信息网络安全 ›› 2024, Vol. 24 ›› Issue (8): 1291-1305.doi: 10.3969/j.issn.1671-1122.2024.08.014
一种全生命周期可控的公共数据共享方案
吕秋云1,2, 周凌飞1, 任一支1, 周士飞3( ), 盛春杰3
), 盛春杰3
- 1.杭州电子科技大学网络空间安全学院,杭州 310018
2.杭州电子科技大学平湖数字技术创新研究院,平湖 314299
3.浙江省嘉兴市平湖市数据局,平湖 314200
-
收稿日期:2024-03-25出版日期:2024-08-10发布日期:2024-08-22 -
通讯作者:周士飞15968334933@139.com -
作者简介:吕秋云(1978—),女,浙江,副教授,博士,主要研究方向为数据延伸控制、隐私保护和监管并存的协议设计、基于区块链的数据安全应用|周凌飞(2000—),男,浙江,硕士研究生,主要研究方向为隐私保护、访问控制|任一支(1981—),男,安徽,教授,博士,CCF会员,主要研究方向为大数据安全、人工智能安全|周士飞(1984—),男,浙江,主要研究方向为数据安全治理、数据安全共享|盛春杰(1985—),男,浙江,主要研究方向为大数据应用与安全、数据安全共享 -
基金资助:浙江省自然科学基金(LY23F020017);浙金平湖实验室创新项目(JPH202301)
A Lifecycle-Manageable Public Data Sharing Scheme
LYU Qiuyun1,2, ZHOU Lingfei1, REN Yizhi1, ZHOU Shifei3( ), SHENG Chunjie3
), SHENG Chunjie3
- 1. School of Cyberspace, Hangzhou Dianzi University, Hangzhou 310018, China
2. Pinghu Digital Technology Innovation Institute Co. Ltd., Hangzhou Dianzi University, Pinghu 314299, China
3. Pinghu Municipal Data Bureau, Jiaxing City, Zhejiang Proince, Pinghu 314200, China
-
Received:2024-03-25Online:2024-08-10Published:2024-08-22
摘要:
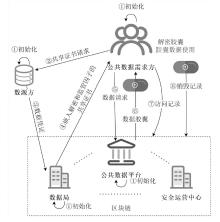
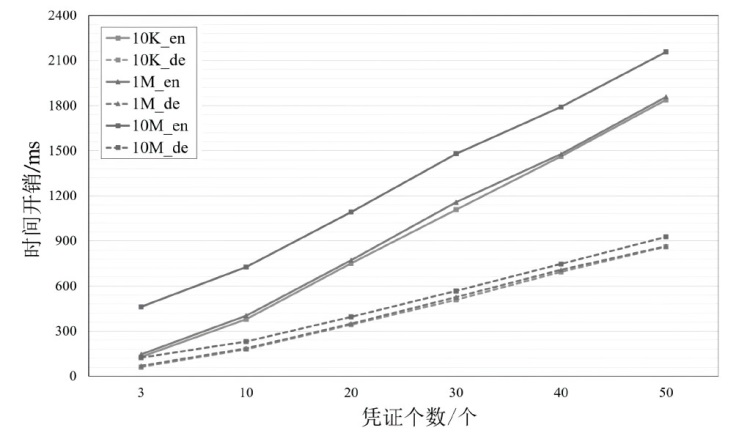
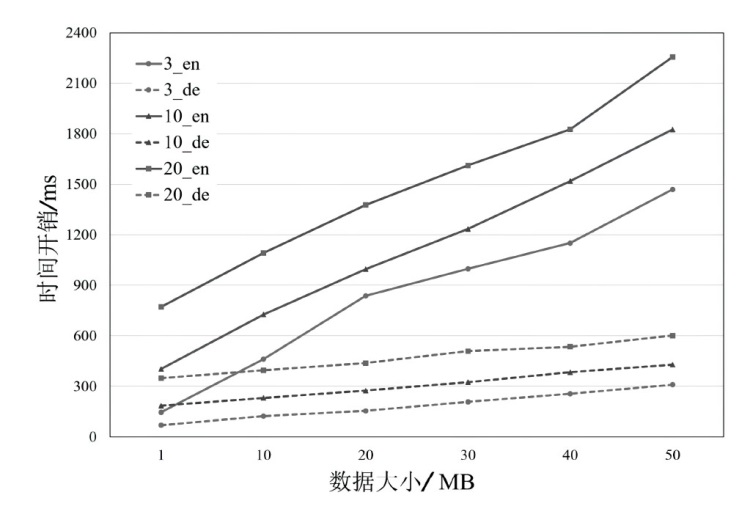
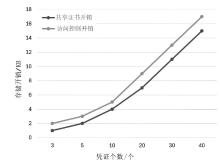
公共数据作为数据要素将极大赋能政府公共服务和社会治理,然而,频繁爆发的数据泄露事件严重阻碍了公共数据共享的进程。虽然现有的属性基加密方案能够实现公共数据的安全访问,但存在授权管理低效、共享后难以管控等问题,不适合现有的公共数据共享模式。为此,文章提出了一种全生命周期可控的公共数据共享方案。该方案设计了一种数据胶囊封装方法,将共享的公共数据与访问授权策略进行深度绑定,并构建了共享数据多方参与的分层授权、全生命周期感知的访问管控方式。安全性分析以及实验仿真表明,该方案实现了公共数据共享的全生命周期可控,开销较小,符合现实需求。
中图分类号:
引用本文
吕秋云, 周凌飞, 任一支, 周士飞, 盛春杰. 一种全生命周期可控的公共数据共享方案[J]. 信息网络安全, 2024, 24(8): 1291-1305.
