信息网络安全 ›› 2023, Vol. 23 ›› Issue (9): 37-46.doi: 10.3969/j.issn.1671-1122.2023.09.004
基于SM9的属性加密的区块链访问控制方案
- 1.广州大学数学与信息科学学院,广州 510006
2.广州大学计算机科学与网络工程学院,广州 510006
-
收稿日期:2023-02-08出版日期:2023-09-10发布日期:2023-09-18 -
通讯作者:周权 E-mail:zhouqq@gzhu.edu.cn -
作者简介:周权(1971—),男,四川,副教授,博士,主要研究方向为可信计算、传感器网络安全和云计算安全|陈民辉(1998—),男,广东,硕士研究生,主要研究方向为密码学、访问控制和区块链|卫凯俊(1999—),男,广东,硕士研究生,主要研究方向为密码学、访问控制和区块链|郑玉龙(2000—),男,安徽,硕士研究生,主要研究方向为密码学、区块链和信息安全 -
基金资助:国家重点研发计划(2021YFA1000600)
Blockchain Access Control Scheme with SM9-Based Attribute Encryption
ZHOU Quan1( ), CHEN Minhui2, WEI Kaijun2, ZHENG Yulong1
), CHEN Minhui2, WEI Kaijun2, ZHENG Yulong1
- 1. School of Mathematics and Information Science, Guangzhou University, Guangzhou 510006, China
2. School of Computer Science and Cyber Engineering, Guangzhou University, Guangzhou 510006, China
-
Received:2023-02-08Online:2023-09-10Published:2023-09-18 -
Contact:ZHOU Quan E-mail:zhouqq@gzhu.edu.cn
摘要:
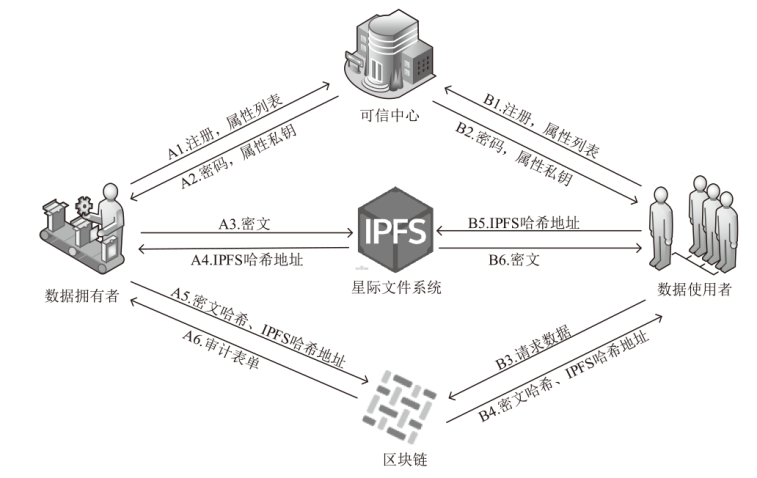
信息化社会中数据的安全共享问题已引起人们的广泛关注。数据安全共享的关键是通过密码技术对数据的访问和使用加以控制,然而传统的访问控制或者公钥加密体制都已经暴露出其在数据共享上的不足,例如访问控制策略的数量易随用户规模的增大而增多,不易管理;传统的公钥加密体制需要获取每个用户的公钥信息,并需要一对一地发送密文,通信成本高;依赖第三方服务商存储数据有单点故障的风险等。为解决上述问题,文章首先引入分布式技术区块链和星际文件系统(IPFS),提出一种基于SM9的属性加密的区块链访问控制方案,实现了安全高效的一对多数据共享和细粒度的访问控制;然后,利用区块链技术使得用户数据不被纂改,实现了数据的安全存储且可审计;最后通过判定性q-PBDHE假设证明了所提方案的安全性。
中图分类号:
引用本文
周权, 陈民辉, 卫凯俊, 郑玉龙. 基于SM9的属性加密的区块链访问控制方案[J]. 信息网络安全, 2023, 23(9): 37-46.
ZHOU Quan, CHEN Minhui, WEI Kaijun, ZHENG Yulong. Blockchain Access Control Scheme with SM9-Based Attribute Encryption[J]. Netinfo Security, 2023, 23(9): 37-46.
表1
访问结构与访问矩阵转换
| 访问结构(L) | 访问矩阵(M) |
|---|---|
| ((a, b, 2),(c, d, 1), e, 2) | (1) |
(a,b,2) \\ (c,d,1) \\ e \\ \end{matrix} \right)$ | 1 & 1 \\ 1 & 2 \\ 1 & 3 \\ \end{matrix} \right)$ |
a \\ b \\ (c,d,1) \\ e \\ \end{matrix} \right)$ | 1 & 1 & 1 \\ 1 & 1 & 2 \\ 1 & 2 & 0 \\ 1 & 3 & 0 \\ \end{matrix} \right)$ |
a \\ b \\ c \\ d \\ e \\ \end{matrix} \right)$ | 1 & 1 & 1 \\ 1 & 1 & 2 \\ 1 & 2 & 0 \\ 1 & 2 & 0 \\ 1 & 3 & 0 \\ \end{matrix} \right)$ |
| [1] | WATERS B. Ciphertext-Policy Attribute-Based Encryption: An Expressive, Efficient, and Provably Secure Realization[C]// Springer. International Conference on Practice and Theory in Public Key Cryptography. Heidelberg: Springer, 2011: 53-70. |
| [2] | GM/T 0044-2016 Information Security Technology-Identity-Based Cryptographic Algorithms SM9[S]. Beijing: Standards Press of China, 2016. |
| GM/T 0044-2016 SM9标识密码算法[S]. 北京: 中国标准出版社, 2016. | |
| [3] | NAKAMOTO S. Bitcoin: A Peer-to-Peer Electronic Cash System[EB/OL]. (2008-10-31)[2023-01-11]. https://bitcoin.org/bitcoin.pdf. |
| [4] | ZHU Liehuang, GAO Feng, SHEN Meng, et al. Survey on Privacy Preserving Techniques for Blockchain Technology[J]. Journal of Computer Research and Development, 2017, 54(10): 2170-2186. |
| 祝烈煌, 高峰, 沈蒙, 等. 区块链隐私保护研究综述[J]. 计算机研究与发展, 2017, 54(10): 2170-2186. | |
| [5] | ZHANG Yunru, HE Debiao, CHOO K. BaDS: Blockchain-Based Architecture for Data Sharing with ABS and CP-ABE in IoT[J]. Wireless Communications and Mobile Computing, 2018(7): 1-9. |
| [6] | PINNO O, GREGIO A, BONA L. ControlChain: Blockchain As A Central Enabler for Access Control Authorizations in the IoT[C]// IEEE. Globecom IEEE Global Communications Conference. New York: IEEE, 2017: 1-6. |
| [7] |
WANG Qiange, HE Pu, NIE Tiezheng, et al. Survey of Data Storage and Query Techniques in Blockchain Systems[J]. Computer Science, 2018, 45(12): 12-18.
doi: 10.11896/j.issn.1002-137X.2018.12.002 |
| 王千阁, 何蒲, 聂铁铮, 等. 区块链系统的数据存储与查询技术综述[J]. 计算机科学, 2018, 45(12): 12-18. | |
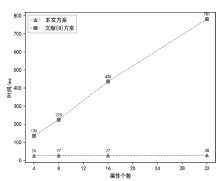
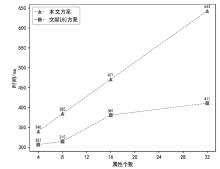
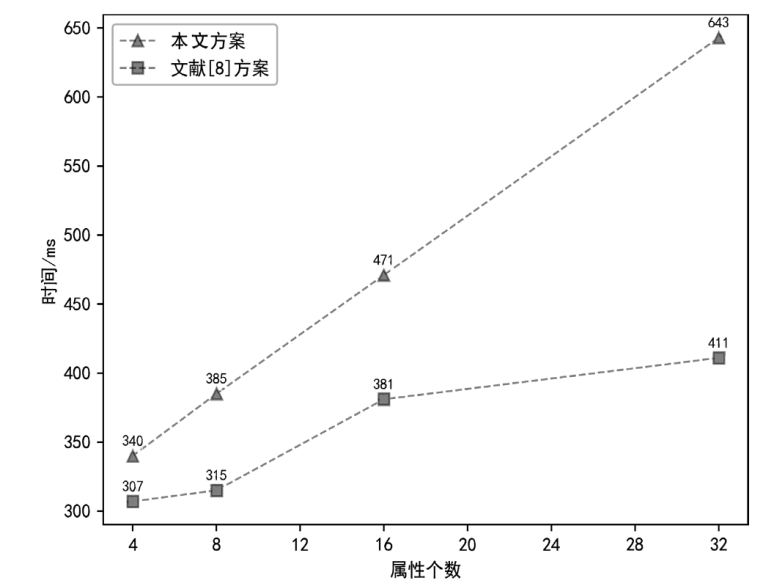
| [8] |
JI Honghan, ZHANG Hongjie, SHAO Lisong, et al. An Efficient Attribute-Based Encryption Scheme Based on SM9 Encryption Algorithm for Dispatching and Control Cloud[J]. Connection Science, 2021, 33(4): 1094-1115.
doi: 10.1080/09540091.2020.1858757 URL |
| [9] |
WANG Hao, SONG Yujiao. Secure Cloud-Based EHR System Using Attribute-Based Cryptosystem and Blockchain[J]. Journal of Medical Systems, 2018, 42(8): 1-9.
doi: 10.1007/s10916-017-0844-y URL |
| [10] |
POURNAGHI S M, BAYAT M, FARJAMI Y. MedSBA: A Novel and Secure Scheme to Share Medical Data Based on Blockchain Technology and Attribute-Based Encryption[J]. Journal of Ambient Intelligence and Humanized Computing, 2020, 11(11): 4613-4641.
doi: 10.1007/s12652-020-01710-y |
| [11] |
TIAN Youliang, YANG Kedi, WANG Zuan, et al. Algorithm of Blockchain Data Provenance Based on ABE[J]. Journal on Communications, 2019, 40(11): 101-111.
doi: 10.11959/j.issn.1000-436x.2019222 |
|
田有亮, 杨科迪, 王缵, 等. 基于属性加密的区块链数据溯源算法[J]. 通信学报, 2019, 40(11): 101-111.
doi: 10.11959/j.issn.1000-436x.2019222 |
|
| [12] |
CHENG Lichen, LIU Jiqiang, XU Guangquan, et al. SCTSC: A Semicentralized Traffic Signal Control Mode with Attribute-Based Blockchain in IoVs[J]. IEEE Transactions on Computational Social Systems, 2019, 6(6): 1373-1385.
doi: 10.1109/TCSS.6570650 URL |
| [13] | ZOU Yipeng, PENG Tao, ZHONG Wentao, et al. Reliable and Controllable Data Sharing Based on Blockchain[C]// Springer. Inernational Conference on Ubiquitous Security. Heidelberg: Springer, 2021: 229-240. |
| [14] | WANG Tong, MA Wenping, LUO Wei. Information Sharing and Secure Multi-Party Computing Model Based on Block-Chain[J]. Computer Science, 2019, 46(9): 162-168. |
| 王童, 马文平, 罗维. 基于区块链的信息共享及安全多方计算模型[J]. 计算机科学, 2019, 46(9): 162-168. | |
| [15] | ZHANG Guochao, WANG Ruijin. Blockchain Sharding Storage Model Based on Threshold Secret Sharing[J]. Computer Applications, 2019, 39(9): 2617-2622. |
| 张国潮, 王瑞锦. 基于门限秘密共享的区块链分片存储模型[J]. 计算机应用, 2019, 39(9): 2617-2622. | |
| [16] | PENG Yanqing, DU Min, LI Feifei, et al. FalconDB: Blockchain-Based Collaborative Database[C]// ACM. ACM SIGMOD International Conference on Management of Data. New York: ACM, 2020: 637-652. |
| [17] |
GUO Yu, XIE Hongcheng, MIAO Yinbin, et al. Fedcrowd: A Federated and Privacy-Preserving Crowdsourcing Platform on Blockchain[J]. IEEE Transactions on Services Computing, 2020, 15(4): 2060-2073.
doi: 10.1109/TSC.2020.3031061 URL |
| [18] | WANG Mingyue, GUO Yu, ZHANG Chen, et al. MedShare: A Privacy-Preserving Medical Data Sharing System by Using Blockchain[J]. IEEE Transactions on Services Computing, 2021, 9: 438-451. |
| [19] |
GUO Yu, ZHANG Chen, WANG Cong, et al. Towards Public Verifiable and Forward-Privacy Encrypted Search by Using Blockchain[J]. IEEE Transactions on Dependable and Secure Computing, 2022, 5: 1-16.
