信息网络安全 ›› 2015, Vol. 15 ›› Issue (3): 59-63.doi: 10.3969/j.issn.1671-1122.2015.03.012
基于脚本注入的HTTPS会话劫持研究
- 1.四川大学电子信息学院,四川成都,610064
2.保密通信重点实验室,四川成都,610041
Research of HTTPS Session Hijacking Based on Script Injection
YANG Feng-fan1, LIU Jia-yong1( ), TANG Dian-hua2
), TANG Dian-hua2
- 1.College of Electronics and Information Engineering, Sichuan University, Chengdu Sichuan 610064, China
2.Science and Technology on Communication Security Laboratory , Chengdu Sichuan 610041, China
摘要:
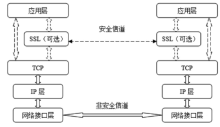
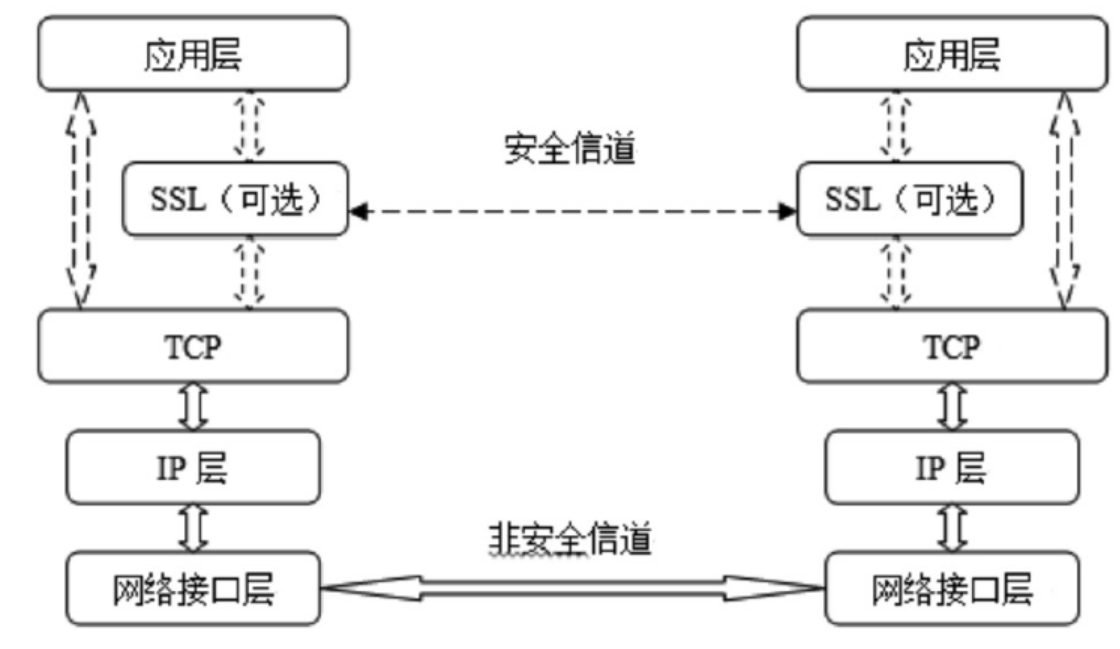
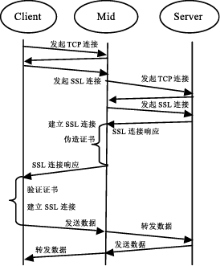
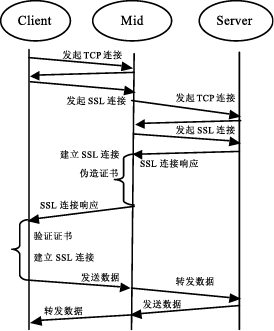