LYU Qiuyun, ZHOU Lingfei, REN Yizhi, ZHOU Shifei, SHENG Chunjie. A Lifecycle-Manageable Public Data Sharing Scheme[J]. Netinfo Security, 2024, 24(8): 1291-1305.
表1
本文方案涉及的符号及其描述
| 符号 | 描述 |
|---|---|
| 系统公开和保密参数 | |
| 公共数据需求方U、公共数据平台P、 数据局DB和数源方S 的公私钥匙 | |
| 公共数据平台P、公共数据需求方U、公共数据需求方直属上级SU、数源方S的身份标识符 | |
| 共享证书请求 | |
| DV,OV, SOV | 数据凭证,组织机构凭证,直属上级组织机构凭证 |
| SC | 共享证书 |
| 访问策略树 | |
| 访问控制树 | |
| 访问控制规则 | |
| CT | 加密后的密文 |
| 访问控制树逻辑节点多项式 |
| [1] | State Council. Opinions of the CPC Central Committee and the State Council on Establishing a Data Base System to Maximize a Better Role of Data Elements[J]. Scientific Chinese, 2023(2): 60-64. |
| 中共中央国务院. 国务院关于构建数据基础制度更好发挥数据要素作用的意见[J]. 科学中国人, 2023(2): 60-64. | |
| [2] | ZHENG Xue. The “Data Elements ×” Three-Year Action Plan Will Be Implemented[N]. 21st CENTURY BUSINESS HERALD, 2023-12-19(2). |
| 郑雪. “数据要素×”三年行动计划将落地[N]. 21世纪经济报道,2023-12-19(2). | |
| [3] | FAN Wenyang. Over 30, 000 Pieces of Sensitive Information of Teachers and Students Leaked from a University in Nanchang, Resulting in an 800, 000 Yuan Fine! Three People Arrested[EB/OL]. (2023-08-16)[2024-03-17]. https://new.qq.com/rain/a/20230817A016UZ00. |
| 樊文扬. 南昌一高校3万余条师生敏感信息泄露,被罚80万!3人被抓[EB/OL]. (2023-08-16)[2024-03-17]. https://new.qq.com/rain/a/20230817A016UZ00. | |
| [4] | SECRSS. Overview of the Top 10 Global Data Security and Cyber Attack Incidents in 2023[EB/OL]. (2023-12-15)[2024-03-17]. https://www.secrss.com/articles/61797. |
| 安全内参. 2023年全球10大数据安全和网络攻击事件盘点[EB/OL]. (2023-12-15)[2024-03-17]. https://www.secrss.com/articles/61797. | |
| [5] | PENG Chun. The Promotion and Boundary of Data Sharing in the Public Sector[J]. SJTU Law Review, 2023(6): 63-77. |
| 彭錞. 论政务数据共享的推进与边界[J]. 交大法学, 2023(6): 63-77. | |
| [6] | FERNANDEZ M, JAIMUNK J, THURAISINGHAM B. A Privacy-Preserving Architecture and Data-Sharing Model for Cloud-IoT Applications[J]. IEEE Transactions on Dependable and Secure Computing, 2022, 20(4): 3495-3507. |
| [7] | DONG Xin, YU Jiadi, YUAN Luo, et al. Achieving an Effective, Scalable and Privacy-Preserving Data Sharing Service in Cloud Computing[J]. Computers & Security, 2014, 42: 151-164. |
| [8] | CHASE M. Multi-Authority Attribute Based Encryption[C]// Springer. 4th Theory of Cryptography Conference, TCC 2007. Heidelberg: Springer, 2007: 515-534. |
| [9] | SAHAI A, WATERS B. Fuzzy Identity-Based Encryption[C]// Springer. 24th Annual International Conference on the Theory and Applications of Cryptographic Techniques. Heidelberg: Springer, 2005: 457-473. |
| [10] | GOYAL V, PANDEY O, SAHAI A, et al. Attribute-Based Encryption for Fine-Grained Access Control of Encrypted Data[C]// ACM SIGSAC. 13th ACM Conference on Computer and Communications Security. New York: ACM, 2006: 89-98. |
| [11] | BETHENCOURT J, SAHAI A, WATERS B. Ciphertext-Policy Attribute-Based Encryption[C]// IEEE. 2007 IEEE Symposium on Security and Privacy (SP’07). New York: IEEE, 2007: 321-334. |
| [12] | ZUO Cong, SHAO Jun, LIU J K, et al. Fine-Grained Two-Factor Protection Mechanism for Data Sharing in Cloud Storage[J]. IEEE Transactions on Information Forensics and Security, 2018, 13(1): 186-196. |
| [13] | LI Chunhua, HE Jinbiao, LEI Cheng, et al. Achieving Privacy-Preserving CP-ABE Access Control with Multi-Cloud[C]// IEEE. 2018 IEEE International Conference on Parallel & Distributed Processing with Applications, Ubiquitous Computing & Communications, Big Data & Cloud Computing, Social Computing & Networking, Sustainable Computing & Communications (ISPA/IUCC/BDCloud/SocialCom/SustainCom). New York: IEEE, 2018: 801-808. |
| [14] | JI Honghan, ZHANG Hongjie, SHAO Lisong, et al. An Efficient Attribute-Based Encryption Scheme Based on SM9 Encryption Algorithm for Dispatching and Control Cloud[J]. Connection Science, 2021, 33(4): 1094-1115. |
| [15] | NING Jianting, HUANG Xinyi, SUSILO W, et al. Dual Access Control for Cloud-Based Data Storage and Sharing[J]. IEEE Transactions on Dependable and Secure Computing, 2022, 19(2): 1036-1048. |
| [16] | KARTHIKA A, MUTHUKUMARAN N. An ADS-PAYG Approach Using Trust Factor against Economic Denial of Sustainability Attacks in Cloud Storage[J]. Wireless Personal Communications, 2022, 122(1): 69-85. |
| [17] | YANG Kan, SHU Jiangang, XIE Ruitao, et al. Efficient and Provably Secure Data Selective Sharing and Acquisition in Cloud-Based Systems[J]. IEEE Transactions on Information Forensics and Security, 2023, 18: 71-84. |
| [18] | BELLARE M, BOLDYREVA A, O’NEILL A. Deterministic and Efficiently Searchable Encryption[C]// Springer. Advances in Cryptology-CRYPTO 2007: 27th Annual International Cryptology Conference. Heidelberg: Springer, 2007: 535-552. |
| [19] | LYU Qiuyun, QI Yizhen, ZHANG Xiaocheng, et al. SBAC: A Secure Blockchain-Based Access Control Framework for Information-Centric Networking[J]. Journal of Network and Computer Applications, 2020, 149: 1-17. |
| [20] | XUE Zhiyuan, WANG Miao, ZHANG Qiuyue, et al. A Regulatable Blockchain Transaction Model with Privacy Protection[J]. International Journal of Computational Intelligence Systems, 2021, 14(1): 1642-1652. |
| [21] | NIE Zixiang, LONG Yuanzhentai, ZHANG Senlin, et al. A Controllable Privacy Data Transmission Mechanism for Internet of Things System Based on Blockchain[J]. International Journal of Distributed Sensor Networks, 2022, 18(3): 303-315. |
| [22] | ZHOU Quan, CHEN Minhui, WEI Kaijun, et al. Blockchain Access Control Scheme with SM9-Based Attribute Encryption[J]. Netinfo Security, 2023, 23(9): 37-46. |
| 周权, 陈民辉, 卫凯俊, 等. 基于SM9的属性加密的区块链访问控制方案[J]. 信息网络安全, 2023, 23(9): 37-46. | |