doi: 10.1109/TDSC.2008.9 URL |
| [20] |
SHI Yang, MA Zhiyuan, QIN Rufu, et al. Implementation of an Attribute-Based Encryption Scheme Based on SM9[J]. Applied Sciences, 2019, 9(15): 3074-3088.
doi: 10.3390/app9153074 URL |
| [21] | SAHAI A, WATERS B. Fuzzy Identity-Based Encryption[C]// Springer. Annual International Conference on Theory and Applications of Cryptographic Techniques. Heidelberg: Springer, 2005: 457-473. |
| [22] | GOYAL V, PANDEY O, SAHAI A, et al. Attribute-Based Encryption for Fine-Grained Access Control of Encrypted Data[C]// ACM. ACM Conference on Computer and Communications Security. New York: ACM, 2006: 89-98. |
| [23] | BETHENCOURT J, SAHAI A, WATERS B. Ciphertext-Policy Attribute-Based Encryption[C]// IEEE. IEEE Symposium on Security and Privacy. New York: IEEE, 2007: 321-334. |
| [24] | LIU Zhen, CAO Zhenfu. On Efficiently Transferring the Linear Secret-Sharing Scheme Matrix in Ciphertext-Policy Attribute-Based Encryption[EB/OL]. [2023-01-11]. https://citeseerx.ist.psu.edu/document?repid=rep1&type=pdf&doi=8f0502461693d016c6a46b73ad20f4fc23f45c54. |
| [1] | 公鹏飞, 谢四江, 程安东. 基于HotStuff改进的多主节点共识算法[J]. 信息网络安全, 2023, 23(9): 108-117. |
| [2] | 赵佳豪, 蒋佳佳, 张玉书. 基于动态默克尔哈希树的跨链数据一致性验证模型[J]. 信息网络安全, 2023, 23(9): 95-107. |
| [3] | 邵震哲, 蒋佳佳, 赵佳豪, 张玉书. 面向跨链的改进加权拜占庭容错算法[J]. 信息网络安全, 2023, 23(8): 109-120. |
| [4] | 覃思航, 代炜琦, 曾海燕, 顾显俊. 基于区块链的电力应用数据安全共享研究[J]. 信息网络安全, 2023, 23(8): 52-65. |
| [5] | 石润华, 谢晨露. 云边缘环境中基于属性加密的可验证EMR外包解决方案[J]. 信息网络安全, 2023, 23(7): 9-21. |
| [6] | 张晓旭, 石润华. EHR系统中一种验证外包加密数据正确性的访问控制方案[J]. 信息网络安全, 2023, 23(5): 85-94. |
| [7] | 郭瑞, 魏鑫, 陈丽. 工业物联网环境下可外包的策略隐藏属性基加密方案[J]. 信息网络安全, 2023, 23(3): 1-12. |
| [8] | 李春晓, 王耀飞, 徐恩亮, 赵钰. 基于双线性映射的区块链安全范围搜索技术研究[J]. 信息网络安全, 2023, 23(3): 22-34. |
| [9] | 王晶宇, 马兆丰, 徐单恒, 段鹏飞. 支持国密算法的区块链交易数据隐私保护方案[J]. 信息网络安全, 2023, 23(3): 84-95. |
| [10] | 冯怡婷, 马兆丰, 徐单恒, 段鹏飞. 跨链接入的区块链安全强度评估方法[J]. 信息网络安全, 2023, 23(1): 84-92. |
| [11] | 张光华, 刘永升, 王鹤, 于乃文. 基于BiLSTM和注意力机制的智能合约漏洞检测方案[J]. 信息网络安全, 2022, 22(9): 46-54. |
| [12] | 胡艺, 佘堃. 基于区块链和智能合约的双链车联网系统[J]. 信息网络安全, 2022, 22(8): 26-35. |
| [13] | 黄保华, 赵伟宏, 彭丽, 谢统义. 基于MPT索引的高效链上PKI模型[J]. 信息网络安全, 2022, 22(8): 72-80. |
| [14] | 王健, 黄俊. 基于智能合约的日志安全存储与公平访问方法[J]. 信息网络安全, 2022, 22(7): 27-36. |
| [15] | KELEKET GOMA Christy Junior Yannick, 易文哲, 王鹃. 一种基于SGX的轻量Fabric链码可信执行环境构建方法[J]. 信息网络安全, 2022, 22(7): 73-83. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||