信息网络安全 ›› 2025, Vol. 25 ›› Issue (2): 215-227.doi: 10.3969/j.issn.1671-1122.2025.02.003
基于ISRSAC-PSS算法的可证安全分组顺序聚合签名算法
- 北京电子科技学院密码科学与技术系,北京 100070
-
收稿日期:2024-07-07出版日期:2025-02-10发布日期:2025-03-07 -
通讯作者:袁煜淇 E-mail:1210346807@qq.com -
作者简介:张艳硕(1979—),男,陕西,副教授,博士,CCF高级会员,主要研究方向为密码理论及其应用|隋吉达(2003—),男,吉林,本科,主要研究方向为密码科学与技术|严梓洋(2001—),男,湖南,硕士研究生,主要研究方向为多变量公钥密码|袁煜淇(2000—),女,江西,硕士研究生,主要研究方向为数字签名 -
基金资助:中央高校基本科研业务费(3282024003);北京市自然科学基金(4232034)
A Provably Secure Block Sequential Aggregate Signature Algorithm Based on ISRSAC-PSS Algorithm
ZHANG Yanshuo, SUI Jida, YAN Ziyang, YUAN Yuqi( )
)
- Department of Cryptography Science and Technology, Beijing Electronic Science and Technology Institute, Beijing 100070, China
-
Received:2024-07-07Online:2025-02-10Published:2025-03-07
摘要:
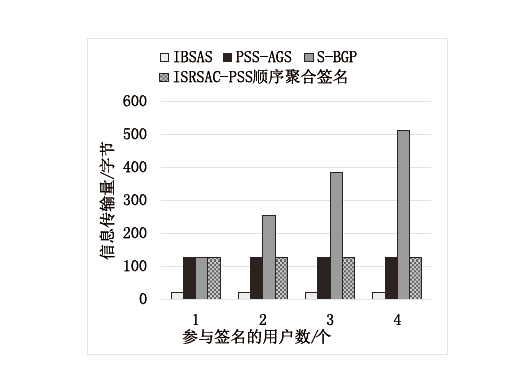
文章深入研究了可证明安全理论、顺序聚合签名算法及聚合签名技术,针对已有的基于ISRSAC-PSS算法的可证明安全顺序聚合签名算法进行改进,引入“分组型”理念,设计了基于ISRSAC-PSS的分组顺序聚合签名算法,经分析可知,该算法在基于大整数分解问题的困难性假设下,可以证明在随机预言模型下是安全的。计算分析得出,在分组合理的情况下,该算法不仅在效率上得到提高,还节省了算法的应用开销。
中图分类号:
引用本文
张艳硕, 隋吉达, 严梓洋, 袁煜淇. 基于ISRSAC-PSS算法的可证安全分组顺序聚合签名算法[J]. 信息网络安全, 2025, 25(2): 215-227.
ZHANG Yanshuo, SUI Jida, YAN Ziyang, YUAN Yuqi. A Provably Secure Block Sequential Aggregate Signature Algorithm Based on ISRSAC-PSS Algorithm[J]. Netinfo Security, 2025, 25(2): 215-227.
| [1] | BELLARE M, NEVEN G. Identity-Based Multi-Signatures from RSA[C]// IACR. Topics in Cryptology-CT-RSA 2007. Heidelberg: Springer, 2007: 145-162. |
| [2] | SUI Jida, ZHANG Yanshuo, YUAN Yuqi, et al. A Sequential Aggregate Signature Algorithm Based on ISRSAC-PSS Algorithm[J]. Journal of Beijing Electronic Science and Technology Institute, 2024, 32(4): 66-77. |
| 隋吉达, 张艳硕, 袁煜淇, 等. 一种基于ISRSAC-PSS的顺序聚合签名算法[J]. 北京电子科技学院学报, 2024, 32(4):66-77. | |
| [3] | CHEN Long, LI Jia, LIN Zhen, et al. Sequential Aggregate Signatures: A Novel Approach to Combine Privacy and Efficiency[J]. IEEE Transactions on Information Forensics and Security, 2020, 15(8): 2032-2047. |
| [4] | JIN Zhe, HE Dong, HUANG Yu, et al. Privacy-Preserving Sequential Aggregate Signature for Cloud-Assisted Internet of Things[J]. IEEE Transactions on Information Forensics and Security, 2019, 14(7): 1057-1070. |
| [5] | BONEH D, LYNN B, SHACHAM H. Short Signatures from the Weil Pairing[J]. Journal of Cryptology, 2004, 17(4): 297-319. |
| [6] | GARG S, GENTRY C, HALEVI S, et al. On the Impossibility of Structure-Preserving Deterministic Primitives[C]// IACR. Advances in Cryptology- ASIACRYPT 2012. Heidelberg: Springer, 2012: 409-436. |
| [7] | SCHNORR C P. Efficient Signature Generation by Smart Cards[J]. Journal of Cryptology, 1991, 4(3): 161-174. |
| [8] | TANENBAUM A S, VAN S M. Distributed Systems: Principles and Paradigms[M]. Boston: Pearson Education, 2016. |
| [9] | SCHNEIDER F B. Implementing Fault-Tolerant Services Using the State Machine Approach: A Tutorial[J]. ACM Computing Surveys, 1991, 22(4): 299-319. |
| [10] | BONEH D, GENTRY C, LYNN B, et al. Aggregate and Verifiably Encrypted Signatures from Bilinear Maps[C]// IACR. Advances in Cryptology- EUROCRYPT 2003. Heidelberg: Springer, 2003: 1-19. |
