信息网络安全 ›› 2024, Vol. 24 ›› Issue (2): 229-238.doi: 10.3969/j.issn.1671-1122.2024.02.006
基于混合区块链的位置隐私保护方案
- 西安邮电大学网络空间安全学院,西安 710121
-
收稿日期:2023-06-12出版日期:2024-02-10发布日期:2024-03-06 -
通讯作者:权家辉 E-mail:yubeilengzhi@163.com -
作者简介:何业锋(1978—),女,陕西,教授,博士,主要研究方向为车联网安全和量子密码协议|权家辉(1999—),男,陕西,硕士研究生,主要研究方向为车联网位置隐私|刘妍(1998—),女,陕西,硕士研究生,主要研究方向为车联网位置隐私 -
基金资助:国家自然科学基金(61802302);陕西省自然科学基础研究计划(2021JM-462)
A Location Privacy Protection Scheme Based on Hybrid Blockchain
HE Yefeng, QUAN Jiahui( ), LIU Yan
), LIU Yan
- School of Cyberspace Security, Xi’an University of Posts and Telecommunications, Xi’an 710121, China
-
Received:2023-06-12Online:2024-02-10Published:2024-03-06 -
Contact:QUAN Jiahui E-mail:yubeilengzhi@163.com
摘要:
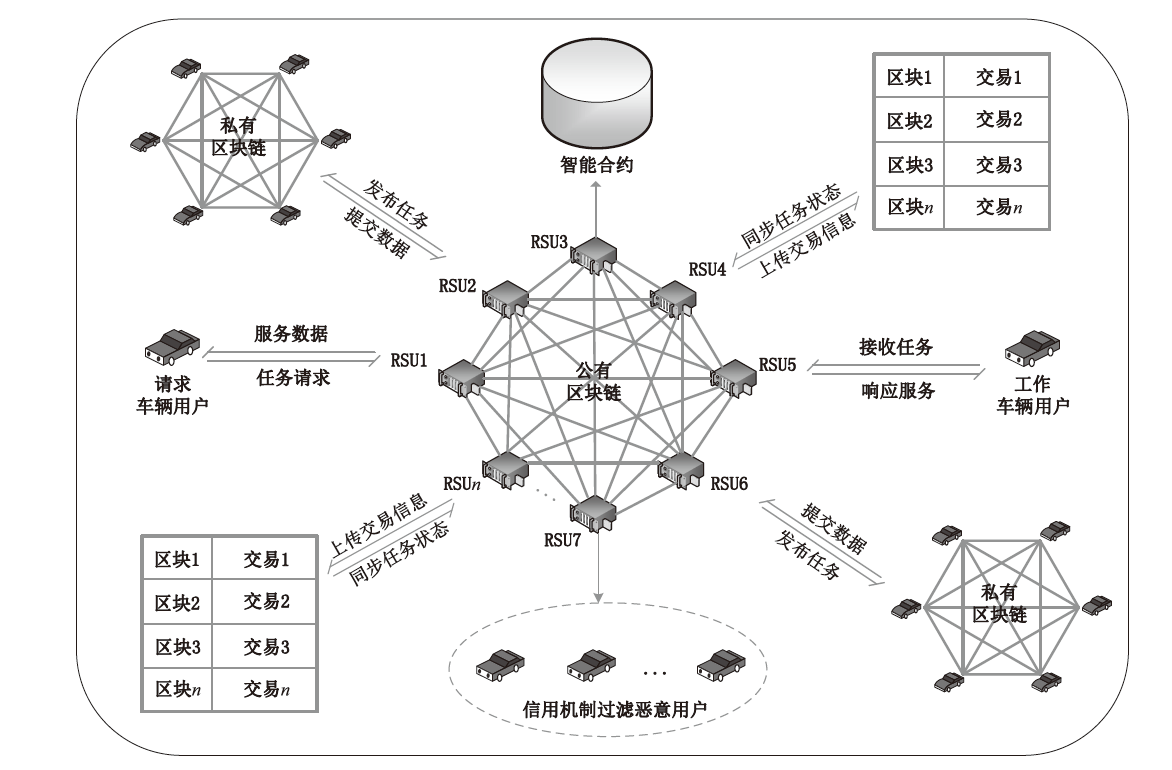
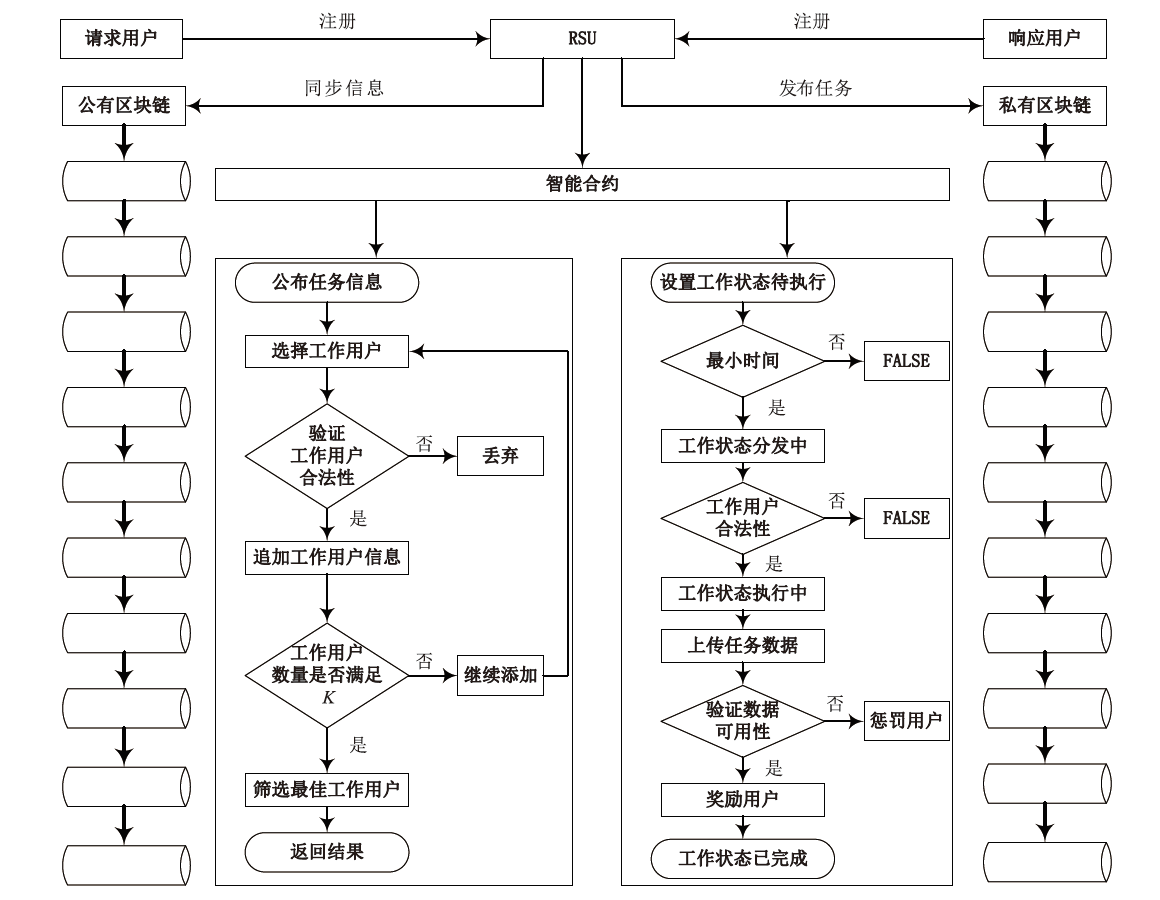
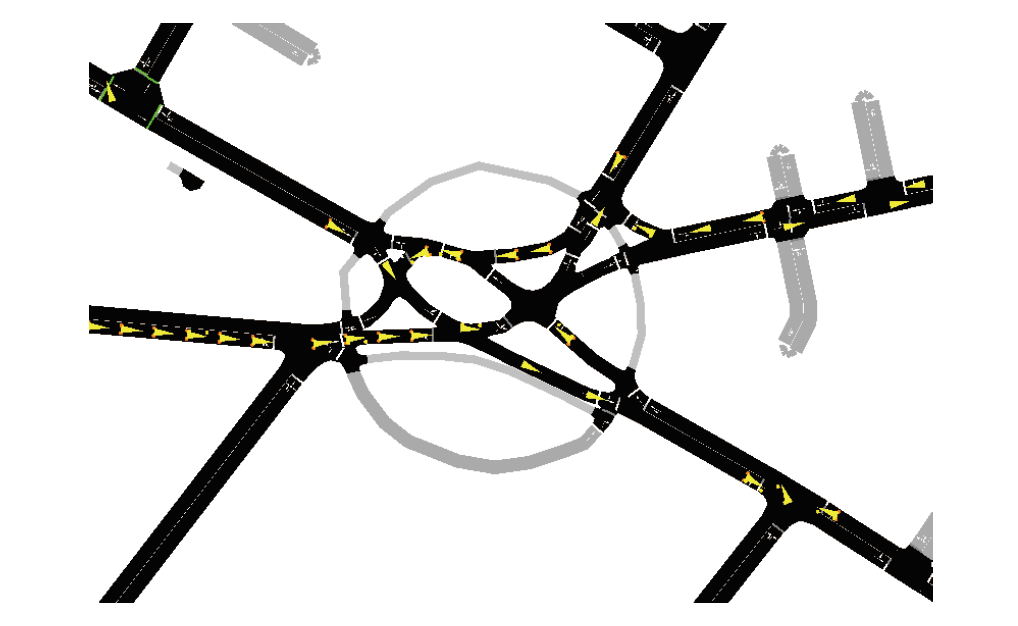
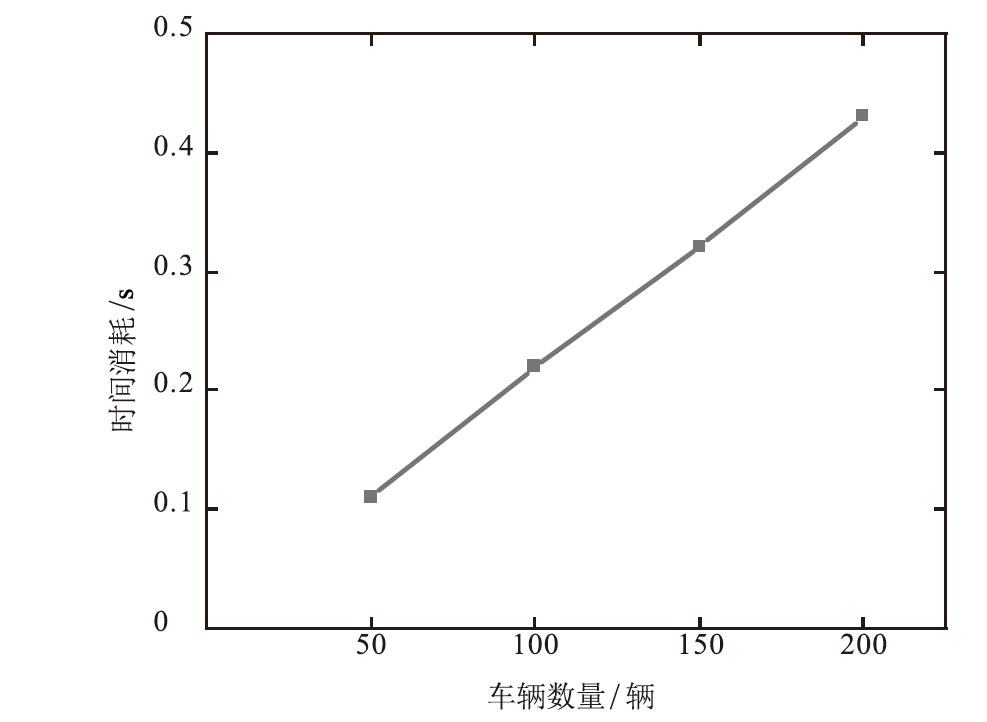
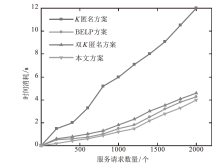
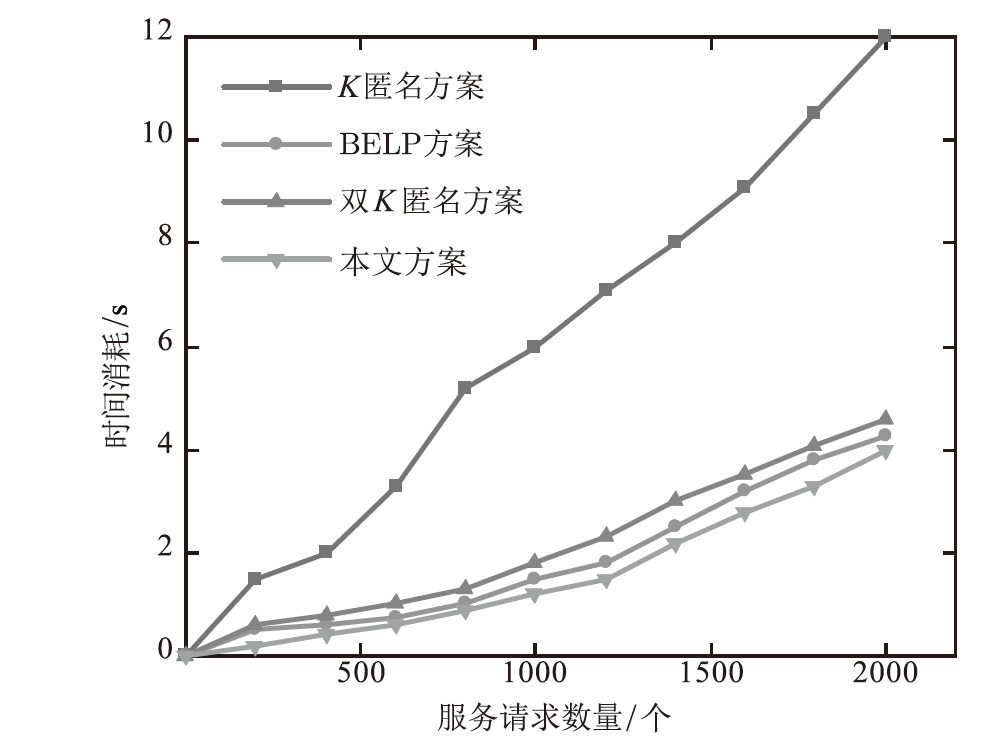
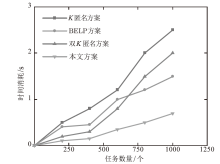
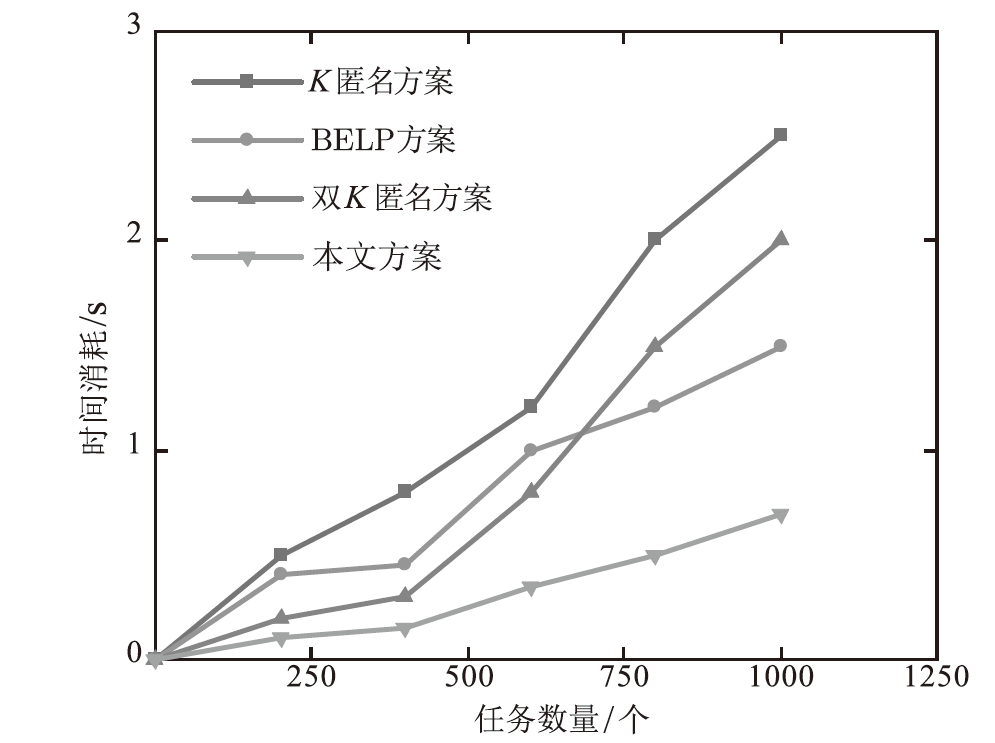
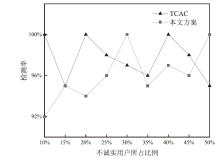
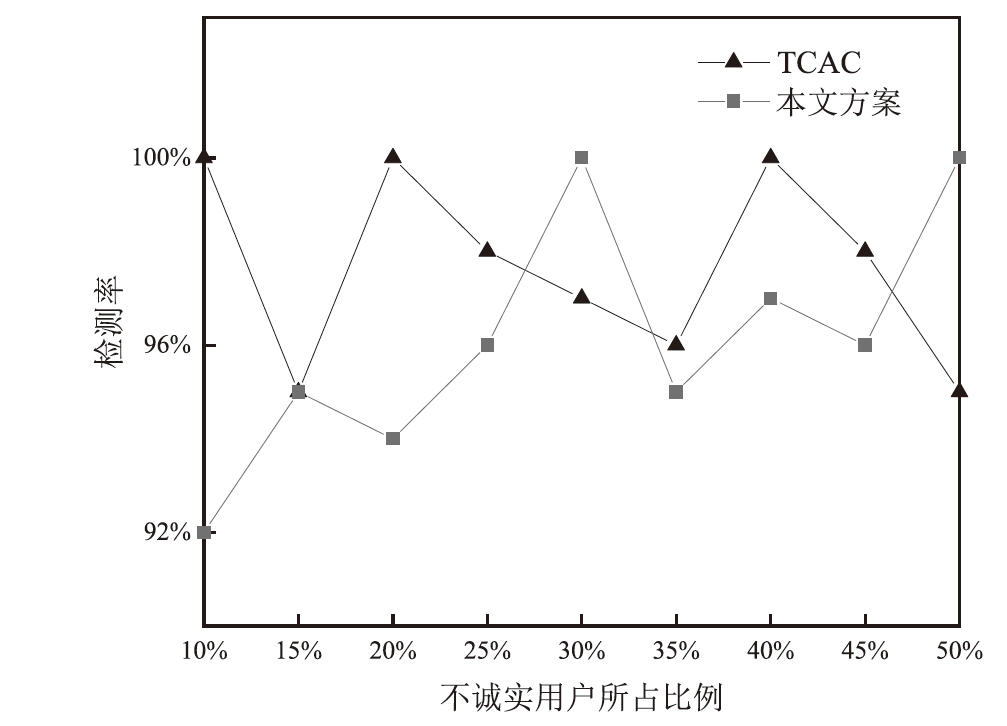
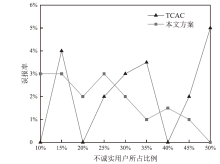
在车联网位置隐私服务中,主流模型需要通过可信第三方进行通信,但该类模型的第三方服务器容易受到恶意用户的攻击,存在隐私泄露的风险。文章基于混合区块链提出一种位置隐私保护方案。该方案根据经纬度在地图上划分出可用位置点,等待用户结合K匿名技术选择位置点代表其真实位置完成匿名预处理,随后参与混合区块链的位置隐私保护服务。在位置隐私服务整个过程中,文章采用用户信用机制和混合区块链信息隔离机制,进一步加强用户位置隐私保护水平。仿真结果表明,与现有方案相比,文章所提方案降低了时间开销。
中图分类号:
引用本文
何业锋, 权家辉, 刘妍. 基于混合区块链的位置隐私保护方案[J]. 信息网络安全, 2024, 24(2): 229-238.
HE Yefeng, QUAN Jiahui, LIU Yan. A Location Privacy Protection Scheme Based on Hybrid Blockchain[J]. Netinfo Security, 2024, 24(2): 229-238.
| [1] | WU W, YANG Z, LI K. Internet of Vehicles and Applications[EB/OL]. (2016-06-17)[2023-06-10]. https://doi.org/10.1016/B978-0-12-805395-9.00016-2. |
| [2] |
ZHOU Haibo, XU Wenchao, CHEN Jiacheng, et al. Evolutionary V2X Technologies Toward the Internet of Vehicles: Challenges and Opportunities[J]. Proceedings of the IEEE, 2020, 108(2): 308-323.
doi: 10.1109/PROC.5 URL |
| [3] |
SUN Yunchuan, WU Lei, WU Shizhong, et al. Attacks and Countermeasures in the Internet of Vehicles[J]. Annals of Telecommunications, 2017, 72: 283-295.
doi: 10.1007/s12243-016-0551-6 URL |
| [4] | OTHMANE L B, WEFFERS H, MOHAMAD M M, et al. A Survey of Security and Privacy in Connected Vehicles[EB/OL]. (2015-03-18)[2023-06-10]. https://doi.org/10.1007/978-1-4939-2468-4_10. |
| [5] |
QIU Ying, LIU Yi, LI Xuan, et al. A Novel Location Privacy-Preserving Approach Based on Blockchain[J]. Sensors, 2020, 20(12): 3519.
doi: 10.3390/s20123519 URL |
| [6] |
KHAN S, SHARMA I, ASLAM M, et al. Security Challenges of Location Privacy in VANETs and State-of-the-Art Solutions: A Survey[J]. Future Internet, 2021, 13(4): 96.
doi: 10.3390/fi13040096 URL |
| [7] | SAGIRLAR G, CARMINATI B, FERRARI E, et al. Hybrid-Iot: Hybrid Blockchain Architecture for Internet of Things-Pow Sub-Blockchains[C]// IEEE. 2018 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData). New York:IEEE, 2018: 1007-1016. |
| [8] | WANG Shuai, YUAN Yong, WANG Xiao, et al. An Overview of Smart Contract: Architecture, Applications, and Future Trends[C]// IEEE. 2018 IEEE Intelligent Vehicles Symposium (IV). New York: IEEE, 2018: 108-113. |
| [9] |
ZHENG Zibin, XIE Shaoan, DAI Hong-Ning, et al. An Overview on Smart Contracts: Challenges, Advances and Platforms[J]. Future Generation Computer Systems, 2020, 105: 475-491.
doi: 10.1016/j.future.2019.12.019 URL |
| [10] |
ZHANG Junwei, YANG Fan, MA Zhuo, et al. A Decentralized Location Privacy-Preserving Spatial Crowdsourcing for Internet of Vehicles[J]. IEEE Transactions on Intelligent Transportation Systems, 2020, 22(4): 2299-2313.
doi: 10.1109/TITS.2020.3010288 URL |
| [11] | KANG Jiawen, YU Rong, HUANG Xumin, et al. Location Privacy Attacks and Defenses in Cloud-Enabled Internet of Vehicles[J]. IEEE Wireless Communications, 2016, 23(5): 52-59. |
| [12] | WANG Fei, DU Yifan, XU Yongjun, et al. EPAF: An Efficient Pseudonymous-Based Inter-Vehicle Authentication Framework for VANET[C]// Springer. Mobile Ad-Hoc and Sensor Networks:13th International Conference. Heidelberg: Springer, 2018: 252-270. |
| [13] |
FENG Jingyu, WANG Yin, WANG Jialin, et al. Blockchain-Based Data Management and Edge-Assisted Trusted Cloaking Area Construction for Location Privacy Protection in Vehicular Networks[J]. IEEE Internet of Things Journal, 2020, 8(4): 2087-2101.
doi: 10.1109/JIoT.6488907 URL |
| [14] |
CHULERTTIYAWONG D, JAMALIPOUR A. A Blockchain Assisted Vehicular Pseudonym Issuance and Management System for Conditional Privacy Enhancement[J]. IEEE Access, 2021, 9: 127305-127319.
doi: 10.1109/ACCESS.2021.3112013 URL |
| [15] |
CHEN Yanru, LI Jingpeng, WANG Fan, et al. DS2PM: A Data Sharing Privacy Protection Model Based on Blockchain and Federated Learning[J]. IEEE Internet of Things Journal, 2021, 10(14): 12112-12125.