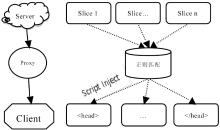
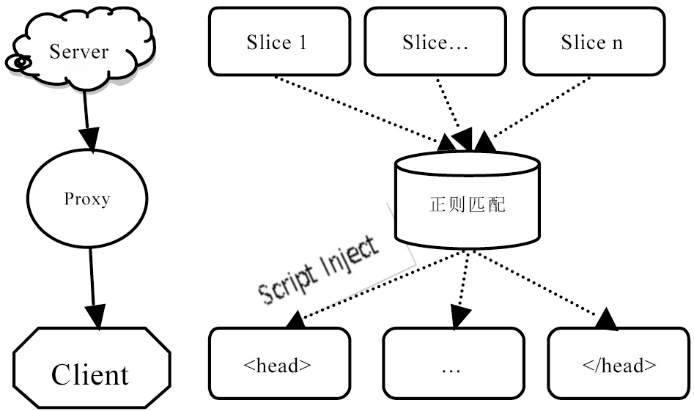
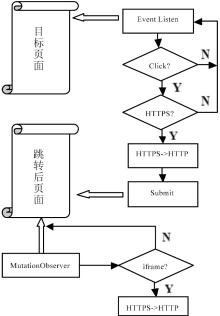
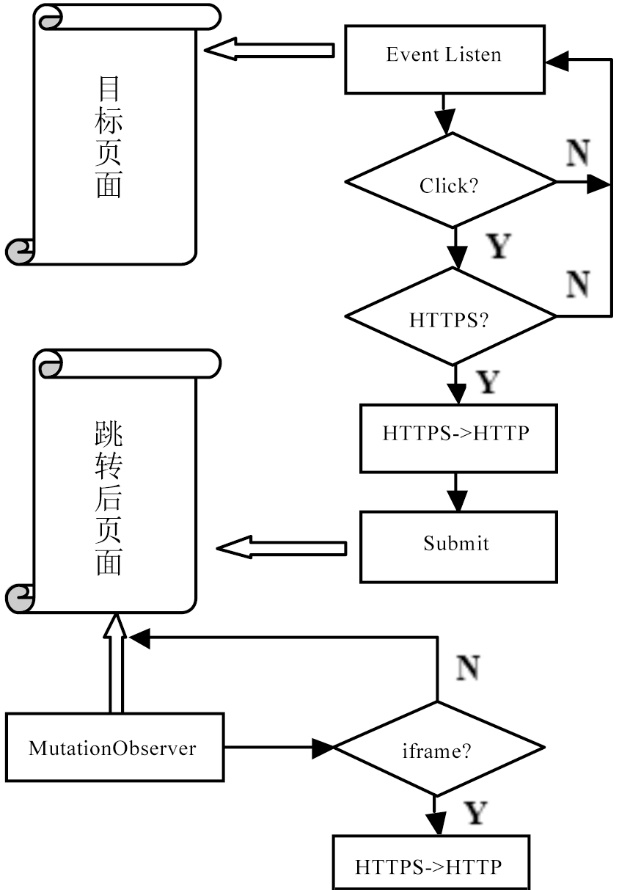
文章研究了目前主流的针对HTTPS会话劫持的手段,详细分析了基于伪造证书与HTTP跳转HTTPS漏洞而进行的劫持方法与流程,同时也给出了这些方法存在的优劣。目前广泛使用的方法是基于HTTP与HTTPS间的跳转漏洞,代理服务器利用中间人攻击与客户端建立HTTP连接,与服务器建立HTTPS连接,从而对整个数据流进行中转,获取用户通信数据。该种方法在PC端能够奏效,但移植到移动终端却效果不佳,主要是由于该种方法需要中间代理服务器对整个数据流进行监控,及时替换掉服务器响应中的HTTPS跳转,这就需要快速的匹配与转发。但是移动终端处理能力有限,很难达到这样的目的。目前,移动终端发展迅速,用户使用量逐渐增大,越来越的人注意到移动端的渗透测试。为了更好的在移动终端实现HTTPS的会话劫持,解决中间节点处理瓶颈问题。文章在dSploit的实现原理基础上,结合移动终端特定环境,提出了一种基于脚本注入的HTTPS会话劫持方法,有效的将中间人所需的替换工作转移到用户端进行,有效提高了中间端的处理性能。文章详细阐述了其实现原理与流程,更进一步分析出了HTTPS通信中可能存在的安全隐患,并对此提供了可行的防范措施。
中图分类号: