信息网络安全 ›› 2023, Vol. 23 ›› Issue (3): 45-55.doi: 10.3969/j.issn.1671-1122.2023.03.005
面向拟态云的异构执行体安全调度算法
- 1.郑州大学计算机与人工智能学院,郑州 450001
2.郑州大学河南省大数据研究院,郑州 450052
3.郑州大学网络空间安全学院,郑州 450002
4.嵩山实验室,郑州 450001
-
收稿日期:2022-11-27出版日期:2023-03-10发布日期:2023-03-14 -
通讯作者:张建辉 E-mail:ndsczjh@163.com -
作者简介:王瑞民(1974—),男,河南,副教授,博士,主要研究方向为密码学、信息安全和物联网安全|省永续(1999—),男,河南,硕士研究生,主要研究方向为拟态安全|宋伟(1972—),男,河南,副教授,博士,主要研究方向为数据挖掘与机器学习、智能系统、大数据安全|张建辉(1977—),男,河南,副研究员,博士,主要研究方向为网络与信息安全、网络体系架构和人工智能 -
基金资助:国家自然科学基金(61872382);国家电网有限公司总部科技项目(5700-202024176A-0-0-00)
Secure Scheduling Algorithm for Heterogeneous Executors for Mimic Clouds
WANG Ruimin1, XING Yongxu1, SONG Wei2, ZHANG Jianhui3,4( )
)
- 1. School of Computer and Artificial Intelligence, Zhengzhou University, Zhengzhou 450001, China
2. Henan Academy of Big Data of Zhengzhou University, Zhengzhou 450052, China
3. School of Cyber Science and Engineering, Zhengzhou University, Zhengzhou 450002, China
4. Songshan Laboratory, Zhengzhou 450001, China
-
Received:2022-11-27Online:2023-03-10Published:2023-03-14 -
Contact:ZHANG Jianhui E-mail:ndsczjh@163.com
摘要:
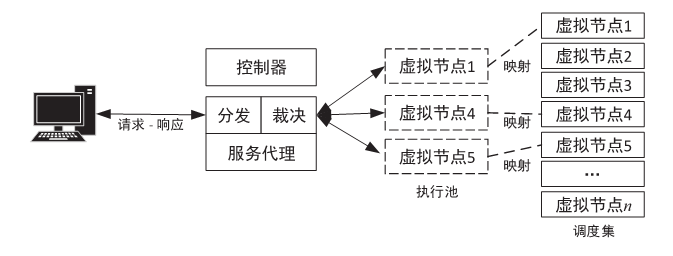
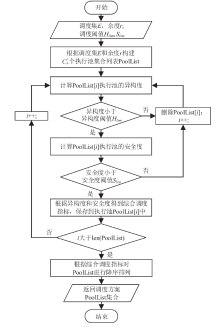
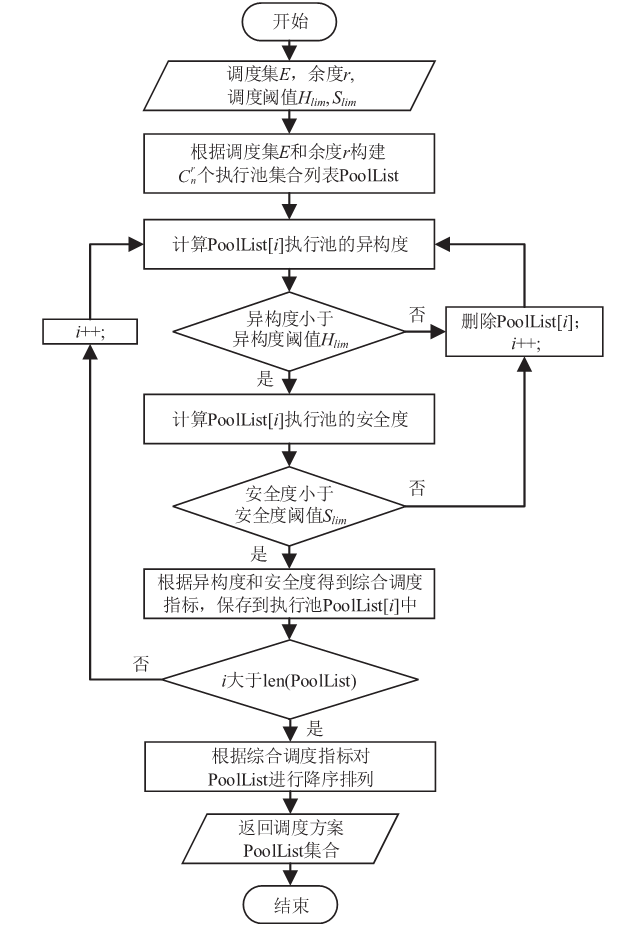
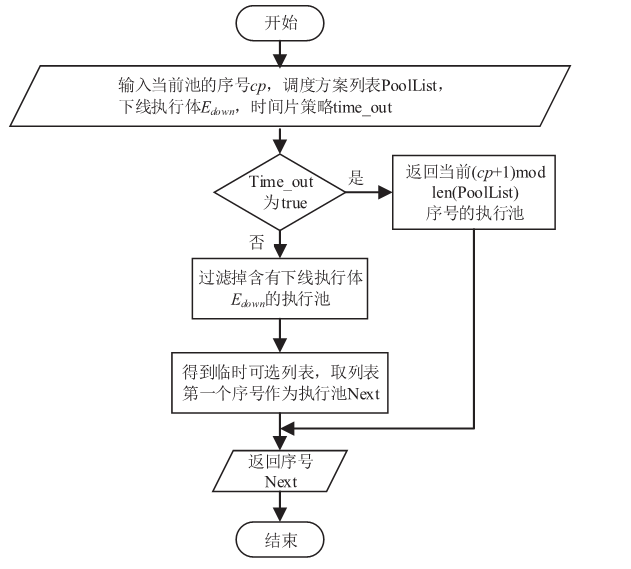
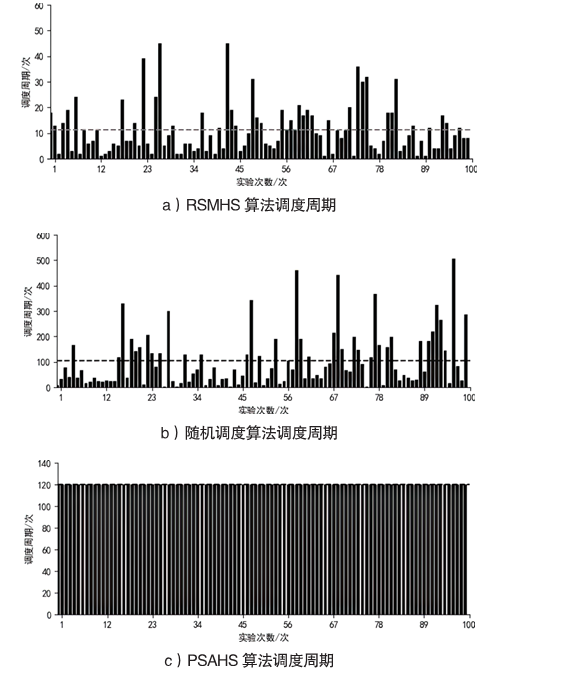
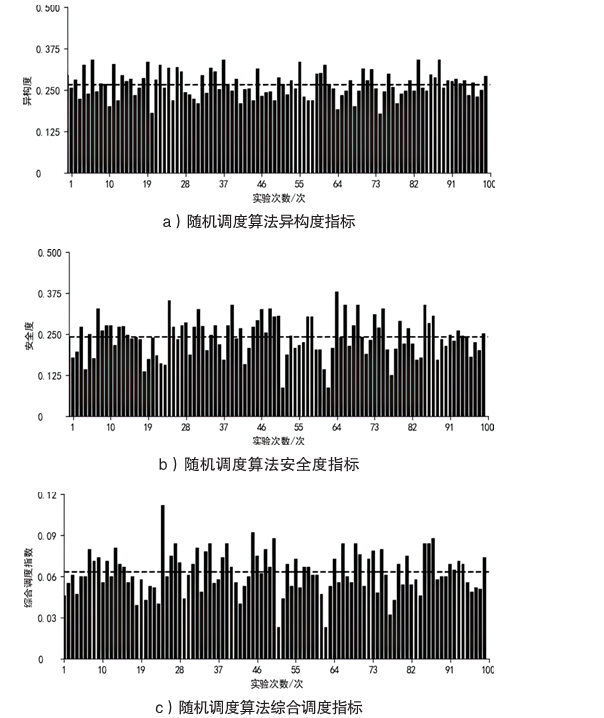
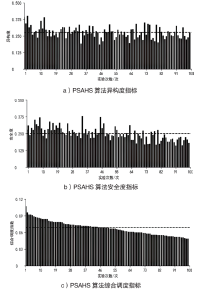
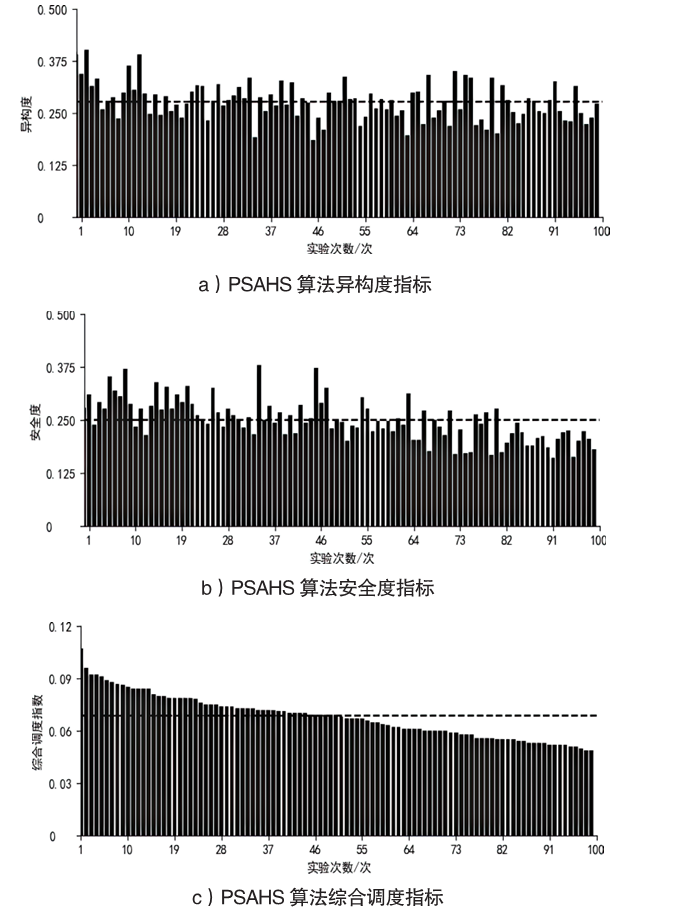
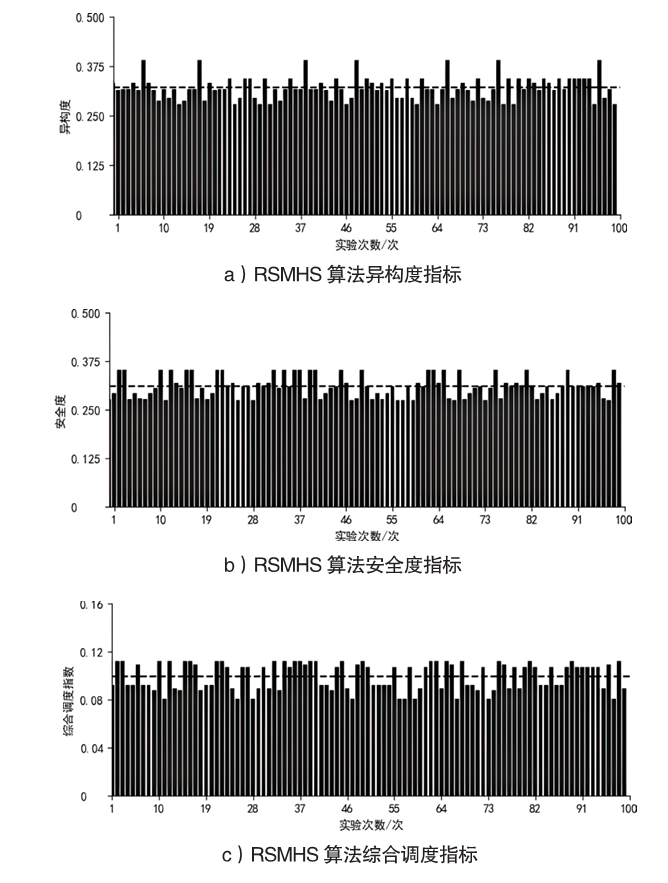
