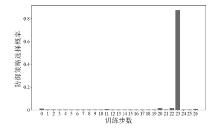
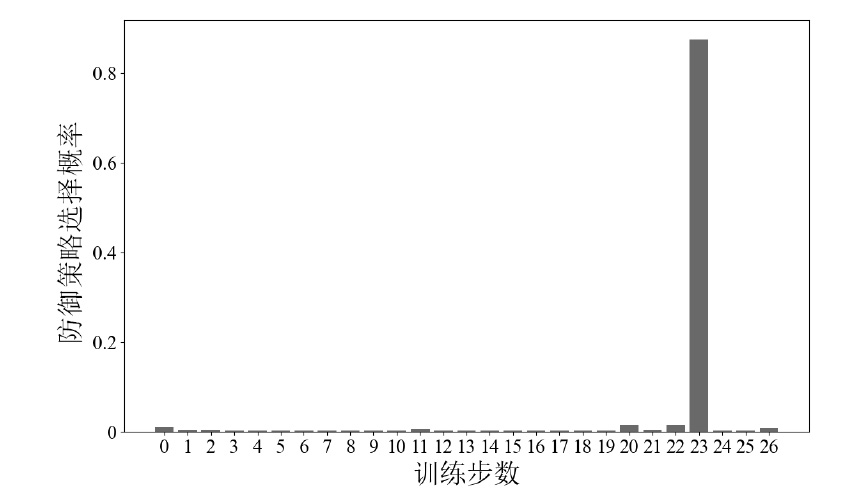
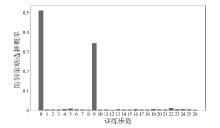
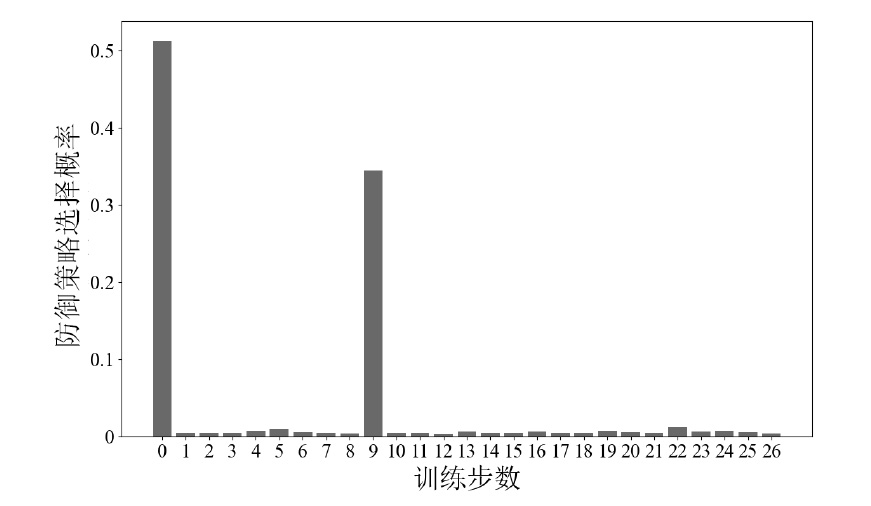
信息网络安全 ›› 2025, Vol. 25 ›› Issue (6): 967-976.doi: 10.3969/j.issn.1671-1122.2025.06.011
基于随机博弈和DQN算法的云原生移动目标防御决策方法
- 信息工程大学密码工程学院,郑州 450001
-
收稿日期:2025-01-16出版日期:2025-06-10发布日期:2025-07-11 -
通讯作者:张恒巍 zhw11qd@163.com -
