.第五届信息安全漏洞分析与风险评估大会(VARA)论文集,2012-12-26,上海.北京:中国信息安全测评中心,2012:195-214. |
| [31] | GANAI M, LEE D, GUPTA A.DTAM: Dynamic Taint Analysis of Multi-threaded Programs for Relevancy[C]//ACM.ACM SIGSOFT 20th International Symposium on the Foundations of Software Engineering, November 11-16 ,2012,Cary, North Carolina. New York:ACM,2012:1-11. |
| [32] | CHABBI M. Efficient Dynamic Taint Analysis Using Multicore Machines[EB/OL]. ,2015-07-20. |
| [33] | HO A, FETTERMAN M, CLARK C, et al.Practical Taint-based Protection Using Demand Emulation[J]. EuroSys, 2006, 40(4): 29-41. |
| [1] | 刘建伟, 韩祎然, 刘斌, 余北缘. 5G网络切片安全模型研究[J]. 信息网络安全, 2020, 20(4): 1-11. |
| [2] | 赵志岩, 纪小默. 智能化网络安全威胁感知融合模型研究[J]. 信息网络安全, 2020, 20(4): 87-93. |
| [3] | 黎水林, 祝国邦, 范春玲, 陈广勇. 一种新的等级测评综合得分算法研究[J]. 信息网络安全, 2020, 20(2): 1-6. |
| [4] | 荆涛, 万巍. 面向属性迁移状态的P2P网络行为分析方法研究[J]. 信息网络安全, 2020, 20(1): 16-25. |
| [5] | 裘玥. 大型体育赛事网络安全风险分析与评估[J]. 信息网络安全, 2019, 19(9): 61-65. |
| [6] | 高孟茹, 谢方军, 董红琴, 林祥. 面向关键信息基础设施的网络安全评价体系研究[J]. 信息网络安全, 2019, 19(9): 111-114. |
| [7] | 陈良臣, 刘宝旭, 高曙. 网络攻击检测中流量数据抽样技术研究[J]. 信息网络安全, 2019, 19(8): 22-28. |
| [8] | 尚文利, 尹隆, 刘贤达, 赵剑明. 工业控制系统安全可信环境构建技术及应用[J]. 信息网络安全, 2019, 19(6): 1-10. |
| [9] | 张可, 汪有杰, 程绍银, 王理冬. DDoS攻击中的IP源地址伪造协同处置方法[J]. 信息网络安全, 2019, 19(5): 22-29. |
| [10] | 倪一涛, 陈咏佳, 林柏钢. 基于自动解混淆的恶意网页检测方法[J]. 信息网络安全, 2019, 19(4): 37-46. |
| [11] | 陈良臣, 高曙, 刘宝旭, 卢志刚. 网络加密流量识别研究进展及发展趋势[J]. 信息网络安全, 2019, 19(3): 19-25. |
| [12] | 傅建明, 黎琳, 郑锐, 苏日古嘎. 基于GAN的网络攻击检测研究综述[J]. 信息网络安全, 2019, 19(2): 1-9. |
| [13] | 韦力, 段沁, 刘志伟. 互联网时代医院网络安全管理综述[J]. 信息网络安全, 2019, 19(12): 88-92. |
| [14] | 张振峰, 张志文, 王睿超. 网络安全等级保护2.0云计算安全合规能力模型[J]. 信息网络安全, 2019, 19(11): 1-7. |
| [15] | 张健, 陈博翰, 宫良一, 顾兆军. 基于图像分析的恶意软件检测技术研究[J]. 信息网络安全, 2019, 19(10): 24-31. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||