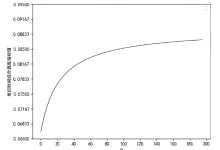
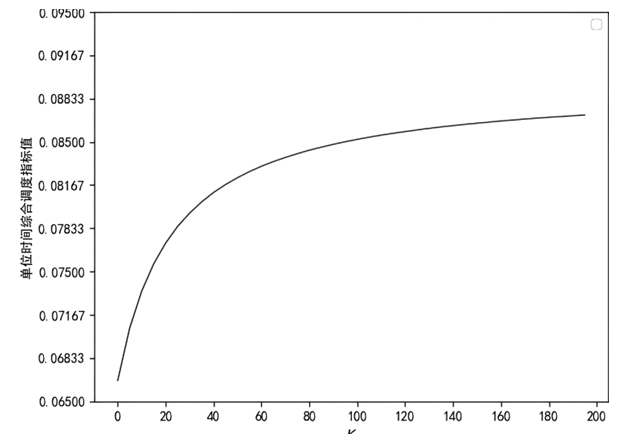
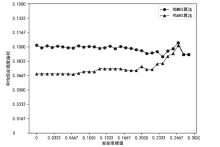
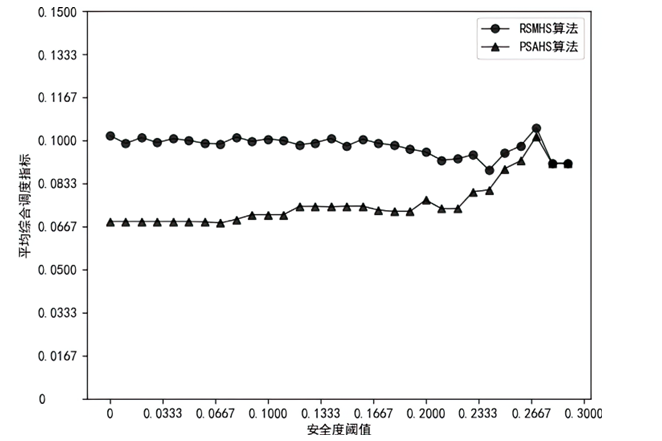
随着云服务的应用范围越来越广,基于未知漏洞或后门的攻击成为制约云技术发展的主要安全威胁之一。基于拟态防御建立的拟态云服务通过降低漏洞的持续性暴露概率来保障安全性,当前已有研究提出的拟态调度算法缺乏对执行体自身安全性的考虑,并且无法兼顾动态性和异构性。针对此问题文章通过引入执行池的异构度和安全度定义,提出一种基于异构度和安全度的优先级调度算法,并引入结合时间片的动态调度策略。实验结果表明,文章所提算法具有较好的动态性,能够获得较优的调度效果,实现了动态性、异构性和安全性之间的平衡,并且时间复杂度较低。
中图分类号:
引用本文
王瑞民, 省永续, 宋伟, 张建辉. 面向拟态云的异构执行体安全调度算法[J]. 信息网络安全, 2023, 23(3): 45-55.