| [11] | BOLDYREVA A. Threshold Signatures, Multisignatures and Blind Signatures Based on the Gap-Diffie-Hellman-Group Signature Scheme[C]// IACR. Public Key Cryptography-PKC 2003. Heidelberg: Springer, 2003: 31-46. |
| [12] | MA Jun, LU Rong, XU Li. Sequential Aggregate Signatures: New Constructions and Applications[J]. IEEE Transactions on Information Forensics and Security, 2018, 13(9): 2204-2217. |
| [13] | BELLARE M, NEVEN G, NAMPREMPRE C. Security Proofs for Identity-Based Identification and Signature Schemes[C]// IACR. Advances in Cryptology- EUROCRYPT 2004. Heidelberg: Springer, 2004: 268-286. |
| [14] | THANGAVEL M, VARALAKSHMI P. Improved Secure RSA Cryptosystem for Data Confidentiality in Cloud[J]. International Journal of Information Systems and Change Management, 2017, 9(4): 261-277. |
| [15] | LIU Ning, YUAN Yuqi, ZHANG Yanshuo. A Summary of ISRSAC-Based Digital Signature[J]. Journal of Beijing Electronic Science and Technology Institute, 2023, 31(2): 125-142. |
| 刘宁, 袁煜淇, 张艳硕. 基于ISRSAC的数字签名研究综述[J]. 北京电子科技学院学报, 2023, 31(2):125-142. | |
| [16] | LIU Chen, HSU C. Comment on “Improved Secure RSA Cryptosystem (ISRSAC) for Data Confidentiality in Cloud”[J]. International Journal of Network Security, 2019, 21(4): 709-712. |
| [17] | YANG Tao, ZHANG Yu, XIAO Sheng, et al. Digital Signature Based on ISRSAC[J]. China Communications, 2021, 18(1): 161-168. |
| [18] | ZHANG Yanshuo, LIU Ning, LUO Leqi. Design and Analysis of Ring Signature Scheme Based on ISRSAC[J]. Journal of Beijing Electronic Science and Technology Institute, 2022, 30(2): 23-34. |
| 张艳硕, 刘宁, 罗乐琦. 基于ISRSAC的环签名方案设计与分析[J]. 北京电子科技学院学报, 2022, 30(2):23-34. | |
| [19] | LIU Tianning, ZHANG Yanshuo, LIU Ning. Two Proxy Multiple Digital Signature Schemes Based on ISRSAC[J]. Journal of Beijing Electronics Science and Technology Institute, 2022, 30(1): 94-103. |
| 刘天宁, 张艳硕, 刘宁. 基于ISRSAC的两类代理多重数字签名方案[J]. 北京电子科技学院学报, 2022, 30(1):94-103. | |
| [20] | YUAN Yuqi, SUI Jida, ZHANG Yanshuo, et al. Design and Analysis of Provably Secure ISRSAC Cryptosystem[J]. Journal of Beijing Electronics Science and Technology Institute, 2024, 32(2): 34-42. |
| 袁煜淇, 隋吉达, 张艳硕, 等. 可证安全的ISRSAC密码体制的设计与分析[J]. 北京电子科技学院学报, 2024, 32(2):34-42. | |
| [21] | LI Chunxiao, WANG Yaofei, XU Enliang, et al. Enabling Privacy-Preserving Range Queries in Blockchain-Based Collaborative Databases with Bilinear Pairings[J]. Netinfo Security, 2023, 23(3): 22-34. |
| 李春晓, 王耀飞, 徐恩亮, 等. 基于双线性映射的区块链安全范围搜索技术研究[J]. 信息网络安全, 2023, 23(3):22-34. | |
| [22] | BELLARE M, BOLDYREVA A, O'NEILL A. Deterministic and Efficiently Searchable Encryption[C]// IACR. Advances in Cryptology- EUROCRYPT 2007. Heidelberg: Springer, 2007: 535-552. |
| [23] | ZHANG Xuewang, ZHANG Hao, YAO Yaning, et al. Privacy Protection Scheme of Consortium Blockchain Based on Group Signature and Homomorphic Encryption[J]. Netinfo Security, 2023, 23(3): 56-61. |
| 张学旺, 张豪, 姚亚宁, 等. 基于群签名和同态加密的联盟链隐私保护方案[J]. 信息网络安全, 2023, 23(3):56-61. | |
| [24] | CRAMER R, DAMGARD I, SCHOENMAKERS B. Proofs of Partial Knowledge and Simplified Design of Witness Hiding Protocols[C]// IACR. Advances in Cryptology-CRYPTO 1994. Heidelberg:Springer, 1994: 174-187. |
| [25] | LYSYANSKAYA A, MICALI S. Sequential Aggregate Signatures from Trapdoor Permutations[C]// ACM. Proceedings of the 2006 ACM Symposium on Information, Computer and Communications Security. New York: ACM, 2006: 1-12. |
| [26] | DIFFIE W, HELLMAN M E. New Directions in Cryptography[J]. IEEE Transactions on Information Theory, 1976, 22(6): 644-654. |
| [27] | WANG Bin, GUO Yunfei, ZHANG Jianhui, et al. Provably Secure Sequential Aggregate Signatures Scheme Based on PSS[J]. Journal of Wuhan University, 2010, 56(4): 441-445. |
| 王滨, 郭云飞, 张建辉, 等. 基于PSS算法的可证明安全顺序聚合签名算法[J]. 武汉大学学报, 2010, 56(4):441-445. | |
| [28] | ZHAO Meiyuan, SMITH S W, NICOL D M. Aggregated Path Authentication for Efficient BGP Security[C] // ACM. Proceedings of the ACM Conference on Computer and Communications Security. New York: ACM, 2005: 128-138. |
| [29] | KENT S, LYNN C, SEO K. Secure Border Gateway Protocol (S-BGP)[J]. IEEE Journal on Selected Areas in Communications, 2000, 18(4): 582-592. |
| [30] | BONEH D, DRIJVERS M, NEVEN G. Compact Multi-Signatures for Smaller Block-Chains[C]// ACM. Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2018: 697-713. |
| [31] | LU Yun, OSTROVSKY R, SAHAI A, et al. Sequential Aggregate Signatures and Multisignatures Without Random Oracles[C]// IACR. Advances in Cryptology- EUROCRYPT 2006. Heidelberg: Springer, 2006: 465-485. |
| [32] | ZHANG Yanshuo, YUAN Yuqi, LI Liqiu, et al. Periodically Deniable Ring Signature Scheme Based on SM2 Digital Signature Algorithm[J]. Netinfo Security, 2024, 24(4): 564-573. |
| 张艳硕, 袁煜淇, 李丽秋, 等. 基于SM2的周期性可否认环签名方案[J]. 信息网络安全, 2024, 24(4):564-573. |
| [1] | 张艳硕, 袁煜淇, 李丽秋, 杨亚涛, 秦晓宏. 基于SM2的周期性可否认环签名方案[J]. 信息网络安全, 2024, 24(4): 564-573. |
| [2] | 刘芹, 张标, 涂航. 基于twisted Edwards曲线的无证书盲签名方案[J]. 信息网络安全, 2022, 22(8): 19-25. |
| [3] | 刘子昂, 黄缘缘, 马佳利, 周睿. 基于区块链的医疗数据滥用监控平台设计与实现[J]. 信息网络安全, 2021, 21(5): 58-66. |
| [4] | 刘峰, 杨杰, 齐佳音. 基于哈希证明系统的区块链两方椭圆曲线数字签名算法研究[J]. 信息网络安全, 2021, 21(1): 19-26. |
| [5] | 王生玉, 汪金苗, 董清风, 朱瑞瑾. 基于属性加密技术研究综述[J]. 信息网络安全, 2019, 19(9): 76-80. |
| [6] | 韩益亮, 王众. 基于多变量和LRPC码的抗量子密码方案研究[J]. 信息网络安全, 2019, 19(8): 36-43. |
| [7] | 胡荣磊, 李文敬, 蒋华, 张昕然. 基于离散对数的无证书聚合签密方案[J]. 信息网络安全, 2019, 19(7): 42-49. |
| [8] | 亢保元, 颉明明, 司林. 基于生物识别技术的多云服务器认证方案研究[J]. 信息网络安全, 2019, 19(6): 45-52. |
| [9] | 王耀杰, 钮可, 杨晓元. 基于生成对抗网络的图像隐藏方案[J]. 信息网络安全, 2019, 19(5): 54-60. |
| [10] | 左黎明, 胡凯雨, 张梦丽, 夏萍萍. 一种具有双向安全性的基于身份的短签名方案[J]. 信息网络安全, 2018, 18(7): 47-54. |
| [11] | 陈亚楠, 梅倩, 熊虎, 徐维祥. 适用于工业物联网的无证书并行密钥隔离签名[J]. 信息网络安全, 2018, 18(10): 1-9. |
| [12] | 张玉磊, 马彦丽, 刘文静, 王彩芬. 具有隐私保护特性的证书否认认证加密方案[J]. 信息网络安全, 2018, 18(10): 62-69. |
| [13] | 姜红, 亢保元, 李春青. 改进的保护身份的云共享数据完整性公开审计方案[J]. 信息网络安全, 2018, 18(10): 85-91. |
| [14] | 齐健, 陈小明, 游伟青. 基于fuzzing测试的网络协议安全评估方法研究[J]. 信息网络安全, 2017, 17(3): 59-65. |
| [15] | 黄鹏, 曾贵华. 连续变量量子密钥分发实际安全性研究进展[J]. 信息网络安全, 2017, 17(11): 7-12. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||