| [23] | WANG Lun, NEAR J P, SOMANI N, et al. Data Capsule: A New Paradigm for Automatic Compliance with Data Privacy Regulations[C]//Springer. Heterogeneous Data Management, Polystores, and Analytics for Healthcare:VLDB 2019 Workshops, Poly and DMAH. Heidelberg: Springer, 2019: 3-23. |
| [24] | SOLTANI R, NGUYEN U T, AN Aijun. Data Capsule: A Self-Contained Data Model as an Access Policy Enforcement Strategy[C]// IEEE. 2021 3rd Conference on Blockchain Research & Applications for Innovative Networks and Services (BRAINS). New York: IEEE, 2021: 93-96. |
| [25] | MÜLLER S, KATZENBEISSER S, ECKERT C. On Multi-Authority Ciphertext-Policy Attribute-Based Encryption[J]. Bulletin of the Korean Mathematical Society, 2009, 46(4): 803-819. |
| [26] | OSTROVSKY R, SAHAI A, WATERS B. Attribute-Based Encryption with Non-Monotonic Access Structures[C]// ACM. 14th ACM Conference on Computer and Communications Security. New York: ACM, 2007: 195-203. |
| [27] | WANG Shulan, WANG Haiyan, LI Jianqiang, et al. A Fast CP-ABE System for Cyber-Physical Security and Privacy in Mobile Healthcare Network[J]. IEEE Transactions on Industry Applications, 2020, 56(4): 4467-4477. |
| [28] | NAKAMOTO S. Bitcoin Whitepaper[EB/OL]. (2008-10-31)[2024-03-17]. https://bitcoin.org/bitcoin.pdf. |
| [29] | LYU Qiuyun, LI Hao, DENG Zhining, et al. A2ua: An Auditable Anonymous User Authentication Protocol Based on Blockchain for Cloud Services[J]. IEEE Transactions on Cloud Computing, 2022(99): 1-16. |
| [1] | 张继威, 王文俊, 牛少彰, 郭向阔. 区块链扩展解决方案:ZK-Rollup综述[J]. 信息网络安全, 2024, 24(7): 1027-1037. |
| [2] | 郭瑞, 杨鑫, 王俊茗. 基于区块链的可验证可撤销属性加密方案[J]. 信息网络安全, 2024, 24(6): 863-878. |
| [3] | 凌治, 杨明, 余江银. 基于IPFS和区块链技术的电力安全交易平台研究[J]. 信息网络安全, 2024, 24(6): 968-976. |
| [4] | 田钊, 牛亚杰, 佘维, 刘炜. 面向车联网的车辆节点信誉评估方法[J]. 信息网络安全, 2024, 24(5): 719-731. |
| [5] | 王巍, 胡永涛, 刘清涛, 王凯崙. 铁路运行环境下ERT可信根实体的软件化技术研究[J]. 信息网络安全, 2024, 24(5): 794-801. |
| [6] | 石润华, 杨婧怡, 王鹏博, 刘华伟. V2G中基于区块链的在线/离线跨域身份认证方案[J]. 信息网络安全, 2024, 24(4): 587-601. |
| [7] | 胡海洋, 刘畅, 王栋, 魏旭. 基于区块链的清洁能源数据溯源机制[J]. 信息网络安全, 2024, 24(4): 626-639. |
| [8] | 薛茗竹, 胡亮, 王明, 王峰. 基于联邦学习和区块链技术的TAP规则处理系统[J]. 信息网络安全, 2024, 24(3): 473-485. |
| [9] | 翟鹏, 何泾沙, 张昱. 物联网环境下基于SM9算法和区块链技术的身份认证方法[J]. 信息网络安全, 2024, 24(2): 179-187. |
| [10] | 何业锋, 权家辉, 刘妍. 基于混合区块链的位置隐私保护方案[J]. 信息网络安全, 2024, 24(2): 229-238. |
| [11] | 吴昊天, 李一凡, 崔鸿雁, 董琳. 基于零知识证明和区块链的联邦学习激励方案[J]. 信息网络安全, 2024, 24(1): 1-13. |
| [12] | 朱郭诚, 何德彪, 安浩杨, 彭聪. 基于区块链和SM9数字签名的代理投票方案[J]. 信息网络安全, 2024, 24(1): 36-47. |
| [13] | 公鹏飞, 谢四江, 程安东. 基于HotStuff改进的多主节点共识算法[J]. 信息网络安全, 2023, 23(9): 108-117. |
| [14] | 周权, 陈民辉, 卫凯俊, 郑玉龙. 基于SM9的属性加密的区块链访问控制方案[J]. 信息网络安全, 2023, 23(9): 37-46. |
| [15] | 赵佳豪, 蒋佳佳, 张玉书. 基于动态默克尔哈希树的跨链数据一致性验证模型[J]. 信息网络安全, 2023, 23(9): 95-107. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||