WANG Ruimin, XING Yongxu, SONG Wei, ZHANG Jianhui. Secure Scheduling Algorithm for Heterogeneous Executors for Mimic Clouds[J]. Netinfo Security, 2023, 23(3): 45-55.
| [1] | ZHANG Yuqing, WANG Xiaofei, LIU Xuefeng, et al. Survey on Cloud Computing Security[J]. Journal of Software, 2016, 27(6): 1328-1348. |
| 张玉清, 王晓菲, 刘雪峰, 等. 云计算环境安全综述[J]. 软件学报, 2016, 27(6): 1328-1348. | |
| [2] | PU Liming, WEI Hongquan, LI Xing, et al. Mimic Cloud Service Architecture for Cloud Applications[J]. Chinese Journal of Network and Information Security, 2021, 7(1): 101-112. |
| [3] | CHEN Fucai, ZHOU Mengli, LIU Wenyan, et al. Feedback Control Method for Mimic Defense in Cloud Environment[J]. Netinfo Security, 2021, 21(1): 49-56. |
| [4] | WU Jiangxing. Research on Cyber Mimic Defense[J]. Journal of Cyber Security, 2016, 1(4): 1-10. |
| [5] | WU Jiangxing. Cyberspace Mimic Defense[M]. Beijing: Science Press, 2018. |
| 邬江兴. 网络空间拟态防御原理[M]. 北京: 科学出版社, 2018. | |
| [6] | PU Liming. Research on the Key Technologies of Mimic Cloud Service Architecture[D]. Zhengzhou: Information Engineering University, 2021. |
| 普黎明. 拟态云服务架构及关键技术研究[D]. 郑州: 战略支援部队信息工程大学, 2021. | |
| [7] |
SONG Ke, LIU Qinrang, WEI Shuai, et al. Endogenous Security Architecture of Ethernet Switch Based on Mimic Defense[J]. Journal on Communications, 2020, 41(5): 18-26.
doi: 10.11959/j.issn.1000-436x.2020098 |
|
宋克, 刘勤让, 魏帅, 等. 基于拟态防御的以太网交换机内生安全体系结构[J]. 通信学报, 2020, 41(5): 18-26.
doi: 10.11959/j.issn.1000-436x.2020098 |
|
| [8] | ZHENG Jiesheng, WU Guangcai, WEN Bojian, et al. Research on SDN-Based Mimic Server Defense Technology[C]// ACM. Proceedings of the 2019 International Conference on Artificial Intelligence and Computer Science. New York: ACM, 2019: 163-169. |
| [9] | LI Chuanhuang, REN Yunfang, TANG Zhongyun, et al. Mimic Defense Method for Service Deployment in SDN[J]. Journal on Communications, 2018, 39(S2): 121-130. |
| 李传煌, 任云方, 汤中运, 等. SDN中服务部署的拟态防御方法[J]. 通信学报, 2018, 39(S2): 121-130. | |
| [10] |
HU Hongchao, WANG Zhenpeng, CHENG Guozhen, et al. MNOS: A Mimic Network Operating System for Software Defined Networks[J]. IET Information Security, 2017, 11(6): 345-355.
doi: 10.1049/ise2.v11.6 URL |
| [11] | TONG Qing, ZHANG Zheng, ZHANG Weihua, et al. Design and Implementation of Mimicry Defense Web Server[J]. Journal of Software, 2017, 28(4): 883-897. |
| 仝青, 张铮, 张为华, 等. 拟态防御Web服务器设计与实现[J]. 软件学报, 2017, 28(4): 883-897. | |
| [12] |
GUO Wei, WU Zhaoqi, ZHANG Fan, et al. Scheduling Sequence Control Method Based on Sliding Window in Cyberspace Mimic Defense[J]. IEEE Access, 2019, 8: 1517-1533.
