信息网络安全 ›› 2016, Vol. 16 ›› Issue (1): 34-39.doi: 10.3969/j.issn.1671-1122.2016.01.007
一种基于TCP协议的网络隐蔽传输方案设计
娄嘉鹏1, 张萌1, 付鹏2, 张开2
- 1. 北京电子科技学院,北京 100070
2. 西安电子科技大学计算机学院,陕西西安 710071
Design of Network Covert Transmission Scheme Based on TCP
Jiapeng LOU1, Meng ZHANG1, Peng FU2, Kai ZHANG2
- 1. Beijing Electronic Science & Technology Institute, Beijing 100070, China
2. IT Academy, Xidian University, Xi’an Shaanxi 710071, China
摘要:
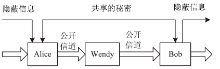
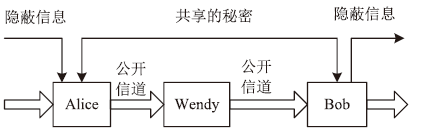
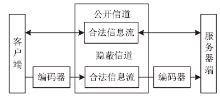
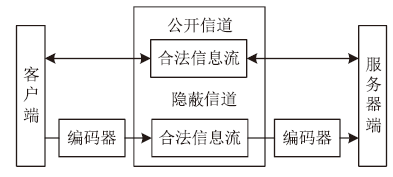
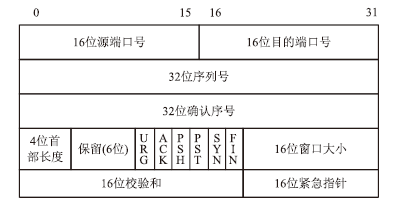
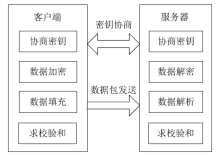
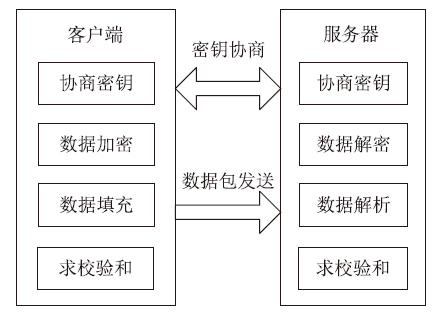
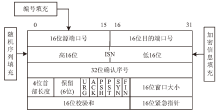
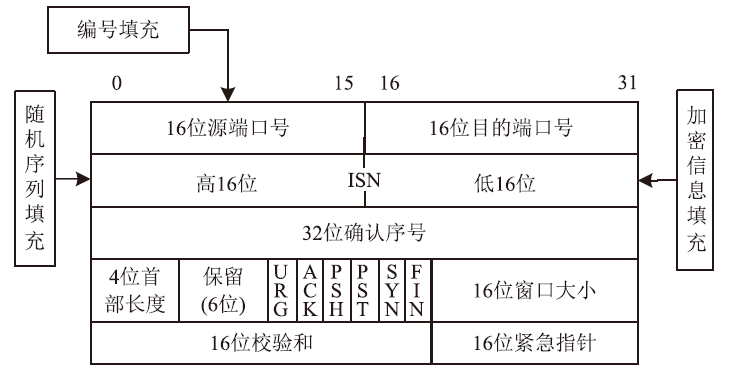
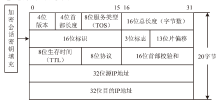
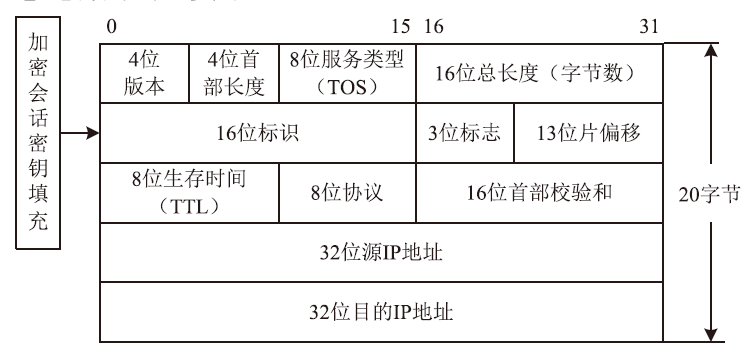
随着互联网的高速发展,以木马入侵为主的网络安全问题也越来越受到重视,隐蔽传输是木马等恶意代码利用的重要技术。网络隐蔽信道在带来危害的同时,也能带来正向利用,通过网络隐蔽信道可以进行信息的隐蔽、安全传输,也可以利用网络隐蔽信道对现有的系统防护设施性能进行测试,因此研究隐蔽信道对网络防护有着重要意义。文章通过研究网络协议、网络防护技术、网络隐蔽传输的实现原理和工作机制,网络协议本身存在的一些技术缺陷,通信系统的构成要素,提出了一种基于TCP协议的网络隐蔽传输方法,进而构建了一种网络隐蔽传输信道,该信道能够绕过防火墙和入侵检测系统进行隐蔽信息的传输。文章设计并实现了该方法,对该方法进行测试和验证,实验证明该信道的隐蔽性较高、传输速度较快,可实现信息的隐蔽传输,从而证明方案的可行性。该方法为防护木马等恶意攻击提供了理论依据和技术支持,在网络安全防护上有一定的意义。
中图分类号: