信息网络安全 ›› 2024, Vol. 24 ›› Issue (7): 993-1005.doi: 10.3969/j.issn.1671-1122.2024.07.002
面向V2I通信的异构跨域条件隐私保护环签密方案
- 1.南昌大学软件学院,南昌 330047
2.共青科技职业学院,九江 332020
-
收稿日期:2024-03-26出版日期:2024-07-10发布日期:2024-08-02 -
通讯作者:罗铭lmhappy21@163.com -
作者简介:罗铭(1983—),男,江西,教授,博士,主要研究方向为物联网、网络空间安全和密码学|詹骐榜(1998—),男,江西,硕士研究生,主要研究方向为公钥密码学、信息安全和物联网隐私保护|邱敏蓉(1983—),女,江西,副教授,博士,主要研究方向为物联网、网络安全和信息系统管理。 -
基金资助:国家自然科学基金(62262041);江西省研究生创新专项基金(YC2023-S013);江西省高校人文社会科学研究项目(JC22217)
A Heterogeneous Cross-Domain Conditional Privacy Protection Ring Signcryption Scheme for V2I Communication
LUO Ming1( ), ZHAN Qibang1, QIU Minrong2
), ZHAN Qibang1, QIU Minrong2
- 1. School of Software, Nanchang University, Nanchang 330047, China
2. GongQing Institute of Science and Technology, Jiujiang 332020, China
-
Received:2024-03-26Online:2024-07-10Published:2024-08-02
摘要:
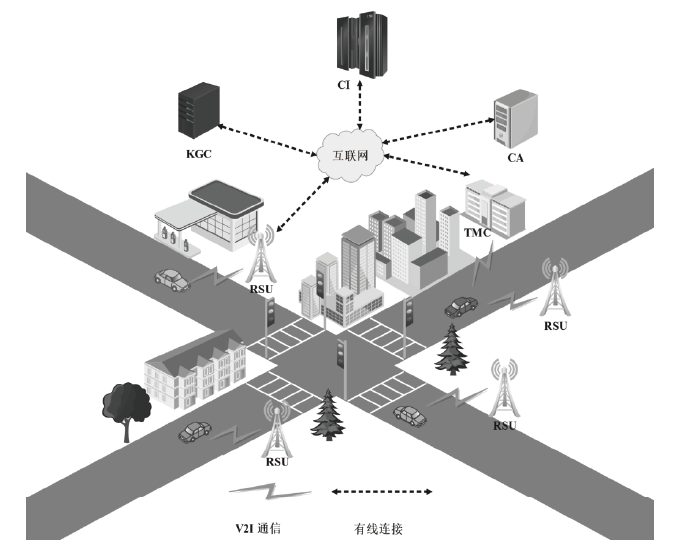
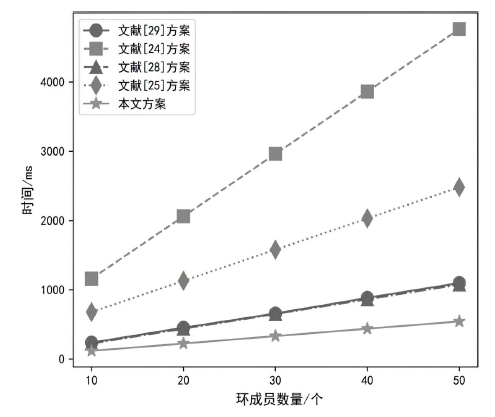
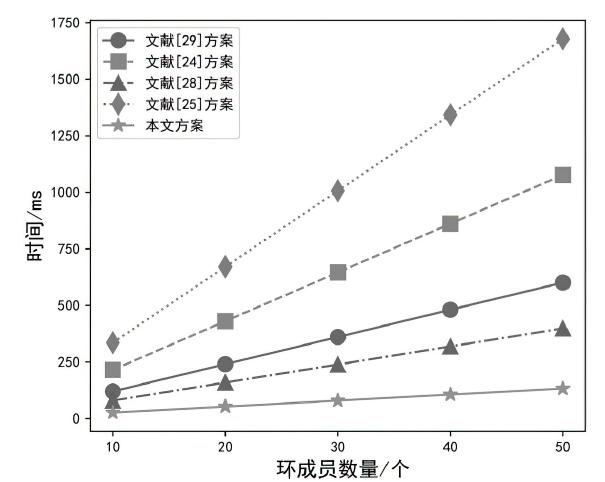
V2I通信是车载自组织网络的重要组成部分。确保在V2I中消息的安全传输一直是近年来研究人员研究的热点,提出了各种适用于V2I通信的条件隐私保护方案。然而,现有大多数基于环签密的方案中,普遍的假设是发送者和接收者都必须处于相同的密码体制和使用相同系统参数的同一域中。随着通信场景的复杂化,这种假设存在局限性,并且大多数基于环签密的方案未能满足已知临时会话密钥安全。为了解决这些问题,文章提出了一种面向V2I通信的异构跨域条件隐私保护环签密方案。该方案实现了无证书密码体制中的车辆到公钥基础设施密码体制中的基础设施的跨域通信。在随机预言机模型中进行了严格安全性证明,结果显示文章方案满足机密性和不可伪造性。与4种提供类似功能的方案进行比较分析,文章方案具有最低的计算成本和跟踪成本。
中图分类号:
引用本文
罗铭, 詹骐榜, 邱敏蓉. 面向V2I通信的异构跨域条件隐私保护环签密方案[J]. 信息网络安全, 2024, 24(7): 993-1005.
LUO Ming, ZHAN Qibang, QIU Minrong. A Heterogeneous Cross-Domain Conditional Privacy Protection Ring Signcryption Scheme for V2I Communication[J]. Netinfo Security, 2024, 24(7): 993-1005.
| [1] | YUAN Xueliang, LIU Xin, ZUO Jian. The Development of New Energy Vehicles for a Sustainable Future: A Review[J]. Renewable and Sustainable Energy Reviews, 2015, 42: 298-305. |
| [2] | KENNEY J B. Dedicated Short-Range Communications (DSRC) Standards in the United States[J]. Proceedings of the IEEE, 2011, 99(7): 1162-1182. |
| [3] | JIN Chunhua. An Efficient Heterogeneous Signcryption for Smart Grid[EB/OL]. (2018-12-18)[2024-03-20]. https://doi.org/10.1371/journal.pone.0208311. |
| [4] | PAN Xiangyu, JIN Yuqiao, WANG Ziqing, et al. A Pairing-Free Heterogeneous Signcryption Scheme for Unmanned Aerial Vehicles[J]. IEEE Internet of Things Journal, 2022, 9(19): 19426-19437. |
