信息网络安全 ›› 2024, Vol. 24 ›› Issue (10): 1553-1561.doi: 10.3969/j.issn.1671-1122.2024.10.009
联邦学习模型所有权保护方案综述
萨其瑞1, 尤玮婧2( ), 张逸飞1, 邱伟杨2, 马存庆1
), 张逸飞1, 邱伟杨2, 马存庆1
- 1.中国科学院信息工程研究所,北京100085
2.福建师范大学计算机与网络空间安全学院,福州 350108
-
收稿日期:2024-06-08出版日期:2024-10-10发布日期:2024-09-27 -
通讯作者:尤玮婧,youweijing@fjnu.edu.cn -
作者简介:萨其瑞(2000—),女,内蒙古,硕士研究生,主要研究方向为数据安全|尤玮婧(1994—),女,福建,副教授,博士,CCF会员,主要研究方向为数据要素确权|张逸飞(1994—),男,陕西,助理研究员,博士,CCF会员,主要研究方向为数据安全|邱伟杨(2001—),男,福建,硕士研究生,主要研究方向为人工智能安全|马存庆(1984—),男,青海,高级工程师,博士,CCF会员,主要研究方向为网络与信息系统安全 -
基金资助:国家自然科学基金(62202102)
A Survey of Ownership Protection Schemes for Federated Learning Models
SA Qirui1, YOU Weijing2( ), ZHANG Yifei1, QIU Weiyang2, MA Cunqing1
), ZHANG Yifei1, QIU Weiyang2, MA Cunqing1
- 1. Institute of Information Engineering, Chinese Academy of Sciences, Beijing 100085, China