作者简介:耿致远(1996—),男,河南,硕士研究生,主要研究方向为网络主动防御|许泽轩(2004—),男,陕西,本科,主要研究方向为网络空间安全|张恒巍(1978—),男,河南,教授,博士,主要研究方向为网络安全博弈、人工智能对抗攻击与防御。 -
基金资助:国家重点研发计划(2017YFB0801904)
A Decision-Making Method for Cloud-Native Moving Target Defense Based on Stochastic Games and DQN Algorithm
GENG Zhiyuan, XU Zexuan, ZHANG Hengwei( )
)
- School of Cryptography Engineering, Information Engineering University, Zhengzhou 450001, China
-
Received:2025-01-16Online:2025-06-10Published:2025-07-11
摘要:
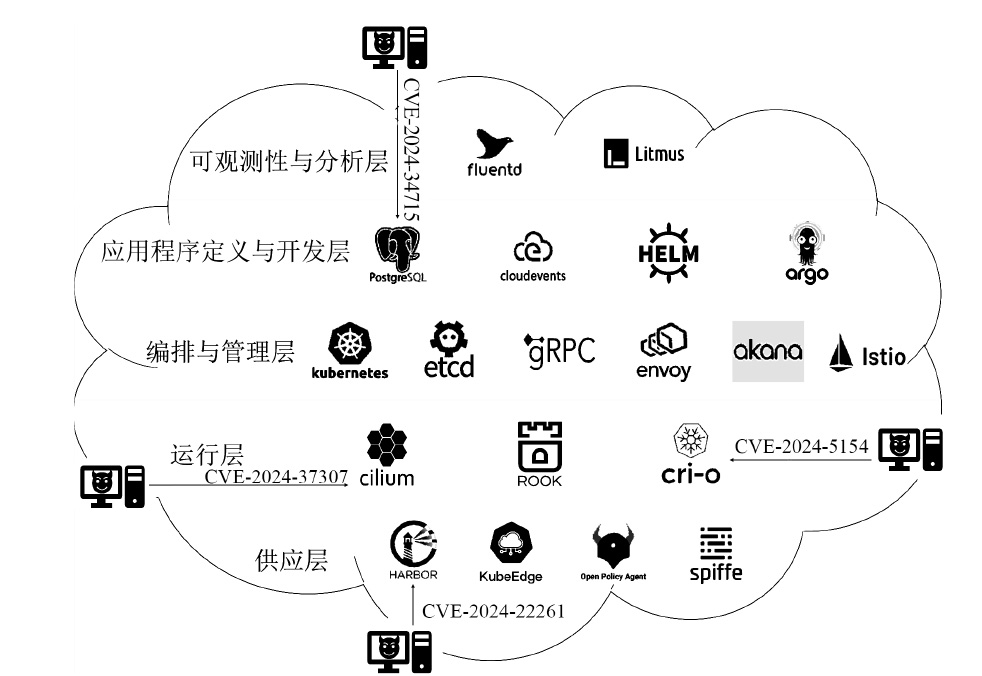
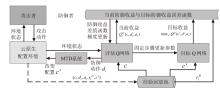
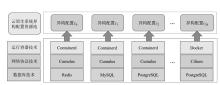
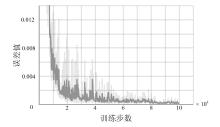
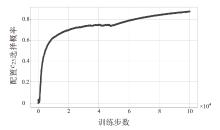
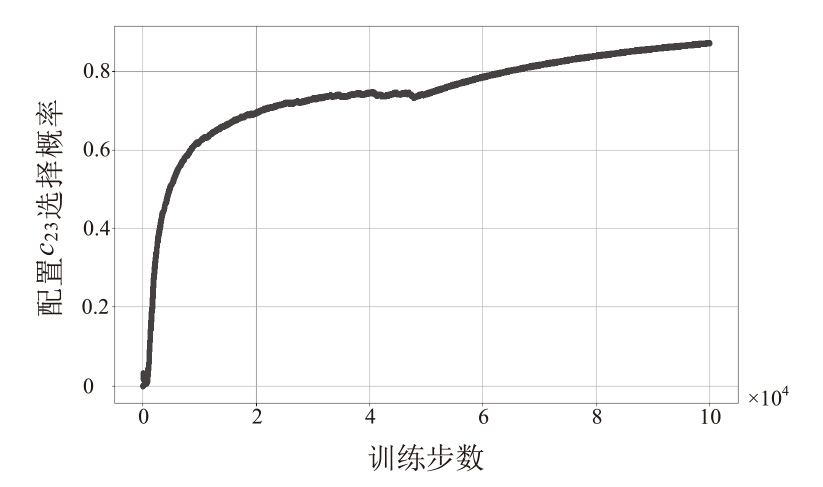
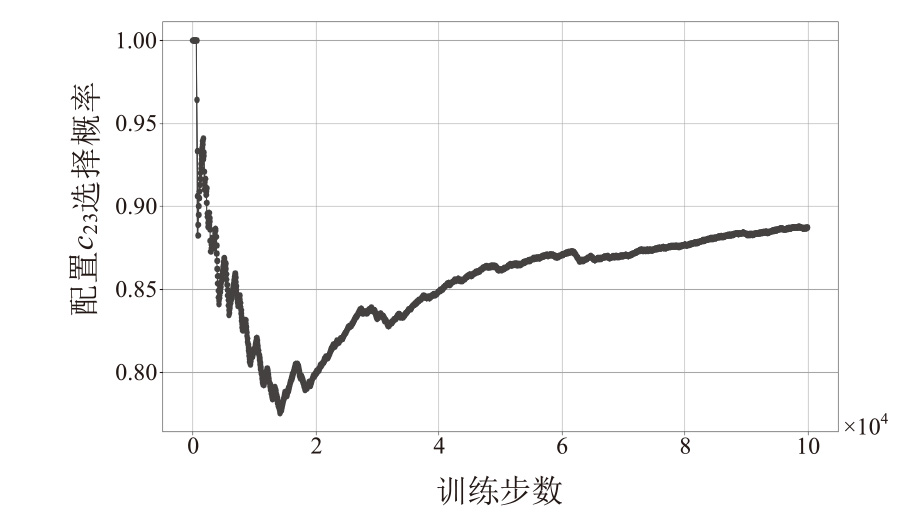
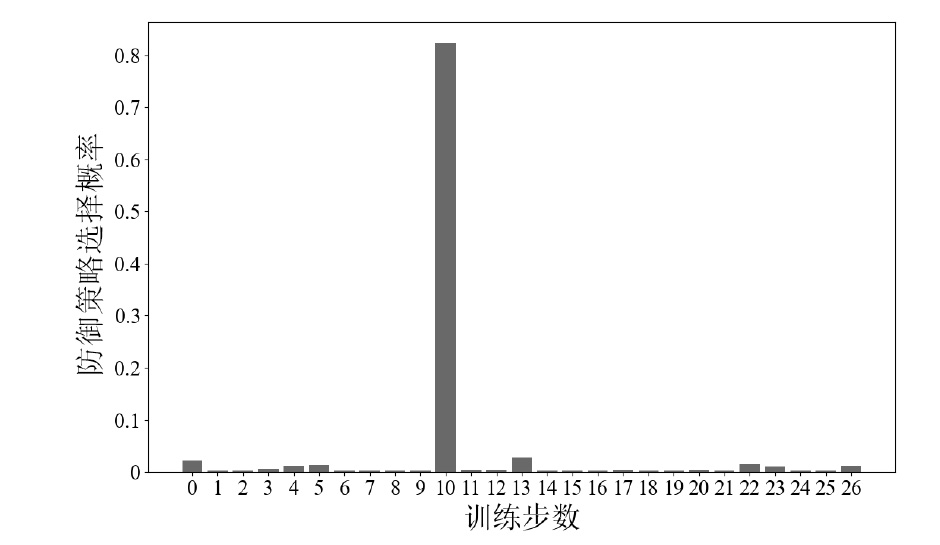
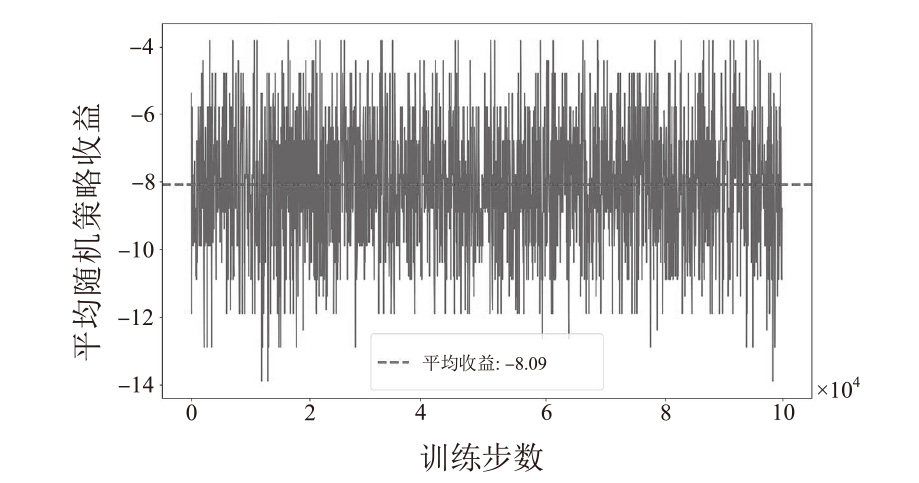
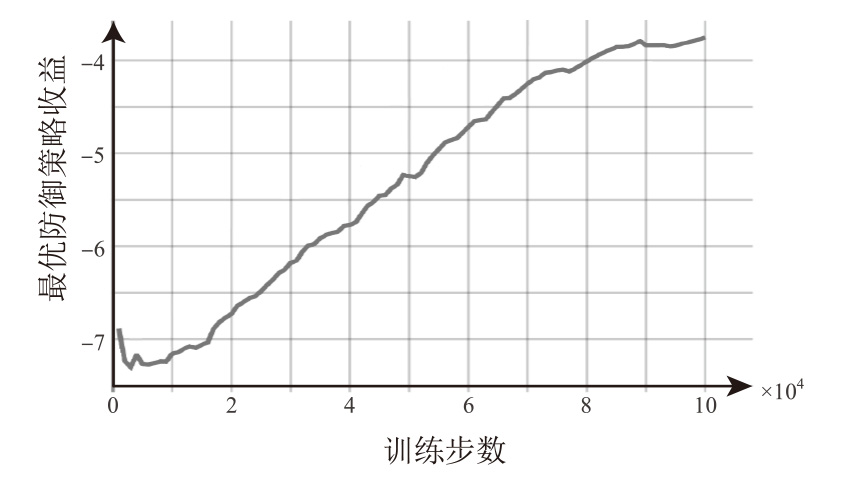
随着云原生系统中集成应用组件的复杂性不断提高,且大部分组件为开源代码,系统组件的漏洞利用已成为影响云原生安全的主要威胁之一。移动目标防御作为一种先进的动态防御机制,被广泛认为是应对该问题的有效手段。然而,在实际应用中,频繁且无序的配置转换可能会使系统运行效率和服务质量降低,进而对资源有限系统的安全性造成不利影响。为解决云原生环境中随机攻防场景下的移动目标防御决策问题,文章结合博弈理论的建模能力与深度强化学习的求解优势,提出一种基于随机博弈和DQN算法的云原生移动目标防御决策方法,实现在大规模策略空间中进行高效最优移动目标防御策略的决策,并通过仿真实验验证了文章所提方法的有效性和实用性。
中图分类号:
引用本文
耿致远, 许泽轩, 张恒巍. 基于随机博弈和DQN算法的云原生移动目标防御决策方法[J]. 信息网络安全, 2025, 25(6): 967-976.