| [5] | NIU Shufen, SHAO Honglin, HU Ying, et al. Privacy-Preserving Mutual Heterogeneous Signcryption Schemes Based on 5G Network Slicing[J]. IEEE Internet of Things Journal, 2022, 9(19): 19086-19100. |
| [6] | KANG Jiawen, YU Rong, HUANG Xumin, et al. Privacy-Preserved Pseudonym Scheme for Fog Computing Supported Internet of Vehicles[J]. IEEE Transactions on Intelligent Transportation Systems, 2017, 19(8): 2627-2637. |
| [7] | QI Jiayu. A Pseudonym-Based Certificateless Privacy-Preserving Authentication Scheme for VANETs[EB/OL]. (2022-10-12)[2024-03-20]. https://doi.org/10.1016/j.vehcom.2022.100535. |
| [8] | GENC Y. ELCPAS: A New Efficient Lightweight Certificateless Conditional Privacy Preserving Authentication Scheme for IoV[EB/OL]. (2022-11-17)[2024-03-20]. https://doi.org/10.1016/j.vehcom.2022.100549. |
| [9] | GORDON S D, KATZ J, VAIKUNTANATHAN V. A Group Signature Scheme from Lattice Assumptions[C]// Springer. Advances in Cryptology-ASIACRYPT 2010: 16th International Conference on the Theory and Application of Cryptology and Information Security. Heidelberg: Springer, 2010: 395-412. |
| [10] | EZERMAN M F, LEE H T, LING San, et al. Provably Secure Group Signature Schemes from Code-Based Assumptions[J]. IEEE Transactions on Information Theory, 2020, 66(9): 5754-5773. |
| [11] | DEVIDAS S, RAO Y S, REKHA N R. A Decentralized Group Signature Scheme for Privacy Protection in a Blockchain[J]. International Journal of Applied Mathematics and Computer Science, 2021, 31(2): 353-364. |
| [12] | LIU J K, AU M H, SUSILO W, et al. Linkable Ring Signature with Unconditional Anonymity[J]. IEEE Transactions on Knowledge and Data Engineering, 2013, 26(1): 157-165. |
| [13] | ALBERTO T W A, STENINFELD R, SAKZAD A, et al. Post-Quantum One-Time Linkable Ring Signature and Application to Ring Confidential Transactions in Blockchain (Lattice RingCT v1. 0)[C]// Springer. Information Security and Privacy:23rd Australasian Conference, ACISP 2018. Heidelberg: Springer, 2018: 558-576. |
| [14] | YU Huifang. Certificateless Multi-Source Elliptic Curve Ring Signcryption for Cloud Computing[EB/OL]. (2023-03-07)[2024-03-20]. https://doi.org/10.1016/j.jisa.2023.103449. |
| [15] | YUAN Chao, ZHANG Wenfang, WANG Xiaomin. EIMAKP: Heterogeneous Cross-Domain Authenticated Key Agreement Protocols in the EIM System[J]. Arabian Journal for Science and Engineering, 2017, 42: 3275-3287. |