2. College of Computer and Cyber Security, Fujian Normal University, Fuzhou 350108, China
-
Received:2024-06-08Online:2024-10-10Published:2024-09-27
摘要:
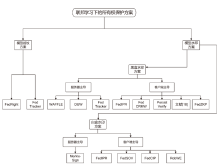
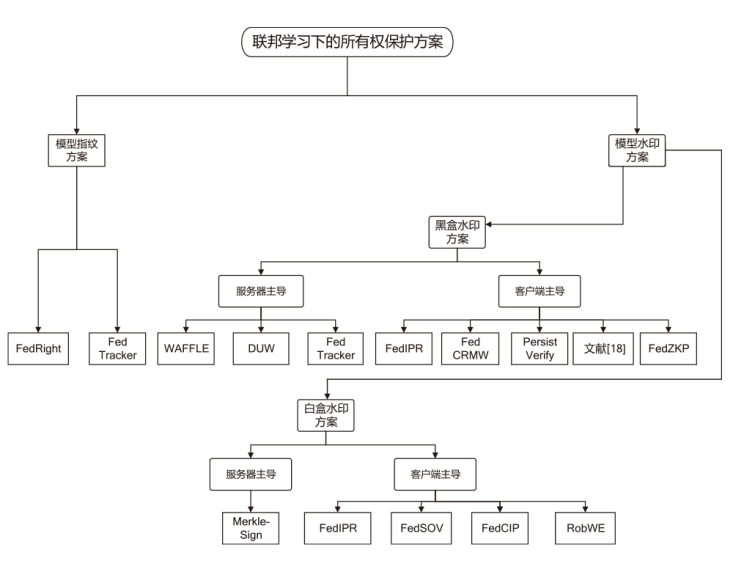
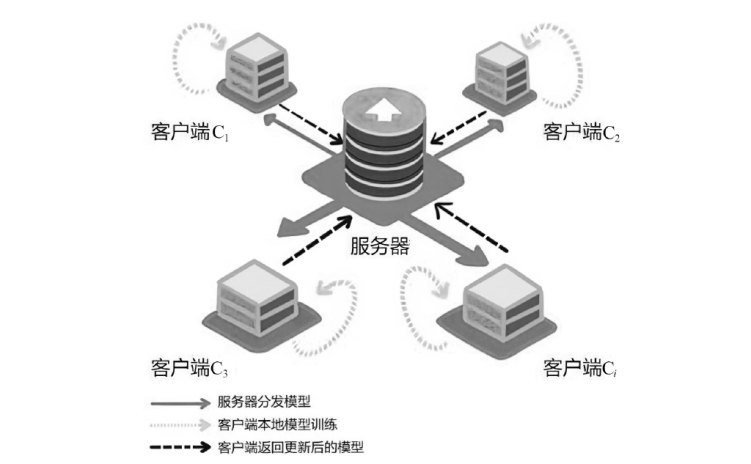
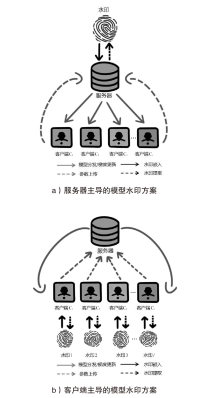
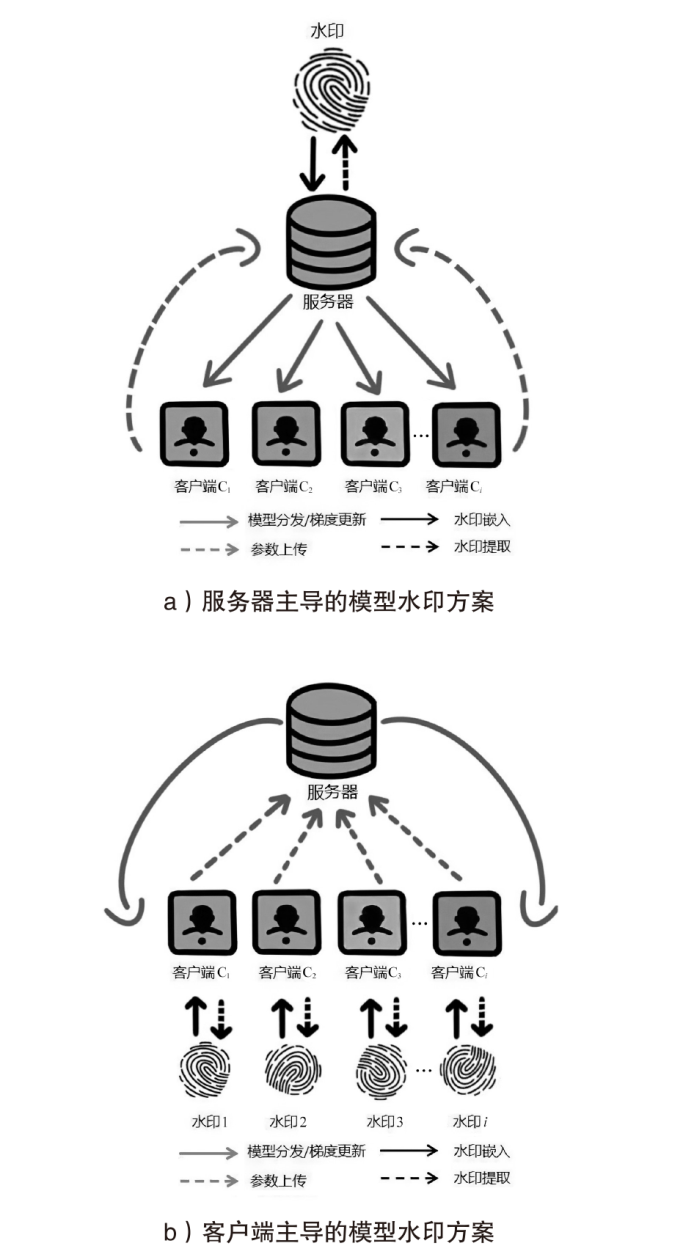
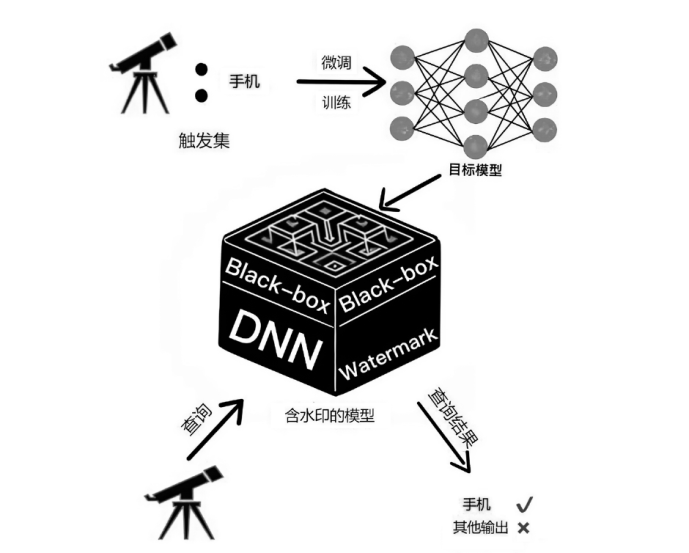
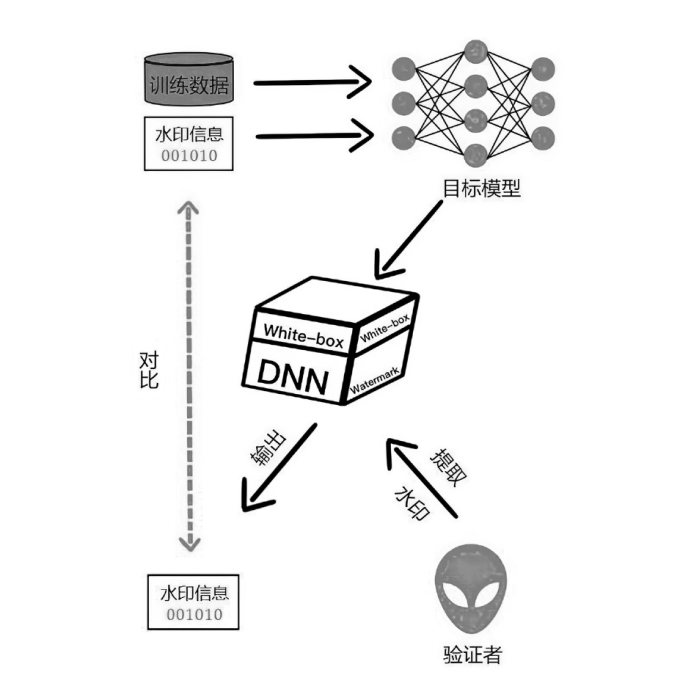
近年来,机器学习逐渐成为推动各行业发展的一种关键技术。联邦学习通过融合本地数据训练和在线梯度迭代,实现了分布式安全多方机器学习中的模型泛化能力和数据隐私保护双提升。由于联邦学习模型需要投入大量的训练成本(包括算力、数据集等),因此,对凝结了巨大经济价值的联邦学习模型进行所有权保护显得尤为重要。文章调研了现存的针对联邦学习模型的所有权保护方案,通过对两种模型指纹方案、8种黑盒模型水印方案和5种白盒模型水印方案的梳理,分析联邦学习模型所有权保护的研究现状。此外,文章结合深度神经网络模型所有权保护方法,对联邦学习模型所有权保护的未来研究方向进行展望。
中图分类号:
引用本文
萨其瑞, 尤玮婧, 张逸飞, 邱伟杨, 马存庆. 联邦学习模型所有权保护方案综述[J]. 信息网络安全, 2024, 24(10): 1553-1561.
SA Qirui, YOU Weijing, ZHANG Yifei, QIU Weiyang, MA Cunqing. A Survey of Ownership Protection Schemes for Federated Learning Models[J]. Netinfo Security, 2024, 24(10): 1553-1561.
| [1] | MCMAHAN H B, MOORE E, RAMAGE D, et al. Communication-Efficient Learning of Deep Networks from Decentralized Data[EB/OL]. (2023-01-26)[2024-05-23]. https://arxiv.org/abs/1602.05629v4. |
| [2] | LANSARI M, BELLAFQIRA R, KAPUSTA K, et al. When Federated Learning Meets Watermarking: A Comprehensive Overview of Techniques for Intellectual Property Protection[J]. Machine Learning and Knowledge Extraction, 2023, 5(4): 1382-1406. |
| [3] | YANG Qiang, LIU Yang, CHEN Tianjian, et al. Federated Machine Learning[J]. ACM Transactions on Intelligent Systems and Technology, 2019, 10(2): 1-19. |
| [4] |
LI Tian, SAHU A K, TALWALKAR A, et al. Federated Learning: Challenges, Methods, and Future Directions[J]. IEEE Signal Processing Magazine, 2020, 37(3): 50-60.
doi: 10.1109/MSP.2020.2975749 |
| [5] | BISHOP C M. Pattern Recognition and Machine Learning[M]. New York: Springer, 2006. |
| [6] | KIM B, LEE S, LEE S, et al. Margin-Based Neural Network Watermarking[C]// PMLR. International Conference on Machine Learning. New York: PMLR, 2023: 16696-16711. |
| [7] | PENG Zirui, LI Shaofeng, CHEN Guoxing, et al. Fingerprinting Deep Neural Networks Globally via Universal Adversarial Perturbations[C]// IEEE. 2022 IEEE/CVF Conference on Computer Vision and Pattern Recognition (CVPR). New York: IEEE, 2022: 13420-13429. |
| [8] | TIAN Yulong, SUYA F, XU Fengyuan, et al. Stealthy Backdoors as Compression Artifacts[J]. IEEE Transactions on Information Forensics and Security, 2022, 17: 1372-1387. |
| [9] | LI Yiming, WU Baoyuan, JIANG Yong, et al. Backdoor Learning: A Survey[EB/OL]. (2020-08-21)[2024-05-23]. https://arxiv.org/abs/2007.08745v2. |
| [10] | ADI Y, BAUM C, CISSE M, et al. Turning Your Weakness into a Strength: Watermarking Deep Neural Networks by Backdooring[EB/OL]. (2018-06-11)[2024-05-23]. https://arxiv.org/abs/1802.04633v3. |
| [11] | CHEN Jinyin, LI Mingjun, CHENG Yao, et al. FedRight: An Effective Model Copyright Protection for Federated Learning[EB/OL]. (2023-09-26)[2024-05-23]. https://doi.org/10.1016/j.cose.2023.103504. |
| [12] | SHAO Shuo, YANG Wenyuan, GU Hanlin, et al. FedTracker: Furnishing Ownership Verification and Traceability for Federated Learning Model[J]. IEEE Transactions on Dependable and Secure Computing, 2024 (99): 1-18. |
| [13] | TEKGUL B G A, XIA Yuxi, MARCHAL S, et al. WAFFLE: Watermarking in Federated Learning[C]// IEEE. 2021 40th International Symposium on Reliable Distributed Systems (SRDS). New York: IEEE, 2021: 310-320. |
| [14] | YU Shuyang, HONG Junyuan, ZENG Yi, et al.Who Leaked the Model? Tracking IP Infringers in Accountable Federated Learning[EB/OL]. (2023-12-06)[2024-05-23]. https://arxiv.org/abs/2312.03205v1. |
| [15] | LI Bowen, FAN Lixin, GU Hanlin, et al. FedIPR: Ownership Verification for Federated Deep Neural Network Models[J]. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2023, 45(4): 4521-4536. |
| [16] | NIE Hewang, LU Songfeng. FedCRMW: Federated Model Ownership Verification with Compression-Resistant Model Watermarking[EB/OL]. (2024-03-26)[2024-05-23]. https://www.sciencedirect.com/science/article/abs/pii/S0957417424006420?via%3Dihub. |
| [17] | NIE Hewang, LU Songfeng. PersistVerify: Federated Model Ownership Verification with Spatial Attention and Boundary Sampling[EB/OL]. (2024-03-21)[2024-05-23]. https://www.sciencedirect.com/science/article/abs/pii/S0950705124003101?via%3Dihub. |
| [18] | YANG Wenyuan, SHAO Shuo, YANG Yue, et al. Watermarking in Secure Federated Learning: A Verification Framework Based on Client-Side Backdooring[J]. ACM Transactions on Intelligent Systems and Technology, 2024, 15(1): 1-25. |
| [19] | YANG Wenyuan, YIN Yuguo, ZHU Gongxi, et al. FedZKP: Federated Model Ownership Verification with Zero-Knowledge Proof[EB/OL]. (2023-05-10)[2024-05-23]. https://arxiv.org/abs/2305.04507v2. |
| [20] | UCHIDA Y, NAGAI Y, SAKAZAWA S, et al. Embedding Watermarks into Deep Neural Networks[C]// ACM. Proceedings of the 2017 ACM on International Conference on Multimedia Retrieval. New York: ACM, 2017: 269-277. |
| [21] | LI Fangqi, WANG Shilin, LIEW A W C. Watermarking Protocol for Deep Neural Network Ownership Regulation in Federated Learning[C]// IEEE. 2022 IEEE International Conference on Multimedia and Expo Workshops (ICMEW). New York: IEEE, 2022: 1-4. |
| [22] | YANG Wenyuan, ZHU Gongxi, YIN Yuguo, et al. FedSOV: Federated Model Secure Ownership Verification with Unforgeable Signature[EB/OL]. (2023-05-10)[2024-05-23]. https://arxiv.org/abs/2305.06085v1. |
| [23] | LIANG Junchuan, WANG Rong. FedCIP: Federated Client Intellectual Property Protection with Traitor Tracking[EB/OL]. (2023-06-02)[2024-05-23]. https://arxiv.org/abs/2306.01356v1. |
| [24] | XU Yang, TAN Yunlin, ZHANG Cheng, et al. RobWE: Robust Watermark Embedding for Personalized Federated Learning Model Ownership Protection[EB/OL]. (2024-02-29)[2024-05-23]. https://arxiv.org/abs/2402.19054v1. |
| [1] | 郭倩, 赵津, 过弋. 基于分层聚类的个性化联邦学习隐私保护框架[J]. 信息网络安全, 2024, 24(8): 1196-1209. |
| [2] | 文伟平, 张世琛, 王晗, 时林. 基于虚拟机自省的Linux恶意软件检测方案[J]. 信息网络安全, 2024, 24(5): 657-666. |
| [3] | 戚晗, 王敬童, 拱长青. 基于随机量子层的变分量子卷积神经网络鲁棒性研究[J]. 信息网络安全, 2024, 24(3): 363-373. |
| [4] | 薛茗竹, 胡亮, 王明, 王峰. 基于联邦学习和区块链技术的TAP规则处理系统[J]. 信息网络安全, 2024, 24(3): 473-485. |
| [5] | 冯光升, 蒋舜鹏, 胡先浪, 马明宇. 面向物联网的入侵检测技术研究新进展[J]. 信息网络安全, 2024, 24(2): 167-178. |
| [6] | 林怡航, 周鹏远, 吴治谦, 廖勇. 基于触发器逆向的联邦学习后门防御方法[J]. 信息网络安全, 2024, 24(2): 262-271. |
| [7] | 金志刚, 丁禹, 武晓栋. 融合梯度差分的双边校正联邦入侵检测算法[J]. 信息网络安全, 2024, 24(2): 293-302. |
| [8] | 印杰, 陈浦, 杨桂年, 谢文伟, 梁广俊. 基于人工智能的物联网DDoS攻击检测[J]. 信息网络安全, 2024, 24(11): 1615-1623. |
| [9] | 陈宝刚, 张毅, 晏松. 民航空管信息系统用户多因子持续身份可信认证方法研究[J]. 信息网络安全, 2024, 24(11): 1632-1642. |
| [10] | 兰浩良, 王群, 徐杰, 薛益时, 张勃. 基于区块链的联邦学习研究综述[J]. 信息网络安全, 2024, 24(11): 1643-1654. |
| [11] | 王南, 袁也, 杨浩然, 文周之, 苏明, 刘晓光. 环保大数据在区块链中的隐私计算[J]. 信息网络安全, 2024, 24(10): 1515-1527. |
| [12] | 张子涵, 赖清楠, 周昌令. 深度学习框架模糊测试研究综述[J]. 信息网络安全, 2024, 24(10): 1528-1536. |
| [13] | 陈婧, 张健. 基于知识蒸馏的无数据个性化联邦学习算法[J]. 信息网络安全, 2024, 24(10): 1562-1569. |
| [14] | 吴立钊, 汪晓丁, 徐恬, 阙友雄, 林晖. 面向半异步联邦学习的防御投毒攻击方法研究[J]. 信息网络安全, 2024, 24(10): 1578-1585. |
| [15] | 吴昊天, 李一凡, 崔鸿雁, 董琳. 基于零知识证明和区块链的联邦学习激励方案[J]. 信息网络安全, 2024, 24(1): 1-13. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||