GENG Zhiyuan, XU Zexuan, ZHANG Hengwei. A Decision-Making Method for Cloud-Native Moving Target Defense Based on Stochastic Games and DQN Algorithm[J]. Netinfo Security, 2025, 25(6): 967-976.
| [1] | China Academy of Information and Communications Technology. Cloud Computing White Paper[R]. Beijing: China Academy of Information and Communications Technology, No. 202404, 2024. |
| 中国信息通信研究院. 云计算白皮书[R]. 北京: 中国信息通信研究院, No. 202404,2024. | |
| [2] | LIANG Jinrong, CHEN Lijun, LI Zhihui, et al. Container Network Performance Anomaly Detection Based on Extended Berkeley Packet Filter and Machine Learning[C]// Springer. The International Conference on Natural Computation, Fuzzy Systems and Knowledge Discovery. Heidelberg: Springer. 2022: 1403-1415. |
| [3] | LI Dong, YU Junqing, WEN Ruibin, et al. Endogenous Security Methods for Container Cloud Based on IPv6[J]. Netinfo Security, 2023, 23(12): 21-28. |
| 李冬, 于俊清, 文瑞彬, 等. 基于IPv6的容器云内生安全机制[J]. 信息网络安全, 2023, 23(12): 21-28. | |
| [4] | AKSAKALLI I K, CELIK T, CAN A B, et al. Systematic Approach for Generation of Feasible Deployment Alternatives for Microservices[J]. IEEE Access, 2021(9): 29505-29529. |
| [5] | ZHOU Shucheng, LI Yang, LI Chuanrong, et al. Context-Based Abnormal Root Cause Algorithm[J]. Netinfo Security, 2024, 24(7): 1062-1075. |
| 周书丞, 李杨, 李传荣, 等. 基于上下文的异常根因算法[J]. 信息网络安全, 2024, 24(7): 1062-1075. | |
| [6] | REHMAN Z, GONDAL I, GE Mengmeng, et al. Proactive Defense Mechanism: Enhancing IoT Security through Diversity-Based Moving Target Defense and Cyber Deception[EB/OL]. (2024-04-01)[2024-12-30]. https://doi.org/10.1016/j.cose.2023.103685. |
| [7] | XU Hanyi, CHENG Guozhen, YANG Xiaohan, et al. Multi-Dimensional Moving Target Defense Method Based on Adaptive Simulated Annealing Genetic Algorithm[J]. Electronics, 2024, 13(3): 487-503. |
| [8] | AWARKEH A, EI-MALKI R, REBECCHI F. Moving Target Defense for Cloud-Native Applications[C]// IEEE. 2024 27th Conference on Innovation in Clouds, Internet and Networks (ICIN). New York: IEEE, 2024: 130-137. |
| [9] | ZHANG Shuai, GUO Yunfei, SUN Penghao, et al. Moving Target Defense Strategy Optimization Scheme for Cloud Native Environment Based on Deep Reinforcement Learning[J]. Journal of Electronics & Information Technology, 2023, 45(2): 608-616. |
| 张帅, 郭云飞, 孙鹏浩, 等. 云原生下基于深度强化学习的移动目标防御策略优化方案[J]. 电子与信息学报, 2023, 45(2): 608-616. | |
| [10] | TAN Jinglei, JIN Hui, ZHANG Hongqi, et al. A Survey: When Moving Target Defense Meets Game Theory[EB/OL]. (2023-05-01)[2024-12-30]. https://doi.org/10.1016/j.cosrev.2023.100544. |
| [11] | HU Yifan, XUN Peng, ZHU Peidong, et al. Network-Based Multidimensional Moving Target Defense against False Data Injection Attack in Power System[EB/OL]. (2021-08-11)[2024-12-30]. https://doi.org/10.1016/j.cose.2021.102283. |