doi: 10.1109/JIOT.2021.3134755 URL |
| [16] |
ZOU Shihong, XI Jinwen, XU Guoai, et al. Crowdhb: A Decentralized Location Privacy-Preserving Crowdsensing System Based on a Hybrid Blockchain Network[J]. IEEE Internet of Things Journal, 2021, 9(16): 14803-14817.
doi: 10.1109/JIOT.2021.3084937 URL |
| [17] |
CASADO-VARA R, CHAMOSO P, DE LA PRIETA F, et al. Non-Linear Adaptive Closed-Loop Control System for Improved Efficiency in IoT-Blockchain Management[J]. Information Fusion, 2019, 49: 227-239.
doi: 10.1016/j.inffus.2018.12.007 URL |
| [18] |
MOHANTA B K, JENA D, RAMASUBBAREDDY S, et al. Addressing Security and Privacy Issues of IoT Using Blockchain Technology[J]. IEEE Internet of Things Journal, 2020, 8(2): 881-888.
doi: 10.1109/JIoT.6488907 URL |
| [19] |
CABALLERO-GIL C, MOLINA-GIL J, HERNÁNDEZ-SERRANO J, et al. Providing K-Anonymity and Revocation in Ubiquitous VANETs[J]. Ad Hoc Networks, 2016, 36: 482-494.
doi: 10.1016/j.adhoc.2015.05.016 URL |
| [20] | LÈBRE M A, LE MOUËL F, MÉNARD E. Microscopic Vehicular Mobility Trace of Europarc Roundabout, Creteil, France[EB/OL]. (2015-04-15)[2023-06-10]. https://zenodo.org/records/16870. |
| [21] |
SWEENEY L. K-Anonymity: A Model for Protecting Privacy[J]. International Journal of Uncertainty, Fuzziness and Knowledge-Based Systems, 2002, 10(5): 557-570.
doi: 10.1142/S0218488502001648 URL |
| [22] |
CHAUDHARY B, SINGH K. A Blockchain Enabled Location-Privacy Preserving Scheme for Vehicular Ad-Hoc Networks[J]. Peer-to-Peer Networking and Applications, 2021, 14: 3198-3212.
doi: 10.1007/s12083-021-01079-5 |
| [23] |
XING Ling, JIA Xiaofan, GAO Jianping, et al. A Location Privacy Protection Algorithm Based on Double K-Anonymity in the Social Internet of Vehicles[J]. IEEE Communications Letters, 2021, 25(10): 3199-3203.
doi: 10.1109/LCOMM.2021.3072671 URL |
| [1] | 周权, 曾志康, 王科梦, 陈梦龙. 具有向后无关性的群签名位置隐私保护方案[J]. 信息网络安全, 2023, 23(3): 62-72. |
| [2] | 何泾沙, 杜晋晖, 朱娜斐. 基于k匿名的准标识符属性个性化实现算法研究[J]. 信息网络安全, 2020, 20(10): 19-26. |
| [3] | 许力, 朱瑞, 曾雅丽. 认知无线电网络中基于SpaceTwist的位置隐私保护方案[J]. 信息网络安全, 2019, 19(2): 18-27. |
| [4] | 方跃坚, 朱锦钟, 周文, 李同亮. 数据挖掘隐私保护算法研究综述[J]. 信息网络安全, 2017, 17(2): 6-11. |
| [5] | 李晴, 叶阿勇, 许力. 公众环境下无线接入的安全问题研究[J]. 信息网络安全, 2016, 16(4): 69-75. |
| [6] | 朱义杰, 彭长根, 李甲帅, 马海峰. 一种结合查询隐私和位置隐私的 LBS隐私度量框架[J]. 信息网络安全, 2016, 16(2): 47-53. |
| [7] | 吴莎莎, 熊金波, 叶帼华, 姚志强. 移动互联网环境下基于假位置的位置隐私保护研究[J]. 信息网络安全, 2016, 16(10): 54-59. |
| [8] | 张海川, 赵泽茂, 田玉杰, 李学双. 基于个性化空间匿名算法最优化选择研究[J]. 信息网络安全, 2015, 15(3): 23-27. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||