doi: 10.1109/Access.6287639 URL |
| [13] | WU Zhaoqi, WEI Jin. Heterogeneous Executors Scheduling Algorithm for Mimic Defense Systems[C]// IEEE. 2019 IEEE 2nd International Conference on Computer and Communication Engineering. New York: IEEE, 2019: 279-284. |
| [14] | YAO Dong, ZHANG Zheng, ZHANG Gaofei, et al. A Survey on Multi-Variant Execution Security Defense Technology[J]. Journal of Cyber Security, 2020, 5(5): 77-94. |
| [15] |
ZHU Zhengbin, LIU Qinrang, LIU Dongpei, et al. Research Progress of Mimic Multi-Execution Scheduling Algorithm[J]. Journal on Communications, 2021, 42(5): 179-190.
doi: 10.11959/j.issn.1000-436x.2021072 |
|
朱正彬, 刘勤让, 刘冬培, 等. 拟态多执行体调度算法研究进展[J]. 通信学报, 2021, 42(5): 179-190.
doi: 10.11959/j.issn.1000-436x.2021072 |
|
| [16] |
LIU Qinrang, LIN Senjie, GU Zeyu. Heterogeneous Redundancies Scheduling Algorithm for Mimic Security Defense[J]. Journal on Communications, 2018, 39(7): 188-198.
doi: 10.11959/j.issn.1000-436x.2018124 |
|
刘勤让, 林森杰, 顾泽宇. 面向拟态安全防御的异构功能等价体调度算法[J]. 通信学报, 2018, 39(7): 188-198.
doi: 10.11959/j.issn.1000-436x.2018124 |
|
| [17] |
PU Liming, LIU Shuxin, DING Ruihao, et al. Heterogeneous Executor Scheduling Algorithm for Mimic Cloud Service[J]. Journal on Communications, 2020, 41(3): 17-24.
doi: 10.11959/j.issn.1000-436x.2020052 |
|
普黎明, 刘树新, 丁瑞浩, 等. 面向拟态云服务的异构执行体调度算法[J]. 通信学报, 2020, 41(3): 17-24.
doi: 10.11959/j.issn.1000-436x.2020052 |
|
| [18] | GAO Yan, ZI Chenchen, FENG Sifeng, et al. Security Scheduling Algorithm for Web Gateways Based on Mimicry Defense Theory[J]. Journal of Chinese Computer Systems, 2021, 42(9): 1913-1919. |
| 高岩, 资郴琛, 冯四风, 等. 面向拟态防御理论构造Web网关的安全调度算法[J]. 小型微型计算机系统, 2021, 42(9): 1913-1919. | |
| [19] |
GARCIA M, BESSANI A, GASHI I, et al. Analysis of Operating System Diversity for Intrusion Tolerance[J]. Software: Practice and Experience, 2014, 44(6): 735-770.
doi: 10.1002/spe.v44.6 URL |
| [20] | ZHANG Jiexin, PANG Jianmin, ZHANG Zheng, et al. Executors Scheduling Algorithm for Web Server with Mimic Structure[J]. Computer Engineering, 2019, 45(8): 14-21. |
| 张杰鑫, 庞建民, 张铮, 等. 面向拟态构造Web服务器的执行体调度算法[J]. 计算机工程, 2019, 45(8): 14-21. |
| [1] | 陈福才, 周梦丽, 刘文彦, 梁浩. 云环境下面向拟态防御的反馈控制方法[J]. 信息网络安全, 2021, 21(1): 49-56. |
| [2] | 朱维军, 樊永文, 班绍桓. 动态虚拟MSISDN的拟态自动机模型与安全性验证方法[J]. 信息网络安全, 2018, 18(4): 15-22. |
| [3] | 翟胜军. 安全态势感知的关键是对安全的有效度量[J]. , 2011, 11(9): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||