| [12] | QIAN Yaguan, GUO Yankai, SHAO Qiqi, et al. EI-MTD: Moving Target Defense for Edge Intelligence against Adversarial Attacks[J]. ACM Transactions on Privacy and Security, 2022, 25(3): 1-24. |
| [13] | AYRAULT M, BORDE E, KUHNE U, et al. Moving Target Defense Strategy in Critical Embedded Systems: A Game-Theoretic Approach[C]// IEEE. 2021 IEEE 26th Pacific Rim International Symposium on Dependable Computing (PRDC). New York: IEEE, 2021: 27-36. |
| [14] | SINGLA R, REDDY N, BETTATI R, et al. Toward a Multidimensional Analysis of the National Vulnerability Database[J]. IEEE Access, 2023(11): 93354-93367. |
| [15] | COSTA J C, ROXO T, SEQUEIROS J B F, et al. Predicting CVSS Metric via Description Interpretation[J]. IEEE Access, 2022(10): 59125-59134. |
| [16] | LIN J, ADAMS B, HASSAN A E. On the Coordination of Vulnerability Fixes[J]. Empirical Software Engineering, 2023, 28(6): 151-162. |
| [17] | FIGUEROA-LORENZO S, AÑORGA J, ARRIZABALAGA S. A Survey of IIoT Protocols: A Measure of Vulnerability Risk Analysis Based on CVSS[J]. ACM Computing Surveys, 2021, 53(2): 1-53. |
| [18] | UR-REHMAN A, GONDAL I, KAMRUZZAMAN J, et al. Vulnerability Modelling for Hybrid Industrial Control System Networks[J]. Journal of Grid Computing, 2020, 18(4): 863-878. |
| [19] | ANAND P, SINGH Y, SELWAL A, et al. IVQFIoT: An Intelligent Vulnerability Quantification Framework for Scoring Internet of Things Vulnerabilities[EB/OL]. (2021-09-23)[2024-12-30]. https://doi.org/10.1111/exsy.12829. |
| [20] | LIU Xiaohu, ZHANG Hengwei, DONG Shuqin, et al. Network Defense Decision-Making Based on a Stochastic Game System and a Deep Recurrent Q-Network[EB/OL]. (2021-12-10)[2024-12-30]. https://doi.org/10.1016/j.cose.2021.102480. |
| [1] | 傅则凡, 潘高宁, 任一支, 胡铭德. 拟态函数:面向无服务器的拟态防御研究[J]. 信息网络安全, 2025, 25(6): 988-1002. |
| [2] | 郭钰铮, 郭春, 崔允贺, 李显超. 基于随机博弈网的窃密木马诱导式博弈模型[J]. 信息网络安全, 2024, 24(8): 1241-1251. |
| [3] | 周书丞, 李杨, 李传荣, 郭璐璐, 贾辛洪, 杨兴华. 基于上下文的异常根因算法[J]. 信息网络安全, 2024, 24(7): 1062-1075. |
| [4] | 胡瑞钦, 谭晶磊, 彭心荷, 张红旗. 面向SDN数据层的双虚假IP地址动态跳变技术[J]. 信息网络安全, 2022, 22(2): 76-85. |
| [5] | 李朝阳, 谭晶磊, 胡瑞钦, 张红旗. 基于双重地址跳变的移动目标防御方法[J]. 信息网络安全, 2021, 21(2): 24-33. |
| [6] | 朱帅, 罗森林, 柯懂湘. Windows Shellcode自动构建方法研究[J]. 信息网络安全, 2017, 17(4): 15-25. |
| [7] | 徐鑫, 张松年, 胡建伟. 基于任意函数地址的ASLR绕过技术研究[J]. 信息网络安全, 2016, 16(7): 47-52. |
| [8] | 毛焱颖, 罗森林. 融合多种技术的堆喷射方法研究[J]. 信息网络安全, 2016, 16(6): 48-55. |
| [9] | . 一种非堆喷射的IE浏览器漏洞利用技术研究[J]. , 2014, 14(6): 39-. |
| [10] | . 基于端口和编号的漏洞代码匹配方法研究[J]. , 2014, 14(4): 20-. |
| [11] | 关通, 任馥荔, 文伟平, 张浩. 基于Windows的软件安全典型漏洞利用策略探索与实践[J]. 信息网络安全, 2014, 14(11): 59-65. |
| [12] | 王宜阳;宋苑. 浅谈渗透测试在Web系统防护中的应用[J]. , 2010, (9): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||