| [16] | JIANG Xin, LIU Mingzhe, YANG Chen, et al. A Blockchain-Based Authentication Protocol for WLAN Mesh Security Access[J]. Computers, Materials & Continua, 2019, 58(1): 45-59. |
| [17] | GONG Bei, ZHENG Guiping, WAQAS M, et al. LCDMA: Lightweight Cross-Domain Mutual Identity Authentication Scheme for Internet of Things[J]. IEEE Internet of Things Journal, 2023, 10(14): 12590-12602. |
| [18] | RIVEST R L, SHAMIR A, TAUMAN Y. How to Leak a Secret[C]// Springer. Advances in Cryptology—ASIACRYPT 2001: 7th International Conference on the Theory and Application of Cryptology and Information Security Gold Coast. Heidelberg: Springer, 2001: 552-565. |
| [19] | LIU D Y W, LIU J K, MU Yi, et al. Revocable Ring Signature[J]. Journal of Computer Science and Technology, 2007, 22: 785-794. |
| [20] | FUJISAKI E, SUZUKI K. Traceable Ring Signature[C]// Springer. International Workshop on Public Key Cryptography. Heidelberg: Springer, 2007: 181-200. |
| [21] | LIANG Weibiao. LRS_PKI: A Novel Blockchain-Based PKI Framework Using Linkable Ring Signatures[EB/OL]. (2023-09-25)[2024-03-20]. https://doi.org/10.1016/j.comnet.2023.110043. |
| [22] | HUANG Xinyi, SUSILO W, MU Yi, et al. Identity-Based Ring Signcryption Schemes: Cryptographic Primitives for Preserving Privacy and Authenticity in the Ubiquitous World[C]// IEEE. 19th International Conference on Advanced Information Networking and Applications (AINA'05) Volume 1 (AINA papers). New York: IEEE, 2005: 649-654. |
| [23] | LIU Feng, WANG Qi. IBRS: An Efficient Identity-Based Batch Verification Scheme for VANETs Based on Ring Signature[C]// IEEE. 2019 IEEE Vehicular Networking Conference (VNC). New York: IEEE, 2019: 1-8. |
| [24] | CAI Ying, ZHANG Hao, FANG Yuguang. A Conditional Privacy Protection Scheme Based on Ring Signcryption for Vehicular Ad Hoc Networks[J]. IEEE Internet of Things Journal, 2020, 8(1): 647-656. |
| [25] | DU Hongzhen, WEN Qiaoyan, ZHANG Shanshan, et al. An Improved Conditional Privacy Protection Scheme Based on Ring Signcryption for VANETs[J]. IEEE Internet of Things Journal, 2023, 10(20): 17881-17892. |
| [26] | LUO Ming, ZHOU Yanzibo. An Efficient Conditional Privacy-Preserving Authentication Protocol Based on Generalized Ring Signcryption for VANETs[J]. IEEE Transactions on Vehicular Technology, 2022, 71(9): 10001-10015. |
| [27] | BOUAKKAZ S. A Certificateless Ring Signature Scheme with Batch Verification for Applications in VANET[EB/OL]. (2020-10-26)[2024-03-20]. https://doi.org/10.1016/j.jisa.2020.102669. |
| [28] | GUO Rui. An Efficient Certificateless Ring Signcryption Scheme with Conditional Privacy-Preserving in VANETs[EB/OL]. (2022-06-26)[2024-03-20]. https://doi.org/10.1016/j.sysarc.2020.102633. |
| [29] | LIU Shuanggen, LIU Zhentao, LIANG Jueqin, et al. Certificateless Ring Signcryption Scheme with Conditional Privacy Protection in Smart Grid[C]// Springer. International Conference on Frontiers in Cyber Security. Heidelberg: Springer, 2023: 189-204. |
| [30] | POINTCHEVAL D, STERN J. Security Arguments for Digital Signatures and Blind Signatures[J]. Journal of cryptology, 2000, 13: 361-396. |
| [31] | DE C A, IOVINO V. JPBC: Java Pairing Based Cryptography[C]// IEEE. 2011 IEEE Symposium on Computers and Communications (ISCC). New York: IEEE, 2011: 850-855. |
| [1] | 石润华, 杨婧怡, 王鹏博, 刘华伟. V2G中基于区块链的在线/离线跨域身份认证方案[J]. 信息网络安全, 2024, 24(4): 587-601. |
| [2] | 俞惠芳, 乔一凡, 孟茹. 面向区块链金融的抗量子属性基门限环签密方案[J]. 信息网络安全, 2023, 23(7): 44-52. |
| [3] | 王瑞民, 省永续, 宋伟, 张建辉. 面向拟态云的异构执行体安全调度算法[J]. 信息网络安全, 2023, 23(3): 45-55. |
| [4] | 刘龙庚. 基于异构网络空管安全监控关联算法研究[J]. 信息网络安全, 2022, 22(4): 58-66. |
| [5] | 石润华, 王树豪, 李坤昌. V2G中一种轻量级的跨域双向认证方案[J]. 信息网络安全, 2022, 22(3): 20-28. |
| [6] | 王思蝶, 马兆丰, 罗守山, 徐单恒. 面向异构多链的区块链链上数据隐私保护方案[J]. 信息网络安全, 2022, 22(12): 67-75. |
| [7] | 余先荣, 樊捷杰. 基于Hadoop的异构网络协同过滤推荐算法设计[J]. 信息网络安全, 2022, 22(10): 91-97. |
| [8] | 王健, 赵曼莉, 陈志浩, 石波. 基于假名的智能交通条件隐私保护认证协议[J]. 信息网络安全, 2021, 21(4): 49-61. |
| [9] | 张玉磊, 骆广萍, 王欢, 刘祥震. 5G网络下可证安全的TPKC-CLPKC异构混合签密方案[J]. 信息网络安全, 2019, 19(5): 30-37. |
| [10] | 曹素珍, 郎晓丽, 刘祥震, 王斐. 5G网络下新的异构签密方案[J]. 信息网络安全, 2018, 18(11): 33-39. |
| [11] | 王柳, 曹珍富, 董晓蕾. 基于身份的指定验证者签名在跨域认证中的应用[J]. 信息网络安全, 2017, 17(10): 63-68. |
| [12] | 叶伟伟, 欧庆于, 柏小武. 基于服务架构的密码服务系统认证方案研究[J]. 信息网络安全, 2016, 16(5): 37-43. |
| [13] | 尹心明, 蒋海平, 黄海晔. 基于WSDL的跨域安全数据共享的柔性化配置技术分析[J]. 信息网络安全, 2016, 16(11): 52-56. |
| [14] | 黄海, 谢冬青, 宋一赞. WiFi-WiMAX异构无线网络认证机制研究[J]. 信息网络安全, 2015, 15(6): 19-25. |
| [15] | . 基于混沌和比特级置乱的并行图像加密算法[J]. , 2014, 14(4): 40-. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||